Spearphishing Compromised two Florida Counties’ Voter Databases in 2016
Governor Ron DeSantis announced today that Russian hackers accessed databases in two Florida counties
While, at least so far, Russian election interference didn’t rise to the same level in the 2018 US midterm elections as it did in the Presidential race two years earlier – we are still learning about the breadth of their efforts to disrupt that 2016 election.
Case in point, today Florida Governor Ron DeSantis announced that a pair of Florida counties had their voter databases compromised by Russian hackers before the 2016 US President Elections. The attackers gained access to these databases with spearphishing emails that fooled county officials into clicking a malicious link.
DeSantis said that no data was altered and that the election results were not compromised, but he wasn’t allowed to disclose the counties by virtue of an agreement with the FBI, which is investigating the matter. They have been notified and are now aware of the matter though.
This is of particular interest to us at The SSL Store™ because we both reside in Florida – our offices are in sunny St. Petersburg (in Pinellas county) – and we deal with email security and phishing quite a bit. In fact, we quite literally just wrote a book on it.
So, today we’re going to talk a little bit about spearphishing and how you don’t have to be a county election official to be targeted by it.
Let’s hash it out.
What is Spearphishing?
Spearphishing is a type of phishing attack that leverages social engineering to target a specific individual. There’s a specific variant called whaling, which targets high-level executives. This appears – with the limited information available – to be more run-of-the-mill spearphishing where they tried to create a believable scenario where the target would take the desired action – opening an attachment or, in this case, clicking a link.
Again, without more information it’s difficult to know exactly how this all played out. We’re not even sure if DeSantis used the correct terminology and was actually describing a different variant of phishing all together. And it’s not as if there’s a consensus on nomenclature in the first place.
What we can do is go over some of the more common tactics associated with his kind of phishing. In a true spearphishing scenario the attackers often build dossiers of information on the target using publicly available data from social media sites like LinkedIn. This helps them if they’re trying to go a more personal route.
In the context of phishing election officials it’s more likely they were focused on less on the individual and more on the role they were targeting, this can be done by mimicking popular brands and companies, or even other employees (when high-level employees are imitated this is sometimes referred to as CEO Fraud). The idea is to create a situation that either causes a sense of urgency and requires immediate action, or – as the recent data indicates – to play to your vanity and get you to click on something without thinking.
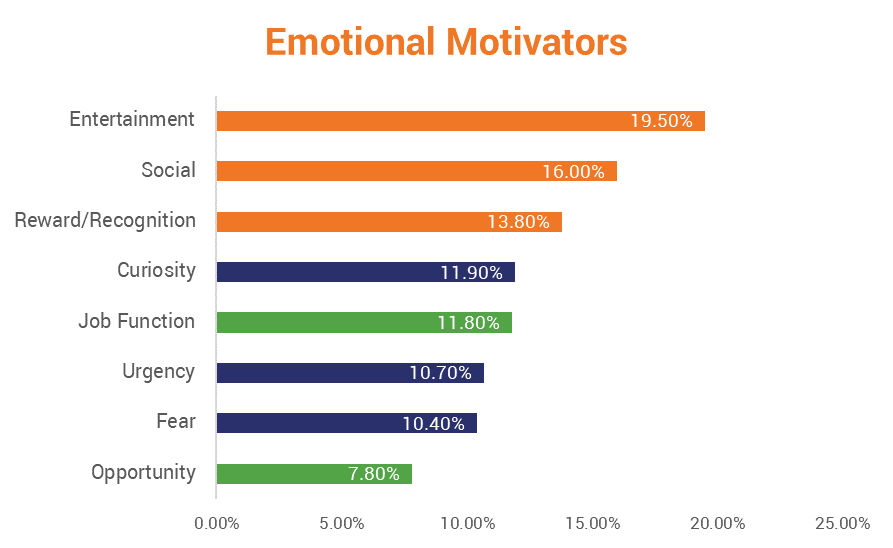
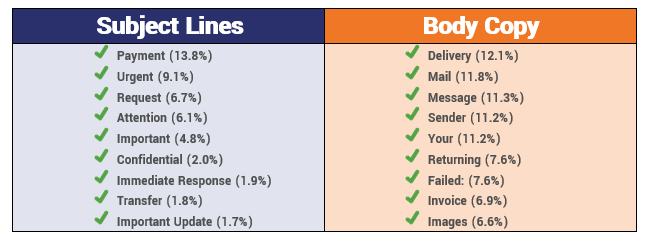
There are certain words and phrases, as well as certain flavors of email that come up more often, too. Here are some of the most popular from a recent study.
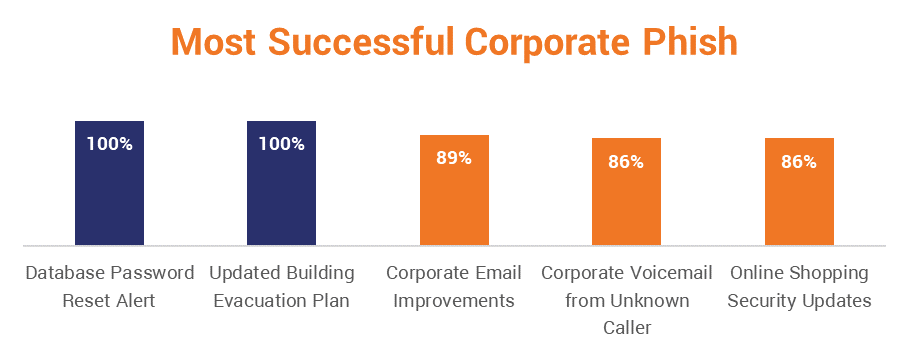
How do you fight Spearphishing?
Education is the best tool when it comes to stopping phishing and improving email security in general. Technology isn’t what’s being defeated when you get phished – people are. So making sure that you train your employees – in addition to implementing the correct safeguards – is tantamount to a strong security posture.
And the good news is that evidence shows this really does work.
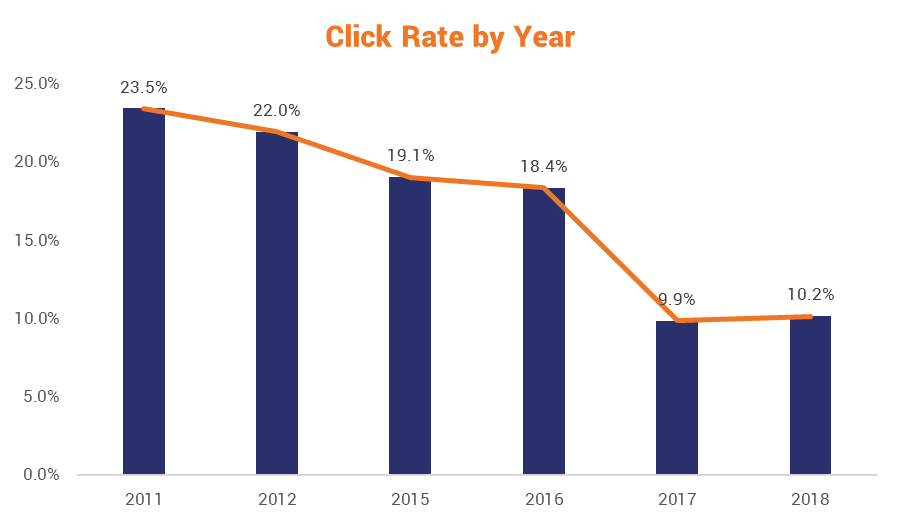
Over time, and across multiple training campaigns, a recent study found that employees in the healthcare industry showed decided improvement in identifying phish.
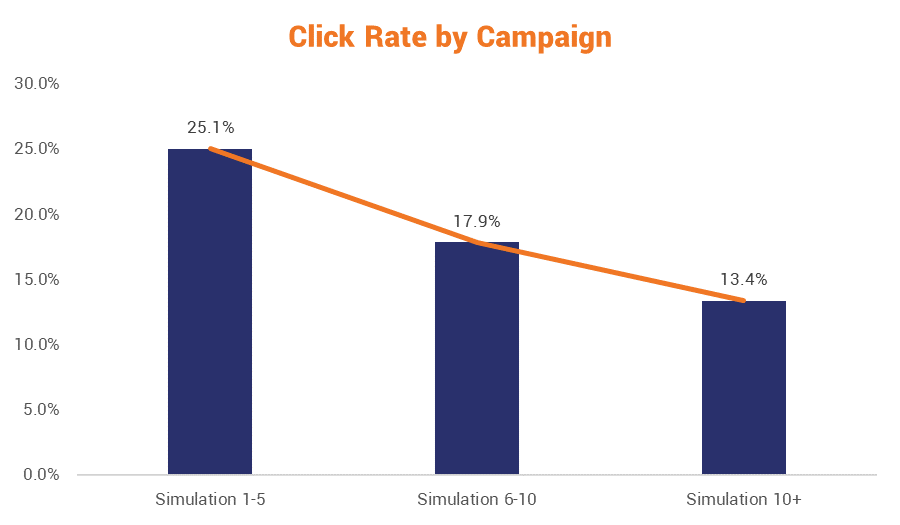
But this is only possible if you take an active approach to email security – something that many, government organizations included, have yet to make a priority.
We may update this story as more information becomes available.







































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown