Zombie POODLE and GOLDENDOODLE – Two new exploits found for TLS 1.2
TLS 1.2 implementations that still support Cipher Block-Chaining are vulnerable.
Before we get started discussing a couple of new exploits that can be found with some TLS 1.2 implementations, let’s begin by discussing the naming conventions that are used in the cybersecurity industry. POODLE, which is an acronym for Padding Oracle On Downgraded Legacy Encryption, is a completely functional name, but still a terrible one.
While I’m typically a proponent of pragmatism, when you’re naming a vulnerability that provides an attacker the means to decrypt and exfiltrate data from a secure connection, you want a name that strikes a harsher chord than the word for a froofy French hunting dog.
Don’t get me wrong, my folks had standard Poodles throughout my childhood – they’re great dogs – but their mention strikes terror into the hearts of exactly no one, save maybe the lizards on my parents’ patio.
So, with that in mind let’s discuss a couple of variants of POODLE that can victimize certain TLS 1.2 implementations that still support Cipher Block-Chaining: Zombie POODLE and GOLDENDOODLE.
Let’s hash it out.
Remembering POODLE
POODLE, which started as an SSL 3.0 exploit, was a threat to the newer TLS protocols if they maintained backwards compatibility with 3.0. Every few months or so we’ll run an article showing the troubling number of websites that still support SSL 3.0. As of last count it was 6.8% of the Alexa Top 100,000. This doesn’t necessarily mean that those websites don’t support newer versions of the TLS protocol, it just means that they maintain legacy support for 3.0, which can be weaponized by attacks like POODLE.
POODLE worked by attacking the padding used with block ciphers. When encryption is done with a block cipher, the length of the data being input needs to be an exact multiple of the block’s length in bytes. For instance, with triple DES, the block length is 8 bytes (64 bits), for AES it’s 16 bytes (128 bits), so before encryption can be performed using either of those ciphers you’d need to pad the input to be a multiple of the block length.
We really don’t need to get more specific than that, and other forms of encryption don’t require padding, but POODLE worked by discerning the padding used to decrypt the message being sent. Now, this exploit relies on a few things to succeed. For starters, you need to be actively executing a Man-in-the-Middle to leverage it. Then you need to force connections to fail in order to force the server to revert back to SSL 3.0. The SSL/TLS protocols were designed, at least early on, to have this fallback feature for the sake of interoperability. POODLE is why we can’t have nice things.
Another variant of the exploit, published later in 2014 (after the SSL 3.0 version), demonstrates the attack working successfully against TLS. It exploits implementation flaws in TLS 1.0-TLS 1.2, specifically with their Cipher-Block Chaining encryption modes. It’s this TLS-based variant that forms the foundation for today’s new exploits, Zombie POODLE and GOLDENDOODLE.
Zombie POODLE and GOLDENDOODLE
Five years after news of POODLE broke and the exploit was patched and somewhat forgotten, it still maintains some viability thanks to products that failed to confront the first POODLE issue.
Craig Young, a researcher for Tripwire, was able to revive the exploit with a slight tweak in a Citrix load balancer. This was the so-called Zombie POODLE exploit. GOLDENDOODLE is a sup-ed variant of POODLE with a much faster, more powerful crypto-hacking mechanism.
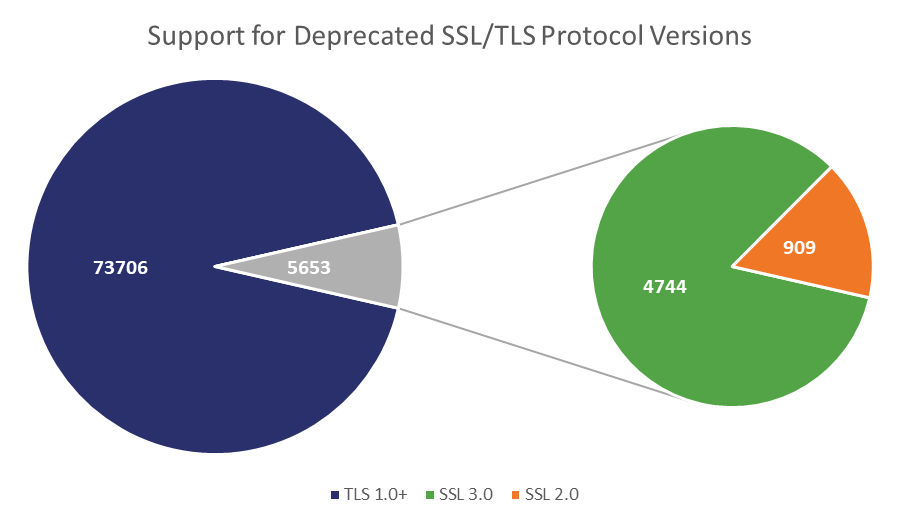
All in all, roughly 2,000 of the Alexa top million websites are vulnerable to Zombie POODLE and around 1,000 are vulnerable to GOLDENDOODLE. More troublingly, about 500 are still vulnerable to POODLE itself.
How to avoid Zombie POODLE and GOLDENDOODLE
The biggest problem with both the original SSL protocols and the newer TLS protocols is that, in the name of interoperability, there hasn’t been adequate deprecation of older crytopgraphic methods and ciphers that have known vulnerabilities. Instead, TLS 1.2 is full of workarounds and tweaks to try to ensure older, legacy devices maintain access to websites despite the security risks that may pose.
The most direct way to continue using TLS 1.2 and defend against these exploits is to completely disable all support for CBC encryption suites. But, longterm, TLS 1.3 is going to need to be the answer. TLS 1.3 has stripped support for older ciphers and cryptographic methods that are known to be vulnerable in addition to refining the handshake, which reduces overhead.
So far TLS 1.3 has seen promising results in its early deployment, but there will likely be websites that are hesitant to completely switch for fear of locking out users on older, legacy browsers and systems.
Exploits like POODLE, Zombie POODLE and GOLDENDOODLE are arguments against that position. They’re what happen when you cater more towards interoperability than security.
It makes everyone less safe.
As always, leave any comments or questions below…







































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown