I Got Phished – A Cautionary Tale
I write about cybersecurity every day and even I almost fell for a recent spearphishing attempt
Business Email Compromises, which is a fancy term for the financial losses that can be incurred from phishing, are one of the most prominent forms of cybercrime. We talk about this all the time, I write about this all time, you may remember:
- 1 out of every 101 emails is malicious
- 70% of US employees don’t know email security best practices
- Criminals search LinkedIn to better tailor their emails to their targets
- Criminals design their phishing emails to create a sense of urgency
- Cybercrime will be a $1.5 trillion industry in 2018
There’s no shortage of other statistics that further drive home the point that email security is kind of a big deal. Over the last three years BECs have accounted for over $5-billion in corporate losses.
But even with all the awareness – and education – about email security, it’s still exceedingly easy to fall victim to a convincing phishing email. Hell, even an unconvincing phishing attempt can fool you if it catches you at the wrong moment.
So, here’s an embarrassing story that hopefully you can use as a cautionary tale about phishing and email security best practices.
…let’s hash it out.
“Hey John, did you need something from me?”
Last week I worked from home one morning while I dealt with… let’s call it a plumbing issue. Around 11 AM that morning I received an email from our owner, John Tuncer, asking if I was in the office.
This created the requisite sense of urgency in me for a couple of reasons. First, I’ve worked here for almost three years and I can count the number of times John has emailed me on one hand – and one of those times was to remind a coworker not to “Reply-All,” (which is actually sound advice but probably shouldn’t count towards that total). Either way, if John was emailing me it must be something important.
The other reason it sparked urgency in me was that I was, in fact, not at the office. So not only is this one of the few times that our owner (who is also our CEO) had contacted me, but I wasn’t even there.
![]() Not good.
Not good.
By the time I got to the office that afternoon, John had already departed for the day. No problem, I figured. I’ll follow up with him in the morning.
The next day – in a moment that I may never live down – I walked into our owner/CEO’s office and asked him, “Hey John, did you need something from me?”
I could tell he had no idea what I was talking about.
“You know, the email you sent me yesterday.”
I never sent you an email, he said. Check the sender. Realizing what had probably happened, I slowly began to back out of John’s office. Little known fact: a CEO’s vision is actually based on motion, so I figured if I could move very slowly I might be able to disappear and avoid finishing what was potentially about to be a very awkward conversation.
Then from the adjacent office our VP of operations let loose a howl.
“You got phished!”
When I got back to my office I checked the suspect email and sure enough, John was not the sender. The email emanated from a Gmail account.
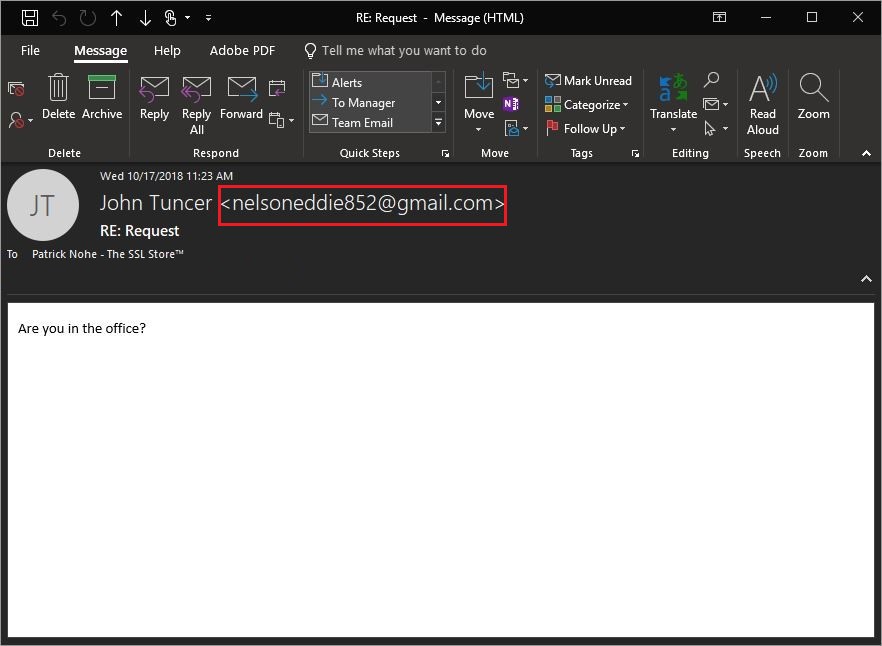
Awesome. I am the Editor-in-Chief of a highly trafficked cybersecurity blog and I just got phished.
But, this also represents an opportunity to reiterate some of our most common talking points about email security.
Some free pieces of advice on Email Security
Let’s start with the basic email hygiene that all employees should be practicing:
- The very first thing you should always check when opening an email is the sender’s email address. Not the display name of the sender that appears, but the actual email address. It’s easy to spoof a name, much harder to spoof an address.
- Unless you’re 100% certain that an email attachment is trustworthy, don’t open it. A malicious payload is one of the fastest ways to a security incident.
- Hover over any hyperlinks that are included in the email. If you are being instructed to go to a specific web page or log into a specific account, navigate there in the browser – independently from the link included in the email.
- Remember, no legitimate business or organization is going to ask you to supply personal information or financial data in an email. Nor will they ask you to transfer large sums of money. Ever.
- Finally, if you have a question about an email’s authenticity, contact the sender directly. Either pick up the phone and call them, or walk into their office and make an ass out of yourself (like I did).
And in my defense, I did follow that last step—even if I missed the obvious first one. If anything this should reiterate just how easily a mistake like this can happen. Your own employees are the biggest threat to your company. That’s not because they aren’t well-intentioned—99.9% of them are. It’s because these criminals are experts at what they’re doing.
Kip Boyle is the CEO of Cyber Risk Opportunities and has contributed to several articles on Hashed Out. He has a book due out in January, Fire Doesn’t Innovate, that starts with its own cautionary tale about an Aerospace company, FACC, that fell victim to a Business Email Compromise that ended up costing it about $45-million and the heads of its CEO and CFO (along with some other less noteworthy heads).
Look at the FACC example: that breach had nothing to do with technology being exploited. Sure, the cyber-criminal used technology to send the email, but none of the company’s technological defenses or controls were compromised. It was an attack on a person— and a process, not technology. More specifically, it was an attack on the lack of process.
One of the best ways to improve those processes and add a much-needed layer of identity authentication is with email signing certificates. Email Signing Certificates are like the less attractive, far less understood sibling to the SSL certificate. If X.509 certificates were the Baldwin brothers, Email Signing would be Stephen or Daniel. Definitely not Alec.
What an Email certificate does is affixes a digital signature to an email and then performs a hash function. The digital signature is typically made using a 2048-bit RSA private key—just like with SSL. And the trust model works about the same, too. The recipient’s system will check the authenticity of the signature in the same way it would an SSL certificate’s. When it does, it displays it in the email, like so:
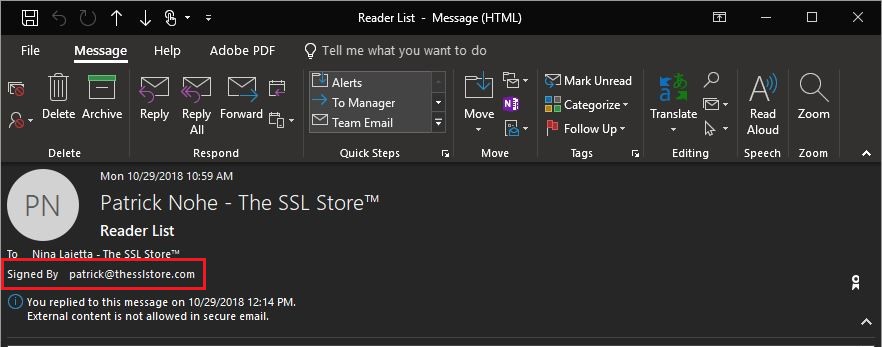
This is an example of a signed email. If you install email certificates on your mail server, it’s absolutely critical that you both mandate their use and teach your employees to look for the digital signature—and not to trust any email without one.
When both of those things happen you can reduce the potential for an email-based mishap considerably.
Granted, email certificates are not a cure-all, they won’t prevent criminals from trying to phish your company. You need to set up DMARC and do some additional work if you’re hoping to filter that garbage out entirely.
What an email signing certificate does is two-fold. It verifies the identity of the sender by virtue of the affixed digital signature. And the hashing function that’s performed during the signing also acts as a monitor that will indicate whether the email has been altered or tampered with.
Remember, no two disparate pieces of data can produce the same hash value. So even the smallest tweak to an email would result in a completely different hash value and the recipient will know immediately that something is amiss.
If you’re looking to add email signing to your email security configuration, we’ve got a few we can recommend.
I’d also suggest having a look at Ross Thomas’ Email Security series:
- Email Security – Part 1: Certificate Signed Emails
- Email Security – Part 2: Phishing and Other Falseness
- Email Security – Part 3: Sender Policy Framework (SPF)
- Email Security – Part 4: DKIM (DomainKeys Identified Mail)
- Email Security – Part 5: DMARC, Reporting and Email
- Email Security – Bonus: S/MIME for Apple Users
As always, leave any comments or questions below…





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)














5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown