New Attack Against SSL Threatens Secure Connections
One third of all servers may be vulnerable to the “DROWN” attack
On March 1st researchers published details about a new vulnerability against the SSL/TLS protocol. Analysis has shown that anywhere between 20-30% of all servers may be affected. Luckily, this attack has probably not been used by malicious parties and protecting your server is easy.
Please read on to learn about this new vulnerability and how you can protect your users and your network.
Like most recent SSL/TLS vulnerabilities, this attack is named with an acronym. “DROWN”, or Decrypting RSA with Obsolete and Weakened eNcryption is a complex attack leveraging vulnerabilities in both the protocol itself and bugs in OpenSSL, the most popular library for implementing the SSL/TLS protocol.
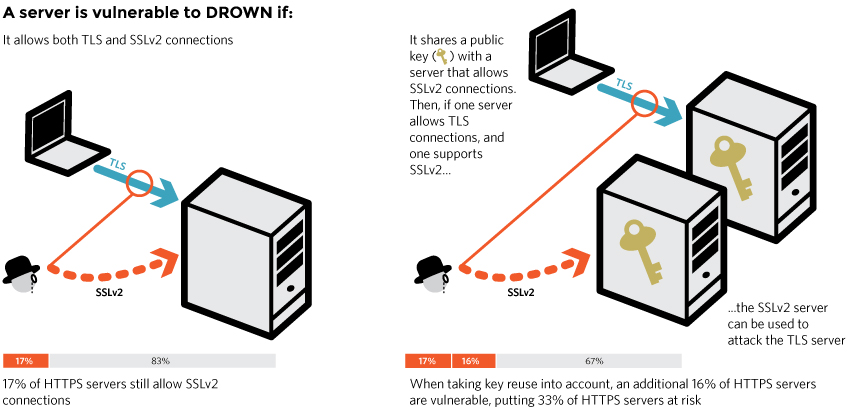
DROWN relies on your server supporting SSLv2 – the oldest version of the protocol ever publically released. By leveraging vulnerabilities in that version of the protocol, DROWN can compromise any SSL session created using the same public key, even if those sessions use a newer protocol version.
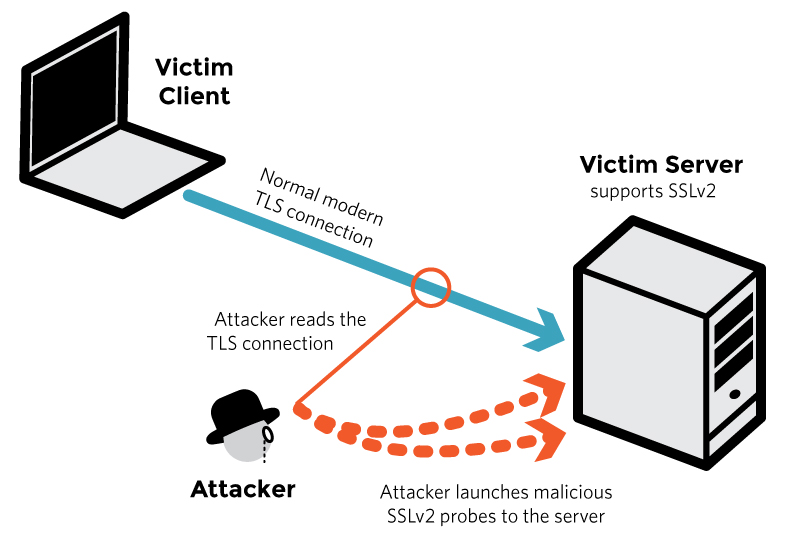
What’s unique about DROWN is that it allows attackers to compromise the encryption even if your user’s connections are not using SSL v2. “Merely allowing SSLv2” server-side puts them at risk.
There are multiple factors that can make your server vulnerable to DROWN, and certain factors make it significantly easier for attackers to use DROWN successfully and quickly. Servers that are the most severely affected can have their user’s connections decrypted in “under a minute using a single PC,” which is startlingly fast.
According to the research team that discovered DROWN, between 20-30% off all servers may be affected by this vulnerability.
We know the most important thing for server admins is to determine if they are affected and what steps they need to take to protect themselves. So we are not going to go in detail about how the attack works (anyone who is curious can visit https://drownattack.com and read their brief summary or dive into the full technical paper).
Instead, what we have done is prepared a helpful checklist for server administrators. If you read through this list – and it should only take about 5 minutes – we will guide you step by step through the situation and at the end you will know if you are affected and how you can patch your system.
1. You DO NOT need to reissue your certificate.
The DROWN attack is NOT able to steal or learn about your private key. This means that your certificate (and its private key) are not compromised and you do not need to reissue your certificate. DROWN can only compromise individual SSL sessions.
2. You DO need to take action with every server and device using SSL on your network.
To protect against DROWN, server operators need to ensure that their private keys are not used anywhere with server software that allows SSLv2 connections.
One of the complexities of DROWN is that attackers using this technique only need to find one device on your network that has SSLv2 enabled. If that device uses a certificate that shares the same public key (and therefore the same private key) with another certificate (or a copy of that same certificate) then all those devices are at risk.
It is common for certificates to be used across multiple devices or servers. For instance, your certificate may be used on your main webserver and your mail server. Research from the DROWN team has shown that many organizations already had their primary webservers protected from this attack, but left mail servers or other less significant servers with poor configurations, putting them all at risk.
First, identify all your devices using SSL, and make sure you know what devices, if any, are sharing certificates or keys. Once you have mapped out your network, you can quickly fix the problem in the following two steps.
(The official website for DROWN offers a test that can help check for vulnerabilities. Please note that this test is not comprehensive and not dynamic. This means you may have vulnerable servers that are not listed here, and that if you update your servers the test results will not change. Please only use this to help with your diagnostics, and do not assume you are unaffected because of these test results.)
3. You DO need to patch Open SSL.
Every server (and other networking hardware) uses a “cryptographic library” (a.k.a. software for cryptography) to implement the SSL/TLS protocol. The most popular library is OpenSSL. If you are using OpenSSL, patch it immediately. Bug fixes have been released that can help prevent DROWN. But don’t stop there – you also need to disable SSLv2.
If your server is running Apache or NGINX you are probably using OpenSSL. If your server is running a Microsoft OS, you are likely not using OpenSSL.
If you have enterprise networking hardware or other devices like a firewall, you will need to consult that manufacturer to see if they use OpenSSL, and how (or if) you can download any patches.
4. You DO need to disable support for SSLv2
DROWN relies on abusing insecure ciphers and protocol flaws in SSLv2. You need to mitigate this problem by turning off SSLv2 support on EVERY device on your network. In 2016 there is no reason that any clients should be using (or need) this protocol version.
Here are ways to disable SSLv2 support on popular server OSs (these commands also disable SSLv3 support, which is a current best-practice since the discovery of the POODLE vulnerability):
Apache: If you are using Apache 2.4.x you are already good to go by default. If you are running Apache 2.2.x, you can configure which protocol versions are disabled by editing the SSL configuration file or Virtual Host configuration file(s). The name and location of this file will vary by distro and your personal preferences.The default location of this file for the apache.org source package is:
/usr/local/apache2/conf/extra/httpd-ssl.confAdd (or update, if you already have “SSLProtocol” present) the following as a new line in your configuration file:
SSLProtocol All -SSLv2 -SSLv3Add (or update, if you already have “ssl_protocols” present) the following directive as a new line in your SSL configuration file:
ssl_protocols TLSv1 TLSv1.1 TLSv1.2That’s it! You are safe!
If you have patched OpenSSL and disabled SSLv2 support across your network then you are no longer vulnerable to DROWN. Before we let you go, we want to stress the unique attack surface of this vulnerability. If ANY device on your network has SSLv2 enabled it will allow attackers to compromise EVERY device that shares that same public/private key pair. Please make sure you are updating the configuration on all of your devices, not just your primary web server.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown