What to Do with Suspicious Emails: How to Report Scam Emails
Tired of scammers filling your inbox with crap? You can (and should) fight back — here’s how to report scam emails
Knowing how to recognize a phishing email is an important piece of knowledge. But once you’ve come across an email that you think is illegitimate, what are you then supposed to do with it? Knowing what to do with suspicious emails when you receive them is a critical yet often overlooked aspect of cyber security.
Verizon reports that phishing was present in 36% of breaches they analyzed for their 2021 Cost of a Data Breach Report. (And those are just of the known breaches they studied!) Knowing this, phishing remains a serious threat to businesses and private individuals alike.
In this article, we’ll break down how to report scam emails and what you should do with other suspicious emails you receive.
Let’s hash it out.
What to Do with Suspicious Emails: Report and Delete Them (Don’t Open Them!)

If you receive an email from someone you don’t know, a good rule of thumb is to avoid trouble altogether by not engaging with the messages in the first place. However, accidents happen, and everyone makes mistakes. If you do open a message, you should at least avoid taking any of the following additional steps:
- Clicking on links in unsolicited emails,
- Opening unsolicited attachments (Word docs, Excel spreadsheets, image files, etc.), and
- Sending requested information or files.
Instead, what you should do is report unsolicited outreach messages. Of course, understanding how to report scam emails differs based on your location, situation, and other factors.
In the next few sections, we’ll explore several of the ways that you can report emails both inside and outside your organization.
Report Scam Emails Within Your Organization
While it’s true that it’s your IT team’s responsibility to implement phishing and spam prevention methods, the fact is that some scam emails and other suspicious messages are still going to make their way into your inbox.
Remember those Smokey the Bear “only you can prevent forest fires” advertisements? The same concept applies here. As an employee, it’s also your responsibility to report scam emails to your organization’s IT team as well when you come across them.
Frankly, this should be something that’s covered in your organization’s employee cyber awareness training. But if it’s not, reach out to your IT team or admin to find out what your organization’s process is for reporting spam, suspicious emails and scams.
The types of information to inquire about include:
- Finding out which email address to send suspected emails to,
- What information regarding the emails you should include, and
- What you should do if you clicked on a link or otherwise engaged with a suspicious email.
Security doesn’t operate in a bubble; it requires everyone to take steps that help strengthen your organization’s cyber defenses.
An Example of Reporting Scam Emails and Phishing Incidents to Your IT Admin
Here at The SSL Store, for example, we have a process outlined that we follow whenever we receive a phishing email. There’s a dedicated email account where we can send information about the email, including:
- A screenshot of the message,
- Email header information,
- Other pertinent information, and
- An attached copy of the email in question (in specific cases but not all).
Here’s a quick screenshot of one such email I sent to our IT admin. As you can see, I started out with just a quick message and a screenshot of the email in question. After that, I copied and pasted the email header information as well (only part of which you can see in the following screenshot):
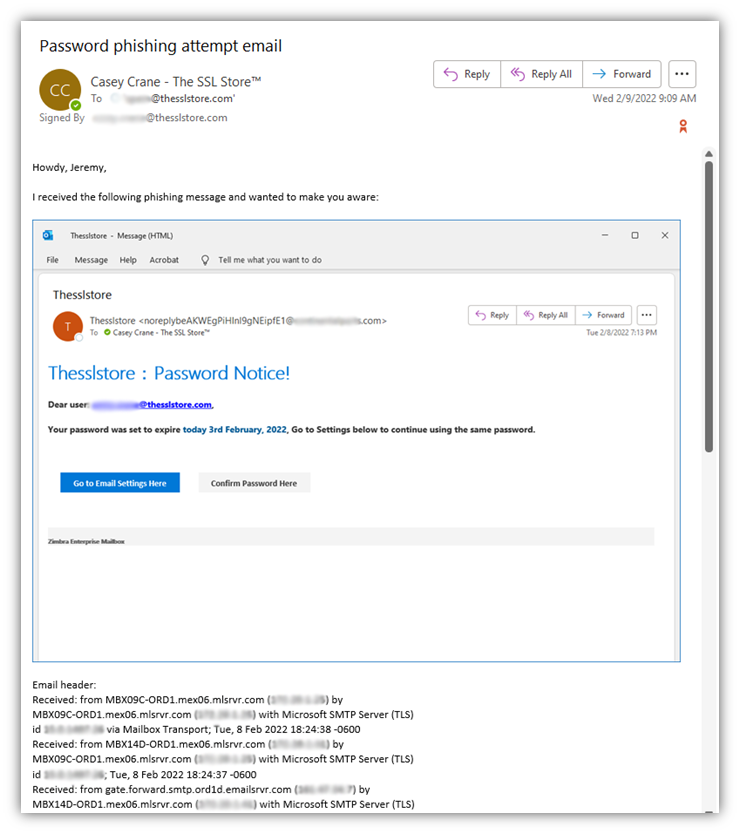
“But, wait, I thought you said not to open the email. So, how do you access the email header information if you don’t open the message first?”
Yes, that’s true — we did say not to open suspicious emails. But what you may not realize is that you don’t always have to open an email to access its header details. In Outlook, for example, there’s another way to access that information: simply add the Message Header command to your quick bar. Here’s how you can do that:
- Click on the down arrow drop-down menu in the right-hand side of your navigation ribbon.
- Select Show Quick Access Toolbar.
- In the new toolbar, select More Commands from the Customize Quick Access Toolbar dropdown menu.
- In the Outlook Options window, select All Commands from the top dropdown menu.
- Scroll down and select Message Header
- Press Add >> and then OK to add it to your Quick Access Toolbar in Outlook.
Don’t worry, you won’t have to do all of these steps next time since you’ve now added the command to your toolbar. Just select the email you want to view the header, press the Message Options command, and you’re good to go.
Report Emails to Your Email Service Provider
Another step you can take is to report scam emails to email service providers as well. This is a pretty easy process because virtually all email providers and clients typically integrate a reporting tool into their platforms.
For example, in Gmail, you’ll open the email in question and select the three-dot menu next to the Reply button. There, you can select the Report Phishing option. Otherwise, if you’re in your inbox and don’t want to open the email, you can instead right-click on the message and press Report Spam.
For Outlook, you can right-click on a message in your inbox or navigate to the Message > Block Sender menu tab as shown below. There, you should see the Junk Email Reporting option:
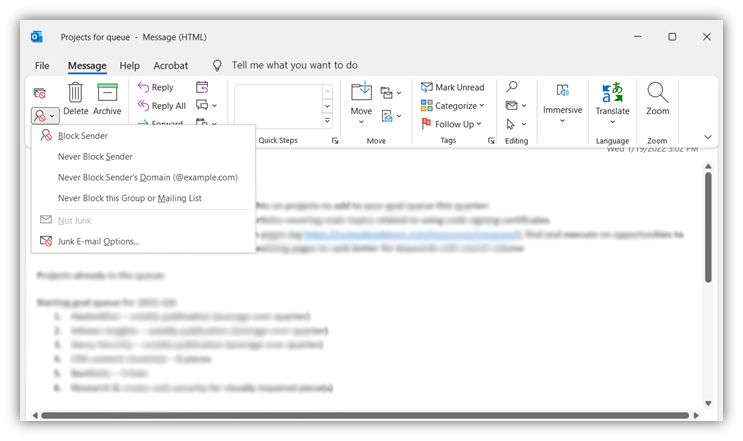
If you don’t see it, you first may need to install the Microsoft Junk Email Reporting Add-in or, at the very least, make sure it’s enabled. Check out this article from Microsoft to learn more about this junk email reporting add-in.
Report Scam Emails to Law Enforcement & Other Authorities (FTC, CISA, IC3, etc.)
Now that you’ve got things handled from an internal organization perspective, it’s time to ask yourself whether the phishing or scam messages you received should be reported to a higher authority. If yes, here’s what you need to know about how to report suspicious emails and malicious electronic messages.
The information you’ll need to provide will vary based on what it is you’re reporting and to which organization(s). For example, if you’re reporting that you’ve fallen prey to an email scam, you’ll need to provide additional information than you would if you were simply reporting the receipt of a scam message. For example, you might have to provide some of the following types of information:
- A description of what occurred
- How much was stolen
- Who was responsible for the attack
- Contact information for the attacker
- Your victim bank account where funds were withdrawn from
- The attacker’s bank account information where funds were sent
Below, we’ve outlined some of the reporting agencies that you can reach out to based on your geographic location.
United States and Canada
For our North American readers, you can report scams and fraud through the following methods and websites:
- Your local police department
- Your area State Consumer Protection Office
- U.S. Federal Trade Commission’s (FTC) Report Fraud website
- FBI’s Internet Crime Complaint Center (IC3)
- U.S. Department of Justice’s National Center for Disaster Fraud (NCDF)
- Canadian Anti-Fraud Centre (CAFC)
- Royal Canadian Mounted Police’s National Cybercrime Coordination Unit (NC3)
European Union, United Kingdom and Australia
For our readers in the UK, EU, or Australia, you can report email scams and fraud through the following authorities and resources:
- European Anti-Fraud Office (OLAF)
- eConsumer.gov
- National Cyber Security Centre (NCSC)
- Australian Competition & Consumer Commission (ACCC)
Report Emails to Impersonated Businesses and Organizations
This last one is important because it involves taking an extra step to help others avoid falling for cyber scams and fraud. While it’s great that you’re reporting scam emails to the proper authorities, it’s also important that you reach out to any organizations that are being impersonated in email and phishing scams to let them know what’s going on.
Until recently, Vade research shows that Microsoft has been the most commonly impersonated brand globally in phishing attacks. However, Microsoft was recently unseated by Meta (formerly Facebook) when the social media company took the undesirable crown as the most impersonated brand in phishing attacks for all of 2021.
Now, put yourself in the shoes of a company that’s being impersonated: how would you like it if someone was fraudulently impersonating you or your business while carrying out cybercrimes? If you aren’t aware of what’s happening and do nothing to warn your customers and other users, imagine the toll that would take on your business, brand, and reputation. Needless to say, you’d likely want someone to let you know what’s going on.
Some companies, governments, and other entities even have pages set up on their websites where you can report suspected fraud and misrepresentations. For example, Interpol has a fraud and abuse reporting form available where you can report instances of someone abusing or fraudulently using Interpol’s name. However, it’s important to note that you shouldn’t report other email scams and fraud to the organization in general — the Interpol website says such crimes should be reported to your local or national law enforcement agencies instead.
How to Tell If an Email Is a Scam in the First Place
Now that you know what to do when you receive a suspicious email and where to report it, this may leave you wondering how to tell if an email is legitimate in the first place. While we aren’t going to do a deep dive into that topic here, we’ll quickly cover a few key signs that can indicate whether an email you’ve received is a potential phishing scam:
- Sender’s name and email address don’t match
- Sender’s email information doesn’t match the organization or entity it claims to come from
- Email contains links to other websites that don’t match the anchor text
- Email contains unsolicited attachments (Office files, PDFs, images) that may contain malware
- Message is written in a way that feels urgent, pushy, desperate, or threatening
- Message is trying to coerce, trick, or manipulate you into doing something you shouldn’t
Check out these phishing email examples for a look at real-world phishing examples that we’ve received at The SSL Store. Furthermore, here are some great additional resources that you’ll likely find useful:
- 10 Types of Phishing Attacks and Phishing Scams
- Spear Phishing: How It Happens & Why You May Be at Risk
- Payroll Fraud: A Growing BEC Threat to Businesses and Employees Alike
- HTTPS Phishing: The Rise of URL-Based Attacks
Final Thoughts on What to Do with Suspicious Emails
From an organizational perspective, something we really haven’t touched on yet in this article is what to do with suspicious emails from an organizational perspective. Sure, you’ll want to take steps to protect your devices, network, users and data from being affected by the emails in the first place. But that’s not where your job ends — instead, something else you should do is use the suspicious emails your organization and users receive to your advantage.
By collecting these communications, you create a repository of phishing emails and other fraud examples that will come in handy. You can use these real-world examples to train and educate your employees and other applicable network users on what to look out for and how they should respond when they receive similar suspicious emails.
Cybercriminals are always looking for new ways to spice up old tried-and-true attack methods. By keeping yourself and your employees up to date on the latest email phishing and scam tactics, you’ll help strengthen your organization’s defenses and make it a more challenging target.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown