5 Real-World AI Cybersecurity Applications That May Benefit Your Business
Cybersecurity companies need to continually develop security technology as new vulnerabilities and threats arise. They have been effectively using artificial intelligence to do so for a long time. Can AI be a game-changer in protecting our data and privacy?
Editor’s Note: This is a guest blog contribution from Mike Jackowski, co-founder and Chief Operating Officer (COO) of ASPER BROTHERS. Mike shares his perspective on ways that AI cybersecurity applications can help strengthen your organization’s cyber defenses.
Cyber attacks and their associated costs are growing exponentially. With the advancement of technology in businesses such as the Internet of Things (IoT), more and more devices are connected to the internet. As such, it’s becoming increasingly difficult to tackle these attacks manually. This is where artificial intelligence in cybersecurity (i.e., AI cybersecurity) comes in.
In general, cybersecurity is all about protecting your organization against cyber attacks that can result in:
- Theft and damage of important data and intellectual property,
- Stolen funds and fraudulent wire transfers,
- Stolen private and business data,
- Reputational harm, and
- Non-compliance issues.
Such attacks, if successful, can cause serious losses to your business and damage customer relationships. With this in mind, it’s imperative that you take steps to help make your organization and its data as secure as possible against attackers.
AI cybersecurity efficiently reduces breach risks with real-time monitoring and has the capacity to handle situations that are no longer of human scale. Integrating advanced cybersecurity techniques by employing artificial intelligence can help you protect your business from cyberattacks and their devastating consequences.
Let’s hash it out.
What Artificial Intelligence In Cybersecurity Entails

In any domain, artificial intelligence is primarily used to study and learn from data in order to improve decision making. AI can be utilized to scale the operations of cyber threat detection and sort through all the “noise.” This enables you to evaluate which approaches to take based on those specific threats so you can make better data-driven decisions concerning cyber security.
Development of AI
Artificial intelligence is progressively taking over all areas of technology because of its rapid advancements and high applicability. The potential technological applications are also increasing because human intelligence is being simulated and expanded with the use of AI.
AI started with an initial set of algorithms that could simulate human intelligence. Now, it’s expanded to become a technology that has become a part of all the aspects of today’s society, including:
- Healthcare,
- Manufacturing,
- Environmental protection,
- Communication technologies.
An influential factor in its development is the huge amount of data available today. The amount of data produced daily is growing exponentially, thus increasing AI’s power and capabilities. Dr. Kai-Fu Lee, an AI Expert and former vice president for tech giants like Apple, Microsoft, and Google, told 60 Minutes:
“I believe (Artificial Intelligence) is going to change the world more than anything in the history of mankind. More than electricity.”
The current advancements show a promising future for AI (and AI cybersecurity). As such, it would not be wrong to assume that, at least in some aspects, AI can attain and even exceed the capabilities of a human mind.
Prevalence and Use of AI in Cyber Security
AI is becoming more and more prevalent in cybersecurity. According to IBM, in terms of mitigating and combating cyber attacks, security professionals struggle for several reasons:
- They face an overwhelming number of tasks. The sheer number of analysis and assessment tasks they’re responsible for handling are beyond human scale.
- There’s never enough time (time deficit). The time required to respond to cyber attacks has to be minimized as much as possible.
- There’s too much data to handle (data overload). Although having lots of data at your disposal is great, all of that data has to be sorted through and analyzed. This takes a lot of time and resources without AI cybersecurity tools at your disposal.
- The industry is facing an ongoing skills shortage. As we’ve seen for a while now within the industry, the necessary skills are not always readily available.
Therefore, all IBM Security products use AI. IBM further details that AI can automate the response to security breaches — it enables faster detection, analysis, and response, thereby accelerating the process with the benefit of enhanced accuracy.
“Where do I think AI will be in 5 to 10 years? While the possibilities are endless, I believe the most consequential will be secure application development.”
— Sridhar Muppidi (Chief Technology Officer for IBM Security)
Similarly, Microsoft also talks about the advancement of cybersecurity with the help of artificial intelligence. Some of the major advantages of using AI in cybersecurity they highlight include:
- Enhanced cyber attack detection and threat analysis,
- Improved ability to resist and respond to the scale and speed of attackers,
- Greater ability to interpret and learn from attacks to improve response
How Implementing AI in Cybersecurity Benefits Your Organization and Customers
There are numerous benefits for you and your customers if AI cybersecurity is utilized as part of your organization’s defenses. Organizations can prevent downtime if they have robust cybersecurity systems that employ AI. Data from a 2019 PwC Digital Trust Insights survey showed that nearly half of their respondents (47% of a total of 3,500 organizations across the globe) reported that cyber incidents caused downtime between 2017 to 2019.
With the increase in cyber attacks occurring each year, these numbers are expected to increase further. With the help of AI, organizations can automate cyber attack detection and response. According to Webroot, AI technologies (like automated detection and response [ADR] tools) can be used to automate everyday security tasks without relying solely on human teams. AI-based cybersecurity systems learn and adapt to ever-evolving cyber attacks and malware.
Automation is particularly useful for shifting the responsibility of handling monotonous tasks from your IT and cybersecurity employees. This allows them to shift their focus to projects and tasks that require their expertise, skills, and critical thinking capabilities.
AT&T emphasizes the benefits of blending AI and cyber security as a reasonable strategy for adaptive cyber security. All of this shows that the organization can benefit greatly by preventing disastrous attacks if they integrate AI into their cyber security defenses, which will result in more accurate, timely, and robust detection of cyber attacks.
According to MIT News, detecting the data generated in a cyber attack among all the normal data generated by the organization’s customers and employees is nothing less than finding a needle in a haystack. Therefore, it seems necessary to human-machine collaboration, which will ultimately optimally cover key areas of cybersecurity.
5 Applications of AI in Cybersecurity
Now that we have a good idea of what AI cybersecurity entails, let’s explore a half-dozen practical applications of it:
1. Enhancing Your Network Security
Network security deals with the protection against destruction, unauthorized access, and misuse of files and data in a system. It also protects the confidentiality of a network within an organization. AI can be utilized to automatically analyze the network traffic for any potential breaches or unauthorized access. Nick Atkin, who is the Head of Solution Architecture at Dubber, is quoted as saying, “AI can signal not just breaches in data protection but also breaches related to the content within that data.”
In network security, your network architecture and security policies are essential. The network architecture is responsible for taking care of the ways a business connects to the internet. The architecture is also important for keeping the business reliably and safely connected to the internet. For managing security on a network, a network policy is typically used to formalize the guidelines and procedures utilized to keep a network secure. According to Toolbox, AI can employ security policies and map the network traffic patterns to these policies.
Some common AI-powered cybersecurity platforms include:
- IBM QRadar
- Cynet
- Darktrace
- FireEye
2. Detecting Advanced Malware
Malware has been a serious threat to the security of organizations, and they evolve very rapidly. According to TechTarget SearchSecurity, one of the most triumphant accomplishments of AI in cybersecurity is the accurate detection of malware due to the availability of large amounts of data for training the deep learning models.
AI cybersecurity threat detection systems are particularly useful for finding malware applications that can keep changing themselves to avoid getting detected (e.g., polymorphic and metamorphic malware).
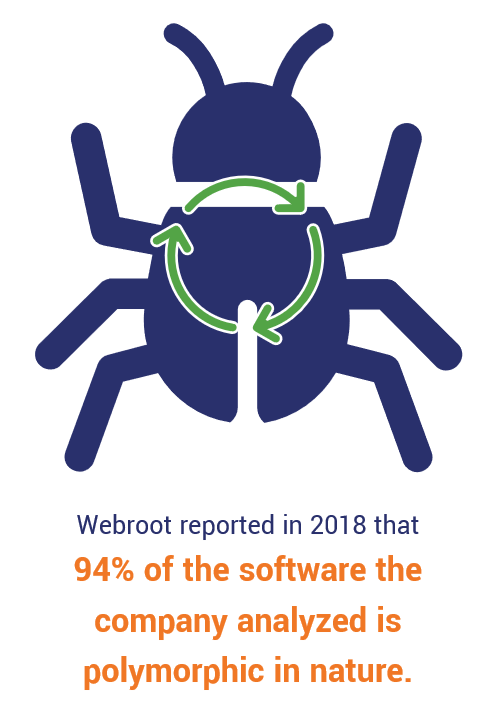
Polymorphic malware is a category of malicious programs that continuously change a portion of their codes and use encryption (for hiding its code) to evade anti-malware software. These cyber weapons use mutation engines to modify themselves and continuously evolve so as to make them difficult to detect. Unfortunately, these malicious programs have become quite common. According to a research by Webroot among the malicious software they analyze, 94% of them are polymorphic in nature.
Likewise, metamorphic malware is a category of similar malicious programs that change themselves to avoid getting detected, but they are even harder to detect than their polymorphic counterparts. The prime difference between metamorphic and polymorphic malware is that the former change their source codes entirely; polymorphic keeps some parts of its code, only modifying others.
The reason for rewriting the entire source code is to evade the anti-malware tools more effectively. These malwares are extremely difficult to detect using traditional cybersecurity tools. Thus, the learning and adaptive capabilities of AI cybersecurity are needed to detect and handle these continuously evolving threats.
3. Increasing Your Organization’s Data Privacy
AI cybersecurity systems can help prevent breaches of sensitive organization and customer data. Google has used Tensorflow to block 100 million spam emails. Tensorflow is a deep learning frame library for preventing image-based emails that are hard to detect and can also be used to steal organizational data.
An IBM Report analyzed the cost of data breaches. According to this report, customer data was exposed in 44% of the crimes, making it the most common type of information exposed in these breaches. The same report also shows that data breaches of organizations with automated security systems resulted in significantly lower costs per breach ($2.90 million) compared to those with no automation ($6.71 million).
4. Taking Your Cloud Security to the Next Level
With almost everything moving to the cloud, the risk of cyber attacks on cloud systems have also increased significantly. Gartner predicts that the cloud-first principle will be adopted by eight in 10 (85%) organizations by 2025. It also predicts that cloud-native platforms will host nearly all (more than 95%) digital workloads in that same timeframe.
According to CNBC, tech giants like Microsoft, Amazon, and Google have invested heavily in cybersecurity to combat the growing number of cyber attacks on their cloud platforms:
- Google acquired Mandiant,
- Microsoft acquired CloudKnox Security and RiskIQ, and
- AWS acquired Wickr.
AI is a very important element for preventing cyber attacks on the cloud because of the large volume and evolution of such attacks. Cloud service providers are actively employing advanced AI to create more robust and resilient cyber security systems. “100% of our products use AI,” says Sridhar Muppidi, the CTO of IBM Security mentioned earlier.
5. Giving IoT Security a Boost
The Internet of Things (IoT) is taking the world ahead by connecting everything to the internet. It has the potential to revolutionize almost all industries, and many businesses are investing heavily in IoT. McKinsey estimates that through 2022, IoT technology will experience a 13.6% increase in investments. IoT will connect a huge number of devices to the internet, thus exposing these devices (and the data produced by them) to potential attacks.
It’s not possible to handle the security of enormous amounts of devices on a human scale. AI will eventually become the only option for automatically monitoring, detecting, and preventing cyber attack activities. Azom describes IoT as still being in its infancy, with few security mechanisms for these devices. Knowing this, capitalizing on AI cybersecurity may help you make these smart devices more secure.
However, the development of AI- and machine learning-based cybersecurity for IoT is still new and under research. Many researchers are exploring this avenue, such as Kuzlu et al. who explored the role that AI will play in the security of IoT devices.
The Cybersecurity Risks of Artificial Intelligence
AI has very promising applications for improving the security of organizations. Simultaneously, it also comes with problems such as misuse by cybercriminals and nation-state actors. The vast amount of publicly available data that helps make advanced AI cybersecurity systems more resilient and effective at attack prevention can also be used by cybercriminals to train their AI systems to bypass them.
It would not be wrong to say that under unfortunate circumstances, AI can be a double-edged sword in the world of cybersecurity. Some of the cases in which bad guys can use AI to their advantage are as follows:
Developing Evolving Tools That Can Enhance Cyber Attacks
As we touched on earlier, malware developers can use AI to develop advanced polymorphic and metamorphic malware. These systems are difficult to detect by traditional anti-malware systems and cause serious problems if they infiltrate your network and other critical systems. AI can be used to make malware adaptable to detection by training the system on detection by powerful anti-malware software thus incrementally making the malware better and better. The more time is spent in training the system for adaptability, the harder it would be to detect such malware.
Creating “Deep Fakes” That Make More Convincing Phishing Attacks
Deep fake data can be generated using a vast amount of training data making it possible to bypass the security systems because such systems are dependent on data. Deep fakes also include facial videos and voices which match the original one so closely that it is extremely hard to distinguish.
With sufficient data for training, cybercriminals can use AI to make super realistic deep fakes that can bypass automated systems and humans as well. One such case is when the hackers used deep fake technology to impersonate an energy company CEO’s voice. The attackers used it to contact one of the CEO’s subordinates to instruct them to transfer $243,000 to a fraudulent account they controlled.
Creating Physical Threats and New Ransomware Opportunities
Self-driving cars use AI for their functioning and security. There is a possibility of attacking these self-driving cars with AI. This is discussed by Macquarie University, which states that self-driving cars can be vulnerable to malware attacks. Similarly, AI-based adversarial attacks can be used to fool self-driving cars into misinterpreting signs.
Final Thoughts on AI Cybersecurity
Artificial intelligence, undoubtedly, has unmatched potential for accuracy, speed, and scale in cybersecurity. New technological advancements such as IoT are bringing larger quantities of data to the table, and along with all of that information comes an increasing number of analyses that have to be made.
The requirement to analyze big data in real-time with acceptable accuracy is already getting out of hand for human intelligence. We need a way to intelligently, quickly, and effectively sort through all the data “noise” to put it to use to enhance our defenses and mitigate security issues. At present and in the future, AI will be needed in cybersecurity to make robust and resilient systems that are adaptive, scalable, and automated.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)






 (5 votes, average: 4.20 out of 5, rated)
(5 votes, average: 4.20 out of 5, rated)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown