Breach and Attack Simulations: How to Find the Gaps in Your Cyber Defenses
Over $1 trillion dollars is expected to be spent cumulatively on information security by 2025, according to Research and Markets
As staggering as this estimate from Research and Markets may seem, it shouldn’t come as a big surprise since cyber attacks have become so rampant that they’re now considered a global threat. Companies are scrambling to adopt various security solutions to mitigate the various attack methods that hackers now employ.
Some business leaders think that the more tools they deploy, the better protected they are. However, they often overlook the need to test whether their deployed solutions actually work or if their defensive perimeters have any gaps that attackers can exploit. The stark reality is that it only takes a single vulnerability for hackers to infiltrate your network.
Fortunately, checking your defenses is now possible through a variety of testing methods. You can perform vulnerability scans, penetration tests, deploy red and blue teams, and perform breach and attack simulations (BAS). The first two methods are great, but they have limitations. This is why the use of BAS technologies is emerging as the popular approach to testing.
But what is BAS? How exactly do BAS platforms work and how can they help uncover gaps in your cyber defenses?
Let’s hash it out.
Why Do Gaps in Security Exist?
Simply put, there’s no perfect technology. Software including operating systems, applications, and even security solutions often contain bugs that can be exploited by attackers. Since software applications continually receive changes and updates, there’s always a possibility that flaws will be introduced to your network.
In addition, poor implementation is another risk. It’s common for some organizations and IT teams to rush their adoption of security tools. In doing so, it’s possible that certain steps or configurations may be overlooked when setting up security solutions. Even the most expensive top-of-the-line solutions may be rendered useless if badly deployed.
For example, you may have the most stringent firewall policies in place to prevent hackers from breaching your network from the outside. However, if your endpoint protection is lacking, it’s possible for malware to still find its way into your network. For example, if a careless staff member inserts an infected USB thumb drive into a workstation, malware can easily spread from there.
Cybersecurity Vulnerabilities: How We Typically Find Gaps
To find these gaps, it’s crucial to regularly test your defenses by going on the offensive on your own networks. Conventionally, this is done through the following security validation methods:
- Vulnerability Scanning. You can use vulnerability scanners to identify the various vulnerabilities across your infrastructure components. They can check for outdated software, open ports, and expired certificates found across your network.
- Penetration Testing. With penetration tests, testers look to see how far they can go in breaching your network by employing similar tactics used by real-world hackers.
- Red and Blue Teaming. This is like war games played on your infrastructure. The red team plays the role of hackers by trying to breach your system. The blue team acts in your defense by preventing the success of the red team’s attack.
These methods, however, have limitations. Reports from vulnerability scans often simply list found vulnerabilities, leaving you to figure out what action is needed to remedy the issues. Furthermore, they can also produce false positives and flag certain issues that might not have much impact to security.
However, penetration tests and red team are resource-intensive activities. While penetration testing tools such as Metasploit and Kali are free, tests still have to be carried out by highly-skilled security professionals. The effectiveness of these tests is largely dependent on the skills of those individuals. A single network penetration test can easily cost $5,000 — and that estimate is on the low end of the ballpark. Needless to say, routinely performing such tests can be quite expensive, especially if you have a limited security budget.
What Are Breach and Attack Simulations (BAS)?
According to Cymulate, BAS platforms simplify testing by allowing users to perform a variety of automated and customizable simulated attacks for a full security validation. Breach and attack simulations are a great way for enterprises and other large organizations to emulate and better understand real world cyber attacks. BAS technologies help organizations embrace automation in cybersecurity and allow organizations to perform consistent assessments while tying up fewer resources.
AlthoughBAS technologies have existed for many years, Gartner appears to have been the ones to coin the phrase in their report Hype Circle for Threat-Facing Technologies, 2017:
“Breach and attack simulation (BAS) technologies use agents and other means to simulate attacks against enterprise infrastructure. BAS can effectively emulate insider threats, lateral move or data exfiltration techniques without the risks to production environments inherent with other testing approaches.”
How BAS Works: An Overview
Breach and attack simulations look to improve upon traditional testing methods by making it easy for users to perform checks on their security controls easily and quickly. In a way, BAS can be viewed as the combination of vulnerability scanning and penetration testing packaged as a do-it-yourself solution.
BAS platforms are mostly available today as software-as-a-service (SaaS). These cloud-based applications host the variety of modules that carry out the tests automatically, unlike with penetration tests where actual human resources perform the hack attempts. With BAS, a software agent is typically installed on a computer that sits within the network and is responsible for interacting with the cloud solution during testing.
The simulated attacks technically use malware and hack tools that are specially configured to trigger and monitor responses from your security solutions. However, unlike malware from real-world cyber attacks, those used in BAS do no real damage to your infrastructure.
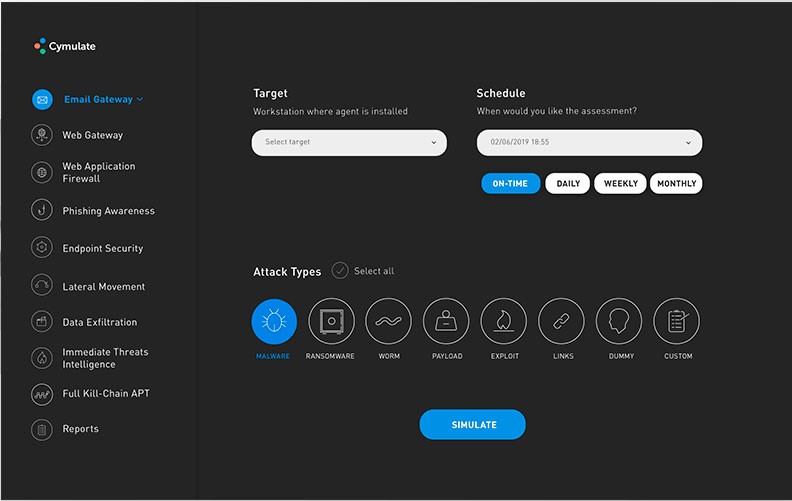
The Nitty-Gritty of Breach and Attack Simulations
Here are several ways BAS tests the various attack vectors and the solutions that protect them:
- Test Your Email Defenses. The breach and attack simulation platform sends a variety of messages to your email service that contain different types of infected file attachments (such as malware, ransomware, worms, and other payloads). This can test email filters, antivirus software, and sanitization solutions.
- Identify Gaps in Your Browser and Website Defenses. The platform connects to dummy websites and pages containing malicious forms and scripts via HTTP/HTTPS protocols. The tests can check what pages make it past internet security filters and if endpoint protection can prevent malicious files from being successfully downloaded by the browser.
- Check the Strength of Your Firewall(s). The platform can attack a specific URL (such as your company’s web portal or application) to find ways to circumvent the firewall that protects it. It tests whether the firewall can deter incoming malicious traffic. To take these attacks to the next level, BAS can also attempt to mine sensitive information and carry out cross-site scripting (XSS) and injection attacks to breach the firewall.
- Test Common Social Engineering Tactics. BAS can launch dummy phishing campaigns on your own email systems to emulate social engineering attacks. Phishing emails, which can be customized for authenticity, are sent to real users within your organization. The test checks if users will actually click on malicious links. This helps you to identify which staff members need more training in social engineering awareness.
- Test the Effectiveness of Endpoint Security Solutions. BAS platforms can check if malware — including viruses, ransomware, spyware, and worms — are able to exist and execute on workstations. They can also test and map out how malware can spread across your devices. This allows you to verify whether your solutions can detect and prevent the spread of malware within your network.
- Identify Potential Network Attack Vectors. BAS can also simulate scenarios in which an attacker successfully breaches your network. This simulation helps you see whether an attacker can move laterally across devices using exploits, privilege escalation, and pass the hash validation requirements. The platform can also test if data can be exfiltrated and sent to a destination outside the network.
Some BAS technologies draw from knowledge bases like MITRE ATT&CK as references to the many possible tactics and techniques that hackers can employ. This makes the simulated attacks as realistic as possible.
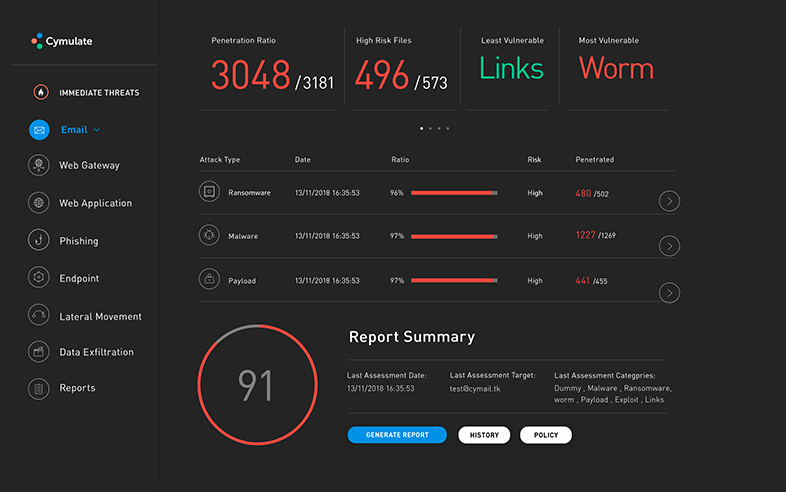
BAS Technology Features, Reports, and Recommendations
The test results from breach and attack simulations come in the form of comprehensive reports and scorecards that identify the gaps and vulnerabilities across your infrastructure components. They also provide information on how well or poorly your solutions perform against the simulated attack.
But rather than simply generating a list of vulnerabilities, the results offer recommendations on how to plug the gaps and strengthen your defenses.
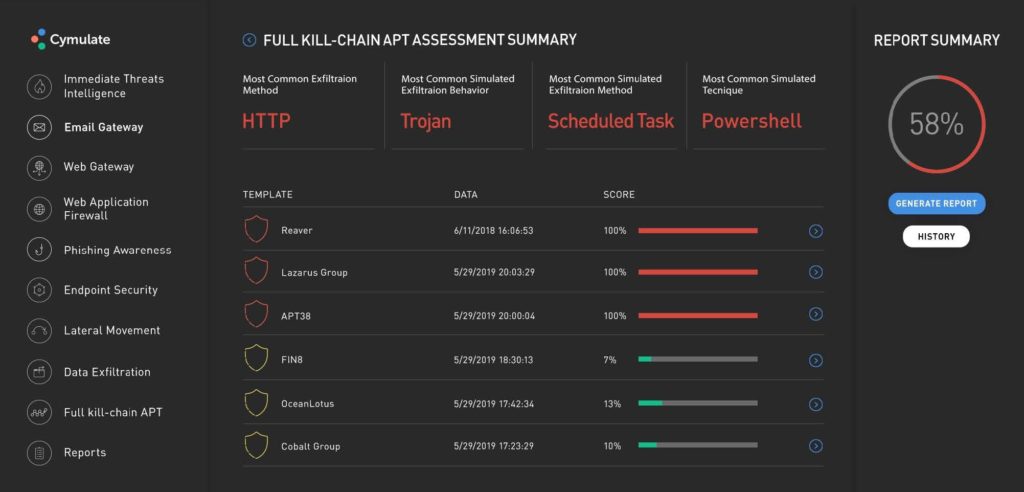
Sometimes, it’s nice to be able to “set it and forget it.” So, the fact that BAS platforms also allow tests to be scheduled helps you to ensure that important testing simulations isn’t a task that falls between the cracks. This way, you can periodically check if any of your security measures are failing or suffering from any faults and downtime.
Some tools even provide notification and alerts features that warn you of new and emerging vulnerabilities and threats. This way, you can stay informed about whether any of your components are affected.
The Advantages of Using BAS Within Your Organization
While BAS platforms essentially combine the capabilities of conventional cybersecurity testing and assessment methods, it holds several advantages over them. These advantages include:
- Comprehensiveness. While penetration tests and red teaming are often limited by the scope agreed upon with the testers, BAS allows for a wider range of tests to be performed across all potential vectors. BAS even scales up both methods as it allows for repeated and continuous testing, which is difficult to do through conventional methods.
- Actionability. Vulnerability scanning often simply lists found vulnerabilities, requiring you to sift through and make sense of information before you can actually do anything. BAS provides actionable insights in the reports so you’d be able to make more targeted adjustments to your security measures immediately.
- Timeliness. Penetration tests and red team exercises have to be coordinated and scheduled. With software and systems receiving daily updates, reports from these tests may quickly become outdated. Since BAS tests give quick results, they can give you a more accurate picture of your defenses.
- Convenience and Ease of Use. Many BAS platforms are intuitive, offering easy-to-use interfaces and dashboards. This means that you don’t have to be a highly skilled white hat hacker to see whether your defenses are vulnerable. Some services are available as cloud-based platforms, which allows you to run tests from basically anywhere.
- Cost-Effectiveness. Although not necessarily cheap, BAS allows multiple tests to be run both on-demand and on schedule. Penetration tests and red team exercises are tough to conduct on a whim, and doing them often comes with a big price tag. Running a penetration test, even on a monthly basis, can easily cost tens of thousands of dollars per year. BAS doesn’t have such limitations because it uses automated simulations.
It’s because of these advantages that many IT teams are now keen on using BAS instead. Adoption is expected to increase with the segment even projected to become worth $1.68 billion by 2027.
Final Thoughts on Breach and Attack Simulations
You must not be lulled into a false sense of security. Just because you bought “enterprise-grade” security solutions doesn’t mean that your defenses are impenetrable. Continuous testing is crucial to ensuring that your infrastructure is kept secure. Fortunately, BAS platforms are now available that allow you to perform timely and accurate tests without needing advanced technical expertise or a massive pentesting budget.
Using BAS to test your defenses would allow you to maximize your cybersecurity investments and ensure that you’re as protected as possible at all times.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown