Re-Hash: The Largest DDoS Attacks in History [2022 Update]
The latest record-breaking distributed denial of service (DDoS) attack peaked at 26 million requests per second (RPS) this past June. This is just the latest in a string of massive botnet-induced attacks targeting service providers
Move aside, Amazon and GitHub — there’s a new DDoS attack that holds the heavyweight title of being the largest DDoS attack in history. Cloudflare reported in June 2022 that its services detected and halted a massive distributed denial of service attack in action that topped 26 million requests per second. Considering that Cloudflare reports that they served “over 25 million HTTP requests per second on average” in Q2 2021, that gives you an idea of the sheer scale of this attack.
Previously, Amazon Web Services (AWS) was recognized as holding the reigning title for defending against a colossal 2.3 -terabit-per-second (Tbps) distributed denial of service (DDoS) attack! At the time (February 2020), this made Amazon attack the biggest reported DDoS attack in history.
It was preceded by GitHub, which sustained a 1.35 Tbps attack in 2018 — a one-two punch that was delivered without the help of a botnet. (Attackers used a method known as memcaching — more on that later.)
In January 2019, Imperva announced a new contender for the title — although they were looking at DDoS attacks from a slightly different angle. This undesirable recognition was awarded to an unnamed client of Imperva, which experienced a DDoS attack in which 500 million packets per second (PPS) were directed at their network or website. A few months later in April, Imperva reported an even larger PPS attack on another client that surpassed the January record — the newest attack peaked at 580 million PPS.
But wait; measuring an attack in terms of the amount of bandwidth used is not the same as measuring the intensity of an attack concerning the number of packets that are unleashed per second, and vice versa. Yes, you’re correct — these two avenues of attack are different, and one may be more difficult to recover from than the other. But how exactly are DDoS attacks really measured? And is one considered more method of attack more significant or challenging to recover from than another?
At Hashed Out, we’re not ones that like to hold any punches. Let’s take a look at the five most recent and biggest DDoS attacks in history (in terms of both forward rates and bit rates) as examples.
Let’s hash it out.
What Happened with the Most Recent (and Largest) DDoS Attack?
This article has been updated multiple times since it was first written by a former colleague a few years ago. When we previously reported on this topic, our talking points focused on GitHub and Imperva’s two unnamed clients.
- In June 2020, we updated the article to reflect the DDoS attack that AWS sustained in February 2020.
- We updated it again that same year to reflect a 2.3 Tbps attack against Amazon’s AWS Shield.
Now, we’re updating it in 2022 to reflect the latest report from Cloudflare.
Cloudflare
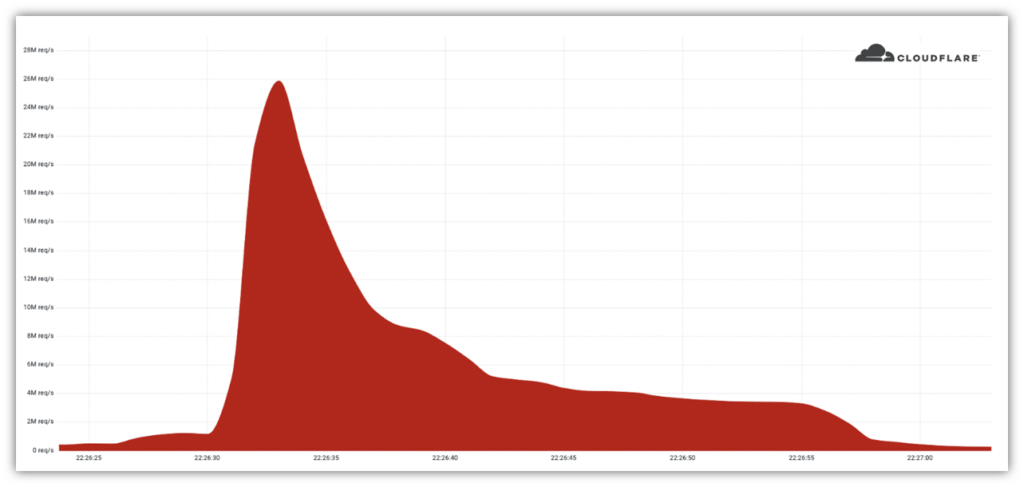
Cloudflare reports that a massive DDoS attack delivered a wallop to an unnamed customer website. This attack was delivered via a small but powerful botnet they’ve named “Mantis.” The network of 5,067 attacker-controlled devices, which relies on the use of both servers and virtual machines, was able to deliver a maximum of 5,200 requests per second per machine (node).
Previously, Amazon’s AWS Shield Observed and Mitigated a 2.3 Tbps Attack
Amazon reported that AWS Shield, their managed threat protection service, observed and mitigated a 2.3 Tbps DDoS attack on Feb. 17. Their research also indicates that there was a notable increase in the total number of events they reported in Q1 2020 over Q4 2019 (10%) and Q1 2019 (23%).
So, what do we know about the 2.3 Tbps attack? According to AWS’s Threat Landscape Report — Q1 2020:
“In Q1 2020, a known UDP reflection vector, CLDAP reflection, was observed with a previously unseen volume of 2.3 Tbps. This is approximately 44% larger than any network volumetric event previously detected on AWS. CLDAP reflection attacks of this magnitude caused 3 days of elevated threat during a single week in February 2020 before subsiding. Despite this observation, smaller network volumetric events are far more common. The 99th percentile event in Q1 2020 was 43 Gbps.”
Previously, the Attack Against Imperva’s Client
In the January 2019 attack, one of Imperva’s clients faced a SYN DDoS attack that resulted in a deluge of 500 million PPS. Each of the packets was thought to range from 800 to 900 bytes in size. While this sounds small, let’s take a moment to calculate this number with an example median number of 850 bytes per packet. That means that 500 million 850-byte packets would result in about 396 Gbps (425 billion bytes, or 3.4 trillion bits) of data targeting your network protocol every second to render it unresponsive.
Imperva reported:
“When we investigated, we realized the attack wasn’t generated using new tools, but two common older ones: one for the syn attack and the other for the large syn attack. Although both tools try to mimic legitimate operating systems, there are some odd, suspicion-raising differences. One tool randomizes various parameters but accidentally malforms the packet. The other tool uses a legitimate, almost identical packet, for the entire attack. One possible hypothesis is that these tools, although used in the same attack, were written by two different individuals and then combined to form an arsenal and launch the most intensive DDoS attack against Network infrastructure in the history of the Internet.”
This attack method differed from the method used in the GitHub attack, which used memcaching. We’ll talk a little more about that in a moment.
Previously, the GitHub DDoS Attack
GitHub is a developer platform that offers distributed version control and source code management for Git. Git is a version control system that tracks changes in computer files and helps coordinate collaboration between multiple people working on the same file. Basically GitHub is a repository for all kinds of code and the projects they come from. It also uses SHA-1 hashing as a check-sum — but that’s another topic for another day.
On Wednesday, February 28, 2018, GitHub got hit by the aforementioned DDoS attack. At the outset, GitHub had a little bit of trouble as it let a digital system assess the issue. After about 10 minutes GitHub called Akamai, the company tasked with DDoS mitigation for GitHub.
Akamai began filtering the traffic through its own systems, acting as a de facto intermediary. Akamai pushed the data through what it refers to as “scrubbing centers” to strip malicious packets.
After about eight minutes, the attackers relented.
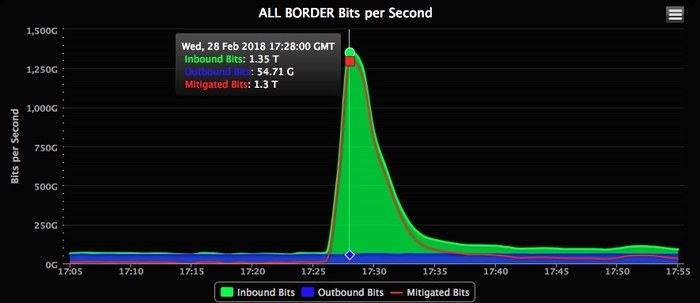
“We modeled our capacity based on five times the biggest attack that the internet has ever seen,” Josh Shaul, vice president of web security at Akamai told WIRED hours after the GitHub attack ended. “So I would have been certain that we could handle 1.3 Tbps, but at the same time we never had a terabit and a half come in all at once. It’s one thing to have the confidence, it’s another thing to see it actually play out how you’d hope.”
The previous record for the largest DDoS attack of all time was the 2016 attack against Dyn. Dyn does a lot of things, but perhaps most importantly it’s a DNS service. That attack came in at 1.2 Tbps and sent the internet into a frenzy.
There are some key differences, though. Dyn was hit by a botnet — a network of infected devices. The Github attack did not use a botnet, rather it used another increasingly popular method: memcaching.
What Is Memcaching?
A Memcashed server refers to database caching systems, which work to speed up websites and networks. There are currently over 100,000 memcached servers that are exposed on the public internet. Obviously, that’s not good.
What the attackers did here was spoof their victim’s IP address. Because of the lack of authentication on these servers, the attacker can send small queries that are designed to elicit much larger responses from the memcached server; 50 times larger, to be exact.
This is a type of amplification attack.
The GitHub attack sent a number of internet service and infrastructure providers scrambling to harden their systems as a result of the increased prevalence of these kinds of attacks. Specifically, that means blocking traffic from memcached servers.
Additionally, companies and organizations that have publicly exposed memcached servers were contacted and asked to take them offline and put them behind a firewall on an internal network.
What’s the Deal with DDoS?
To quickly recap: A DoS attack — a denial of service attack — is an assault that launches in rapid succession with a focus on making computer systems unresponsive and unavailable. It does this through an excess of connections, requests, and other data inputs that intends to overload the victim’s system. DDoS takes this attack approach to another level by using multiple internet connections and devices to launch a series of simultaneous attacks — a distributed denial of service — rather than using a single computer or internet connection (i.e., a traditional denial of service or DoS attack).
DDoS attacks target different layers of a network connection. (Think of the seven layers of the OSI model — application, presentation, session, transport, network, datalink, and physical.) They’re typically divided into a few defining categories of attacks (which we’ll talk about a little later), although some DDoS attacks are multi-vectored in nature.
What You May See With a DDoS Attack
This is what you want to see when you visit a service provider’s website:
Attacks Vary in Terms of Strength, Frequency, and Length of Occurrence
Typically, DDoS attacks last less than four hours, Kaspersky reports in its Q1 2022 findings. Of course, four hours is still a long time, we get it. But it’s not nearly as long as the 549 hours (i.e., 23 days) of attack Kaspersky Lab reported one client experiencing.
The research team’s report indicates that DDoS attacks jumped significantly in Q1 2022, when they detected 91,052 DDoS attacks.
“Before evaluating the Q1 2022 data, it is worth recalling that our previous quarter report mentioned a record number of DDoS attacks. This quarter, we saw an almost 1.5-fold (46%) increase in the number of attacks relative to the record, and a 4.5-fold rise compared to the same period last year.
The reason for this growth is obvious: the crisis in Ukraine led to a cyberwar, which could hardly fail to impact the statistics. Looking at the distribution of DDoS attacks by week, we see that the peak of new attacks occurred in the eighth week of 2022, that is, February 21–27, and we repelled the largest number of DDoS attacks that week on February 25.”
Data from Cisco predicts that the total number of DDoS attacks globally will double to 15.4 million by 2023. This is up from their estimate of 10.8 million in 2020.
How DDoS Attacks are Measured: Packets vs Bandwidth
As you’ve seen in this article, many of the largest DDoS attacks are often measured in different ways — typically in terms of bandwidth/capacity, which is measured in bits per second (bps), or forwarding rate, which is measured in packets per second (PPS). The choice of terms used can significantly change the meaning of any blanket statements about what attacks would be in the running for the title of the biggest DDoS attack in history:
- The first, bandwidth or capacity, typically refers to the amount of data that can travel through an internet connection.
- The latter, the packet forwarding rate, refers to the number of packets that can be processed by network devices.
Large DDoS attacks often try to use both routes of attack, aiming to saturate their victims with high bps attacks (such as Gbps or Tbps) or overwhelm and crash their network devices with high PPS attacks.
How DDoS Attack Routes Are Defined
DDoS attack methods include amplification attacks (NTP, DNS, SSDP, etc.), floods (UPD, SYN, etc.), IP fragmentation, and zero-day attacks. DDoS attacks often focus on the victim’s network protocols, bandwidth, and/and application layer, and are typically measured in terms of packets per second (PPS), bits per second, and requests per second (RPS) depending on the area of focus.
DDoS attack methods are very distinct and approach the goal of disrupting services from different avenues. What makes it difficult about discussing DDoS attacks is that companies tend to use different terminology to refer to the same (or similar) concepts. For example, Cloudflare and Cisco refer to DDoS attacks in the following terms:
- Application layer attacks (think HTTP request floods)
- Protocol attacks (think TCP SYN floods)
- Volumetric attacks (bandwidth attacks like DNS amplifications)
Imperva, on the other hand, categorizes DDoS attacks as the following:
- A packet per second attack is a DDoS attack that focuses on network protocols such as the transmission control protocol/internet protocol (TCP/IP). The more packets that are forwarded and your system must try to process, the longer it takes and the more resources and network hardware you’ll need. The idea here is that hackers want to thoroughly overwhelm server and intermediate communication equipment resources by making phony protocol requests. These types of PPS attacks include fragmented packet attacks, SYN floods, and “ping of death” attacks.
- A gigabit per second attack is volumetric in nature and uses reflection or amplification techniques (or a botnet of seemingly innocuous connected IoT devices such as baby monitors and security cameras) to “flood” the victim with DNS server responses. The idea here is to utterly saturate the victim’s bandwidth to prevent it from processing genuine traffic and can cause their server(s) to crash.
- A request per second (RPS) attack is an application layer attack and refers to the number of requests that are made of an application. It involves targeting an edge server that is responsible for application execution and overwhelms its CPU and memory to consume its resources so it can’t process anything else.
Regardless of which categorizations or units of measurement companies use to track these attacks, the big takeaway here is that DDoS attacks are increasing both in terms of severity and size.
Bit to Packet Forwarding Rate Metric Conversion
Imperva shares that throughput and forward rates aren’t directly convertible. The reason for this is that there is no one-size-fits-all measurement for network packets — they come in a variety of sizes and are transmitted via different interfaces at varying speeds. This means that there is no way to say how many packets make a megabit or gigabit without first knowing the size of an individual network packet, which can range significantly depending on whether you’re calculating the size of a TCP packet versus, say, an Ethernet UDP packet.
Remember: eight bits equals one byte, and each packet may contain a different number of bytes depending on various factors.
Now that you know what the most recent and largest DDoS attack is and how it was measured, here’s a historical perspective on some of the largest or most famous DDoS attacks in the past nearly eight years.
The List of the Most Famous DDoS Attacks — By Year and Month
Want to see some others who have unwittingly competed for the title of sustaining the largest DDoS attacks on record? Check out our timeline to see the progression of the largest and most famous distributed denial of service attacks that have occurred within the past several years (both traffic-based and packet-based attacks):
2022
June — Cloudflare reported detecting and mitigating a 26 million RPS DDoS attack on an unnamed client’s website. This is the one we discussed earlier in the article.
April — Cloudflare reported the detection and mitigation of a 15.3 million RPS DDoS attack on a customer operating a crypto launchpad. The attack utilized a botnet consisting of an estimated 6,000 unique devices from 112 countries. Unlike many other DDoS attacks, this one was carried out via HTTPS, which is uncommon because it’s more expensive for threat actors to use secure, encrypted connections.
2021
December — Microsoft reported two additional attacks against customers in Asia. The first was a 3.25 Tbps UDP attack that lasted more than 15 minutes; the second was a 2.55 Tbps UDP flood that lasted more than five minutes. While the latter might not sound like a long time, it’s five minutes longer of unrelenting attack time than any organization wants to sustain.
November — Microsoft previously reported detecting and mitigating a whopping 3.45 Tbps DDoS attack against an Azure customer in Asia. This security incident had a packet rate of 340 million packets per second.
July — Cloudflare reported a DDoS attack that topped out at 17.2 million traffic requests per second against financial websites.
2020
February — Amazon Web Services (AWS) reported in their TLR for Q1 2020 that they observed and mitigated a 2.3 Tbps UDP reflection vector DDoS attack. Not only is this the largest DDoS attack that AWS reported ever facing, but it was also thought to be the largest DDoS attack in history on record at the time in terms of bit rate.
2019
April — Imperva reports one of their clients was able to thwart a DDoS attack that peaked at 580 million packets per second. To date, this is considered the largest DDoS attack by packet volume to date.
January — Another Imperva client sustained a 500 million packets per second DDoS attack.
2018
March — NETSCOUT reported that its Arbor ATLAS global traffic and DDoS threat detection system confirmed a 1.7 Tbps memcached reflection/amplification attack on an unnamed U.S.-based service provider.
February — The GitHub DDoS attack inundated the company with 1.35 Tbps of data (129.6 million PPS) — the largest DDoS attack on record as of that time — via memcaching. This means that the attackers spoofed GitHub’s IP address to send small inquiries to several Memcached servers to trigger a major response in the form of a 50x data response.
2017
October — The Czech statistical office websites relating to the Czech Republic’s parliamentary elections — volby.cz and volbyhned.cz — failed temporarily due to DDoS attacks during the vote count.
August — Web host company DreamHost, which was said to host the Nazi-advocate website Daily Stormer under its new name Punished Stormer, suffered a DDoS attack of unannounced proportion. This attack followed a Department of Justice request for visitor data relating to the stormer site.
June — Throughout the second half of the year, video game software developer Square Enix’s Final Fantasy XIV online role-playing game (RPG) sustained intermittent DDoS attacks via botnets. The attacks spanned the summer and another set of attacks occurred during the fall.
2016
October — The Dyn DDoS attack, which measured in at 1.2 Tbps and was considered the largest DDoS attack at the time, brought down much of the internet across the U.S. and Europe. Using the Mirai botnet, the attack targeted Dyn, a company that controls much of the domain name system (DNS) infrastructure of the internet.
September — French web host OVH experienced a DDoS attack measuring in at nearly 1 Tbps. The attackers used a botnet of hacked IoT devices (CCTV cameras and personal video recorders) to launch their attack.
2015
March — GitHub sustained a DDoS attack that was thought to be politically motivated because it focused on two GitHub projects that aimed to provide Chinese citizens with a way to circumvent Chinese state web censorship.
2014
November —The website for Occupy Central in Hong Kong, which was campaigning for a more democratic voting system, experienced a 500 Gbps DDoS attack that was executed via five botnets. Also targeted were the online news site Apple Daily and PopVote, a mock election site, both of which supported OC’s message.
Have questions or want to share your thoughts about DDoS attacks? Feel free to do so below.
This article was originally written by Patrick Nohe in 2018. It has since been updated with new information and data by Casey Crane multiple times, including 2019, 2020 and now in 2022.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)



![Re-Hash: The Largest DDoS Attacks in History [2022 Update]](https://www.thesslstore.com/blog/wp-content/uploads/2018/03/DDoS-Feature-698x419.png)








5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown