Want to Do More Than Secure Emails? You Can With Our New S/MIME Certificates
New security requirements for publicly trusted email security certificates are now in effect. Here’s an overview of TheSSLstore.com’s new S/MIME products that are compliant with the industry’s latest requirements.
Starting Sept. 1, 2023, industry changes officially rolled out regarding how publicly trusted email security certificates would be issued and managed. The goal? To improve email security and authenticity while not breaking existing deployments.
Historically, the industry lacked standardized requirements regarding certificate subject validation. The new S/MIME standards, released on Jan. 1 and covered previously in another article, aim to set specific parameters that certificate issuers must adhere to regarding the issuance of publicly trusted email security certificates. The CA/B Forum, the industry’s standards body, has since released an updated version of its S/MIME Baseline Requirements (version 1.0.1).
Now, here we are nine months later after these new requirements have kicked into effect. So, what do these changes look like in terms of our new S/MIME certificate product offerings and their validation requirements?
Let’s hash it out.
TL;DR: An Overview of the New S/MIME Products
The new email security certificates are a mix when it comes to their validations and capabilities. Some allow you to digitally sign and protect the confidentiality of your messages (using encryption and decryption) while others provide additional functionalities.
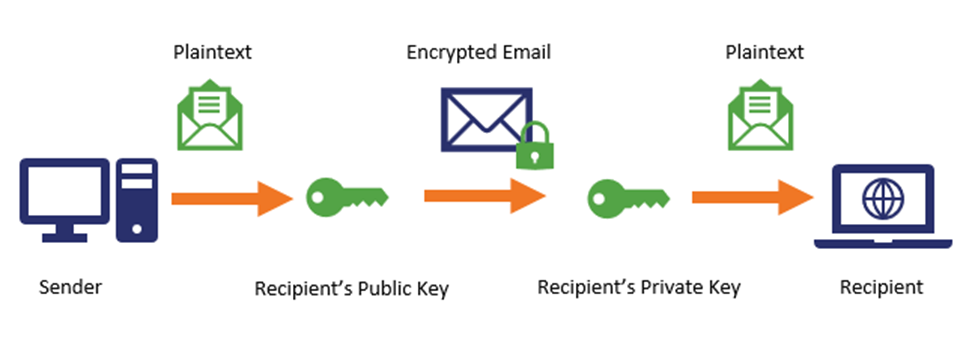
Different certificate authorities (CAs) are approaching the rollout of the new standards in different ways. For example:
- Sectigo offers three types of S/MIME certificates (called Personal Authentication Certificates),
- DigiCert offers two types of S/MIME certificates.
Here’s a quick overview of the three types of S/MIME certificates we offer — all of which are valid for a maximum of two years (825 days):
| Strict Mailbox-Validated S/MIME Certificate | Multipurpose Mailbox-Validated S/MIME Certificate | Multipurpose Organization-Validated S/MIME Certificate | |
| What It Does | Digitally signs and secures emails (encrypt and decrypt) for an individual employee’s account. | Gives individual employees the ability to do more than “just” digitally sign, encrypt, and decrypt emails. (Also provides document signing and client authentication capabilities.) | Displays your company name and does more than “just” sign, encrypt, and decrypt emails. (Also provides document signing and client authentication capabilities.) |
| Validation Type | Email Verification | Email Verification | Email + Organization Verification |
| Issued To/Displays | Email Address (name@company.com) | Email Address (name@company.com) | Email Address & Organization (name@company.com and Company Name) |
| Works for Shared Email Providers (@gmail.com, yahoo.com, etc.)? | Yes | Yes | No |
| S/MIME Certificate Providers We Partner With | Sectigo DigiCert | Sectigo | Sectigo DigiCert |
Strict, multipurpose, mailbox validated, organization validated — what do these terms mean? In a nutshell, our three types of certificate offerings fall within two overarching categories. Let’s break it all down.
Mailbox-Validated S/MIME Certificates
Mailbox validation refers to the use of an individual’s email address (e.g., example@randomemaildomain.com) for validating that the certificate Subject is in control of that mailbox. This type of S/MIME certificate can be used for:
- Individuals who aren’t associated with a company, or
- Individuals who work for an organization.
But this approach isn’t one size fits all; there are two categories of certificates that fall within this classification, which vary based on the certificates’ functionalities:
Option #1: A Strict Mailbox Validated S/MIME Certificate
The Strict Mailbox Validated S/MIME Certificate is the most basic type of email validation and is used to secure an individual mailbox. To complete validation for this type of certificate, the certificate issuer must verify that the email address is controlled by the certificate Subject (i.e., the person it’s issued to).
It’s useful for digitally signing, encrypting, and decrypting messages. (NOTE: To exchange encrypted messages, both the sender and receiver must use S/MIME certificates.) Currently, we offer two types of strict mailbox-validated email security certificates:
- DigiCert’s Class 1 S/MIME certificate
- Sectigo’s Basic S/MIME certificate
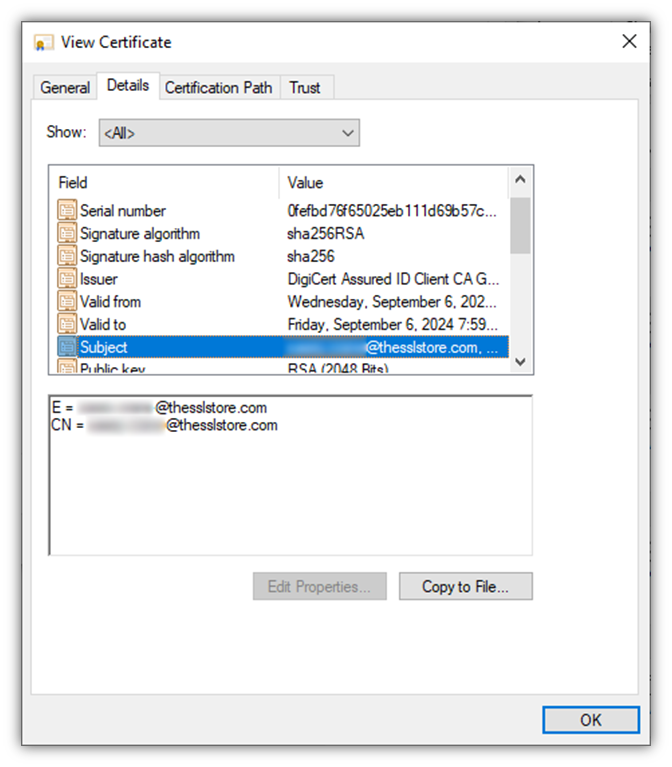
Here’s an example of what it looks like when I digitally signed an email using DigiCert’s Class 1 S/MIME Certificate:
Option #2: A Multipurpose Mailbox-Validated S/MIME Certificate
As the name implies, multipurpose S/MIME certificates aren’t just good for email signing and encryption/decryption. They’ve “leveled up” and provide greater flexibility, being capable of performing additional functionalities:
- Email encryption and decryption,
- Email digital signing,
- Document signing*, and
- Client authentication.
NOTE: To digitally sign Adobe PDFs, you’ll need a separate document signing certificate*
At this time, we offer Sectigo’s Pro S/MIME certificate.
Organization-Validated S/MIME Certificates
The use of this type of S/MIME certificate extends beyond the uses of any individual mailbox. Rather, its intended uses are broader in terms of representing your company or organization.
Tired of sending unsigned emails from your company? Are your customers unsure about whether your messages are legitimate or phish? Install an organization-validated S/MIME certificate and remove any doubt. Digitally signing your messages in your organization’s name allows recipients to check the veracity of your messages to know whether your organization really sent them.
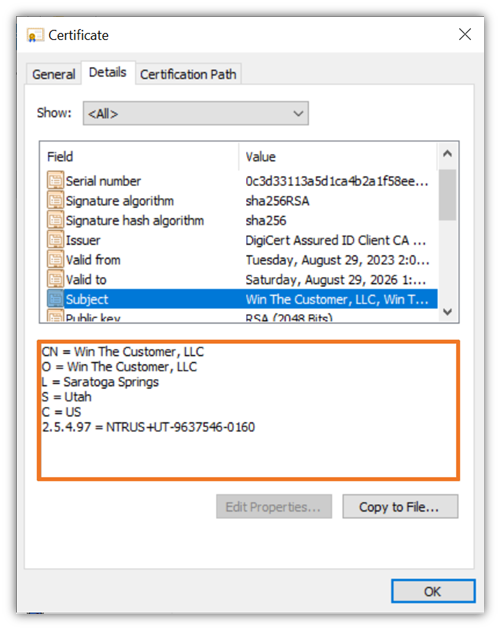
Option #3: A Multipurpose Organization-Validated S/MIME Certificate
This type of certificate offers the best of both worlds — organization validation + the multipurpose functionalities that extend beyond digital signing and encryption/decryption. It’s a tool for large organizations or enterprises that want to send emails from a validated company name and email address.
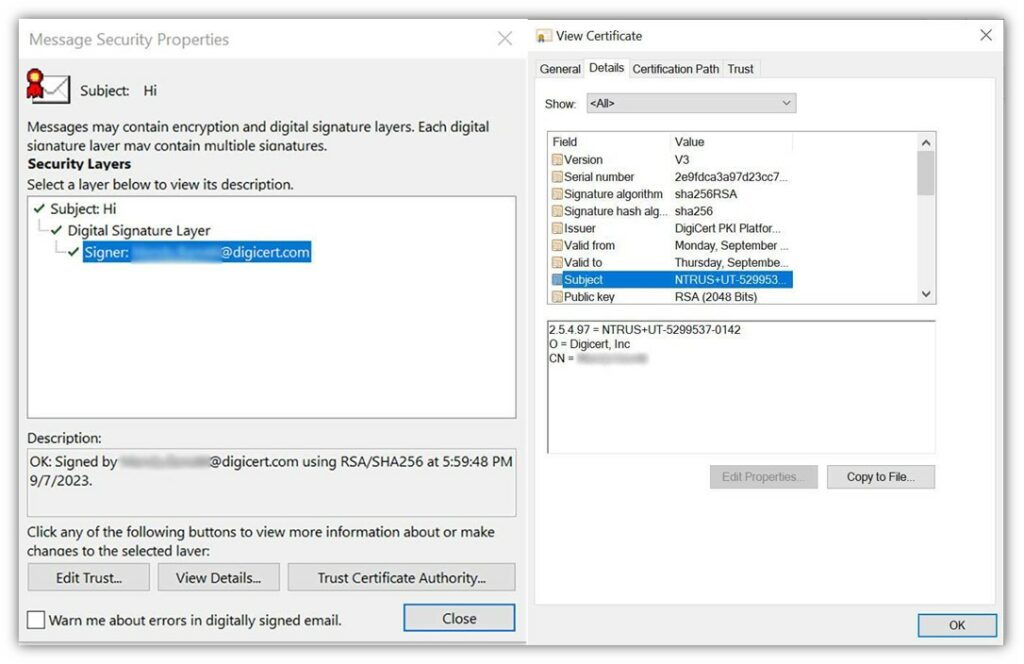
Here’s another example of how this information displays when you’re using an individual employee’s email address for an organization-validated certificate:
Much like the mailbox-validated multipurpose certificates we mentioned earlier, these organization-validated multipurpose S/MIME certificates enable you to digitally sign documents* and perform client authentication in addition to their traditional email signing and encryption/decryption capabilities.
NOTE: To sign PDFs using Adobe Acrobat, you’ll need a separate document signing certificate*
We offer two options for Multipurpose Organization-Validated S/MIME Certificates:
- DigiCert’s a premium S/MIME certificate
- Sectigo’s Enterprise S/MIME certificate
Want to learn more about our certificate offerings, or need help placing an order? Contact our support team to get help right away.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown