WannaCry Ransom Total: How Much Money Did The WannaCry Authors Make?
The WannaCry Ransom Total Is Lower Than You Think.
Many cyber security professionals worked through the weekend thanks to the WannaCry ransomware which started spreading around the globe on May 12th.
The story of the WannaCry malware resembles a Hollywood script. On Friday the ransomware spread like wildfire – starting in Europe – and infected over 200,000 computers, including large portions of England’s National Health Service causing hospitals and doctor’s offices to shut down non-emergency services.
The ransomware exploited a Microsoft Windows’ vulnerability, which had been discovered by the NSA, subsequently leaked by The Shadow Brokers, and patched two months ago (seriously, go patch now if you haven’t). This particular exploit made WannaCry particularly effective at infecting devices within an organization.
Then an anonymous researcher accidentally discovered how to stop the attack simply by registering a domain name. This weekend the British media ‘doxxed’ the researcher (published his real world identity) and Microsoft pointed fingers at the NSA for causing all this trouble in the first place. Then the alien invasion started! Wait, no.
After pulling a weekend-shift, many IT professionals and researchers are now prepared for Monday morning which will likely see a spike of new strains and new infections as offices start their week.
So, if you are a ransomware author who successfully spreads your attack across the globe and infects nearly a quarter of a million devices and major companies including Renault, Fedex, how much money can you expect to make?
Shutting down Fortune 500 companies must pay a pretty penny – these authors, whoever they are – must be ready to retire, right?
Ransom Revenue
First, let’s cover the ransom demands. Upon infection, WannaCry encrypts your computer’s files and demands $300 USD paid in Bitcoin. After three days the ransom doubles to $600. Because the infection hit many computers on Friday, that ransom will now have doubled for many who did not pay over the weekend.
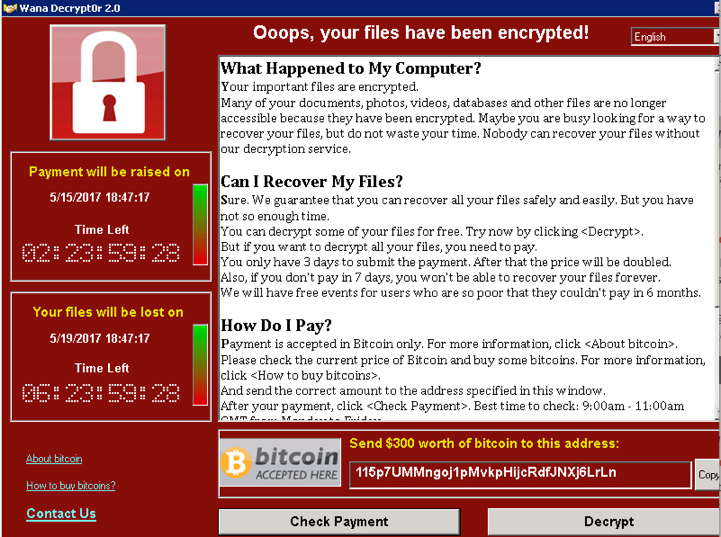
The ransomware asks for payment to one of three bitcoin addresses. While bitcoin payments are ‘anonymous’ (only revealing the bitcoin address of the sender and receiver) all transactions are publicly recorded in the blockchain. This makes it quite easy to see just how much revenue WannaCry’s authors are receiving.
Looking at the blockchain data allows us to see the amount of bitcoins transferred, the sender and recipient’s bitcoin address, and the time of the transaction. This is a good amount of data but requires us to guess certain factors, such as why particularly large or small payments would have been made.
The three bitcoin addresses listed in the ransomware are:
13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
As of Monday afternoon, those addresses have received a total of 215 payments.
But not all of those payments were ransom – 35 were under $1USD, and 15 under $25 USD. Many of these payments were duplicates – sent by the same person. This suggests these small payments were likely made by researchers testing the ransomware application.
Two additional payments were around $50 USD – larger than necessary for testing, but far below the ransom. They may have been errors or victims who have negotiated a smaller ransom.
The remaining 163 payments are likely ransoms – ranging from $3,424 to $168. The total amount of ransom collected is $51,644. Nearly $20,000 of the total ransom has been collected today.
(UPDATE: As of 5/16 the total ransom collected is $72,000. Updated total courtesy of actual_ransom.)
Eleven ransoms – including the largest for $3,424 – were likely payments for decrypting multiple computers. These payments were for more than $500 and occurred before 5/15, when ransoms would still have been $300 per device.
The average ransom paid (excluding the $3,424 ransom) is $318. Bitcoin’s price has been fluctuating between $1,640 to 1,820 over the last few days, which means the current value of the ransom may be slightly higher or lower depending on when the ransom was originally paid.
While Bitcoin can be directly used to buy some items, the criminals will need to be able to turn their collected ransom into USD (or their local currency) for this to be a true payday. But given the massive amount of attention they have drawn to themselves, safely converting that Bitcoin into real currency could be a problem.
For now, these criminals have not actually made a single penny. None of the ransom has been withdrawn or moved from any of the associated bitcoin addresses. It is possible that the bitcoin never moves – especially if the criminals are afraid it will lead to their identification. If that happens, this money will essentially be “missing” – visible on the blockchain but never being used.
Economics of Ransomware
Even though WannaCry has been severely crippled by MalwareTech’s discovery, it has still infected and successfully encrypted more than 100,000 computers. While there is not yet evidence of a “v2” circulating in the wild, it is possible that a variant could be released and spread.
Hopefully the businesses and owners of these computers have backups – which will allow them to wipe the device, restore the data, and clean the infection themselves. But we know that many don’t have the proper security measures in place. This means that tens of thousands of victims have three choices: pay the ransom, deal with the loss of their data, or wait for the research community to develop a decrypter.
For many businesses waiting isn’t an option.
Over the next few days the total ransom collected will rise substantially as businesses and users give in to the demands to recover their data. More ransoms are being paid every hour; by the time you read this post the exact figures given here will be out of date.
But given the current trend, it’s hard to imagine the total ransom surpassing $200,000. While a dollar may go much further in other countries, this sum is likely not worth the risk given the number of governments and law enforcement agencies that will be trying to identify these criminals.
It turns out you need more than a successful exploit to guarantee financial success.
But more important than the attacker’s payday is just how insignificant that sum is in comparison to the amount of damage done.
Many affected businesses shut down for the day (or longer) and had technicians working overtime to deal with infections and prevention measures over the weekend. Imagine the economic loss that comes from shutting down a single office or factory for a single day. Even a company with all the necessary backups will have to spend hours restoring machines or ensuring every computer is properly patched.
Microsoft’s bandwidth bill for delivering the MS17-010 patch is likely more than the $50,000 collected by the criminals.
Clearly this attack has shown that major organizations – who should know better and have the necessary resources – are not even doing the minimum needed to keep their machines secure. Running Windows Update and installing a two month old patch would have saved these computers.
But it’s also concerning that criminals have incentive to cause millions of dollars of damage and disruption for fractions of a penny on the dollar. So far, the criminals have made about 25 cents per infected computer – while the total ransom may rise substantially over the next few days, we are still talking about less than a single dollar per computer. Do you think you could defend yourself for that little?






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown