Cyber Attack Prevention Can Save Businesses Up to $1.4M Per Attack
While that headline sounds great, research from a study by the Ponemon Institute and Deep Instinct shows that 76% of surveyed security professionals indicate that cyber attack prevention is too difficult for their organizations to achieve and instead focus on easier detection and containment efforts
It sounds like a bad joke: Why did the security department give up on their cyber attack prevention and mitigation efforts? Because prevention’s too hard to achieve.
Unfortunately, though, this is not just a bad joke. According to research from a new study that was released today by the Ponemon Institute and Deep Instinct, that’s exactly what more than three-quarters of survey respondents said they believe. The unsettling data indicates that 40% they “strongly agree” and another 36% said they “agree” with the statement that “My organization focuses on the detection of cyberattacks because prevention is perceived to be too difficult to achieve.”
We’re not here to argue the psychological semantics of perception versus reality — but we are saying that this data shows that perceptions relating to the cybersecurity lifecycle do matter (particularly where an organization’s resource allocation and budgetary decisions are concerned).
To better understand the data, we’re going to dive into the results of this survey, which focuses on the responses to questions relating to perceptions of the cybersecurity lifecycle and the economic value of prevention efforts.
Let’s hash it out.
Companies Are Focusing on Response Rather Than Cyber Attack Prevention — But That’s a Mistake…
The study takes a deep dive into the economic impact of costs associated with cyber attacks on organizations. But we’ll get more into who the survey respondents are later — let’s get to the meat of what they were asked about… The cybersecurity lifecycle itself and the ways that their organizations prevent cyber attacks.
The lifecycle represents a series of cybersecurity-related processes an organization goes through when identifying and responding to virtually any type of cyber attack. So, what are the five phases?
- Prevention — This first step focuses on stopping malicious threats and classifying threats in real time. This is the phase where respondents say they feel they’re least effective. Prevention is the tertiary consideration when it comes to budget allocation within the cyber security lifecycle (only 21% of the budget).
- Detection — This phase focuses on identifying threats that may already exist within an established IT security infrastructure. This is also where they place the second highest budget priority (26%) in terms of the cyber security lifecycle.
- Containment — This step kicks in and outlines how to stop an identified threat from spreading to other systems. This is where the majority of surveyed organizations say they’re most effective and successful. It’s also where the focus the majority (29%) of their cyber security lifecycle budget.
- Recovery — This phase focuses on restoring your IT security infrastructure to its previous condition once the threat has been contained.
- Remediation — This step focuses on ensuring that the right “everything” in place — the people, processes, and technologies — to thwart future incidents.
The survey asked participants to estimate the costs associated with five types of attacks — zero-day, phishing, nation-state, ransomware, and spyware — and the percentage of the cost that’s associated with each of those lifecycle phases. For example, their data shows that a single phishing attack could cost an average of $832,500 due to costs associated with detection, containment, recovery, and remediation efforts. But if an organization was able to prevent the attack in the first place, they could save $682,650 of those total costs!
Why only 82% — wouldn’t it prevent 100% of the costs of a cyber attack? Well, no. That’s because there are costs associated with cyber attack prevention initiatives in terms of the human and technological resources that are involved.
So, ask yourself: If there is a chance that you could potentially save your organization 82% of the costs it could face by preventing an attack from happening in the first place, would you put the necessary resources in place to do it? Where do you and your organization stand on this particular issue — are you in the camp that supports focusing more of your efforts on prevention, or do you believe more resources should be dedicated to detection and containment?
The Key Takeaway from the Survey: Put More Resources Into Cyber Attack Prevention
Unsurprisingly, the survey finds that preventing attacks from causing damage not only protects an organization’s reputation, but it also saves them time, resources, and money. That seems like pretty common sense to me. But what was surprising was the weight given to perceptions surrounding the topics of cyber attack detection and prevention. Herein lies the issue.
As we mentioned earlier, the majority of survey respondents’ cybersecurity resources appear to be devoted significantly more to responding to threats (containment) than stopping them from occurring in the first place (prevention). In fact, only 24% say that they focus on optimizing their prevention capabilities!
But what leads to such a big discrepancy in priorities?
Dr. Larry Ponemon, the chairman and founder of the Ponemon Institute, was quoted in the press release as saying that the reason seems to boil down to perceptions of accountability:
“This study shows that the majority of companies are more effective at containing cyberattacks after they happen because it is perceived to be more accountable. This explains why cybersecurity budgets focus on containing attacks rather than preventing them, as well as the increased rate of breaches despite investments in cybersecurity solutions.
Prevention of cyberattacks is perceived to be too difficult, but as companies continue to suffer revenue losses due to cyber breaches, we expect budgets to start allocating increased resources to preventative solutions given the amount of money they save.”
If you want to ensure that your budget money is best spent, then it’s imperative for businesses and organizations to dedicate more of their moolah to cyber attack prevention initiatives, personnel resources, and technologies. But even with increased resources, that doesn’t mean that your cyber security prevention efforts will be without challenges.
The Challenges of Preventing Cyber Attacks on Businesses
When it comes to figuring out how to prevent a cyber attack, it’s all about identifying and stopping any type of malicious threat in real time, regardless of the types of files that are used in the attack or if it’s a zero-footprint attack (one that lacks files).
The five types of cyber attacks we mentioned earlier — zero-day, phishing nation-state, ransomware, and spyware — were among those that the survey respondents found very difficult to prevent. According to the research, a few reasons really stand out about why almost 80% of the survey respondents feel like preventing these types of cyber attacks is too difficult:
- Their detection capabilities are lacking. By the time they recognize that an attack is taking place — whether it’s because of difficulties arising with detecting threats in various file types or due to a lack of real-time data — it’s already too late.
- There aren’t enough resources allocated to prevention. Simply put, they lack the necessary resources to prevent cyber attacks in terms of budgets, personnel, and expertise. In fact, only 40% of the practitioners who responded to the survey think their organization’s budgets are enough to create a strong cyber security posture.
- Current technologies can’t handle modern attacks. Whether it’s a matter of using outdated tech, tools that are too complex, or simply not having enough solutions at their disposal, these experts feel like they can’t prevent attacks in real time with their existing tech resources.
- Advanced technologies aren’t perceived as real solutions. As one of their three answers to a question about the challenges of deploying AI-based tech, half of the survey respondents indicate that adopting such solutions would meet internal resistance because people think its benefits aren’t real or are highly exaggerated.
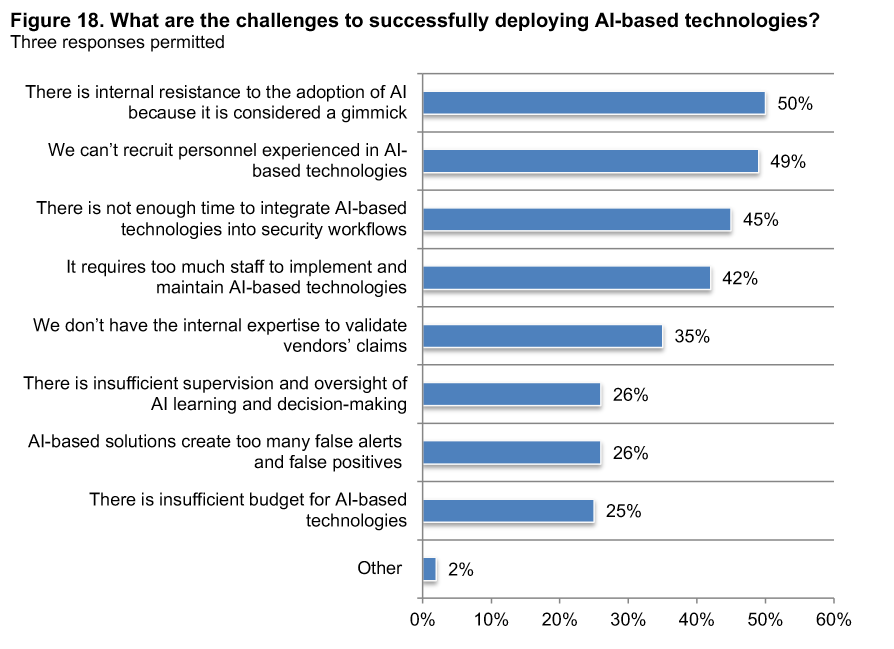
So, even if it is harder and more challenging to prevent attacks than to detect and contain them, it’s still worth the effort to do what you can to prevent them from happening. Having the right tools and technologies in place is especially useful and is among the best ways to prevent cyber attacks. Using encryption and authentication technologies, in addition to automation and AI, is definitely one of the best approaches and should be part of a larger cyber attack prevention strategy.
How PKI and Digital Certificates Help with Cyber Attack Prevention
Something that always interests us in these types of articles is where public key infrastructure (PKI) and encryption fall within the purview of necessity.
On a scale of 1-5, with 5 meaning very high impact and 1 meaning very low impact, public key infrastructure (PKI) has an impact score of 3.9 in terms of how well it helps to prevent cyber attacks. This tied PKI with privileged access management (PAM). This is behind only a few others:
- Intrusion detection / prevention (4.6)
- Incident & event management (SIEM) (4.4)
- Network traffic intelligence (4.2)
- User behavior activity monitoring (4.1)
- Access governance systems (4.1)
This means that while PKI isn’t the top contributing factor, it is one of the most valuable technologies that organizations are putting to use. Although this is something we already knew in terms of the importance of PKI, it’s nice to see what we proclaim being validated by other reputable organizations.
Digital certificate management also made the list with an impact rating of 3.6. We’ll get more to the importance of that momentary. But, first, let’s keep going with the benefits of having a well-established PKI and how it helps you prevent cybersecurity attacks.
Why PKI Is Useful in Preventing Cyber Attacks
Public key infrastructure is the framework, technologies, processes, and other integral components that are required for issuing, using, and managing public key encryption certificates. This infrastructure involves web browsers, certificate authorities (CAs), X.509 digital certificates, and their public/private keys.
But how does PKI play a role in preventing cyber attacks? Public key encryption does two things exceptionally well:
- It keeps bad guys out of your networks with certificate-based authentication. (It’s a lot easier for hackers to steal a password than it is for them to steal a certificate and private key!)
- It protects your data so hackers can’t mess with it (for example, to inject malware) or steal it. (This protects the integrity of your data.)
Digital Certificates Enable Organizations to Encrypt and Protect Files
When asked which types of solutions they currently use to prevent cyber attacks, encryption is one of the top solutions listed. Encryption is important and is already in use in various ways in many businesses around the globe. For example, data in transit encryption is used on many businesses’ website servers. Some businesses also use encryption to secure their IoT devices, email servers, and the email communications of specific users. However, it doesn’t appear to be as widespread as we’d like yet in terms of protecting mobile devices.
The survey data indicates that only 39% of organizations reportedly take steps to protect data on employees’ mobile devices. Of those respondents, 41% say their organizations use data in transit and at rest encryption to secure data both while it is stored and being transmitted.
This is definitely an area that can use some improvement. This is especially true considering that the survey respondents also indicate that more than half (54%) say their organizations allow them to use their personal mobile devices in the workplace and 41% say they use the devices for work purposes.
Email Security
When talking about email security, phishing is a major concern for every business. All it takes it for one email to be successful for all of your good intentions, resources, and hard work to go out the window.
The FBI’s 2019 Internet Crime Report also indicates that email is among the most common entry points for fraud. According to the Ponemon/Deep Instinct survey, 79% of the respondents indicate that their organizations experienced at least one phishing attack. Of those, only 18% said that they were able to prevent them.
Of course, this is where cyber awareness training and the use of digital signatures can really have an impact. For example, if your employees are aware of the threats that exist with regard to phishing emails and social engineering attacks, they’ll be less likely to fall for those types of scams.
However, if their organizations also implement the use of digital signatures via email signing certificates, it could help email recipients more easily verify whether an email came from a legitimate person or an imposter.
Digital Certificate Management
Managing your digital certificates is a critical task that must be done effectively. This means that you need to have strong visibility within your network and IT infrastructure to know what you have and whether it’s protected. Having unknown certificates (shadow IT) and expired certificates can lead to a variety of costly headaches for your team and your organization as a whole.
For example, outages that result from certificate expirations can cost organizations more than $11.1 million, according to research from another Ponemon Institute report (sponsored by KeyFactor). Some of the resulting issues include:
- Website or service downtime/outages (which displays that ugly “Not Secure” warning)
- Lost sales and revenue
- Reputational damage and customer loss
- Non-compliance penalties
So, how do you manage all of these certificates to ensure that this doesn’t happen at your organization? And what other solutions can you use to streamline your cyber security efforts and prevent cyber attacks?
The Answer Lies with Automation and the Use of Other Advanced Technologies
More than two-thirds (67%) of the survey’s respondents believe that automation, artificial intelligence (AI), and other advanced technologies can help to prevent cyber attacks. This makes sense in many ways — computers are capable of scanning and analyzing logs and records faster than any human would ever be capable of doing. Furthermore, humans are more likely to make errors than machines and may forget to perform essential tasks.
The use of AI and machine learning-based solutions isn’t about machines replacing humans. It’s about augmenting our practitioners’ capabilities and reducing some of the strain that’s placed upon them each day. Part of this involves removing menial tasks from their workload that can be automated. Another part is taking advantage of the vast processing and analytical capabilities of AI to teach it to identify and recognize threats and attacks more quickly — even those that have before been seen.
So, what are some of the reasons why automation and learning-based solutions should be implemented?
- To ensure that basic yet critical tasks are completed.
- To enable your team to focus on higher-level priorities and functions.
- To improve the efficiency of your IT and cybersecurity teams and give them peace of mind.
- To increase visibility within your network and systems.
- To ensure that expiring certificates are renewed prior to expiration.
- To ensure compliance with various cyber security laws and regulations
- To decrease false positives.
- To Improve threat and attack detection rates,
- To improve an organization’s ability to prevent unknown, zero-day attacks.
Breaking Down the Research Survey: A Look at the Respondents
The survey focuses on the responses of more than 634 cybersecurity and IT professionals to questions relating to the following five overarching phases of the cybersecurity lifecycle. Of those respondents, 24% were IT management professionals and 18% work in the financial services sector.
Summary: Organizations Can Save a Lot by Using Proven Attack Prevention Tactics
This study highlights a key opportunity for cybersecurity-savvy companies. By focusing more of their budget and resources on cyber attack prevention, they can save significant costs, while protecting their reputation and business. Key attack prevention tactics include (but are not limited to):
- Using PKI for authentication and encryption
- Implementing automation where practical
- Using automated digital certificate management systems





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown