Apple, Microsoft, Google Announce Plans to Disable TLS 1.0, TLS 1.1
The tech giants announced they will be dropping support for the outmoded TLS versions at the start of 2020.
Today Apple, Microsoft and Google announced their intentions to deprecate support for TLS 1.1 and TLS 1.0. This means that TLS 1.2 will effectively become the default, with websites and companies encouraged to add support for TLS 1.3 as soon as possible.
This was a coordinated announcement by the three tech giants and Mozilla. That means all of the major browsers – Apple Safari, Google Chrome, Mozilla Firefox and Microsoft Edge & Internet Explorer – will all be dropping support for TLS 1.1 and TLS 1.0 by early 2020.
![]() As you no doubt are aware, TLS was the successor to Secure Sockets Layer. We still use SSL colloquially because that’s what most people know it as, but since 1999 we have actually been using Transport Layer Security. The last vestiges of SSL, support for SSL 3.0, has been ill-advised for some time now with even the most slow moving of organizations having deprecated it because of known vulnerabilities.
As you no doubt are aware, TLS was the successor to Secure Sockets Layer. We still use SSL colloquially because that’s what most people know it as, but since 1999 we have actually been using Transport Layer Security. The last vestiges of SSL, support for SSL 3.0, has been ill-advised for some time now with even the most slow moving of organizations having deprecated it because of known vulnerabilities.
January 19 will mark the 20 year anniversary of TLS 1.0. We are now on TLS 1.3. For frame of reference, the payment card industry was mandated to deprecate support for TLS 1.0 earlier this year, while removing support for TLS 1.1 was strongly advised.So this isn’t coming from out of no where, it’s been a long time coming.
The reason that TLS 1.0 and TLS 1.1 are considered unsafe is that they make use of outdated algorithms and cryptosystems that have been found vulnerable, such as SHA-1 and MD5. They also lack modern features like perfect forward secrecy and are susceptible to downgrade attacks.
Apple, Google and Microsoft all stated that this will likely have a minimal impact as only a very time fraction of the connections made using the Safari, Chrome, Edge and Internet Explorer browsers are still being made with TLS 1.0 or TLS 1.1.
Here’s a table provided by Microsoft:
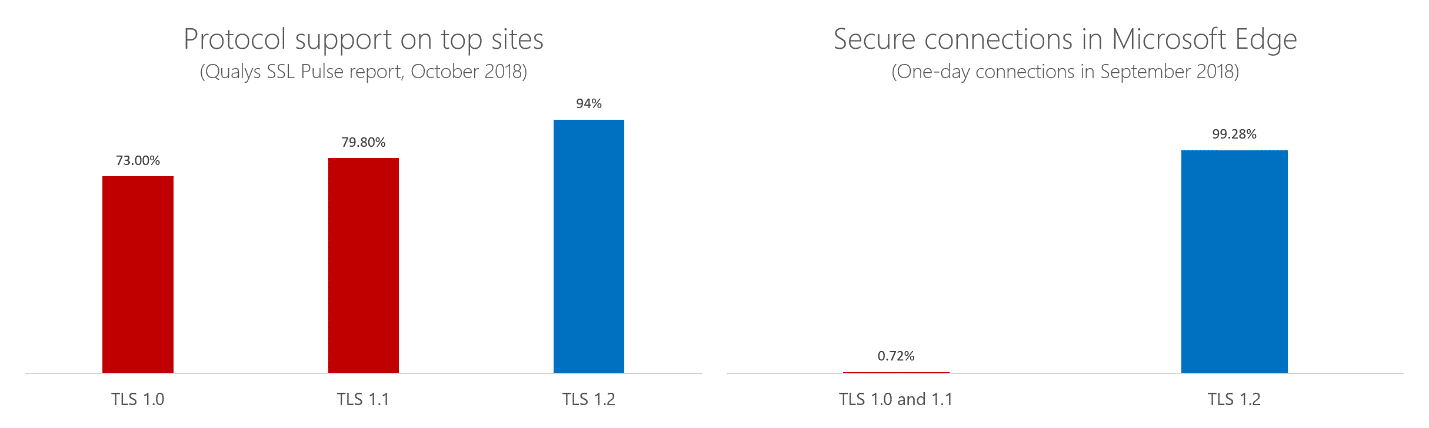
Here’s what Apple had to say about the decision:
Now is the time to make this transition. Properly configured for App Transport Security (ATS) compliance, TLS 1.2 offers security fit for the modern web. It is the standard on Apple platforms and represents 99.6% of TLS connections made from Safari. TLS 1.0 and 1.1 — which date back to 1999 — account for less than 0.36% of all connections. With the recent finalization of TLS 1.3 by the IETF in August 2018, the proportion of legacy TLS connections will likely drop even further. TLS 1.2 is also required for HTTP/2, which delivers significant performance improvements for the web.
Microsoft took a quick stroll down memory lane:
Two decades is a long time for a security technology to stand unmodified. While we aren’t aware of significant vulnerabilities with our up-to-date implementations of TLS 1.0 and TLS 1.1, vulnerable third-party implementations do exist. Moving to newer versions helps ensure a more secure Web for everyone. Additionally, we expect the IETF to formally deprecate TLS 1.0 and 1.1 later this year, at which point protocol vulnerabilities in these versions will no longer be addressed by the IETF.
And Google’s post was oozing with personality:
In line with these industry standards, Google Chrome will deprecate TLS 1.0 and TLS 1.1 in Chrome 72. Sites using these versions will begin to see deprecation warnings in the DevTools console in that release. TLS 1.0 and 1.1 will be disabled altogether in Chrome 81. This will affect users on early release channels starting January 2020.
What does this mean for you?
For the vast majority of businesses and organizations this is not going to be a problem. TLS 1.2 has been the standard for a while now (10 years) so it won’t be a matter of adding support for the new version so much as turning off support for the old ones. Because while the browser community is dropping support on their side, maintaining support for it server-side can leave you open to exploits like downgrade attacks.
Generally speaking your TLS implementations should:
- Support TLS 1.2 (and preferably TLS 1.3)
- Use EDCHE- and AEAD-based ciphers
(Google advises: “AEAD-based cipher suites are those using AES-GCM or ChaCha20-Poly1305. ECDHE_RSA_WITH_AES_128_GCM_SHA256 is the recommended option for most sites.”) - Use the SHA-2 hashing algorithm
You should be making every effort to move towards TLS 1.3, quite frankly. TLS 1.3 spent a long time up on the drawing board, but for good reason. It’s stripped away a number of algorithms and ciphers that were found vulnerable or may soon be while refining the handshake down to a single round trip.
RELATED: Examining the TLS 1.3 Handshake
The sooner you can ramp up and add support for TLS 1.3, the better. The browsers have already announced plans and/or started to support it. And it is more secure.
In the meantime, if you are still supporting TLS 1.0 and TLS 1.1 – Stop.
As always, leave any comments or questions below…







































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown