Crypto and SSL Improvements in High Sierra and iOS 11
Announced at WWDC: LibreSSL, TLS 1.3 Beta, New Revocation Checking, & More
Last week Apple hosted their annual WWDC conference for developers. One of the big announcements was the new versions of their operating systems: High Sierra for macOS, iOS 11, tvOS 11, and watchOS 4.
Apple took some time to talk about the improvements they have made to their platforms’ cryptographic libraries and SSL/TLS support.
We have summarized all the changes below. The majority of these were announced at the session “Your Apps and Evolving Network Security Standards.” You can stream that session here (Safari and iOS devices only).
New Certificate Error UI
The certificate error UI has been redesigned in High Sierra’s certificate viewer and in Safari.
In Safari, the new error page has been designed to give a plain-English explanation of the problem without invoking jargon-y words like “Protocol” or “Signature.” There are a few similarities to Chrome’s UI.

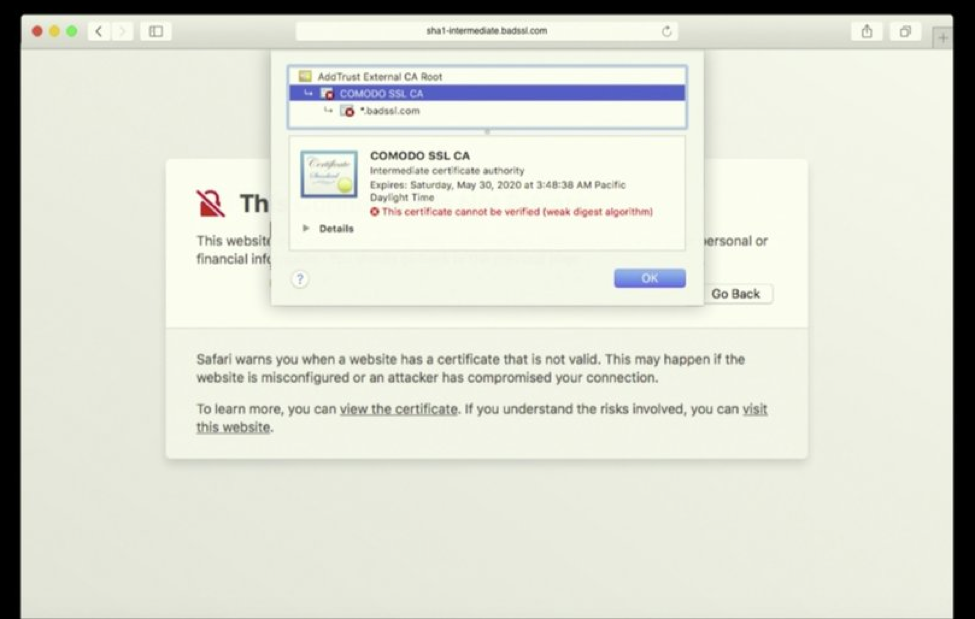
The certificate viewer also has more specific messaging. In the screenshot below you can see that a warning is displayed for the specific trust error. In this case, the error reads “This certificate cannot be verified (weak digest algorithm)” because it is signed with SHA-1.
Improved Revocation Checking
Apple unveiled a new revocation checking method for their platforms. It has not been given a proper name, but it operates similar to Mozilla’s OneCRL.
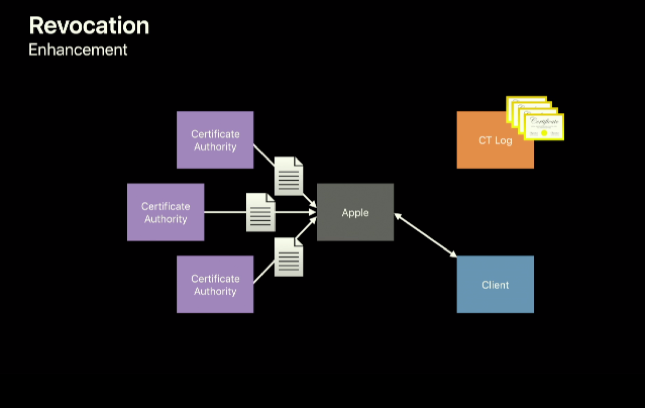
Apple’s method starts by scanning Certificate Transparency logs to discover certificates trusted on their platforms. It then queries the revocation status of discovered certificates from the Certificate Authorities. All the information about revoked certificates is bundled together and automatically distributed to client devices (like Macbooks and iPhones) silently and at regular intervals.
When a TLS connection is made, the client checks to see if the certificates is marked as revoked in the centralized list. If it is marked as revoked, the client will then perform a live OCSP check to confirm that is accurate. Once confirmed, the client understands the certificate is revoked and refuses to make a connection. If the server provides a stapled OCSP response, it will use that as confirmation instead of performing the live check.
If the certificate is not marked as revoked by the centralized list, then OCSP is not used.
Ditching OpenSSL For LibreSSL
In High Sierra, Apple has switched SSL libraries from OpenSSL 0.9.8zh to LibreSSL 2.2.7. LibreSSL is a fork of OpenSSL supported by OpenBSD.
Secure Transport is Apple’s own API for SSL/TLS but it is primarily used for their first-party software. LibreSSL will serve as the SSL library for third-party software.
This was not included in any WWDC sessions but has been observed by High Sierra beta users.
Expanded ATS Exemptions
Chris Wood, Secure Transports Engineer at Apple talked about the adoption and use of App Transport Security (ATS). Wood explained that Apple is expanding support for ATS exemptions after receiving developer feedback that transitioning was taking longer than expected.
Wood noted that Apple is still fully committed to HTTPS via ATS and that developers reliance on these exemptions should be temporary while they work on a proper transition to HTTPS.
New Apple OSes will now support ATS exemptions for the following frameworks: AVFoundation, WebView, and Webkit. Exemptions will also be configurable for local network connections (IP addresses and unqualified hostnames).
Exemptions can be scoped to a specific domain name, or for the entire app. There will also be a way to indicate if you want to have a hostname’s certificate checked for Certificate Transparency compliance.
TLS 1.3 Beta
The latest version of TLS, version 1.3, has not yet been finalized by the IETF. High Sierra and iOS 11 support a draft specification for TLS 1.3, which will be very similar to its final form. This allows developers to begin testing TLS 1.3 ahead of its official finalization.
Chris Wood highlighted the faster handshake time of TLS 1.3. He shared Apple analytics which found that 10% of TLS connections made over cellular connection take 800ms or longer, and on Wifi 10% of connections took 500ms or longer. With TLS 1.3’s more efficient handshake that time can be reduced by a third.
You can enable TLS 1.3 on iOS 11 by downloading and installing a profile from this link (Apple Developer account required).
The TLS 1.3 draft can be enabled on macOS High Sierra with the following terminal command:
defaults write /Library/Preferences/com.apple.networkd tcp_connect_enable_tls13 1
Ending Support for SHA-1 and <2048-bit Private Keys
Apple’s platforms are catching up with industry-standard deprecations of aging hashing algorithms and cryptography.
Certificates signed with SHA-1 and/or using private keys under 2048-bits will no longer be trusted on High Sierra, iOS 11, watchOS 4, or tvOS 11.
There will be some exemptions to this change. Certificates distributed through Mobile Device Management (MDM), or by the user through Safari, Mail, or Keychain Access can continue to use these weak hashes and keys. Client certificates (used in mutual authentication) are also unaffected.
SHA-1 signed root certificates are also not affected as signature verification works differently for these certificates. Roots using <2048-bit keys have already been removed from Apple platforms in 2015.
These requirements should not cause any concern for those using modern, CA-signed certificates. SSL industry standards have forbidden these weak practices for some time.
Developers will be able to identify this problem by a unique error code: “InvalidCertChain (-9807).” This will be returned in URLSession / URLConnection. Because Apple is totally dropping support in these cases, the only way to resolve the error is to replace your certificate.
Future Removal Of RC4 and 3-DES
Bailey Basile, Secure Transports Engineer, noted that two aging cipher algorithms, RC4 and 3-DES, would be removed from Apple platforms “in the future.” No specific date was given but developers should begin migrating away from these ciphers which have been known to be weak for quite some time.
Basile also recommended avoiding AES in CBC mode (AES-CBC). The recommended ciphersuites are AES-GCM or ChaCha20-Poly1305.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown