Google Search Console Reaffirms Upcoming HTTP Warning
A reminder that Chrome will eventually mark all HTTP pages as “not secure.”
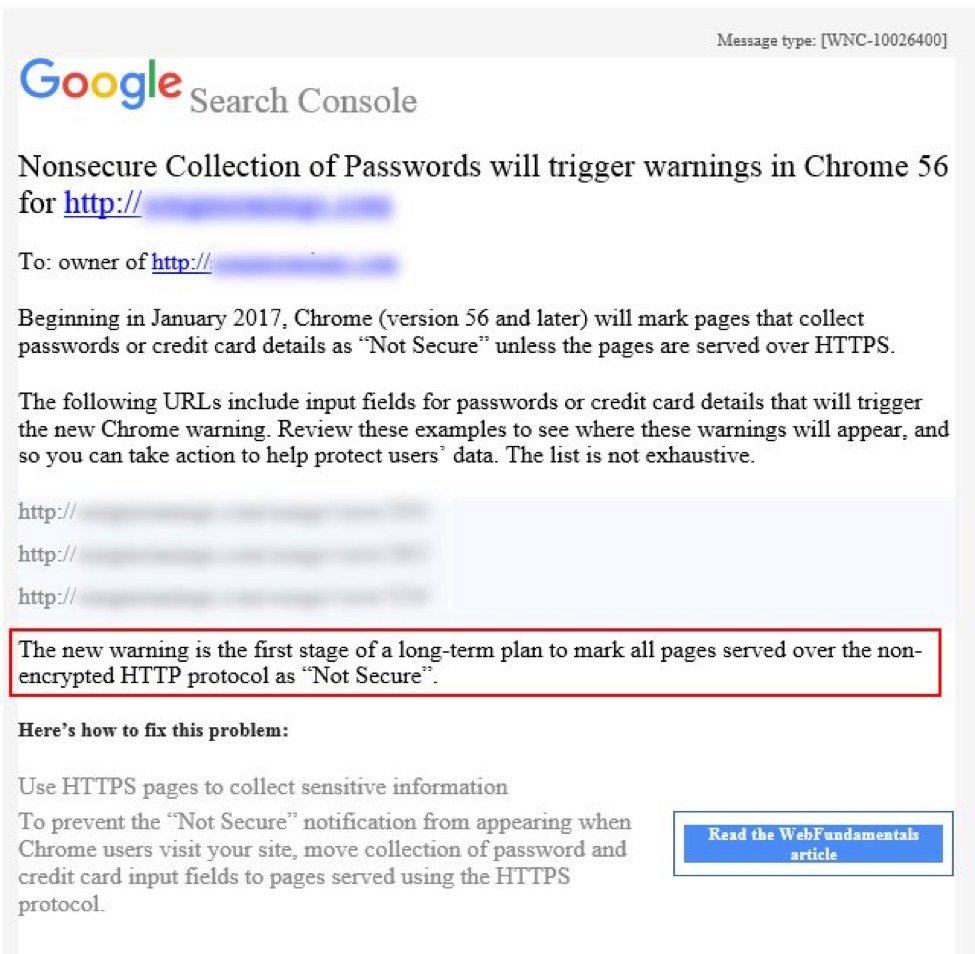
Google Search Console (formerly Webmaster Tools) has begun sending a new message to site owners about unsecured HTTP.
The message is a reminder that, with the release of Chrome 56 next month, all pages that collect passwords or credit cards over HTTP will be labeled “Not Secure.” This will appear in address bar and pages will also lose the green padlock icon.
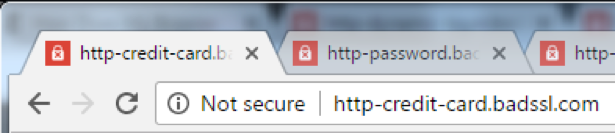
Also included in the message is a sneak peek of the future. Near the bottom, it says “the new warning is the first stage of a long-term plan to mark all pages served over the non-encrypted HTTP protocol as “Not Secure.”
For those who follow HTTPs news closely, you will know this is not a new announcement. Google published its plan more than a year ago.
Since then, Google has been working on improvements across the board: redesigning its security UI for improved user understanding, making it easier for sites to adopt the secure protocol, and waiting for HTTPS to become prevalent enough to make the switch without large-scale disruption.
But no one knows when the big change – the labeling of all HTTP pages as “Not Secure” – will happen. In Google’s original proposal they suggested benchmarks based on the percentage of pages loaded securely over HTTPS. Though it was noted this was only an example, and Google has not publicly committed to any specific criteria.
While we can’t say for sure, it’s likely more than a year until all HTTP traffic is marked ‘Not Secure’. Chrome already has one major plan for SSL in 2017 – mandatory participation in Certificate Transparency; and despite a major landmark for encrypted traffic in 2016, there is still a long way to go until the majority of the web is ready for HTTPS.
Note: Thanks to Glenn Gabe who shared the Google Search Console message on Twitter.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown