Google Chrome 72 deprecates support for TLS 1.0, TLS 1.1
The update also completely removed support for HPKP.
Google Chrome 72 was released yesterday, just hours after the release of Firefox 65. And while Google has been pre-occupied with UI/UX changes over its previous few releases, this update focuses much more on security updates, tweaks to APIs and support for various protocols.
Obviously, we’re mostly interested in the SSL/TLS-related stuff, which is good because there are several big changes in store for Windows, Mac, Linux and Android users.
So, today we’ll discuss those changes and how you can harden your own personal security in conjunction with one of those updates.
Let’s hash it out.
Bye bye HPKP
HTTP-based Public Key Pinning (HPKP) is a practice that pins one or more of a website’s public keys in an HTTP header. It’s a great idea in theory as it helps defend against mis-issuance, but in practice it can be incredibly dangerous. Ok, that may be a bit hyperbolic, but HPKP is challening to use correctly because it’s difficult to build a set of pinned key that is guaranteed to work on account of the ever-evolving nature of the digital certificate industry and the variance in user trust stores.
As a result, HPKP can cause websites to break. It causes a lot of errors. And it can actually be weaponized, though there has never been a confirmed case of this happening.
Google had already announced it planned to deprecate HPKP, now support has been removed entirely in Chrome 72.
PKP offers a way to defend against certificate misissuance, by providing a Web-exposed mechanism (HPKP) for sites to limit the set of certificate authorities (CAs) that can issue for their domain. However, this exposes as part of the Open Web Platform considerations that are external to it: specifically, the choice and selection of CAs is a product-level security decision made by browsers or by OS vendors, and the choice and use of sub-CAs, cross-signing, and other aspects of the PKI hierarchy are made independently by CAs. As a consequence, site operators face difficulties selecting a reliable set of keys to pin to, and adoption of PKP has remained low. When site operators’ expectations don’t match the reality of trust anchors on real world client machines, users suffer. Unexpected or spurious pinning errors can result in error fatigue rather than user safety.
Chris Palmer, Security Engineer, Google
We’ve written about how HPKP was a failed concept before, and that’s backed up by the fact that neither Apple nor Microsoft support it anymore. Now Google has completely removed support in Chrome 72.
RIP HPKP.
Deprecating support for TLS 1.0 and TLS 1.1
At the end of last year, in a fairly unprecedented joint announcement, the major browser makers – Google, Apple, Microsoft & Mozilla – announced their decision to deprecate support for TLS 1.0 and TLS 1.1 in early 2020.
With the release of Chrome 72, Google is laying the foundation for that final deprecation. For now, traveling to sites that still only support TLS 1.0 or TLS 1.1 will simply show a warning in the Dev Tools. Starting with the release of Chrome 81 users won’t be able to connect with sites that have not upgraded to TLS 1.2.
This isn’t anything surprising, TLS 1.0 and TLS 1.1 are being widely deprecated as a result of known vulnerabilities. Last year PCI DSS dictated that any website that accepts payment cards needed to deprecate TLS 1.0 with a strong recommendation for removing TLS 1.1, too.
Unfortunately, despite the fact TLS 1.2 has been out for about ten years and we’ve now moved on to TLS 1.3, too many websites are still only supporting outmoded versions of the SSL and TLS protocols.
Here’s a breakdown of the Alexa top 100,000 by the highest protocol supported:
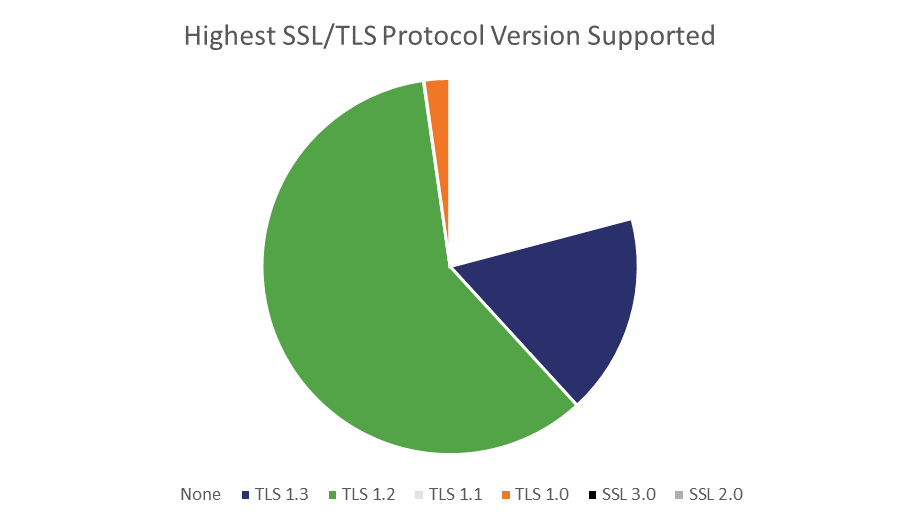
Oddly, there are more than 40 times as many sites whose highest level of support is TLS 1.0 than TLS 1.1. Overall though, that’s about 2.3% of the Alexa top 100,000 that will effectively be unreachable if they haven’t upgraded by Chrome 81.
If you’re running a website, now would be a good time to turn off server support for these older protocol versions, too. It’s great that you support newer, more secure versions of the protocol but continuing to support outmoded versions opens you up to downgrade attacks.
Disabling support for TLS 1.0 and TLS 1.1 in Google Chrome
As for regular Chrome users, now would be a good time for you to drop support for TLS 1.0 and TLS 1.1 on the browser side, too. One of the best ways to force the stragglers to upgrade their support is to stop visiting sites that don’t support TLS 1.2 or higher.
UPDATE: The correct way to adjust these settings for Microsoft users are in Windows’ native TLS stack, not Chrome. Chrome only picks up its proxy settings from there (h/t David Benjamin).
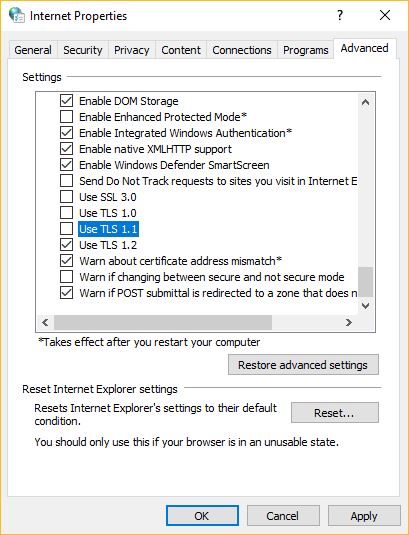
So, to do that, open your control panel and select Internet Options. Navigate to the Advanced Tab and then scroll down to the security settings and untoggle TLS 1.0 and TLS 1.1
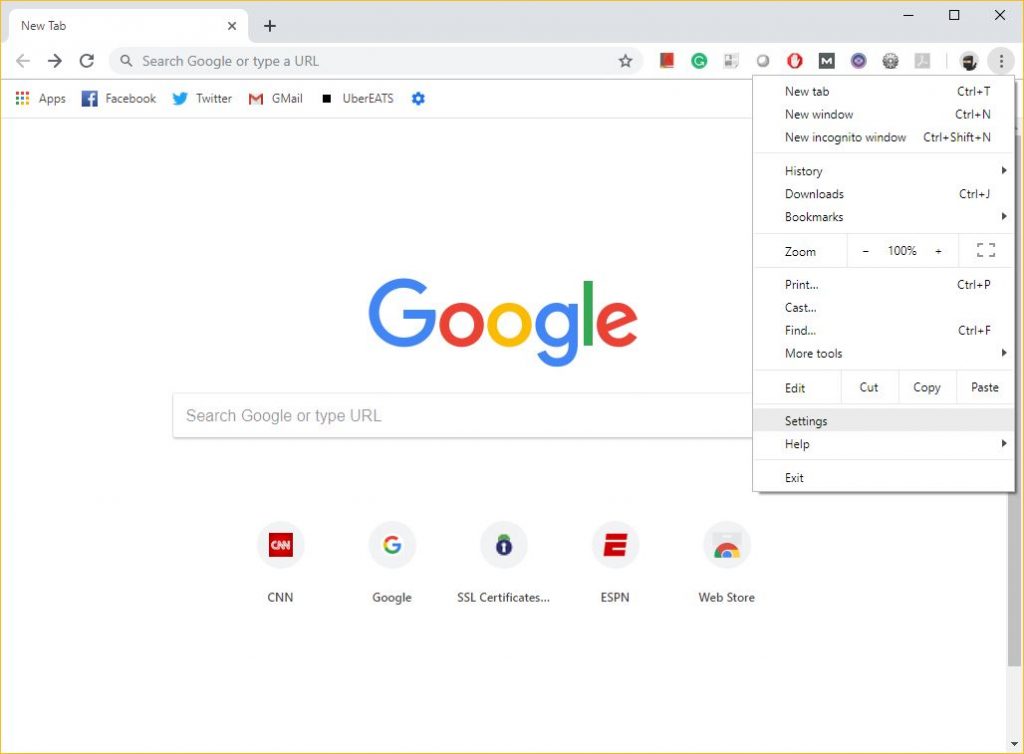
Here’s how to drop support for TLS 1.0 and TLS 1.1 through Chrome.
- Click the vertical ellipsis (three dots) in the upper right-hand corner of the browsers and select settings.
- Scroll down and click “Advanced.”
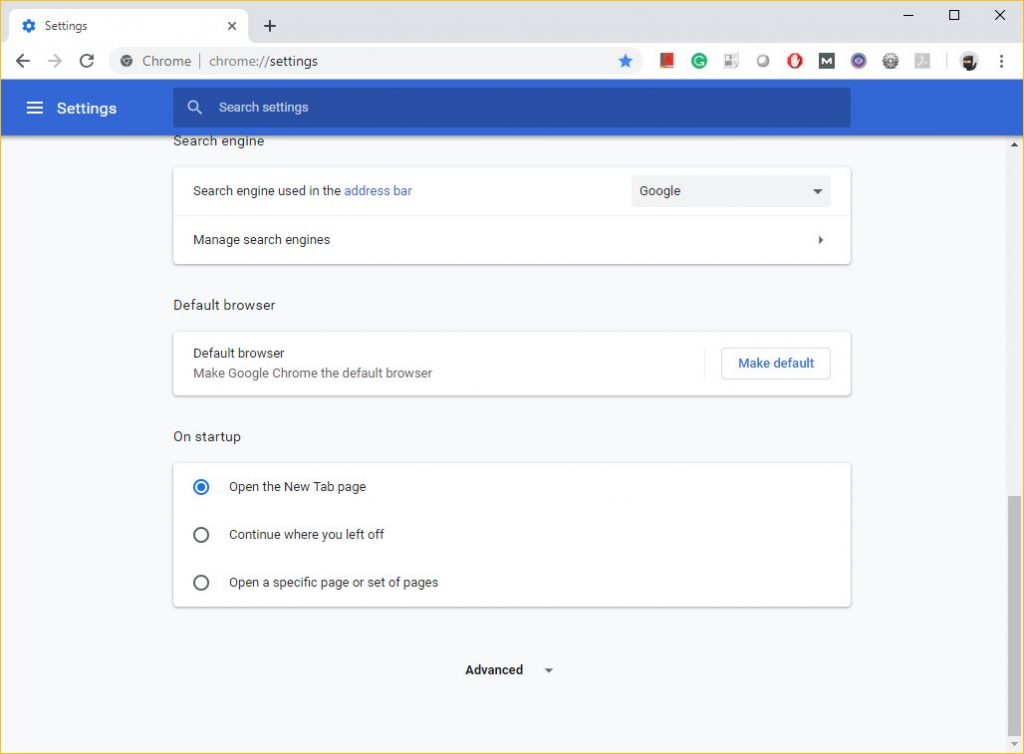
- Scroll down to the “System” section and click “Open proxy settings.”
- Click on the advanced tab and scroll down to security, de-select TLS 1.0 and TLS 1.1 (you should also have SSL 3.0 and SSL 2.0 disabled, too). Notice this is actually the Windows Internet Properties menu that you’re altering.

- Click OK.
I’ll admit, doing this could render some of the sites you visit regularly unreachable. You can always click through the warnings when that happens, just keep in mind that TLS 1.2 has been out for a decade now, which should give you an idea of how much the website you’re trying to visit prioritizes security.
At any rate, expect to see more updates like this to other browsers over the coming months.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown