1/3 of Government Email Domains Miss DMARC Deadline
The deadline for implementing Domain-Based Message Authentication, Reporting and Conformance was Tuesday.
The deadline for federal email domains to implement DMARC was on Tuesday and just over two-thirds managed to do it. That leaves around 33% of federal email domains vulnerable past the DHS’ deadline according to the Global Cyber Alliance.
This comes amid a year of staggered deadlines for DMARC implementation. DMARC helps to verify that the identity of an email’s sender in an effort to stop spoofing.
The 67 percent of government domains that made the Tuesday deadline, is a major jump from 8 percent that had DMARC installed when Homeland Security first issued that order, the department’s Deputy Assistant Secretary for Cyber Policy Tom McDermott noted during an event sponsored by the Global Cyber Alliance and the Cybersecurity Tech Accord.
So that’s progress, but it’s hardly the complete implementation the Department of Homeland Security, which oversees cybersecurity for the federal government, had hoped for.
 What is DMARC and why does this matter?
What is DMARC and why does this matter?
Let’s hash it out…
What is DMARC?
DMARC or Domain-Based Message Authentication, Reporting and Conformance is a system for email validation purpose-made to detect and prevent email spoofing. Our resident IT expert, Ross Thomas actually covered this during his series on email security:
Now that we’ve covered everything else, we’ll take a look into the master sword, the infinity gauntlet, the one ring of email security that binds some security pieces together to form DMARC (Domain-Based Message Authentication, Reporting and Conformance). DMARC utilizes DKIM and SPF (which are previous article topics) to report on how the email domain is doing: compliance, alignment, failures, etc.
To illustrate this point, Ross also tossed in this graphic from Agari:
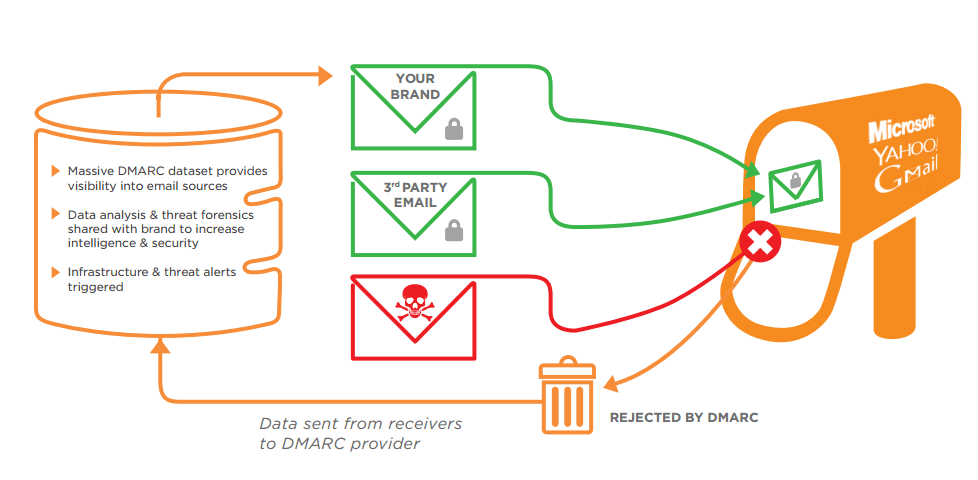
I really recommend you read the whole article, but that should be sufficient.
Now let’s talk about why this matters.
Why is DMARC important?
Obviously, being able to snuff out spoof emails would be important for any company or organization, but for the federal government it can be a matter of national security. Granted, a number of things would have to also go wrong for it to get that far, but you need only look back to the plight of John Podesta, the chairman of the ’16 Clinton Presidential Campaign, as well as the DNC to see how much damage a spoofed email can do.
Now, neither of those attacks took place on federal domains, so this deadline wouldn’t have helped them one bit. But still, a cautionary tale does it make.
From the standpoint of the business or organization you’re with, there’s no shortage of anecdotal evidence as to why you should be adding systems like DMARC to your own email domains, as well as using digital certificates to help with email validation. Keep in mind:
- 1 out of every 101 emails sent is malicious
- 70% of US employees don’t know email security best practices
- Criminals use LinkedIn to tailor emails to their targets
- These emails are socially engineered to create a sense of urgency
- To aid these campaigns, 1.4 million phishing sites are created per month
- In 2018 Cybercrime will cost over 1.5 Trillion
Are you doing enough to protect your company’s email? The point here isn’t to scare you, it’s to reinforce that you’re potentially opening yourself and your employees up to legitimate risks if you aren’t doing enough.
As always, leave any comments or questions below.
Check out the rest of Ross’s Hashed Out Email Security Series:
- Email Security – Part 1: Certificate Signed Emails
- Email Security – Part 2: Phishing and Other Falseness
- Email Security – Part 3: Sender Policy Framework (SPF)
- Email Security – Part 4: DKIM (DomainKeys Identified Mail)
- Email Security – Part 5: DMARC, Reporting and Email
- Email Security – Bonus: S/Mime Certificates for Apple Users






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown