What Is a Rootkit and How Does It Work?
Here’s everything you need to know about the most dangerous breed of security threats
The cyber security industry might not have perfected the techniques to thwart security threats completely, but it has definitely mastered the art of naming security threats. Names like trojans, worms, viruses, malware, ransomware are a testament to this. But today, we’re going to talk about another threat that might not have as original a name as others but definitely trumps all of them when it comes to destroying your privacy and security: rootkits.
What is a rootkit and what does it mean for you in terms of data security and privacy?
Today, we’re going to explore this pernicious threat — one that might be lurking on your computer right now.
Let’s hash it out.
What Is a Rootkit? Something Difficult to Detect and Impossible to Ignore
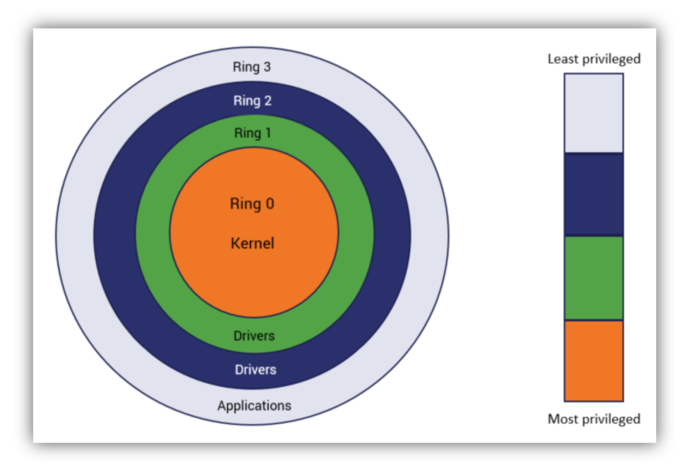
If you find yourself wondering “what is a rootkit,” we’ve got your answer. A rootkit is a collection of programs/software tools — typically malicious — that gives a threat actor remote administrative access to and control over a computer while hiding its presence on that machine. In simpler words, a rootkit is typically associated with malware that you can’t see but make sure that the cyber-criminal sees your computer and, possibly, your actions as well.
It’s like an enemy country’s secret agent who infiltrates your computer to provide continuous privilege access while masking their identity — all without you knowing it. And it can potentially remain hidden for years if undetected.
As you can see, the term “rootkit” has been derived from two words: “root” and “kit.” The term root is the traditional name of the most privileged administrator-level access in a UNIX system. In UNIX, root access gives a user full rights to control and change almost everything. The word “kit,” on the other hand, refers to the group of software applications that form the tool.
The thing that makes rootkit so unique is that it remains hidden inside your system and is designed to keep malware detection applications and other security tools at bay. Most antivirus and anti-malware applications are unable to distinguish rootkits from other software your system trusts because it piggybacks on those trusted applications.
What Can a Rootkit Do?
A more appropriate question is be “What can’t a rootkit do?” The reason why a rootkit is regarded as being so dangerous is that it can do almost everything to your privacy and security you’re afraid of. A rootkit can contain malicious tools that allow cybercriminals to:
- track everything you type on your computer.
- steal your usernames, passwords, and credit card information.
- disable the security applications you might have installed on your computer.
- alter other sensitive settings and programs in your system.
What Is a Rootkit? 7 Different Types of Rootkits
Depending upon its location in the hierarchical protection domains or protection rings, we can classify rootkits into at least seven types. These types range from the lowest privilege level to the kernel-mode (highest privileges).
User Mode Rootkits
In terms of user privileges, these rootkits rank the lowest. User mode rootkits, sometimes referred to as application rootkits, start as a program during system start-up, or they’re injected into the system. These rootkits — depending upon the operating system — operate through various ways to intercept and modify the standard behavior of application programming interfaces (APIs). For example, this could be a .DLL file in Windows and a .dylib file in Mac OS X. These rootkits are quite popular in financial and banking malware. One such piece of malware, named Carberp, was based on this technique, and its user mode rootkit component has been used in many financial malware families.
Hardware/Firmware Rootkits
As the name suggests, this type of rootkit is intended to infect hardware or firmware such as hard drives, routers, network cards, and even your system’s basic input operating software (BIOS). These rootkits can seize the data written on the disk or data transmitting through a router.
Bootloader Rootkits
Sometimes called a bootkit, a bootloader is a program/code that runs as soon as you turn your computer on and the operating system starts to load. If your computer has been infected with a bootloader rootkit, it could replace the original bootloader.
Memory Rootkits
Much like the name suggests, these rootkits usually hide inside the computer’s RAM (random access memory). The lifespan of these kits is quite short, and most of them disappear once the system reboots.
Kernel Mode Rootkits
Kernel mode rootkits target the innermost circle of the protection ring, and that’s why they’re the most dangerous. They infect the core of the operating system by adding or replacing portions of it, which allows them to conceal malware. These rootkits have unrestricted access and can modify data structures, making them exceedingly difficult to detect.
How to Detect and Remove Rootkits
Unlike other security threats, the detection of rootkits is quite tricky since they disguise themselves. However, there are tools provided by anti-malware providers to scan and detect rootkits. Unfortunately, many of them can’t detect all varieties of rootkits — especially if a given rootkit has infected the kernel — so one method of detection is to use scanners or solutions from multiple vendors.
Other methods of rootkit detection are quite complicated and expensive for organizations. These methods can include behaviour-based detection methods, signature scanning, and firewall and event log analysis. For consumers, these solutions aren’t of much use — reinstalling the operating system (OS) might be the only solution out for these types of users.
Best Practices to Protect Your Endpoint Devices from Rootkits
There’s not much you can do once your computer has been infected with a rootkit. However, you can stop them from entering into your computer in the first place. Here are the best practices to keep your computer safe from sinister rootkits:
Only Download Computer Drivers from Authorized Sources
One of the most common routes a rootkit enters is through drivers that disguise themselves as original drivers. Therefore, you should always insist on installing drivers from authorized sources only. Here’s a post that will help you determine whether the website is fake or genuine.
Always Check an Email Thoroughly Before Engaging with It or Any Attachments
Spoofy emails are one of the favorite weapons in the arsenal of cybercriminals. That’s because they don’t have to do much apart from sending you an email. You do the rest while they have their piña colada. Phishing emails often lead users to download something, and often, rootkits come as a part of the package.
There are many types of phishing emails out there:
- some claim to be official emails from companies;
- some appear to be sent from someone you know;
- some give you a lucrative offer that you can’t (or don’t want to) refuse; and
- some give you some sort of warning to do something within a certain period.
You should always check the email header information and sender’s email address before clicking or downloading something sent via email. Here are some examples of phishing emails that will give you a better idea of how phishing emails look.
Maintain an Up to Date OS, Browser and Security Software
Let’s face it; nobody wants to see the update pop up whenever we start a computer. As annoying as updates are, they exist for a reason — many reasons, in fact. Keeping your system, browser, and security software up to date is one of the most effective ways to protect against rootkits.
Be Careful About What You Download (and Whom You Give Access to Do So)
As much as we love downloading (illegally) the just-released episodes of our favorite TV shows, we should be extremely vigilant about downloading anything from the internet. Most of the time, rootkits come as a part of the package, and there’s no way you can sniff them out. That’s why the best strategy is to only download/buy digital products from official sources.
For organizations, another recommendation is to implement a policy of least privilege. This entails only giving the ability to download or install programs to users who need it for their jobs or to perform specific functions.
A Final Word
Rootkits aren’t much different from other threats when it comes to getting inside a computer system. However, they’re entirely different once they infect the system. Removing them from your system is a mightily difficult task, and you don’t want to find yourself in a position of needing to do so. That’s why it’s always a wise choice to stay vigilant when browsing on the internet and engaging with emails. We hope this answers your questions on the topic of “what is a rootkit?”





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown