Everything You Need to Know About Broken Authentication
This Common OWASP Top 10 Vulnerability Let’s Hackers Take Over User & Admin Accounts – Learn How to Protect Against Broken Authentication and Keep Them Out
How many different users log in to your business’s systems everyday? For most companies, it’s a significant number. These days, more and more services are requiring our credentials – from work accounts to banking to entertainment and much more. When users log in, they assume their credentials and account are safe, right? After all, that’s the point of having secure, SSL-protected pages in the first place – to keep them protected. And that’s usually the case unless broken authentication is involved.
Broken authentication is a major issue plaguing internet users, and it has risen to the number two spot on the OWASP Top 10 List for a reason. A 2019 study by Positive Technologies found that 45 percent of web applications had vulnerabilities relating to broken authentication. These weaknesses let attackers gain unauthorized access to accounts and ultimately carry out illegal activities such as identity theft, money laundering, fraud, or stealing confidential data.
Improper configurations or poor design can result in broken authentication, as can human-related factors. For example, a 2019 survey from the National Cyber Security Centre in Great Britain found a whopping 23.2 million instances of “123456” being used as a password. Similarly, millions more used common and easy to guess passwords including vulgar words, sports teams, and of course the ultra-secure “password.”
So, what is broken authentication exactly? What are the different types of attacks? And how can you protect your site and your users against broken authentication?
Let’s hash it out.
What Does Broken Authentication Mean?
Broken authentication refers to anything that lets someone log in to an account they’re not supposed to have access to. It means that there are vulnerabilities present in a particular website or application that lets an attacker sidestep the standard security measures in order to gain unauthorized entry. Basically, they are trying to log into a victim’s account like normal, with all the regular capabilities and functionality. Since they are impersonating the user, they can perform actions under the guise of their identity and may be able to view sensitive personal and financial information, as well.
There are several different ways in which the authentication can be broken. We can be dealing with passwords, session IDs, keys, user account details, and other data that can help impersonate a victim. Regardless, the ultimate goal is to take over an account and all that comes with it.
Broken authentication can be discovered via either manual or automated means. Once a vulnerability is found, a hacker can exploit it with programs that employ things like password lists and dictionary attacks to make their way inside a system.
Broken authentication is a broad term that can refer to two different types of weaknesses – those relating to either session management or credential management.
Session Management Vulnerabilities
For a closer look at session management vulnerabilities, check out our previous article on session hijacking. Basically, a session ID is created and assigned to a user whenever they log in to a site. The session ID is used to track what the user does and helps the site respond to the user’s actions.
If an attacker can get a hold of a user’s session ID while they are logged in, then that is essentially as good as having their password. They can use the stolen session ID to impersonate the user and perform actions within the website. The image below illustrates how a session hijacking attack works:
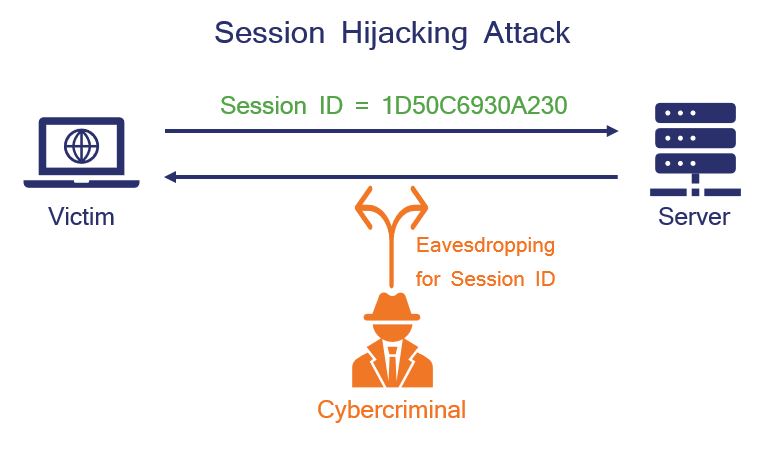
Developers should treat session IDs the same as passwords themselves. It’s critical to verify that there are no weaknesses or loopholes that can be exploited by attackers.
Credential Management Vulnerabilities
The theft of usernames and passwords is the first thing that usually comes to mind when we think of attackers gaining unauthorized access to an application. Proper credential management is critical for the users of any system, and applications themselves must take all possible precautions when dealing with passwords and their creation.
In this case, broken authentication occurs when a site fails to protect its users from attackers that try to gain access via hacked or stolen passwords.
Types of Broken Authentication Attacks
Now that we know what broken authentication refers to and the two main categories of vulnerabilities, let’s take a look at the most common types of attacks:
- Session Hijacking – As we touched on earlier, hackers can use stolen session IDs to gain unauthorized access to a system and impersonate the victim within. These kinds of attacks can occur through attack vectors such as phishing attacks, public wi-fi sniffing, or malware.
- Credential Stuffing – When databases of unencrypted login credentials are leaked, hackers can use automated tools to test out the entries and determine if any are still valid. This is essentially a kind of brute force attack, and many applications have protections to guard against this method of using compromised credentials.
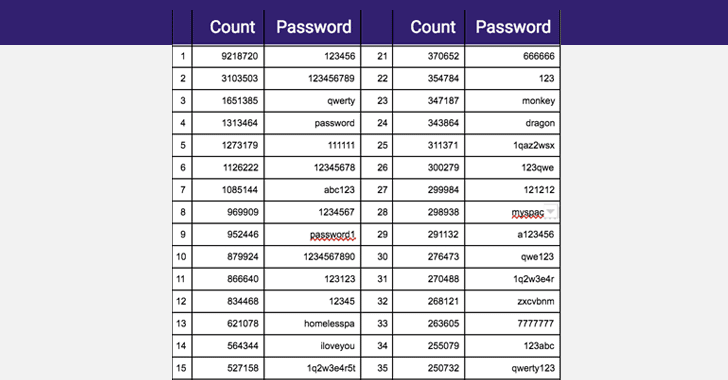
- Password Spraying – This is somewhat similar to Credential Stuffing in that it is a type of brute force attack. In this case though, attackers use lists of the most common and weak passwords. And as we saw earlier, this method often pays off considering how often “password”, “123456”, and similar strings are used as passwords. Password-complexity requirements help protect against Password Spraying. You can see some of the most commonly used (and therefore worst) passwords below:
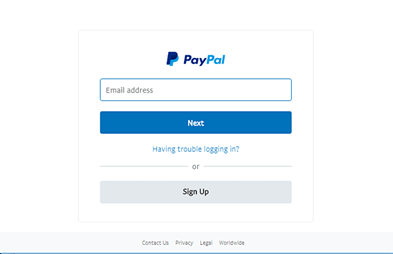
- Phishing Attacks – Here, hackers use an authentic-looking login screen (like the one seen below) in an attempt to trick users into providing their credentials. These kinds of attempts can be prevented by avoiding suspicious links, verifying the website in question, and following email security best practices. Admins can protect their users’ accounts by implementing multi-factor authentication, so even if a phishing attack is successful there’ll be another hurdle the hacker has to clear before getting account access.
What Makes an Application Vulnerable to Broken Authentication?
Broken authentication risks should always be considered, no matter what kind of website or application you’re looking at. The following items will potentially expose users to broken authentication attacks and should be avoided at all costs:
- Permitting a large number of incorrect login attempts, which enables Credential Stuffing attacks
- Permitting weak or commonly-used passwords (your computer should never look like the image below)

- Using cleartext passwords and failing to properly encrypt them
- Not requiring multi-factor authentication
- Exposing session IDs in URLs
- Not changing the session ID after each session
- Allowing passwords or session IDs to be sent over HTTP
- Not invaliding session IDs after periods of inactivity
How to Prevent Broken Authentication
Now that we’ve examined things you should avoid to minimize broken authentication risks, let’s take a look at some best practices to use instead:
- Use multi-factor authentication whenever possible in order to protect against automated attacks
- Implement stronger security on admin level accounts, such as multi-factor authentication, certificate-based authentication, IP or geo-based filtering, etc.
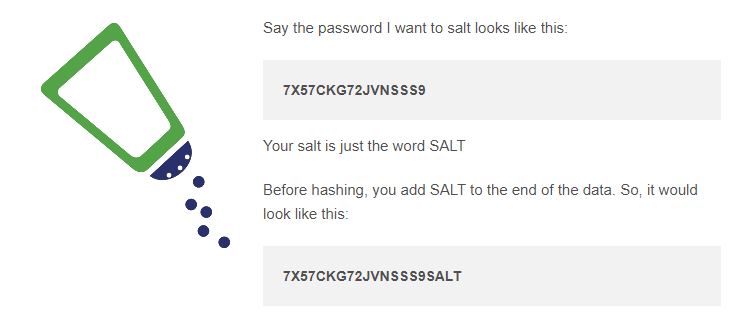
- Never store passwords in cleartext, and always encrypt or salt them (you can see an example of a “salted” password below)
- Avoid default credentials, especially for accounts with elevated privileges like administrators
- Use password-complexity checks and require that passwords contain capital and lowercase letters, numbers, and special characters
- Limit unsuccessful login attempts
- Introduce a time delay after an unsuccessful login attempt
- Alert administrators of multiple login failures
- Force HTTPS on all URLs to protect passwords and session IDs
- Block users from using common passwords like letmein or rainbow
- Keep an up-to-date password blocklist of credentials compromised in various data breaches
- Use a server-side session manager that generates random session IDs after each login
- Store session IDs in cookies, not URLs
- Invalidate session IDs after the user logouts, or after a set idle time has elapsed
If It’s Broken, Fix It
Broken authentication is a relatively straightforward and simple concept, and the vulnerabilities that enable broken authentication attacks can usually be easily prevented. By designing your site or application with authentication best practices in mind, you can eliminate the potential headaches that might spring up later on when hackers are searching for exploits. Even if you have to go back and modify what you’ve already created, it’s still worth taking the extra time and effort. After all, it only takes a single attack to erode user trust and damage the brand you’ve worked so hard to build.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown