WordPress GDPR Compliance Plugin: Critical vulnerability, update immediately
Over 100,000 WordPress websites are potentially vulnerable to a major exploit
Since the end of May, GDPR compliance has been a key consideration for any company or organization with a footprint in Europe. In the leadup to the GDPR enforcement date, May 25, multitudes of GDPR compliance products and services have hit the market. And while many are well-intentioned, sometimes they can cause unforeseen problems of their own. Case in point: a WordPress GDPR Compliance Plugin was recently found to be vulnerable to a pair of exploits that could give an attacker control of the website.
In a report made last Thursday, WordFence, the company behind a popular WordPress security plugin, outlined a privilege escalation flaw in the WordPress GDPR Compliance Plugin that could endanger over 100,000 websites.
After its removal from the WordPress plugin repository yesterday, the popular plugin WP GDPR Compliance released version 1.4.3, an update which patched multiple critical vulnerabilities. At the time of this writing, the plugin has been reinstated in the WordPress repository and has over 100,000 active installs. The reported vulnerabilities allow unauthenticated attackers to achieve privilege escalation, allowing them to further infect vulnerable sites. Any sites making use of this plugin should make it an immediate priority to update to the latest version, or deactivate and remove it if updates are not possible.
So, given that we’ve spent more than a little time covering GDPR compliance, today we’re going to go over what the WordPress GDPR Compliance Plugin is, what it’s vulnerable to and what you need to do if you’re using it.
Let’s Hash it Out…
What is the WordPress GDPR Compliance Plugin?
The WordPress GDPR Compliance Plugin is designed to assist websites and organizations with European privacy regulations. Designed by Van Ons, it’s essentially a suite of features, like support for Contact Forms, Gravity Forms, WooCommerce and WordPress comments.
WP GDPR Compliance helps you as a site owner take care of:
– Keeping a consent log for supported plugins.
– Adding checkboxes to supported plugins for explicit visitor consent.
– ‘Right to access’ through encrypted audit logs.
– ‘Right to be forgotten’ by anonymising [sic] user data.
As we covered last week, one of the benefits of a CMS like WordPress is the ability to use plugins, which save site owners time and resources that would otherwise need to be spent developing web applications and additional functionality to their websites. The downside is that sometimes these plugins, which are designed by third parties, can cause unforeseen complications – like disabling certificate authentication.
That’s what’s happening in the case of the WordPress GDPR Compliance plugin.
What are the WordPress GDPR Compliance plugin’s critical vulnerabilities?
There are two. And these have been spotted in the wild, meaning that they have already been exploited. While WordFence says it hasn’t seen any “final payloads,” clearly there is an imminent threat posed by these vulnerabilities.
The first is a bit simpler, and more common:
Administrator Access via Modified Settings
Distilled to its simplest, this attack lets an attacker create a new user, give it admin privileges and then change the settings it just exploited to create the new user – as a way to prevent the attack vector from being exploited again.
Here’s an example of the log entries from one attack:
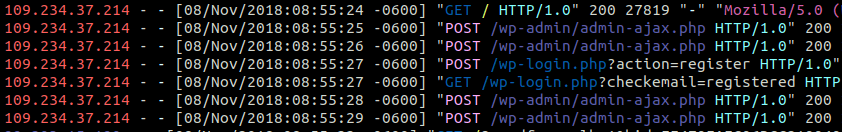
While we’re not going to go line-by-line, you can see where the attacker is able to enable the “users_can_register” option, create a new account, and then disable the registration option, effectively shutting the window behind them.
WordFence has seen the attackers installing a PHP webshell, that can allow for remote access. From there, the attacker has carte blanche to upload any additional malicious payloads it wants to.
Backdoor Installation via Injected Cron
The second exploit is a bit more involved, but provides the attacker with a persistent backdoor that can be replaced if it’s found and removed. The attack works by injecting malicious actions into a website’s WP-Cron schedule. This exploits a technology that allows a website to run scheduled tasks like checking for updates or pushing live new content.
This exploit takes advantage of part of WooCommerce’s functionality:
..to install the 2MB Autocode plugin, which allows the injection of arbitrary PHP code into all posts on a site. The code to be injected is stored by 2MB Autocode as an option in the database…
That setting is then modified with a PHP backdoor script that downloads a response from the attacker’s server and saves it as wp-cache.php, before covering its tracks. This makes it difficult to detect, but results in persistent backdoor access to the site.
While the backdoor script seen in these cases shares the name wp-cache.php with other methods, the contents are much different. Instead of a self-contained web shell, this script contains some decoding functions and some execution syntax, but none of the executed payload is stored in the file. Instead, the payload to be decoded and executed is stored as a POST variable or in a cookie.
Again, WordFence doesn’t know what the intent is behind this attack is. It knows the means, it just hasn’t ascertained the ends yet. Still, there’s no shortage of potential dangers having admin permissions and remote access to a website can cause.
How would I know if I’m in trouble?
WordFence has provided the following indicators of compromise:
Prevalent IP Addresses
Admin Creation
- 234.39.250
- 234.37.214
 Cron Injection
Cron Injection
- 39.65.176
- 123.213.91
Attacker Domain Accessed: pornman.com
Malware Hashes
Admin Creation
- MD5: b6eba59622630b18235ba2d0ce4fcb65
- SHA1: 577293e035cce3083f2fc68f684e014bf100faf3
Cron Injection
- MD5: c62180f0d626d92e29e83778605dd8be
- SHA1: 83d9688605a948943b05df5c548bea6e1a7fe8da
Installed Plugins: 2MB Autocode (if you aren’t using it intentionally)
RELATED: Pro Tip: Don’t look at porn at work – especially if you work for the government
What do I need to do if I’m using WordPress GDPR Compliance Plugin?
Update immediately. Following the WordFence report the plugin was temporarily pulled offline, it has since been patched and the updated version is once again available. If you plan to continue using the WordPress GDPR Compliance plugin, update it now. Like, right now. Push the pause button on whatever you’ve got blaring through your headphones, open a new window and go fix this problem immediately.
You cannot afford to leave an attack vector this dangerous open.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown