SHA-1 Option will be Completely Shutdown for SSL & Code Signing Certificates
The deadline has passed, SHA-1 is officially outmoded and will now be met with browser security warnings.
The day has come…SHA-1 SSL and Code Signing Certificates are no longer offered by major Certificates Authorities (CAs) such as Symantec, GeoTrust, Thawte, Comodo, and RapidSSL. If you haven’t already updated all certificates to SHA-2 – which is the latest industry standard – we highly recommend consulting with your system administrator/SSL Provider and update all certificates accordingly.
If you are using a SHA-1 certificate that has been issued on or after January 1st, 2016, certain internet browsers such as Google Chrome 48 (currently in beta) will display a security warning stating “Your connection is not private.”
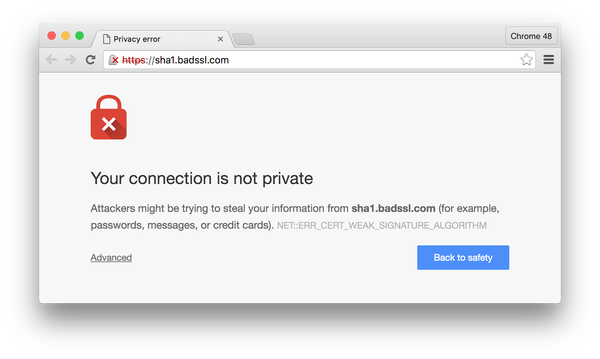
Furthermore, after January 1st, 2017, Chrome will completely block SHA-1 based certificate chains and continue to display fatal network errors.
All web browsers and websites have the ability to securely communicate and encrypt any data transmitted using the help of hash functions. These hash functions are unique digital signatures that helps verify the authenticity of the device receiving the transmitted data and eliminate malicious man-in-the-middle attacks. Since 1995, SHA-1 encryption has been widely adopted as the industry standard and is approximately deployed over 90% of websites. Fortunately, the industry has drastically evolved over the past two decades and recent studies noticed that SHA-1 is getting weaker – from a security point of view – and was the reason behind several major attacks recently.
Google and other companies such as Mozilla Firefox and Microsoft Edge have identified the weakness in SHA-1 and designed a plan to completely ban any SSL Certificates using SHA-1 encryption over time. Microsoft is going one step further and even blocking SHA-1 based certificates on their Operating System (i.e. Code Signing Certificates for Windows 7 or higher). Even User Mode Programs (msi and exe files) and Kernel Mode Programs (sys files) recommend users to update their Code Signing Certificates from SHA-1 to SHA-2 encryption as early as possible. In addition to the weakening SHA-1 algorithm, browsers such as Google Chrome 48 have also decided to discontinue the support for RC4 cipher suites which are used during the TLS connection.
With CAs no longer issuing SHA-1 certificates, Google hopes all website owners will update their SSL certificates immediately to avoid having their end-users receiving nasty error messages. At the same time, tech giants like Facebook stated 7% of browsers are not able to support SHA-2 based certificates and do not want to cut off millions of people from the internet. Yes, the industry does not want to limit internet access to end-users, but at what point does providing a more secured environment to the majority of the population take precedence.
In the end, the industry is leaning towards a safer online community and TLS features are being updated to accommodate new industry standards. If you haven’t already updated your certificate(s) from SHA-1 to SHA-2, we highly recommend you make this a priority and join the new-age TLS era. Trusted companies like The SSL Store™ spend every wakening moment devoting their services to the online community and help website owners stay up-to-date with industry standards while providing genuine products like SSL and Code Signing Certificates with the latest SHA-2 hashing algorithm, at a great low price.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown