Sectigo to start issuing from new Roots on January 14th
The Comodo CA roots are out, USERTrust roots will replace them
Last month we were excited to share news that one of our biggest partners, Sectigo, was changing its name from Comodo CA. It was a much-needed move as Comodo Group, the company Sectigo split from, operates in the same space and had, more or less the same colors and logo.
Thus, Sectigo was born.
Now, in an announcement made today, Sectigo is entering the next phase of its transition: it’s swapping out the old Comodo CA roots come January 14, 2019.
So, today we’ll keep it short and we’ll discuss what Sectigo is doing and what it will mean to Sectigo customers moving forward.
Let’s hash it out.
 Let’s start by talking about Root CAs
Let’s start by talking about Root CAs
While we’re not going to go in-depth about Root CAs and Intermediates, it is worth just glossing over really quickly so the rest of this information will make a little more sense.
Every operating system maintains a Root store (sometimes called a trust store) that contains a set of root certificates that literally live on your system. These roots are incredibly valuable, because they can be used to issue trusted digital certificates like SSL/TLS certificates and signing certificates.
When you visit a website and your browser is presented with the site’s SSL/TLS certificate, your browser performs a series of checks to authenticate it. One of those checks involves tracing the signature on the leaf or end-user SSL/TLS certificate back to the certificate whose key signed it. If it can follow the certificate chain back to one of the roots in whatever trust store it’s using, it will trust the end-user certificate. If not, you get an error and the connection fails.
Now, once again, here’s the thing about Roots: they’re powerful, and valuable to the point of being dangerous. The various root programs (Mozilla’s, Apple’s, Microsoft’s, Google’s) are exceedingly stringent in their requirements before adding new roots. CAs must undergo audits, there are review processes and some of the folks running them are a bit… difficult.
But that’s for good reason, a Root CA can issue trusted certificates, so if it’s ever compromised it’s going to be a full-fledged disaster. This is an eventuality that everyone wants to guard against. It’s why CAs issue intermediate roots and sign certificates with those – adding an additional layer of protection – that way should it ever be necessary to revoke one you’re not losing the actual Root. It’s much easier to spin up an intermediate than a Root, as you’ll see in a moment.
One last thing, whereas publicly trusted leaf certificates have lifespans not exceeding 27 months, Roots can have lifespans of over 20 years.
Sectigo is changing its Root CAs and its Intermediates
Ok, now let’s talk about what’s going on with Sectigo and its decision to change roots on January 14th. As we just discussed, CAs typically don’t issue certificates directly off their roots. Instead they spin up intermediate roots and use those to sign.
Currently, this is what the certificate chain for Sectigo’s SSL/TLS certificate looks like:
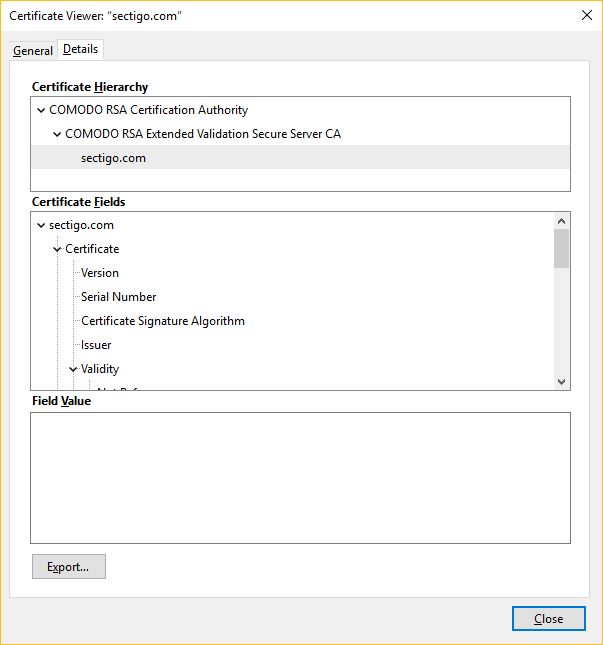
Up top you have the Comodo Root CA. Sectigo.com uses an Extended Validation certificate, so you can also see that the EV intermediate was used to sign the Sectigo leaf EV certificate.
Obviously, Sectigo is trying to get away from the Comodo branding, so having Roots and Intermediates that say “Comodo” is not desirable.
Personally, I had wondered how Sectigo was going to handle this transition from a PKI standpoint given the time it takes (and the rigor involved with) getting a root accepted into the various root programs. Not to mention the fact I keep pretty close tabs on what’s happening with the Mozilla root program and hadn’t seen anything to indicate an attempt had even been made.
Well, now we know. And the answer involves going back to the past to help sort out the future. Sectigo will begin using its USERTrust Root CAs as opposed to the Comodo Root CAs it had previously been chaining from. The USERTrust root is not new, the first of its ilk was actually created back in 2000 and expires on May 30, 2020. Newer versions have been generated since 2010 with lifespans pushed out as far as 2038. So the USERTrust Root CAs aren’t new, it’s just they don’t have “Comodo” in their name.
Using the USERTrust Root CAs, Sectigo will spin up its own branded intermediates so that its certificate chain will reflect its new branding, instead of being a holdover from a previous iteration of the company.
This move will prove doubly useful for Sectigo, too. Not only will it be able to apply its new branding to its intermediates and remove all semblance of Comodo from its certificate chains, but this also gives Sectigo more time to get its dedicated roots into the various root programs. I would imagine eventually the end goal is to have actual Sectigo Root CA certificates, but that obviously doesn’t happen overnight. So, swap roots, spin up new intermediates and take your time on getting the Root CAs accepted.
Makes sense.
What does this mean for existing Sectigo customers?
Much like when the Certificate Transparency requirement went into place, this is really something that’s only going to affect the Certificate Authority side of things.
As Sectigo said in its statement:
We want to assure all customers and partners that this change will happen seamlessly with no action needed. Your existing certificates, issuing CAs, and roots will remain active and trusted. The new Sectigo intermediates will be used to fulfill new requests, renewal requests, and requests that are pending at the time of this transition. Reissuance requests that are handled directly by Sectigo will be fulfilled using the same issuing CA that issued your original certificate.
Ok, so let’s just run through a few things specifically:
- All Sectigo-issued certificates will continue to be trusted globally
- No action is required from customers, no need to re-issue or replace certificates until expiration
- All current Comodo CA and Sectigo certificates issued off the old roots will continue to work until expiry
- Finally, if you have a branded issuing CA, nothing will change with that
These changes are set to take effect on January 14, 2019. We will let you know if anything changes between now and then…
As always, leave any comments or questions






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown