Mobile Browsers Vulnerable to Address Bar Spoofing Attack
This clever tactic would be effective in a phishing attack.
A new vulnerability affecting browsers would be a nasty tool in the hands of phishers, luckily it will be patched quickly. The mobile versions of Firefox and Chrome were found to be vulnerable to address bar spoofing, which allows a malicious attacker to disguise a URL as another address.
Rafay Baloch, an independent security researcher, discovered the vulnerability and publically disclosed it last week.
Mozilla has already patched their Firefox browser for Android (make sure you update!) and their iOS version was never affected. Google’s Chrome browser on both iOS and Android is also vulnerable, however, it won’t be patched until September. The desktop versions of these browsers (Windows, Mac OS, and Linux) are not affected.
The vulnerability stems from a bug in the way that mobile browsers handle languages which read right-to-left. Computers understand how to consistently display text by using the Unicode standard (your web browser is using Unicode right now to show you this text). Unicode is a global standard and therefore supports a variety of written languages.
Some languages, like Arabic, are written and displayed right-to-left. Unicode allows computers to know which scripts are displayed left-to-right (LTR) and which are displayed right-to-left (RTL). The vulnerability comes into play when characters from an LTR language are combined with characters from an RTL language.
In this scenario, the attacker would construct a URL that includes both RTL and LTR characters. Baloch gave the example of:
127.0.0.1/|/http://example.com.
When you viewed the page in your mobile browser, it would misunderstand how to display the text and show it as:
http://example.com/|/127.0.0.1
(It’s tough to see the RTL character hidden in there – it’s between the pair of backslashes separating the IP address and the domain. We highlighted it in red above to make it easier to spot)
So while you are really connected to the IP address “127.0.0.1”, your browser is showing that you are on “example.com.” This is known as Address bar spoofing because the URL is able to masquerade as another URL in the address bar. Spoofing is a general term for any method which involves falsifying or forging data to make it appear like something else (usually another email address or website).
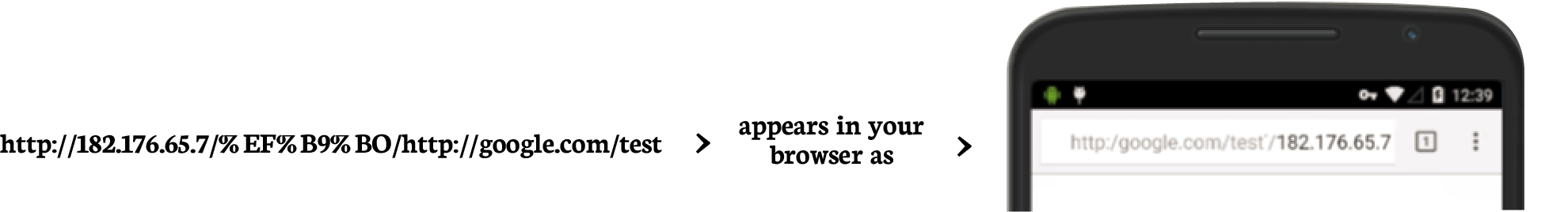
With this vulnerability, attackers could target any site they choose, all they need is a publically accessible IP address. If you want to see how this would look, click on this link from the Chrome browser on iOS or Android:
http://182.176.65.7/%EF%B9%B0/http://google.com/test.
When you visit the page it will appear like you are on Google.com. Now imagine if that page looked just like Google’s log-in page. Would it have tricked you?
An attack that can modify the appearance of the address bar is extremely dangerous. Confirming the URL in the address bar is legitimate security advice frequently published by high-security sites like Paypal.com.
If an attacker can make you think you are connected to a site like Google.com or Paypal.com, they could trick you into supplying login information or other sensitive details. This makes this vulnerability an incredibly effective tactic in a phishing attack. Google’s own security team has even stated, “We recognize that the address bar is the only reliable security indicator in modern browsers.”
If you are using Chrome on iOS or Android be aware of this attack, as both versions of these browsers will be vulnerable until a patch is released next month. Ensure you are tapping on the address bar and looking at the full contents of the URL. This is especially important when you are following a link from an email or webpage.
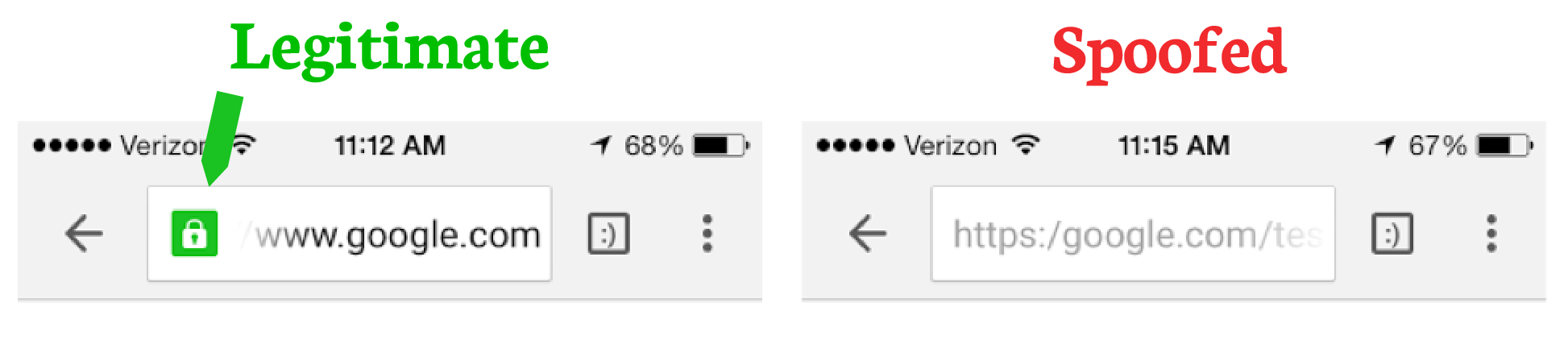
While this attack is quite effective in spoofing a URL, it is not able to easily replicate a secure connection. The legitimate versions of sites like Google.com and Paypal.com always use an SSL connection. So make sure that you see the green padlock icon in your browser before proceeding. Any site that you are logging into or sharing personal details with (credit card information, physical address, etc) should be using SSL.
The picture below shows you both the real Google.com site and a spoofed site using this vulnerability (on iOS). Notice that the green padlock only appears with the legitimate URL because it is truly using an HTTPS connection.
The spoofed URL on the right is only pretending to use HTTPS. Note how there is no padlock, and only one forward slash:
https:/.
The protocol being using should always be followed by two forward slashes.
In the disclosure on his personal blog Baloch writes that a variation of this vulnerability “has also been discovered in several other browsers that are still undergoing a fix there [sic] I am refraining from disclosing them. Details will be disclosed, once a fix has been landed.”
Baloch also presented a number of browser vulnerabilities at Black Hat Asia earlier this year.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown