4 Takeaways from DigiCert’s 2021 PKI Automation Study
What are the top PKI challenges organizations are facing in 2021, and how are they tackling them? Data from DigiCert’s 2021 State of PKI Automation unveils several important trends.
A whopping 91% of enterprises say they want to automate their public key infrastructure (PKI), according to data from DigiCert’s latest research report. And there’s a good reason for that — public key infrastructure is the backbone that supports virtually everything relating to internet security. If even one website security certificate expires on your server, all hell can break loose regarding service outages, security risks, and non-compliance issues. Not to mention all of the penalties and potential lawsuits those issues can bring…
When it comes down to it, PKI is a beast for enterprises and other large-scale environments if it’s not properly managed. This is where PKI automation can help. PKI automation helps to bring order to that chaos.
But what does PKI automation entail? We’ll quickly review what it is and why it’s necessary. Then we’ll move on to cover four key takeaways for enterprises from DigiCert’s latest PKI automation report. In each section, we’ll explore insights and statistics as well as useful recommendations for dealing with each situation.
Let’s hash it out.
A Quick Overview of the Advantages of PKI Automation
PKI automation is the processes and tools relating to managing PKI certificates’ and keys’ lifecycles. Basically, it’s all about taking the monotonous tasks associated with managing your digital certificates and keypairs — everything from requesting or renewing your certificates to deploying and revoking them (and everything in between) — and freeing up your team to focus on higher-level functions.
So, what happens if you don’t have strong PKI management practices and tools in place? If even just one of those certificates expires or keys becomes compromised, you’ll be in for a world of hurt for a range of reasons! For example, let’s consider what can happen when an SSL certificate expires:
- Insecure data can lead to costly and devastating data breaches.
- Non-compliance issues can lead to massive penalties and potential lawsuits.
- Service outages not only decrease productivity and also interfere with your customers.
- Reputation damage can deliver a devastating blow that could have lasting effects you can feel for months or years to come.
- Loss of customer trust and relationships could lead to sales and revenue losses that might force you to close your doors permanently.
By using automation to manage your certificates and keys, you reduce the likelihood of these scenarios occurring by making yourself a tougher target for attackers.
So, now that we know what PKI automation is and why it’s beneficial for enterprises, let’s time to look at the big takeaways from DigiCert’s survey data.
Takeaway #1: Experienced Certificate-Related Downtime? You’re Not Alone
Unexpected downtime is like a heart attack for businesses. It strikes suddenly — often without any warning — and can have devastating effects in terms of revenue losses and reputational damage.
To avoid a heart attack, you need to take steps to ensure that you’re living a healthy life: exercise regularly, drink plenty of water, eat a generally healthy diet, etc. Likewise, there are things you can do to reduce unexpected downtime relating to your public key infrastructure. (We’ll cover those recommendations momentarily.)
DigiCert’s State of PKI Automation report data shows that more than 33% of PKI leaders believe that automation is integral to that responsibility. These organizations, which are generally kicking butt and taking names when it comes to managing their PKIs, are significantly less likely to experience outages than other organizations that are PKI “laggards.”
In general, DigiCert’s data shows that two-thirds or organizations experience outages due to certificates expiring unexpectedly. However, the organizations they recognize as PKI leaders experienced far fewer of these expiration-related outages — only one outage in six months. (Compare this to the three to five outages that their less-concerned enterprise counterparts experienced — more on both types of organizations momentarily.)
What You Can Do to Mitigate This Issue
Downtime happens to virtually everyone at one point or another — the difference is whether the downtime is intentional (planned ahead of time) or unintentional (i.e., “oops!”). But what can you do to reduce unexpected downtime and its related costs?
- Schedule downtime for necessary updates — This is the first critical step to avoiding any type of downtime in general. If you know that you need to apply updates, for example, you can plan for that ahead of time so your customers are aware and can plan accordingly. This courteous move helps your customers minimize their downtime as well because they know about it in advance.
- Set up certificate discovery — Certificate discovery is a crucial took for PKI management as well as network security in general. If you don’t know what is on your network, how can you protect it? Certificate discovery should apply both to your public (external) and internal networks.
- Enable certificate automation — Use automation to your advantage and set your certificate renewals to occur automatically whenever possible. This will make certificate management a breeze and will take many monotonous, renewal-related tasks off your plate.
- Set up PKI alerts — Many PKI management-related tools offer the ability to set up alerts. This notification system informs you when things are going sideways so you can escalate anything right away to ensure it’s taken care of quickly and efficiently.
Takeaway #2: Overly Confident Organizations Tend to Have the Biggest Issues

The organizations that worry the most about PKI certificate management tend to be the ones that have the fewest PKI security issues. (Note: This takeaway is also in line with research we previously shared in an article on a 2020 study by Keyfactor and the Ponemon Institute.)
In general, these worriers seem to be two or three times better at handling many security-related tasks:
- Managing their PKI digital certificates,
- Minimizing downtime and PKI-related security risks (such as rogue certificates),
- Staying compliant with industry and regional data security laws and regulations.
It makes sense, really. There are several key reasons why these A-game organizations likely do better in these areas:
- Their employees are more aware, so they tend to keep a closer eye on things.
- They recognize the importance of efficient certificate management and automation.
- They recognize their organizations’ shortcomings — as such, they tend to take steps to mitigate the issues as early as possible.
Needless to say, it’s for this reason DigiCert recognizes these organizations as the PKI “leaders.”
Now, let’s compare this to their more overly confident counterparts — the organizations DigiCert recognizes as the “laggards.” These are the enterprises that express fewer concerns about their PKI security effectiveness and processes. In general, organizations that are less aware of their shortcomings tend to have more rogue certificate issues and service outages. I guess it’s true about that popular saying: ignorance is bliss.
What You Can Do to Mitigate This Issue
There are several key recommendations that we can make. Of course, not every recommendation may apply to you but may apply to someone else in your organization (based on your role):
- Pay attention to the needs of your business and talk to people. How can you make informed decisions if you don’t know what’s happening? You can’t address issues if you’re not in touch with what’s happening within your organization.
- Use the right tools that increase efficiency without sacrificing security. Use tools that give you greater visibility of your network and greater IT environment as a whole. PKI discovery and monitoring helps you be aware of PKI-related issues before they happen (like certificate expirations). Ideally, you’ll want to use a tool that enables PKI automation of PKI-related processes such as certificate renewals to also nip these issues in the bud.
- Implement strong PKI policies and procedures. No company is perfect — and neither are your employees. People can be lazy and sometimes make mistakes. This is why it’s a good idea to have documented resources in place that they can rely on to ensure they check all the boxes to ensure your PKI is managed as safely and securely as possible.
- Be forthright no matter how bad the truth may be. Don’t put lipstick on the pig — if something is wrong, you need to address it right away. Don’t sugar-coat bad situations that can lead to security events, data breaches, and non-compliance. Convey the seriousness of the situation and ask for the tools and resources you need to keep your organization and its data secure.
- Listen to what your employees have to say. Although not everyone wants to hear bad news, it’s better to face it head-on than deal with the consequences of a breach after the fact. Be open to what your PKI managers, IT team and CISO have to say when they share concerns and make suggestions. Taking this open-minded approach may help you avoid becoming the next certificate outage-related headline.
Takeaway #3: Enterprises Don’t Have the Capacity to Manually Manage PKIs

Manually managing the public key infrastructure at scale within some largescale environments simply isn’t feasible. Why? Because managing your PKI equates to being a full-time job for multiple people. DigiCert’s survey data shows:
- 61% of surveyed enterprises worry about the time requirements of certificate management.
- The number of PKI certificates that enterprises need to manage increased by 43%.
- Enterprises typically manage more than 50,000 certificates within their environments!
Based on this number, it means you’d have to track and manage an average of nearly 137 certificates per day. Needless to say, that’s a recipe for disaster that worsens when you also consider the management of the cryptographic keys that accompany each digital certificate…
- Data from a 2020 Keyfactor report shows that organizations say they have upwards of 88,750 certificates and keys within their environments. (That’s an average of 243 certificates and keys per day that you and/or your team would have to manage.)
- Another Keyfactor report indicates that more than half (53%) of respondents say they have no clue how many of these assets they have. (This estimate includes self-signed certificates as well.)
Why You Need to Have PKI Management Practices Early On
DigiCert’s 2021 report data shows that as organizations grow, their struggles to manage certificates (and their PKI workloads overall) grow with them:
- Two in three enterprises have experienced outages due to expired certificates.
- 25% reported having up to six PKI-related outages in the previous six months.
That’s a lot of outages to have in such a relatively brief period. For obvious reasons, this can have a devastating effect on your brand.
Let’s compare this to going to eat at your favorite restaurant. How would you feel if the restaurant’s staff frequently screw up your order and provide poor service frequently when you visit? It would be a horrible experience for you and would likely ruin your trust and faith in that brand. Needless to say, that restaurant wouldn’t remain your favorite for long…
What You Can Do to Mitigate This Issue
Using a certificate management platform that offers certificate automation is a great way to handle many of the issues you’ll face in terms of improving security. Heck, certificate automation is even a recommendation by the National Cybersecurity Center of Excellence (NCCoE). The Center is the collaborative “brain trust” at the National Institute of Standards and Technology (NIST) that consists of respected public, private and academic entities.
In the NIST special publication “Securing Web Transactions: TLS Server Certificate Management” (SP 1800-16), they recognize certificate automation as a way to “prevent, detect and recover from certificate-related incidents.” Moreover:
“Automation should be used wherever possible for the enrollment, installation, monitoring, and replacement of certificates, or justification should be provided for continuing to use manual methods that may cause operational security risks.”
In addition to decreasing cyber security risks, PKI automation also helps you streamline processes to increase efficiency and free up your employees to work on other critical tasks.
Of course, the PKI needs within an environment vary from one organization to the next. The determining factors largely depend on the size of the organization and the number of certificates and keys it requires. But regardless of your size, in many cases, using a PKI management tool is a great way to address the issues you face in managing certificates and frees up your team to work on other critical tasks.
Takeaway #4: Rogue Certificates Are the Biggest Concern for PKI Leaders
Rogue certificates, much like shadow IT, are a concern for every business. This term describes unauthorized or otherwise unknown PKI digital certificates that exist within your network or IT infrastructure. It’s very similar to the concept of shadow IT, which describes applications, devices, and other unauthorized or unknown elements that increase your organization’s attack surface. In other words, rogue certificates serve are weaknesses within your organization’s cyber defenses.
It’s virtually impossible to defend your fortress if someone is creating openings in the walls without your knowledge. Rogue certificates are certificates within your IT environment that you either don’t know about or aren’t tracking. But rogue certificates aren’t a small concern; for PKI leaders, it’s their leading concern — ranking ahead of other lurking concerns such as post-quantum computing readiness and shrinking certificate validity periods. And what makes matters worse is that:
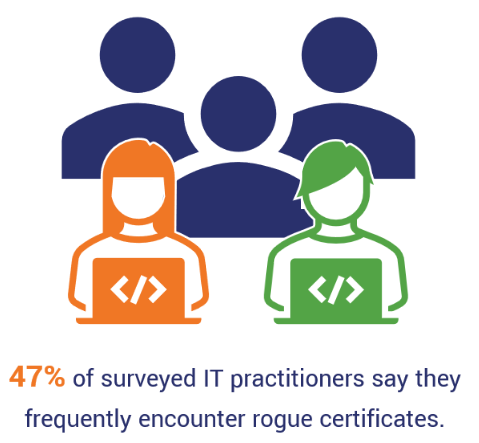
- Nearly half (47%) of surveyed enterprise IT practitioners report encountering rogue certificates frequently within their organizations.
- Surveyed enterprises reported having as many as 1,200 unmanaged certificates within their environments.
What You Can Do to Mitigate This Issue
There are two primary things you can do to mitigate issues of rogue and mismanaged certificates: create documented resources and use the right tools.
Create PKI Security Policies & Procedural Guidelines
The first option is to create procedural documents that help you cross your t’s and dot your i’s. These policies and procedural records should provide guidance on:
- Why and for what uses PKI certificates should be created or purchased,
- Who is responsible for managing public and private PKI certificates (and their corresponding key pairs),
- What the processes are for creating, managing, and destroying certificates and keys,
- Create workflows for staff to request and get certificatest that you ultimately control (i.e., within your certificate management platform), and
- Which public CAs are approved for issuing certificates for your organization.
Use a PKI Management Tool
The second recommendation is to use a certificate management tool that gives you complete visibility of your network. The purpose of this type of platform is to help you answer important questions like:
- What certificates do I have in use on my network, website, or elsewhere in my organization’s IT environment?
- Where and how is each of these certificates being used?
- When do they expire?
- Who is responsible for tracking and managing each certificate?
Ideally, this tool should offer PKI automation that helps your organization’s public key infrastructure capabilities and support scale with your business to encourage — rather than hinder — its growth.
A Look at Who and What DigiCert’s PKI Automation Study Surveyed
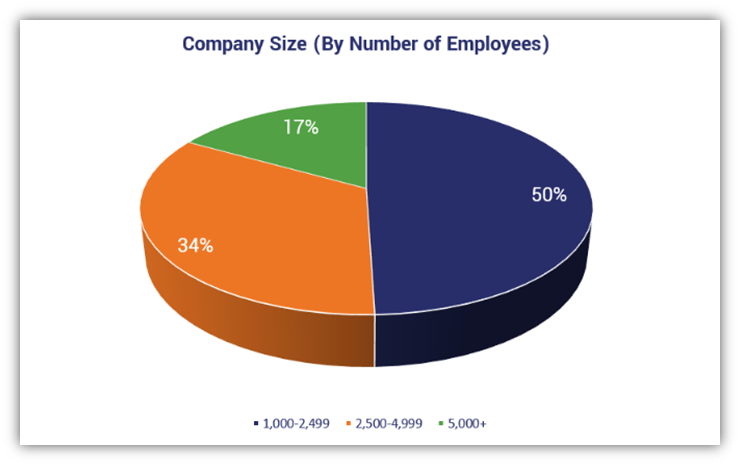
DigiCert’s report data is the result of a survey of IT professionals at 400 enterprises with 1,000+ employees. The research, which surveyed employees across North America, Latin America, EMEA and Asia Pacific, was carried out by ReRez Research of Dallas, Texas.
The surveyed practitioners include the following IT experts within these organizations:
- IT generalists,
- IT security managers, and
- IT directors.
Final Takeaways on PKI Automation for Enterprises
DigiCert’s study data shows that the most successful enterprises in terms of PKI security are those that recognize and embrace the value of practicing strong certificate management. These are generally the larger, high-PKI certificate volume organizations that have tens of thousands (or more than 100,000 certificates) of certificates to manage.
In addition to wanting to avoid unexpected certificate expirations, they’re also more focused on minimizing time spent managing certificates. It’s likely for this reason that these PKI leaders are six times more likely to have already implemented PKI automation within their organizations.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown