Britney Spear-Phishing: Malware, Instagram and Russia
A group of Russian hackers has used Britney Spears’ Instagram account to come up with an ingenious malware scheme.
The comments section of Britney Spears’ Instagram account was used by a Russian hacking operation in an ingenious malware scheme.
Now, a few things to get out of the way right off the bat. First of all, this isn’t actually a phishing attack, it’s a malware scheme. But the pun was just too good to pass up. So, just this once let’s sacrifice accuracy in the name of a good joke (or a bad joke, depending on your sensibilities).
And don’t worry, I won’t lace this article with bad puns playing on popular Britney Spears song titles. That would be Crazy. Ok, sorry, I’ll just do it that once. Any more would be Toxic. Oops… I did it again. Damnit! That last one wasn’t on purpose. I swear. I hope you won’t Hold it Against Me.
Ok, I’m really done this time.
Anyway, here’s how this crazy Britney Spears Instagram malware scheme works:
Turla, a hacking group thought to be associated with Russian intelligence, was found to be distributing malware and using Instagram as part of their attack. In order to hide the location of their server, which was being used to control infected machines, they posted an encoded message to Britney Spears’ Instagram account that appeared to be nothing more than the feelings of an enthusiastic fan.
There is a long path before we get to Britney. First, Turla needs to compromise a website. In this incident, it was an unnamed Swiss security company. With that done, Turla can now modify the code on that site. The second thing they do is begin distributing a malicious Firefox extension through the compromised site. The advantage of compromising an existing site with a user base is that they can leverage that trust to convince visitors it’s okay to install the extension.
Once that malicious extension is installed, Turla has successfully compromised the machine. This is where Britney Spears’ Instagram comes into play.
When hackers have infected a computer, depending on their goals, they may want to retrieve data from, and send commands to that computer. This is done with a command and control (C&C) server – set up specifically by the hackers to manage the devices they have infected.
It is vital that the C&C server remain hidden and operational. Hackers and researchers are in a constant cat-and-mouse game to take down C&C servers and get new ones online in order to keep control of compromised computers.
To hide the location of their C&C server, Turla used a specially-formatted message which encoded the URL of the server. It would be much simpler to just include the C&C URL directly in the code, but that would also make it easier for researchers to discover.
The message was posted on a picture on Britney Spears’ Instagram account and appeared like a fan comment. The comment is highlighted in red below:
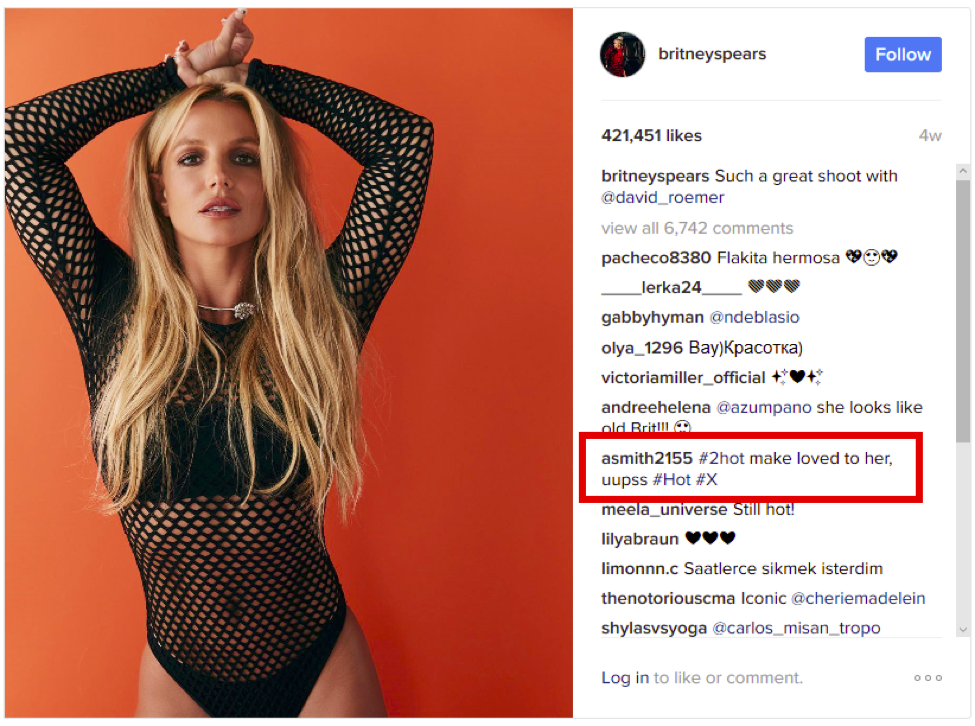
The Firefox extension would use a “regex,” or regular expression, to turn that comment into a URL. A regular expression is a common programming function which can transform data. In this case, Turla wrote a regex which turned the comment into a Bit.ly URL (a link shortening service).
The Firefox extension would then visit the Bit.ly URL and be redirected to the C&C server. Once contact with the C&C server was established it could send and receive data and commands with the compromised computer. If the hackers suspected their C&C server was discovered, they could send out a new URL to communicate with.
The whole goal here is to obfuscate – make it difficult for a researcher to determine how the extension works and what C&C server it is communicating with. The hackers may have found a link on Instagram to be beneficial. For instance, they may know it’s a website likely to be accessible from most networks around the world.
It’s important to understand that Britney’s account was in no way “hacked” or compromised. The hackers are just using her post as a covert message board, hidden in plain sight. They could just have easily as chosen Selena Gomez, Usher, or your neighbor Fred.
ESET, the security company that first reported on this incident, noted that other malware have used similar tactics. In 2014, they found malware hiding encoded messages on a Twitter account. This is the first time ESET has seen Instagram being used to hide messages.
Why they chose Britney Spears’ account is anyone’s guess. Maybe they determined Spear’s account was less likely to moderate comments or delete posts. Maybe the early 2000s were just this hacker’s favorite era of pop. Or maybe they’re just a Criminal. Sorry, sorry. I said I’d stop.
I’m going to just cut myself off now.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown