Chrome Considers Restricting Data URLs to Combat Phishing
Data URL phishing has Google thinking restrictions.
Chrome is considering limiting the functionality of data: URLs in order to curb mis-use of the URL scheme by phishers.
Data: is a URL scheme, similar to schemes like http: and tel: which most users are more familiar with. Each one of these has a unique function. The function of data: is to contain data within the URL itself.
A legitimate use of a data: URL would be to reduce the number of HTTP requests a website needs to make, or to display dynamically-generated content within the browser. However, phishers often use data: URLs in their malicious activity.
What makes data: URLs so effective for phishing is that webpages can redirect to, or be opened via a link and displayed as stand-alone pages. They can also circumvent certain detection methods and filtering.
Chrome is considering removing any top-frame navigation to data: URLs to prevent this. Top-frame navigation refers to anything that occurs in the main browser window, instead of within a page. This means that the browser would ignore HTML <a> links and JavaScript functions like window.open and window.location if they lead to data: URLs.
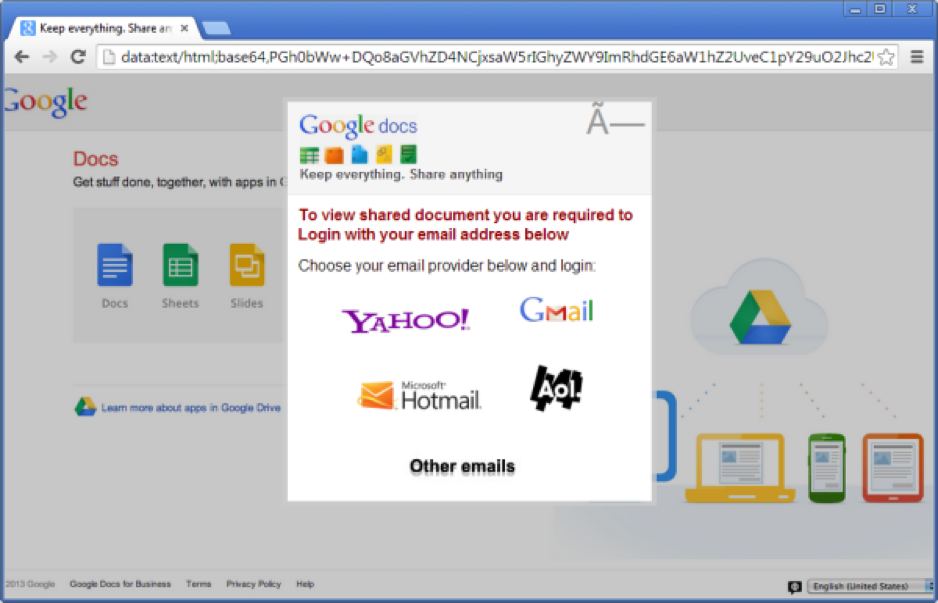
This would mean the only way to directly open data: URLs would be to type or paste them in. In proposing this change, Chrome’s engineers noted that Microsoft’s Internet Explorer and Edge browsers already block all top-frame navigations to data: URLs.
Website’s that would want to continue using data: URLs would need to use them in-line through iframes or loaded as resources on the page, instead of as their own pages.
Chrome has already made the decision to label all data: URLs as “Not Secure,” with a patch to Chrome 56. This is the same treatment that HTTP pages containing password/credit card fields are now given.
The Danger of Data:
Unlike an HTTP URL, which is a path to data, a data: URL is the data itself. One way to think of it is that a data: URL can actually be a phishing site. Here is an example of a very simple data: URL:
data:text/html, This is a data URL!
If you paste that into your address bar, it will display a page that says “This is a data URL!”
Dosen’t seem too dangerous, right?
Data: URLs can also contain arbitrary HTML, images, and other types of data. You can even embed script tags that load external files. Data URLs can also use encoding to obscure what they are doing. While a jumble of letters and numbers may not look very legitimate, it can be combined with other tactics to be an effective mask.
Attackers can pack a data URL with blank spaces to “hide” the full URL. Matthew Bryant put together a demo where he constructed a data URL that mimics Yahoo.com. While the layout is not perfect, it is a fairly good example of how a data URL could be an effective phishing tool:
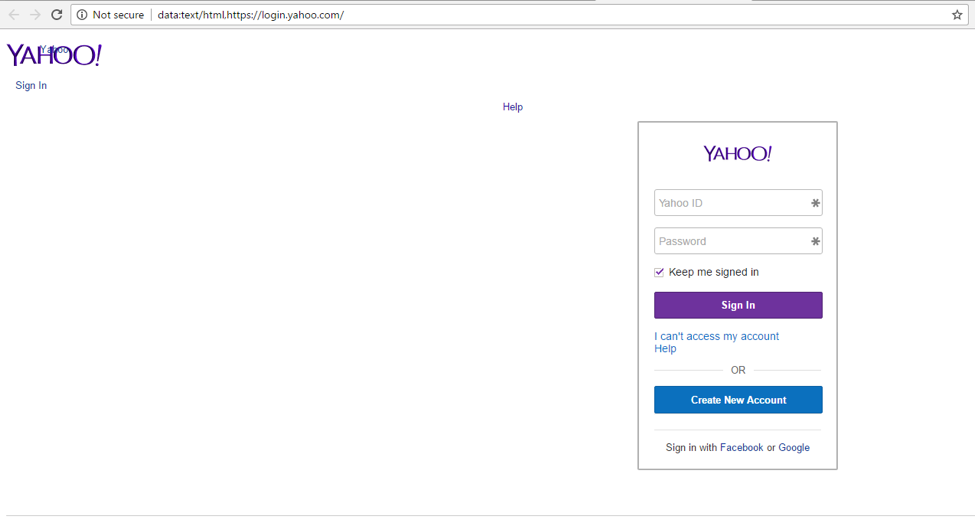
What you aren’t seeing in the screenshot above is that the URL continues far past the end of the address bar, where it is hiding a script tag that is loading the malicious form. Click here to see this proof of concept live in your browser.
Chrome’s engineers noted that data: URLs accounted for 0.05% of all top-frame navigations over the last 28 days. This may seem small, but it is actually a rather large percentage for a feature that is being considered for removal. However, given the sheer number of cases and complaints of phishing, the danger appears to outweigh legitimate use.
Before Chrome makes changes they usually solicit comments from other Google engineers and the public in the form of an “Intent To” thread. So far, there is support from multiple engineers to have navigation to data: URLs limited. However, they may ultimately decide not to make the change if it will break a significant portion of the web. If you want to voice your comments on this change, you can do so here.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown