What Is SOC2 Compliance & How Does It Affect Your Business?
How SOC 2 reports can help cloud service providers stand out from the competition (and make your customers feel more confident in your ability to protect their data)

While we can all appreciate the humor of this comic, it’s scary how many organizations have this type of mindset when it comes to the security, privacy, and confidentiality of their cloud-stored data. This is where SOC 2 compliance audits and reports really come in handy.
But what is SOC 2 compliance? SOC2 compliance is an essential component of information security for many businesses and organizations. This rings especially true for those that are third-party service providers such as cloud storage, web hosting, and software-as-a-service (SaaS) companies… Or, really, any organization that stores its customer data in the cloud. As you can imagine, that expands the list a lot.
Basically, SOC 2 audits and reports help service providers show that the privacy, confidentiality and integrity of the data they handle — meaning their customers’ or their customers’ users’ data — is a priority. While it’s not saying that they’re 100% secure as organizations as a whole, it shows that they’re ahead of their competitors who lack these reports. This helps their customers understand that those vendors are doing what they should be doing to keep said data secure in the cloud.
So, when we talk about SOC2 compliance, what exactly does that mean? And why is having an SOC 2 report so important to your customers? And who actually performs these examinations and creates the reports that organizations worldwide trust?
Let’s hash it out.
What Is SOC 2? A Look at What SOC2 Compliance Entails…
Feeling a little lost? You’re not alone (hence why we wrote this article). In a nutshell, SOC2 (commonly pronounced “sock 2”) stands for the second of three System and Organization Controls (SOC) audits and reports that are integral to information security. The SOCs are a set of compliance standards that were developed by the American Institute of CPAs (AICPA), a member network of more than 430,000 CPAs around the world.
SOC audits are designed to examine the policies, procedures, and internal controls of an organizations. Testing and reporting on these controls are important because they impact the security, privacy, and confidentiality of an entity’s sensitive data. Every audit is conducted in accordance with the AIPCA audit guide and Attestation Standards Section 101 more commonly known as AT Section 101).
SOC audits are what draws the lines that service providers need to color within regarding data privacy, security, and integrity. It’s about showing customers and potential customers that you know what you’re doing and are taking the appropriate steps to ensure their data is secure with you.
The Three Types of SOC Reports
So, what are the three types of SOC reporting options for service organizations? They include:
- SOC 1 —This is designed for reporting on the processes and controls that influence an organization’s internal control over financial reporting (ICFR). Essentially, the choices you make as a service organization may affect the financial reporting of your users’ organizations.
- SOC 2 — This report is designed for service organizations and reports on non-financial reporting controls and focuses on five key trust services criteria (formerly called trust services principles), or TSCs as they’re more commonly known (which we’ll discuss more in depth momentarily). Basically, the goal here is to help outline the standards that are necessary to keep sensitive data private and secure while it’s in transit or at rest.
- SOC 3 — The third type of SOC report is akin to the second in terms of the reporting criteria – the difference between the two boils down to how the info is reported. SOC 2 is tailored for specific organizations, whereas SOC 3 reports are more applicable for general audiences (the public).
There are also technically SOC reports for cybersecurity and the supply chain as well, but we won’t get into all of that today. Just know that there are several key differences between an SOC for cybersecurity report (which, essentially, is an examination of an organization’s cybersecurity risk management program) and an SOC 2 engagement report. KirkPatrickPrice reports that those differences relate to subject matter, purpose and use, audience, and report types.
There are specific standards that apply to all types of SOC reports — these are known as the Statement on Standards for Attestation Engagements (SSAE), which is currently at version No. 18. This auditing standard is basically the successor of the now-deprecated SSAE No. 16 auditing standard, which used to only apply to SOC 1 reports.
How SOC 2 and SOC 1 Differ, and Why SOC 2 Compliance Matters to Your Organization
The SOC 2 standards, in particular, focus on the non-financial reporting on the internal controls and systems that you can implement to protect the confidentiality and privacy of data that’s stored in cloud environments.
Basically, these controls are a specific set of policies and procedures that help to ensure the security of any sensitive information that the third-party service providers are responsible for protecting. This differs from a SOC 1 examination, which focuses on financial reporting. Basically, this type of report is created by auditors, for auditors.
Well, considering your organization has to adhere to specific data security standards (think: CCPA, GDPR, FIPS, PCI DSS, HIPAA, etc.), then you should be able to expect that any third-party organizations you’re contracted with to store or process your data online does the same… right?
If you believe that, then I have a bridge or two to sell you… and possibly a unicorn.
Unfortunately, not all service providers are stringent about protecting their own data. If your data isn’t properly handled, it can leave you vulnerable to various security issues, including:
- Data theft, breaches and leaks — Considering that Risk Based Security reported that more than 15 billion records were exposed in 2019 due to data breaches, this is a critical issue.
- Malware and ransomware attacks — Ransomware were a very costly issue for key organizations and institutions around the U.S. last year. Emsisoft reports that ransomware attacks cost a cool $7.9 billion to healthcare providers, government organizations, and educational institutions in 2019 alone.
- Reputational damage and related losses — Loss of trust, for any reason, deals a major blow to an organization. When it’s the result of cyber security events that could have been avoided by implementing security measures, it’s a double whammy.
So, if they’re not stringent in their own practices, why would you expect them to put in the effort to protect your data? This is where the five trust services criteria of an SOC 2 examination come into play.
So, What Are the Trust Services Criteria of SOC 2?

As you now know, an SOC 2 examination is a way for you to ensure that a third-party service provider is doing what they’re supposed to do to protect and secure your customers’ data. This provides you with some security assurance by knowing that a reputable third party (in this case, a licensed CPA) has evaluated the service provider’s policies, controls and procedures to mitigate or identify potential risks based on five specific trust services criteria (TSCs):
These reporting options are outlined in the AICPA’s TSP 100 2017 Trust Services Criteria for Security, Availability, Processing Integrity, Confidentiality, and Privacy):
1. Security
This section of the trust service criteria is included in all SOC audits. It focuses on the common criteria (CC) within the principles of the SOC 2 audit report that relate to protecting the data and systems that are used to collect or create, store, use, process, or transmit data. (We’ll talk about those CCs after we finish up with the TSCs.)
According to the AICPA’s 2017 Trust Services guide, the security TSC is all about ensuring that:
“Information and systems are protected against unauthorized access, unauthorized disclosure of information, and damage to systems that could compromise the availability, integrity, confidentiality, and privacy of information or systems and affect the entity’s ability to achieve its objectives.”
Here at Hashed Out, we always harp on the importance of data security and integrity. So, we’re happy to see that security is number one on the AICPA’s list as well because, well, it’s just that important!
Some examples of tools and policies that could fall under this category include:
- Intrusion detection and intrusion detection systems (IDS)
- Firewalls and other network and application security measures
- Multi factor authentication tools and potentially client certificates
- Penetration tests and vulnerability assessments
- Implementing computer use policies
- Digital and physical access controls
There is one important thing we’d like to note: The security category is one that applies to all engagements, whereas the other four categories don’t necessarily have to be covered in the report. (Basically, you can report on just security if you want, or you can choose to report on security + any of the other options that we’ll talk about shortly.)
Some organizations opt to be thorough and include all five, whereas others only include the criteria that they believe are most applicable to them. Really, the choice is up to you for how you want to proceed.
2. Availability
This TSC category is all about accessibility — how readily available the data is to both an entity’s systems and to the products or services its customers receive. During this part of the audit, a licensed CPA examines the systems’ controls to see whether they support such accessibility for operation, monitoring, and maintenance and to help the organization achieve its objectives.
Some examples of tools, processes and policies that would fall under this category include:
- Disaster response and recovery
- Secure data backups
- Performance and incident monitoring and response
3. Processing Integrity
Well, this category is kind of self-explanatory. But let’s go ahead and break it down anyway. It’s commonly understood that businesses and organizations want to know that their customers’ data isn’t being compromised or manipulated in any way during processing. So, if they’re working with a third-party service provider, this part of the trust services criteria helps them to ensure that the accuracy, completeness, validity, and timeliness of the data is there and that the provider’s systems are processing the data as authorized.
Ultimately, the focus here is to address whether an entity’s systems are able to achieve their goals or purposes for which they were designed. So, this part of the audit process assesses whether the systems demonstrate any delays, omissions, errors, or manipulations (inadvertent or unauthorized) in the processing. But that doesn’t necessarily mean that the data is free of errors that are caused by erroneous data entry, however, of course — that’s a data integrity issue, which is a separate concern.
Some examples of processes and policies that would fall under this category include process monitoring and quality assurance (QA) processes.
4. Confidentiality
This category of the five trust services criteria aims to demonstrate that any “confidential” data remains protected and secure. This includes a variety of types of information… everything from an entity’s personal information to their intellectual property.
Encryption, such the in-transit data security offered by SSL/TLS certificates and email signing certificates (aka client certificates and personal authentication certificates), is essential.
Some tools and processes that would be particularly useful for protecting data include:
- Digital and physical access controls
- Network and application firewalls
- Cryptographic solutions
5. Privacy
Wait, aren’t confidentiality and privacy the same thing? Nope. The confidentiality TSC applies to various categories of sensitive information, whereas privacy applies only to personally identifiable information (PII) that includes (but isn’t limited to):
- First and last names
- Social security numbers (or other similar identifiers)
- Addresses and contact information
The AICPA outlines privacy criteria in its guide as:
- Notice and communication of objectives
- Choice and consent
- Collection
- Use, retention, and disposal
- Access
- Disclosure and notification
- Quality
- Monitoring and enforcement
To qualify for SOC 2 compliance in this area, an organization must demonstrate that they protect and handle personal information securely. This particular reporting option relates to how data is collected, used, disclosed, retained, and disposed of as part of how an entity performs its job.
Some important tools, processes and policies that could be useful for SOC 2 compliance include:
- Encryption
- Access controls
- Privacy and disclosure notifications
- Secure disposal processes
About Those Common Criteria We Mentioned Earlier…
Did you know that the five trust services criteria are only one part of the TSP? There’s actually a second component to consider — basically, that each of the five SOC 2 common criteria are comprised of nine specific sub-categories:
- Control environment (CC1)
- Communication and information (CC2)
- Risk assessment (CC3)
- Monitoring of controls (CC4)
- Control activities related to the design and implementation of controls (CC5)
- Logical and physical access controls (CC6)
- System operations (CC7)
- Change management (CC8)
- Risk mitigation (CC9)
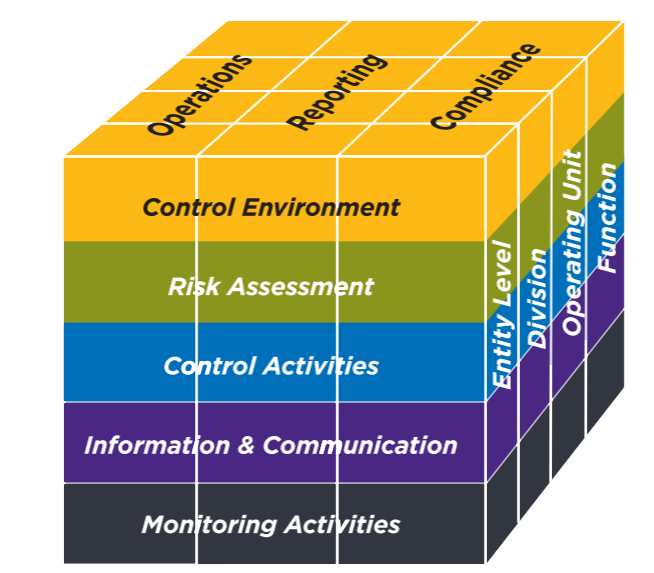
The first five common criteria categories correspond to the first five that are outlined in the 2013 COSO Framework, which is composed of 17 principles. (Note: The 2013 COSO Framework is still in use as part of the 2017 TSC standards.) The remaining four supplemental criteria categories are outlined in TSP Section 100.05 as additional criteria that supplement COSO principle 12.
There are also additional specific criteria for the remaining four TSP categories that are covered in TSP Section 100.07.
So, What Are the 17 SOCO Principles?
The 17 SOCO principles are as follows (note: these are written verbatim from the AICPA 2017 TSP Section 100 document):
Principle 1: The entity demonstrates a commitment to integrity and ethical values.
Principle 2: The board of directors demonstrates independence from management and exercises oversight of the development and performance of internal control.
Principle 3: Management establishes, with board oversight, structures, reporting lines, and appropriate authorities and responsibilities in the pursuit of objectives.
Principle 4: The entity demonstrates a commitment to attract, develop, and retain competent individuals in alignment with objectives.
Principle 5: The entity holds individuals accountable for their internal control responsibilities in the pursuit of objectives.
Principle 6: The entity specifies objectives with sufficient clarity to enable the identification and assessment of risks relating to objectives.
Principle 7: The entity identifies risks to the achievement of its objectives across the entity and analyzes risks as a basis for determining how the risks should be managed.
Principle 8: The entity considers the potential for fraud in assessing risks to the achievement of objectives.
Principle 9: The entity identifies and assesses changes that could significantly impact the system of internal control.
Principle 10: The entity selects and develops control activities that contribute to the mitigation of risks to the achievement of objectives to acceptable levels.
Principle 11: The entity also selects and develops general control activities over technology to support the achievement of objectives.
Principle 12: The entity deploys control activities through policies that establish what is expected and in procedures that put policies into action.
Principle 13: The entity obtains or generates and uses relevant, quality information to support the functioning of internal control.
Principle 14: The entity internally communicates information, including objectives and responsibilities for internal control, necessary to support the functioning of internal control.
Principle 15: The entity communicates with external parties regarding matters affecting the functioning of internal control.
Principle 16: The entity selects, develops, and performs ongoing and/or separate evaluations to ascertain whether the components of internal control are present and functioning.
Principle 17: The entity evaluates and communicates internal control deficiencies in a timely manner to those parties responsible for taking corrective action, including senior management and the board of directors, as appropriate.
The Two Types of SOC 2 Reports
If you’re like most people, who’ve at least heard of the SOC 2 report. But what you may not know is that there are actually two types of SOC 2 reports: report 1 and report 2. Both reports aim to provide detailed info and assurance about the controls and system an organization uses to process and secure users’ data and protect their privacy. Just how they go about doing so — and what each report focuses on specifically — differs from one report to the next, and part of that difference boils down to time.
Let’s explore these two reports a little more to better understand SOC2 compliance:
- SOC 2 type 1 report — According to the AICPA, this report is the “management’s description of a service organization’s system and the suitability of the design and operating effectiveness of controls.” This report evaluates the controls at a specific point in time.
- SOC 2 type 2 report — This report takes the first a step further and focuses not just on the description and design of the controls, but it actually involves evaluating the operational effectiveness of them. Furthermore, this doesn’t happen over a week or two — the evaluating CPA writes this report over an extended period of time to ensure the effectiveness of the controls (potentially taking several months).
Jacob Nemetz, CEO of Dash Solutions, which provides solutions for security compliance in the public cloud, emphasizes the importance of businesses having a SOC report.
“Generally, a service organization should look at getting a SOC report every year to ensure that there is continuous coverage by the SOC 2 reports. Coverage issues could lead to further security scrutiny by partners or clients.”
— Jacob Nemetz, CEO, Dash Solutions
How You Can Get a SOC 2 Compliance Report
Only a licensed CPA firm can provide one of these reports. Why? Because the AICPA requires that SOC audits and reports are performed only by independent, licensed CPAs. From the beginning to the end of the auditing and reporting process, you’re required to hire the services of a certified CPA or CPA firm.
So, this means that while you might have a great working relationship with your non-CPA bookkeeper Sue, if she isn’t a certified public accountant, then she can’t perform your SOC 2 audit. That’s just the way it is.
Organizations should engage with a reputable SOC 2 audit firm and can expect to deal with the following when going through a SOC 2 audit:
- Security Questionnaires — Service organizations will most likely be provided with a set of questions around your team’s security program, policies and implemented security controls.
- Documentation and Evidence Collection — Teams may be asked to provide evidence of effective controls within the organization. Teams will want to provide current policies and proof that technical security controls are currently in place.
- Security Evaluation — An auditor may ask for additional evidence or information around internal controls. Teams with SOC 2 compliance gaps may be asked to update their security program and resolve security issues before receiving a report.
- Report Creation — After an auditor has successfully evaluated your internal controls, they will write up and provide a SOC 2 report for your organization.
While an audit firm may work with your organizations to ensure that security controls are current, teams should have certain internal controls and documentation in place to simplify the compliance process.
“Teams that are unprepared for a SOC 2 audit often face a longer assessment process, additional scrutiny, and higher overall costs. Teams should prepare security controls and collect all relevant evidence to streamline the audit process.”
— Jacob Nemetz, CEO, Dash Solutions
To learn more about what SOC 2 compliance entails, what’s involved in the auditing and reporting processes, and just about SOC in general, reach out to a licensed CPA who handles SOC reports. While we’re here to provide you with insights, we’re not licensed CPAs, so be sure to check with the experts!
Final Thoughts on SOC 2 Compliance (TL;DR for You Skimmers)
Yeah, we know all of that was a lot to take in, but we hope this article answered all of your questions relating to the questions “what is SOC 2?” or “what is SOC 2 compliance?” That’s also why we’d like to include a little summary of what we talked about for those of you who prefer to skim instead of read content:
- SOC 2 is one type of three types of System and Organization Controls audits and reports that are integral to information security.
- They’re useful for providing information about specific entities regarding how they handle and store sensitive or private data in the cloud.
- SOC 2 reports can contain one or more trust services criteria, but always include security:
- Security,
- Availability,
- Processing integrity,
- Confidentiality, and
- Privacy.
- There are common criteria for the TSCs:
- Control environment (CC1)
- Information and Communications (CC2)
- Risk management (CC3)
- Monitoring of Activities (CC4)
- Control activities (CC5)
- Logical and physical access controls (CC6)
- System operations (CC7)
- Change management (CC8)
- Risk management (CC9)
- There are 17 SOCO principles
- Only licensed CPAs can evaluate whether your organization meets SOC2 compliance standards.
If you’re a service provider or other organization that stores customer data in the cloud, regardless of whether you choose to report on just the security trust services criteria or all five TSCs, it’s important that you embrace SOC 2 audits and reports. After all, this type of report tells organizations — your prospective customers — that you’re serious about protecting their data. So, why not give them that security assurance by proving that your business stands head-and-shoulders above the competition?
SOC 2 compliance is about showing organizations that you’re competent and are taking steps to ensure your customers’ data is secure. Unlike what the comic suggested at the beginning, you’re not an organization that depends on sheer luck, disorganization, or other unreliable factors to protect their data in the cloud.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown