Raccoon Attack: Researchers Find A Vulnerability in TLS 1.2
Bad news: there’s a vulnerability in TLS 1.2. Good news: researchers say it’s “very hard to exploit” and major vendors have already released security patches for it.
A team of researchers has documented a vulnerability in TLS 1.2 (and earlier versions) that could allow a man-in-the-middle attacker to acquire a shared session key and decrypt SSL/TLS traffic.
The vulnerability only applies in very specific circumstances and is difficult to execute, but software vendors have released patches to block potential attackers from taking advantage of this loophole.
(In case you’re wondering: No you don’t have to re-issue any certificates!)
What is the Raccoon Attack? How does it work? What should site owners do?
Let’s hash it out.
What Is the Raccoon Attack?
The Raccoon attack is a newly discovered vulnerability in TLS 1.2 and earlier versions. It allows hackers (in certain situations) to determine a shared session key and use that to decrypt TLS communications between the server and client.
The attack doesn’t allow a hacker to obtain the private key, so they’d have to perform the attack individually on each connection they want to eavesdrop on.
In order to execute the Raccoon Attack, a hacker needs several conditions in place:
- Successfully setup a man-in-the-middle attack to intercept communications
- Connection must use TLS 1.2 or previous (but we’ve all disabled SSL 3.0, TLS 1.0, and TLS 1.1 already…right?)
- Connection must use Diffie-Hellman key exchange
- Server must re-use Diffie-Hellman public keys
- The attacker needs to be near the target server in order to run precise timing measurements
If you’d like to learn more about how the attack is executed, the researchers have setup a very informative website at raccoon-attack.com with technical details and FAQs.
As far as we know, this attack has not been used in the real world. Researchers say that due to the multiple conditions that have to be in place for this attack to work, “a real-world attacker will probably use other attack vectors that are simpler and more reliable than this attack”.
What Should Site Admins Do?
Raccoon is a possible but rather unlikely attack, and it targets configurations that were already considered bad practice and were being disabled by browsers. In the words of the researchers who found it:
“Raccoon is a complex timing attack and it is very hard to exploit. It requires a lot of stars to align to decrypt a real-world TLS session.”
Raccoon might not be a very likely real-world attack, but it’s still a proven vulnerability, so site admins would be wise to check their servers and plug this potential security hole if necessary.
Test Your Server
As a first step, you can do a quick test to see if your server software/configuration might be vulnerable to Raccoon.
Here’s how:
1) Go to SSL Labs, run a test for your domain, and look for this setting:
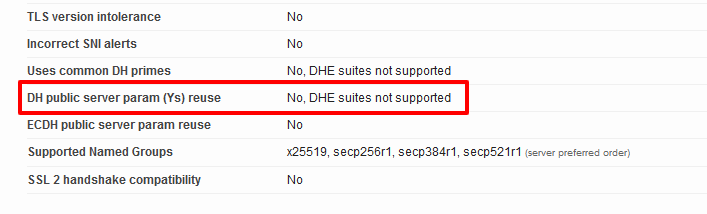
2) If that parameter says “Yes” then your server may be vulnerable.
Patching Your Server
If your server is vulnerable to this attack, you will likely be able to solve the issue by simply patching or upgrading the relevant software package:
- F5 has released a list of versions affected by Raccoon and details on how to patch each one.
- OpenSSL 1.1.1 is not vulnerable to Raccoon. Older versions may need to upgrade.
- Microsoft has released security patches for impacted software versions.
Researchers indicate that BearSSL, BoringSSL, Botan, Mbed TLS and s2n are not vulnerable to Raccoon.
Does this Affect My SSL Certificate?
No, this should not affect any SSL certificates—it’s an issue with server/client configuration, not the digital certificate. We don’t anticipate any SSL/TLS certificates will need to be revoked or re-issued.
Let’s Move to TLS 1.3
This vulnerability is another great reminder to move towards TLS 1.3—which is generally more secure and efficient than TLS 1.2.
“The complexity of this attack makes it unlikely to be used in practice; however, to be safe, organizations are encouraged to adopt TLS 1.3 and begin deprecating older versions of the protocol.”
Dean Coclin, CISSP, DigiCert
For more details on why TLS 1.3 is better, faster, and more secure, see our previous post: TLS 1.3: Everything you need to know.
What’s in A Name?
POODLE, GOLDENDOODLE, and now RACCOON. (All animal names that include “oo”. I wonder what’s next…Baboon? Kangaroo? Coonhound?)
If you’re curious where this name came from, it was chosen by the team of researchers that discovered the vulnerability: Robert Merget, Marcus Brinkmann, Nimrod Aviram, Juraj Somorovsky, Johannes Mittmann, and Jörg Schwenk. Unlike many other TLS vulnerability names, Raccoon isn’t an abbreviation or acronym for a longer title. In this case, it’s just a name the researchers liked: “Raccoons are just cute animals, and it is well past time that an attack will be named after them.”
Plus, it turns out that raccoons are pretty good at getting into things that are supposed to be locked and secure, so the name seems pretty fitting to us:






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)





 (3 votes, average: 4.33 out of 5)
(3 votes, average: 4.33 out of 5)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown