SSL Certificate Validity Will Be Limited to One Year by Apple’s Safari Browser
Starting Sept. 1, Safari will no longer trust SSL/TLS certificates with validity periods longer than 398 days
Starting Sept. 1, Apple’s Safari browser will no longer trust SSL/TLS leaf certificates with validity of more than 398 days. (This is the equivalent of a one-year certificate plus the renewal grace period.) Other types of SSL/TLS certs, including intermediates and roots, are unaffected.
Apple announced their unilateral decision at a face-to-face meeting of the CA/Browser Forum (CA/B Forum) on Feb. 19, which is the industry standards group that consists primarily of certificate authorities and several of the major browsers.
While there’s been no formal posting anywhere that we’ve found by Apple about this change, we were able to verify this information with some of our CA partners who were in the meeting. The good news is that this change doesn’t really come as a surprise, and the SSL industry is ready for it — so there won’t be any major impacts to customers or service providers.
So, what exactly has transpired here? And, more importantly, what does this all mean for you, the user or seller of SSL/TLS certificates?
Let’s hash it out.
Is Shorter Validity a Good Thing?
We knew it was only a matter of time before this type of initiative would occur. Last year, we wrote on how one-year certificate validity was back on the ballot of the CA/B Forum. The idea here is that the shorter an SSL/TLS leaf certificate’s validity period, the more secure the certificate is.
That’s the argument that’s been made for several years for why browsers wanted to cap the maximum validity for SSL/TLS certificates to 1 year. The theory is that by requiring SSL/TLS certificates to be renewed after a shorter period:
- When any security updates to certificates are made, they roll out into the wild more quickly.
- It also theoretically makes websites more secure by ensuring that new keys are being generated regularly.
SSL/TLS leaf certificates used to have a maximum validity of five years (for domain and organization validated certificates). However, a compromise was ultimately struck that led to certificate validity being reduced to a maximum of three years, and then later, it was capped at two years for all SSL/TLS leaf certs.
Last year, Google’s Ryan Sleevi introduced a ballot at the CA/B Forum that pushed for a maximum one-year validity for SSL/TLS certificates. The initiative ultimately failed, but it looks like Apple has picked up where Google left off in the fight for shorter validity.
Today, Tim Callan at Sectigo posted the following on his LinkedIn page:
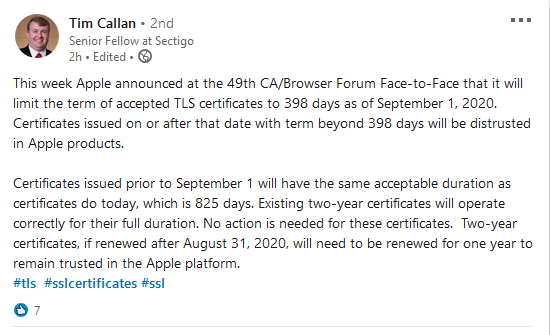
Honestly, we knew it was only a matter of time before this move would be made. We just figured it would have been Google or Mozilla making the first move. But, regardless of who made the first move, there are a few things you should know.
What Does This Mean for Your Website and Customers?
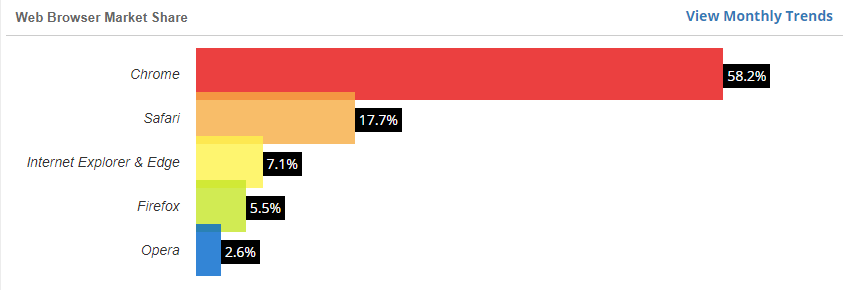
Safari is one of the internet’s two leading web browsers. W3Counter lists Safari’s browser market share at 17.7% as of January 2020. This falls behind only Google Chrome (58.2%) and ahead of Microsoft Internet Explorer and Edge (7.1%). So, as you can imagine, you want to ensure that your website — and your customers’ websites — are trusted by Safari.
What Site Admins Need to Know
Essentially, any SSL/TLS certificates issued prior to Sept. 1, 2020 are not affected by this change. They’ll remain valid (barring any unrelated certificate revocations) for the entire two-year period and won’t need to be modified or replaced. However, any certificates that are issued on or after Sept. 1 will need to be renewed every year to remain trusted by Safari.
What this means is that you’ll want to streamline and improve your existing certificate management practices. For larger organizations, in part, this entails using a reliable certificate management solution and no longer relying on manual cert management.
What Certificate Resellers Need to Know
In a nutshell, you can continue issuing two-year certificates until Aug. 31, 2020 that your customers can use until they expire. Any certificates that you issue after that date, however, would need to be issued with one-year validity to remain valid as far as Safari is concerned.
This means that any two-year certificates that you sell will need to be re-issued after one year in order to continue being trusted by the browser.
A New Option: Multi-Year Subscription SSL
Luckily for you, the leading CAs saw the writing on the wall. They decided to create new certificate lifecycle automation options and subscription plans that would make certificate management easier for shorter certificate lifecycles.
Some CAs announced a new option for purchasing/implementing SSL. Sectigo rolled out their SSL subscription plan months ago and DigiCert will roll out their multi-year plans before September. With these multi-year subscription-based SSL services, webmasters can purchase coverage for longer periods and reissue their certificate as often as they need with the maximum allowed validity period.
There are a few benefits to this option:
- Cost: It allows customers to continue receiving a multi-year pricing discount, which saves money, and
- Time: Customers only have to purchase the subscription once and not worry about it again for five years (especially useful if you need to get purchases approved by your accounting department).
So, basically, customers can purchase SSL coverage for an extended time period (for example, 5 years) and then just re-issue their certificate each year to update it —while saving money and time. That sounds like a win-win for everyone.
What’s Next
It was only a matter of time before we’d see this type of push for one year certificate validity by one of the browsers. Once one browser makes the move, it means that all of the CAs will change their certificates from two years to one year regardless of what the other browsers do.
We’re not worried and you shouldn’t be, either. This move by Apple won’t leave you stranded as a customer or reseller because the CAs have already put solutions in place that will help. With SSL subscription plans and certificate management solutions available, it’ll be a pretty straightforward transition that, hopefully, will have the intended effect — greater website security and improved certificate management.
As always, leave any comments or questions below…





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown