Email Spoofing 101: How to Avoid Becoming a Victim
Knowing how to check if an email is valid is key to helping you avoid becoming a phishing victim
Although the term “email spoofing” doesn’t sound particularly scary, the results of it can be terrifying. Considering that research from IRONSCALES, an automated phishing defense platform, shows that “secure email gateways (SEGs) fail to stop 99.5 percent of all non-trivial email spoofing attacks,” you can see why this is such a serious concern.
But what is email spoofing? In a nutshell, it’s a tactic that’s integral to virtually all types of email phishing scams. If you’ve ever received a phone call from “yourself” (either with your caller ID showing your phone number and/or your name), or if you’ve ever received an email from “yourself” (with the “from” field of the email header displaying your name and/or email address), then I’m sorry to break the news to you, but you’ve been spoofed.
Cybercriminals use this tactic to impersonate someone else to accomplish their goals. Anyone can be the victim of email spoofing — either as the recipient or as the person/organization/institution whose email is spoofed.
But there’s more to know about spoofing than just what it is and what it does. So, do you want to get answers to those other burning questions you have about email spoofing?
Let’s hash it out.
What You Need to Know About Email Phishing (and Email Spoofing)
Originally, when I set out to write this article, my focus was just to talk about what email spoofing is and what it does. But as I started to research and work on writing the content, I thought it might be best to approach this topic in terms of answering some of the top questions on the topic.
1. What is Phishing and Email Spoofing?
To put it simply, phishing refers to deceptive tactics that criminals use to trick victims into taking some action the hoodlum wants them to. Email spoofing (one of many phishing tactics criminals use) refers to sending an email that looks like it’s sent from someone it’s not. For example, a cybercriminal might send you an email that looks like it’s from your boss, your email service provider, or other trusted source.
But why would someone want to do something like this?
With phishing, the goal could be to get their targeted victims to:
- provide personal or financial information;
- turn over intellectual property and other proprietary information or data;
- perform a wire transfer or another electronic transfer of funds;
- provide login information or other user credentials;
- download a file from an email that contains malicious software; and/or
- click on a malicious link.
By sending a spoofed email that’s crafted to look like it came from someone you trust, cybercriminals know you’re more likely to engage with the content of the email and any links or attachments it contains. You’re also more likely to trust what the person says in the message. And gaining your trust is crucial to pulling off a successful scam.
2. How Does Email Spoofing Work?
Contrary to what some non-tech users may believe, email spoofing isn’t black magic. It’s not some hugely complicated task. It’s actually a very simple process that involves making email headers look like they’re coming from one person or organization when they’re really coming from another. I’m not going to provide directions for how to do it (hey, I may be a bit crazy at times, but I’m not stupid), but just know that it basically involves the use of an SMTP server and email software. Just going to leave it at that.
Proofpoint makes a salient point about spoofing in email fraud: The act of email spoofing isn’t just about spoofing the sender’s display name. It also includes other tactics such as email address spoofing, domain spoofing, and the use of look-alike domains, although display name spoofing is the most common. The company reports that in Q2 2017, “90.27% of the email fraud attacks that Proofpoint analyzed and blocked employed this tactic.”
Another tactic cybercriminals use is to research specific individuals within an organization they wish to target. They can find information about that individual, their department, and the organization’s hierarchy through the use of the company website and social media platforms such as LinkedIn.
3. Why Is a Spoof Email Such a Big Deal?
So, if you receive a spoof email — or, if someone receives an email that appears to come from you (but didn’t) — it may not seem like a big deal. But as you recently read, it’s a very big deal. Let’s say someone is pretending to be you. They change their caller ID to your name, create email addresses with your name, and identify themselves in all communications with your friends, family, colleagues, and customers. You’d be pretty worried, right? They could do nearly anything they want, and they’d be doing it in your name!
This is essentially what happens when someone uses email spoofing.
At its core, a spoof email is a method of deception. It’s a way for someone to accomplish something while hiding behind a disguise. They often use the identity of a real person, organization, or business to trick users into performing some type of action. And, as you can imagine, it’s usually bad news for both sides — the email recipients they’re trying to fool, and the people or organizations whose identities they’re using to do so.
Examples of Email Spoofing
At The SSL Store, we’re no strangers to spoofed emails. In fact, as the largest global provider of SSL/TLS certificates, we receive these types of messages all the time from malicious actors around the world. Thankfully, we understand the importance of cyber security awareness training for our employees and they know how to identify and respond to phishing and spoofed emails.
But what does a email spoofing actually look like? Some spoofed emails are well crafted and appear to come from an authentic source on first glance due to the display name spoofing. Most, however, aren’t that well designed (thankfully). Here are a few real-world spoofed email examples we’ve received over the past few months:
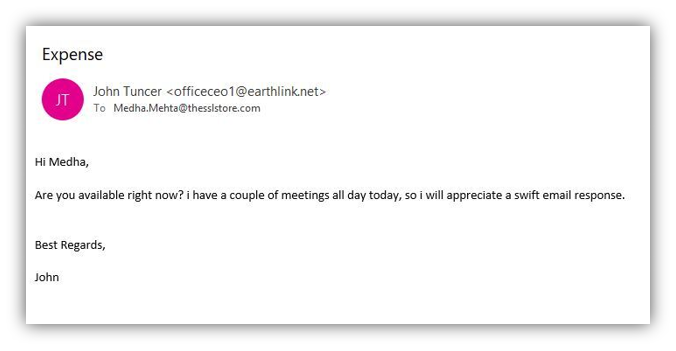
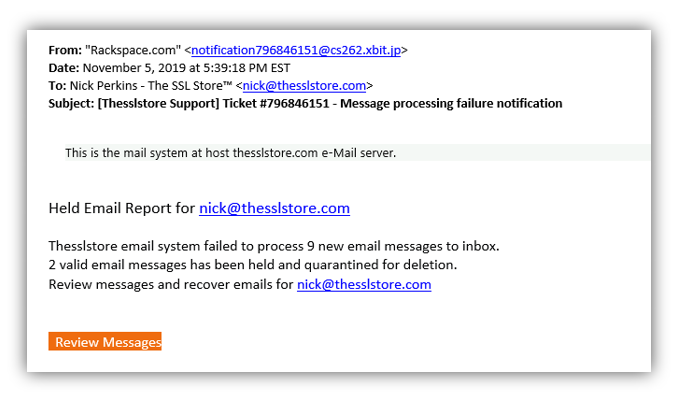
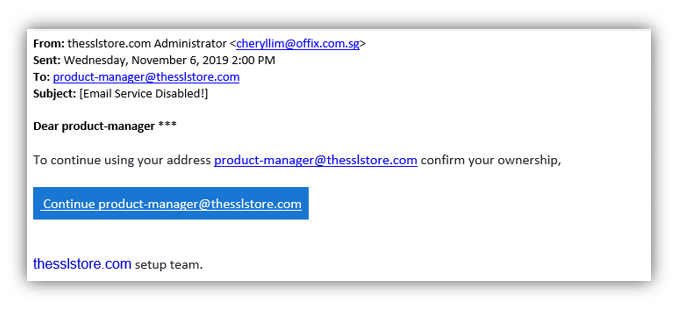
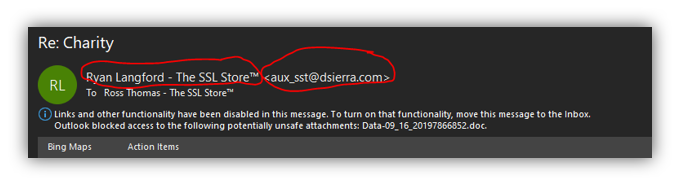
In all of the above examples, the sender used display name spoofing rather than email spoofing. That’s because display name spoofing is easier to pull off because all the cybercriminal needs to do is sign up for an email address from a free email service provider (such as Gmail, Yahoo Mail, etc.) using the name they wish to display.
4. How to Stop Email Spoofing from Affecting Your Organization.
We often receive questions from people who want to know how to prevent email spoofing attacks — both as the organization the sender is impersonating and as the potential recipient. Maybe you’re one of them. If you’ve suddenly received an influx of “undeliverable” notices in your email inbox, it’s likely that your email address is being spoofed.
So, how do you prevent your email address or domain from being spoofed in the future? And how do you help your employees recognize spoofed emails for what they are? We’ll answer both of those questions by discussing the following:
- SPF, DKIM, and DMARC email security standards
- email signing certificates
- cyber security awareness training
- email header data
Let’s start by answering your question of “how do I stop email spoofing from my domain?”
Implement SFP, DKIM, and DMARC to Stop Spoofers from Using Your Domain
Sigh. Yeah, the cybersec industry certainly loves its acronyms. This particular bowl of alphabet soup — with acronyms that stand for sender policy framework (SPF), domain keys identified mail (DKIM), and domain-based message authentication, reporting and conformance (DMARC) — is a useful combination of tools that enable you protect your email and your domain reputation. Still now sure what all of this means?
Of course, you’re welcome to read all three of the linked articles in this section for more info, but we’ll still break it all down for you here. In a nutshell:
- SPF outlines valid IP addresses that are approved to send emails for a specific domain.
- DKIM allows you to establish greater trust by preventing spoofing emails from being sent as outgoing messages on your domain. It does this by updating the DNS entry of an email domain to add a digital signature to the message header and to ensure that the email remains unaltered from when it was sent.
- DMARC is an email authentication, reporting and policy protocol that uses both SPF and DKIM to provide information about the email domain’s (its alignment, compliance, failures, etc.).
Essentially, these things together help you to prevent third-party threats from tarnishing your good name. While they’re not foolproof, they’re at least another method of security — and as we all know, you never want to be dependent on just one method.
Which brings us to our next point…
Use Email Signing Certificates to Protect Your Outgoing Emails
An email signing certificate — sometimes referred to as an S/MIME certificate or a personal authentication certificate — is something that you can use to help email recipients verify whether an email is coming from you. These certificates do two things:
- assert identity through the use of unique digital signatures, and
- use public key encryption to provide secure, end-to-end encryption for your emails. And considering that most email servers nowadays also use SSL/TLS encryption, it means that you can enjoy both data at rest and data in transit protection.
When you assert your identity, not only are you affirming that you are who you claim to be, but you’re also instilling trust and confidence in your email recipients. They’ll be more likely to click on your links or engage with your emails if they know you’re you.
This is how it looks when you receive an email from someone using an email signing certificate:
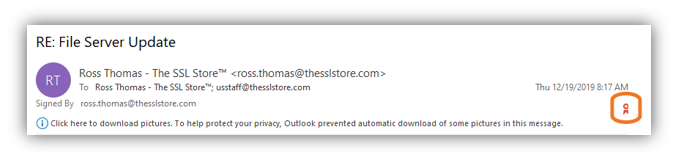
Now, let’s address what you can do to protect your business from the perspective of being an email recipient of a spoofed email.
Provide Cyber Awareness Training for Your Employees to Help Them Identify Threats
It’s no secret that your employees are often both your biggest strength and weakness in the battle against cyber security threats. Proofpoint reports that 83% of surveyed global information security professionals reported experienced phishing attacks in 2018.
That’s why cyber awareness training is so important. This type of training is beneficial to all of your employees, and no one — not even the CEO — should be excluded from this training. When you regularly train your employees, you can help them increase their knowledge and understanding of the very real threats they and your business face. And when you test them through phishing simulations, you can identify any gaps in their knowledge and tailor future trainings to meet those needs.
Teach your employees to look for some common warning signs of phishing emails:
- use of poor language, grammar, and punctuation.
- use of language that conveys a sense of urgency (to spur users to action).
- mismatching or inaccurate information in the “from” field. (For example, does the sender’s name match their email address?)
Teach Employees to Check Their Email Header Information
To identify email spoofing, what you’ll want to do is take a close look at the email header information of a suspicious message. Why? Because an email header contains a significant amount of data pertaining to the transmission of an email. In addition to email subject line information and the basic “from” and “to” sender/recipient info, other email metadata you can find in the header properties include:
- the type of content,
- browser information,
- delivery date information,
- suspicious flag or spam flags,
- language used in the email, and
- Microsoft Exchange threat scan results.
Taking the time to check email address validity sounds like a boring and unnecessary task. However, in cyber security, it’s generally considered a best practice to verify who an email is from so you know whether the sender is who they say they are. You wouldn’t just open your front door in the middle of the night if someone knocked, would you? You’d probably look through the peep hole or call out, “who is it?” if you don’t have a peep hole (at least, I’d hope you would!) to inquire as to who you’re going to yell at momentarily for waking you up.
It’s the same way with email spoofing. Before you open the door to your network (by clicking on a link, downloading an attachment, or otherwise engaging with an email), you should at least check to make sure the sender is authentic.
5. How to Check If an Email Is Valid.
So, you want to check email address validity. Good! As my gruff grandfather used to say, “now you’re cooking with gas!”
Knowing how to check whether an email is valid is an important piece of knowledge that can help keep you and your business safe in the digital world. As mentioned only moments ago, email headers provide a lot of useful information — the “who,” “what,” “when,” “where,” and “how” of an email. The only thing it doesn’t communicate is the “why.”
But, in reality, it doesn’t take a genius (evil or otherwise) to figure out why someone would want to use email spoofing. Cybercriminals just want to be able to do something and either don’t want to get caught, or they want to gain your trust by using the name or organization name of someone you know and/or trust. Either way, email spoofing is a useful way of doing what they want to do.
So, how do you check if an email is valid in Outlook 2016 or Outlook 2019? Well, you can do it one of two ways — by opening the email in a new window or by simply clicking on the email in your inbox.
Method One: From the Email Window
Step One: Open the Email in Its Own Window
You’re going to find yourself staring, confused, at another set of menu options if you don’t follow this critical first step.
Step Two: Access the Properties Menu
Select File and navigate to Properties at the bottom of the list (as shown below).
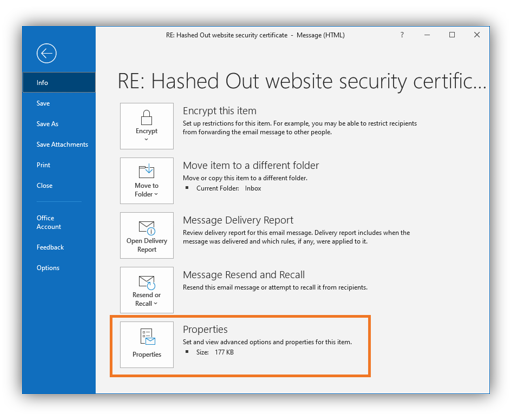
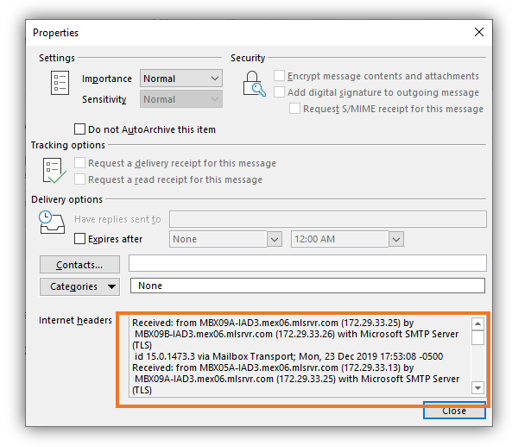
Step Three: View Your Email Property Information.
Once that window is open, you can view the message header details in the Internet headers field at the bottom of the window.
Method Two: From Your Inbox
This method is one that you can do from the comfort of your inbox.
Step One: Add a New Command Quick Access Toolbar (QAT).
At the top of your Outlook window, you’ll likely notice a few lonesome icons in the blue application bar above the main tabs. It may include icons for functions like “undo,” “redo,” and “save.” To the right, you’ll notice an arrow pointing down with a dash above it labeled Customize Quick Action Toolbar when you mouse over it. Select that and drop-down to click More Commands.
Step Two: Navigate to the All Commands Window.
In the new Outlook Options window that pops up, select All Commands from the drop-down menu labeled “Choose commands from.”
Step Three: Select Message Options from the List.
In the long column below that menu, you’ll find a long list of commands. Scroll down and select Message Options. Click Add in the center between the two list columns and select the Okay button.
Step Four: Select the Email and Press the Message Options button.
In your inbox, select the email that you wish to view the email header information for and then press the Message Options button in the QAT at the top of your Outlook window.
Not much to it, right? Yes, it’s really that simple.
Note: You can only view the email header information for emails you receive, not the ones you send.
6. Is It Illegal to Spoof an Email Address?
The CAN-SPAM Act, which spells out specific requirements for commercial messages as well as penalties for violations, prohibits spoofed headers. Not really sure whether phishing emails would fall under “commercial emails,” but still, it’s important to note.
The National Conference of State Legislatures shares that only 23 states and Guam have laws that specifically address phishing, although all states have laws that prohibit the fraudulent acquisition of another person’s personal information, computer crimes, and identity theft.
For example, here in Florida, we have Fla. Stat. §§ 668.701-.705. Under 668.703:
(1) A person with an intent to engage in conduct involving the fraudulent use or possession of another person’s identifying information may not represent oneself, directly or by implication, to be another person without the authority or approval of such other person through the use of a web page or Internet domain name and use that web page, Internet domain name, or a link to that web page or domain name or another site on the Internet to induce, request, or solicit a resident of this state to provide identifying information.”
This means that a person who fraudulently obtains a victims’ personal information may not use it to impersonate that individual.
Section 668.704 also indicates that while there’s an opportunity to bring a civil suit against the perpetrator, any civil action “must be brought within 3 years after the violation occurred.” The following individuals and groups would be able to bring a civil suit:
(a) A person engaged in the business of providing Internet access service to the public who is adversely affected by the violation.
(b) A financial institution as defined in s. 655.005(1) that is adversely affected by the violation.
(c) An owner of a web page, trademark, or service mark who is adversely affected by the violation.
(d) The Attorney General.”
7. How Do I Report a Suspicious Email?
Unfortunately, many users don’t realize they’ve been spoofed until after the fact. This realization may occur immediately for someone after they click on a malicious link, or it may not be until a few weeks (or months) down the road when they realize their information is compromised and their information is being used fraudulently to commit crimes. However, for those of you who recognize a spoofed email for what it is, there are a few things you can do to try to prevent future email spoofing.
The U.S. Federal Trade Commission (FTC) asks users to forward phishing emails to its Anti-Phishing Working Group (APWG) at reportphishing@apwg.org. What you can also do is report suspicious emails or spam to:
- your employer’s IT team. You should only do this if you receive the suspicious email on your work email address. Forward the questionable email to your IT admin or cyber security team — of course, warn them about your suspicions at the top of the email so they know to not engage with any links in the email.
- the sender’s email provider. If you can tell who their email service provider is, you can inform them about any users you think may be abusing their systems. Forward the entire email in question and specify that you think it’s spam. However, cybercriminals often use free email service providers and will simply close the email accounts after a brief period of use. Then they go and open another. It’s a seemingly never-ending cycle of abuse.
- the organization/domain the sender is spoofing. If you think that someone is pretending to be a specific company, take a moment to reach out to the company to make them aware of the situation. For example, if someone is spoofing PayPal, you can forward the entire email to PayPal to let them know about the spoof.
Email Spoofing Isn’t Going Anywhere
Unfortunately, as much as I’d like to say that email spoofing is set to become a thing of the past, it’s not. Cybercriminals are always coming out with new ways to scam people and businesses into providing money and the most valuable currency of all: information. Whether it’s your personal or financial information — or that of your customers — it’s imperative to do everything within your power to keep it out of the hands of cybercriminals. But at least there are things that you can do to protect yourself and your business from the dangers of spoofed emails.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)







 (3 votes, average: 3.67 out of 5, rated)
(3 votes, average: 3.67 out of 5, rated)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown