What Is a DNS Leak?
What causes a DNS Leak and what can be done to fix one?
Do you remember the first time you grew a little bit concerned about your digital privacy? Maybe it was the first time you figured out the ads you’ve been seeing are specifically targeted to you. Maybe it was Google’s eagerness to be helpful that betrayed just how much information it has about you (it knows where you are right now). Or maybe you’ve never really considered these things and today’s discussion about DNS leaking will really open your eyes.

If that’s the case, I envy you. In fact, maybe even consider just taking a rain-check on the rest of this article and then just continue living your life – because ignorance truly is bliss.
But for the rest of us, privacy is an unfortunate consideration in many of the decisions we make online.
And when it comes to our digital privacy, DNS leaks are a particularly pernicious threat to said privacy. But despite their ability to compromise your anonymity, DNS leaks are also one of the least understood threats faced by the modern internet user. That’s owing to a lot of different factors, chief among them that aforementioned blissful ignorance.
If we’re being honest, the average internet user doesn’t understand how the connections being made by their own computer actually work, nor do they understand the Internet Protocol, IP addresses, the Domain Name System or even Virtual Private Networks. In turn, that lack of information makes everything else feel abstract and basically blunts any concern we would otherwise have about the threat.
So, today we’re going to talk about DNS Leaks, what they are, why they’re dangerous and how to fix them.
Let’s hash it out.
Internet Connections and VPNs
If you’ll recall a few weeks ago we went in-depth on the TCP/IP model for network connections. If you want a complete explanation of all that, I recommend checking it out. But for now, here’s the abridged version:
Anytime you make a connection on the internet, data is being routed across multiple layers, in multiple ways, to facilitate the connection itself. In fact, calling it a singular connection can even be a little misleading as there are actually multiple connections being made throughout the process. Of course, this all happens in the background, so for most of us our only exposure to a lot of it is the error messages that are triggered when something goes wrong (TLS handshake error, I’m looking at you).
So, while on the user side visiting a website might seem as straightforward as typing “amazon.com” into your address bar and within seconds you’re connected to Amazon. But that belies just how complicated making that connection actually was.
Let’s illustrate with an example. Here’s a quick breakdown of what a mail connection would look like:
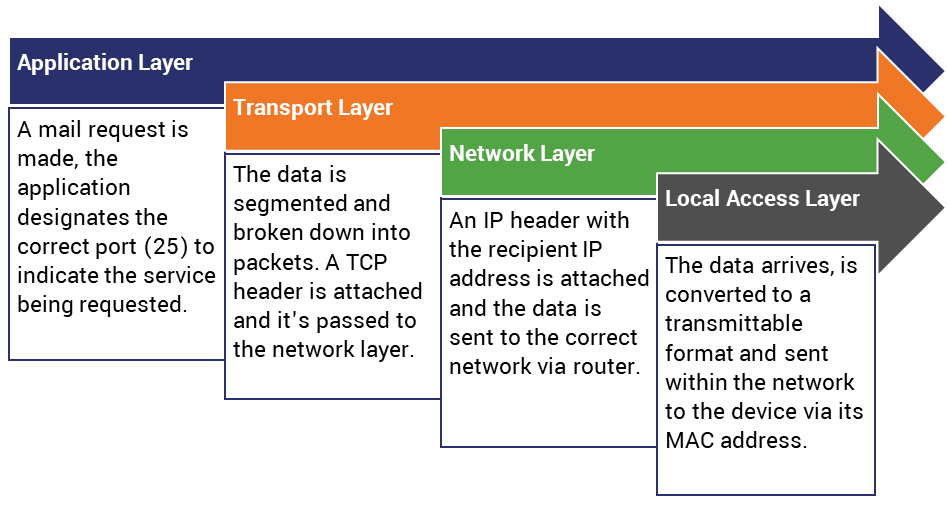
Again, we’re not going to go too far into the weeds on thre of the four layers you see here, instead we’re going to focus in on the Network Layer where the Internet Protocol functions.
The top two layers, Application and Transport, largely deal with the defining the connection itself. What port will it use. What connection type (TCP or UDP). Data is ported, segmented and put into transmittable packets.
On the Network Layer you’re handling the connection between different networks via the Internet Protocol and the networks’ respective IP addresses.
You’re likely familiar with IP addresses, but you might not know why they’re significant. While Google has plans to kill it, colloquial use of the internet has always relied on the URL or Uniform Resource Locator. Asking people to remember strings of numbers has historically not been a good idea. Our cell phones have largely eliminated the problem, but before everyone had a mobile device in their pocket, remembering phone numbers was a huge pain in the rear. (Also, using Maps.) People often had to carry around black books full of phone numbers or else record them on the walls of bathroom stalls for their use in perpetuity.

So, asking you to remember an IPv4, or even worse an IPv6 address is going to yield a lot less success than just rolling with a URL like “company.com.” People remember “company.com.” Thus, we use URLs.
But that creates its own issue, now you need to keep a dedicated resource that serves as a de facto phone book, pairing URLs with their respective IP addresses. But given the fact the internet is constantly growing, that websites can change IP addresses, and considering the amount of space that would be required to keep an ongoing record of all that, how do you reconcile letting users use URLs when networks and websites use IP addresses?
The Domain Name Service or DNS.
DNS is that resource. In the example above, after the information has been segmented and ported, it needs to be delivered to the correct network. In order to do this, the Internet Protocol will likely be used, which will require the correct IP address to be affixed to the data in the form of a header that will be used to route it to the correct destination.
But in order to get the correct IP address, you’re going to need to perform a DNS look-up.
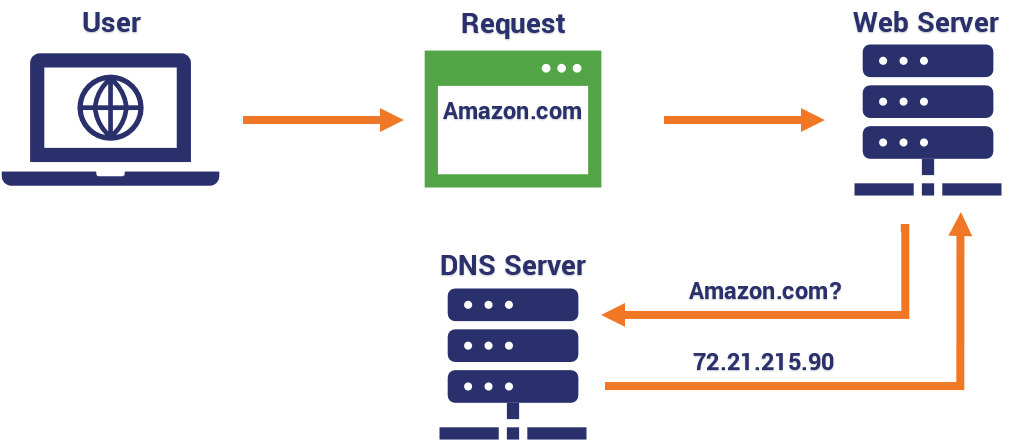
This occurs on the network layer. Before the data can be routed to its intended recipient, the sender’s computer system or network is going to need to reach out to a DNS server or resolver to pair the given URL with its IP address. This is a highly technical step that many people never give a second thought to. But if you’re worried about your privacy this is also one of those critical steps in a connection that can effectively muck up everything.
Here’s why…
What’s the Big Deal About a DNS Leak?
Ideally, in a perfect world, you wouldn’t need to worry about your DNS lookups being a problem. Guess what, that’s not the world we live in. This issue really plays out on two different levels depending on your geography. But before we get to that, let’s contextualize just a little bit more by bringing VPNs into this conversation.
People use VPNs for two primary reasons:
- Security
- Privacy
And those two reasons are hardly mutually exclusive. Aptly named, a VPN is a literal virtual network through which all of a user’s internet traffic can be funneled through to improve privacy.

A well-configured VPN can block your IP address, shield you from tracking and all but make you anonymous. A third party might know that you’re using a VPN, but it doesn’t know what you’re doing with it.
DNS leaking screws all of that up. Typically, the result of misconfiguration (or using a shoddy VPN), DNS leaking occurs when a device or network attempts to make a DNS call outside of the VPN tunnel.
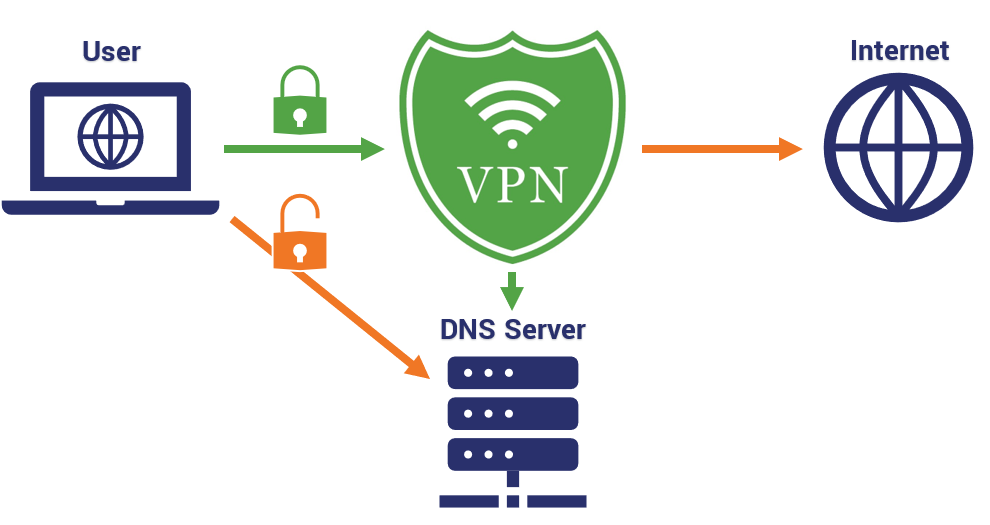
Now, if you’re not using a VPN, then all of this information is already being logged by your Internet Service Provider (ISP), anyway. Every time you try to resolve a URL your ISP’s DNS server records your IP address, the given URL and the IP address you’re attempting to reach. That means it can effectively track you across the internet.
And that’s a big part of why you would want to use a VPN, DNS records provide myriad information about an internet user and their behavior online. Remember how we started this section by mentioning that the severity of your DNS lookups not being private varies by your geography and typically breaks down into one of two different categories?
In the developing world, where internet freedom is not at a premium, DNS records can be used to track internet use, help censor material and even punish people for trying to access banned or blocked content. There are some places around the world where even being tangentially connected to the wrong website or network can land you in a labor camp or jail.
Fortunately, that’s a reality most of us will never experience. For internet users around the rest of the world, VPN use and digital privacy are concerned more with “first world problems” than anything that registers on a human rights scale.
In more developed countries having a DNS leak can lead to:

- Having your internet speed throttled when attempting to access streaming content
- Having certain websites and networks slowed down or even blocked by some ISPs
- Unwanted legal attention when downloading torrents or pirated content
- Potential sale of your internet activity/history to third-parties like ad networks
So, admittedly, having your ISP throttle your speed when you’re trying to watch Netflix kind of pales in comparison to being sent to the Gulags for visiting the wrong news site, but across the world there are real reasons for people to want to keep their DNS look-ups off the radars of their governments and ISPs.
Having your DNS records leak completely undermines that goal, it could also allow a third party to fingerprint you, and figure out your actual IP address, which is its own problem in and of itself. Your IP address reveals a treasure trove of information, things like:
- Location
- ISP
- What scripts you have enabled/disabled
- What privacy measures you have in place
- Your system time
- Screen size
- Operating System
So while many people have never given a single thought to DNS leaking, if you care about your digital privacy you need to start thinking about it.
How Do I Know If I Have a DNS Leak?
Like carbon monoxide poisoning, there’s really no telltale sign that you have a problem without monitoring for it. That’s kind of a macabre comparison, but also apropos. Fortunately, there are some pretty good tools that can help you to test for DNS leaks.
- DNSLeakTest.com
- BrowserLeaks.com
- IPLeak.net
- DNSLeak.com
Using them is simple enough, just navigate to the website and follow their instructions. They’ll give you a pretty clear idea about what’s leaking.
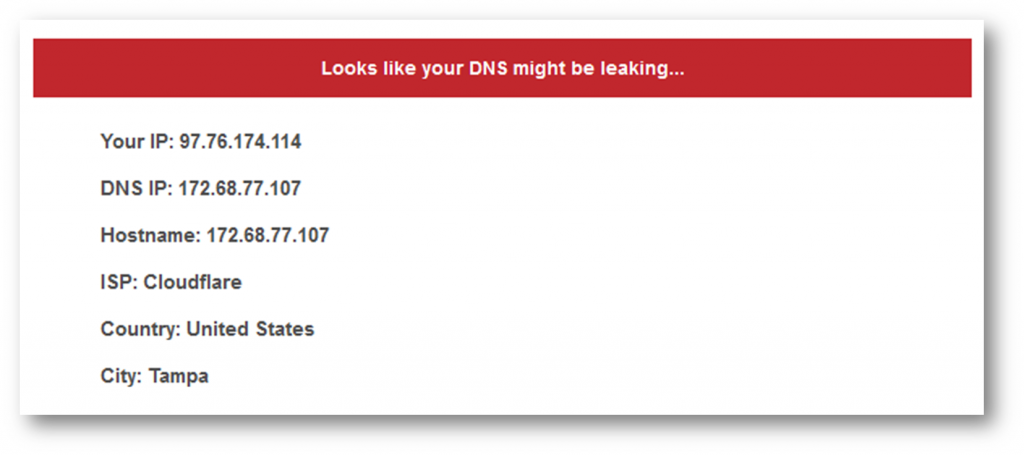
Some even explain what exactly the ramifications of a leak are.
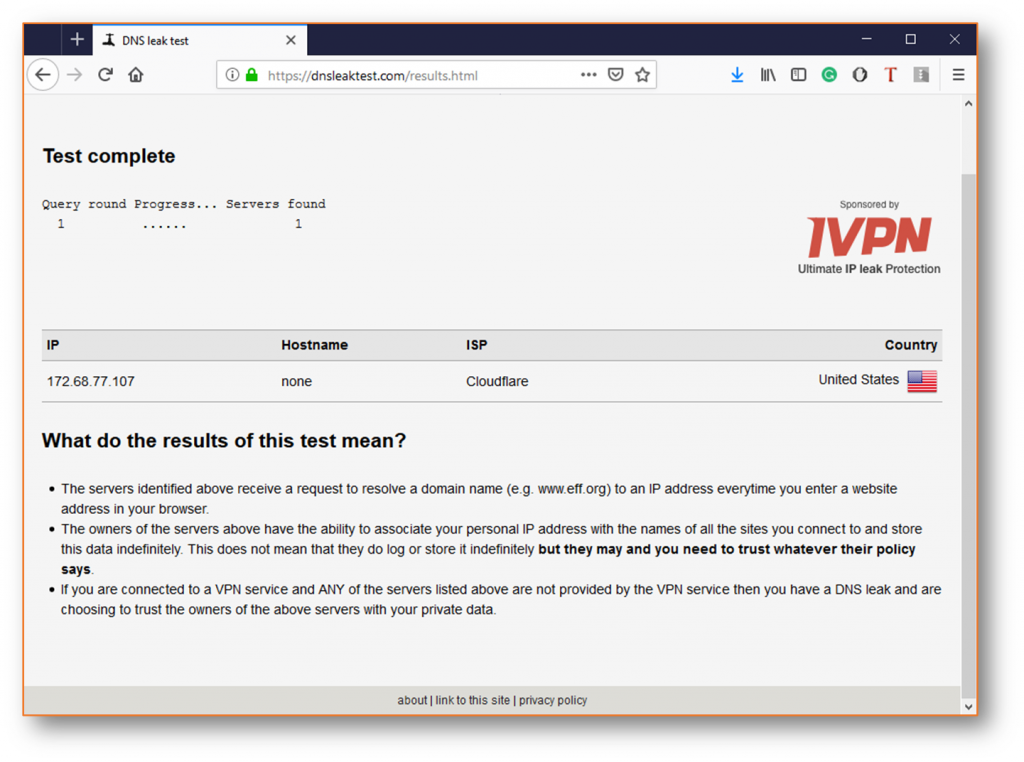
One thing to note is that you may occasionally see a discrepancy or two when switching between tests. This can be attributed to the various databases in use. As long as the IP address shown corresponds to your network or VPN, you’re fine.
What Causes DNS Leaks?
There’s a few main reasons these DNS leaks occur, again it’s typically the result of misconfiguration in some form – either a VPN or a network issue – or Microsoft Windows working against itself. It could also be something much more malignant, for instance if an attacker takes control of your router – in which case you’ve got much bigger problems than a DNS leak. So, we’ll assume it’s not that.
Major factors that contribute to DNS leaks:
- Your Operating System might have features that interfere with DNS traffic
- Your DNS is configured to use DNS servers that aren’t controlled by your VPN (or secured)
- Incorrect network configuration is causing DNS requests to leak
- IPv6 addresses are not supported
We’ll cover a few of the more common ones:
Improperly Configured Networks

Let’s start with network misconfiguration and work our way out. The most common type of network misconfiguration mostly occurs for remote workers that are connecting to the organization’s network via VPN/Split Tunneling. To understand this we’re going to have to take a (very) quick detour into DHCP or Dynamic Host Configuration Protocol. And rather than get too technical, we’ll just pick up the explanation in media res and catch DHCP in action.
Devices don’t have native IP addresses, they have MAC addresses, networks have IP addresses that they delegate to devices upon their connection. Say you’re visiting a friend and feel like checking your email, they give you their (probably never-changed) WiFi password and you go online. Before your device can start communicating on the network, it needs to have an IP address assigned to it (as well as receiving any other network configuration parameters that are in place). DHCP facilitates that.
Ok, back to DNS leaks, one of the aforementioned network configuration parameters that DHCP handles is DNS – it automatically assigns a DNS server to handle any requests. Ideally, things should be configured so that the DNS call is made to a secure DNS server, typically one under the auspices of your VPN. It’s when the DNS server that’s assigned (usually the ISP’s) is outside of that tunnel that DNS leaks occur.
This can be addressed at the client level, or it can be handled at the admin level, depending on your setup.
Not Supporting IPv6
IP addresses are more Ross Thomas’s area of expertise, and he’s written about them extensively (if you’re interested check it out), so we’ll keep this high level. When most people think of an IP address they think of IPv4 addresses, which are basically four sets of three numbers divided by a period. Those are on their way out. They’re being replaced by IPv6 addresses.
| IPv4 Address | IPv6 Address |
| 97.76.174.114 | 2001:0db8:85a3:0000:0000:8a2e:0370:7334 |
The reason for this is that we’re running out of IPv4 addresses. IPv4 is a 32-bit scheme, that’s good for about 4.3 billion addresses. The internet is now at the point of eclipsing that, so it’s in the early stages of a mass migration to IPv6 addresses, which will offer more than enough possible addresses to support the modern internet. As we’ve covered before though, these migrations typically take time and they don’t always go smoothly. Therein lies the rub.
Some VPNs just don’t support IPv6, which if you’re using a commercial service might be a sign to start investigating other options, but that lack of support can cause DNS leaks. If the VPN doesn’t support IPv6, or at least know how to block the requests, then the DNS requests are going to leak from the tunnel. Fortunately, IPv6 leaks aren’t quite as dangerous as regular DNS leaks, yet, it’s still not a situation you want occurring.
Again, ensuring your VPN supports IPv6 is the ideal route, failing that there is a protocol, 6in4, that places IPv6 traffic in an IPv4 wrapper for compatibility.
Or the nuclear option is you could just choose to block IPv6 traffic entirely.
Your ISP Is Using a Transparent Proxy
The whole debate over Net Neutrality looms over today’s conversation about DNS leaks. In the US, at least, they are now an even more relevant threat due to the end of Net Neutrality. The democrats in the US House of Representatives are currently working to restore those protections but given the fact the opposition party controls the Senate, which also need to pass the resolution, that’s likely going no where until the 2020 elections, at least.
Part of the reason this was even a debate at all though is that people do not trust their Internet Service Providers. Ignoring the troubling amount of consolidation that’s occurred within the industry, and the lack of consumer choice that’s led to, they have historically demonstrated a tendency to put their own profitability over the rights and privacy of their customers. And that’s being diplomatic. While they have so far behaved since the end of Net Neutrality (a well-calculated move), practices like transparent proxies – which is essentially your ISP forcing a DNS leak – are why the general public is loathe to trust ISPs.
As we covered earlier, many ISPs want you to use their own DNS servers – after all they get to record all of that valuable information about you when you use their servers – so they don’t handle it well when you configure your settings to use a third-party DNS server. Oftentimes they’ll deploy a transparent proxy, which intercepts all DNS requests and reroutes them to their own DNS servers.
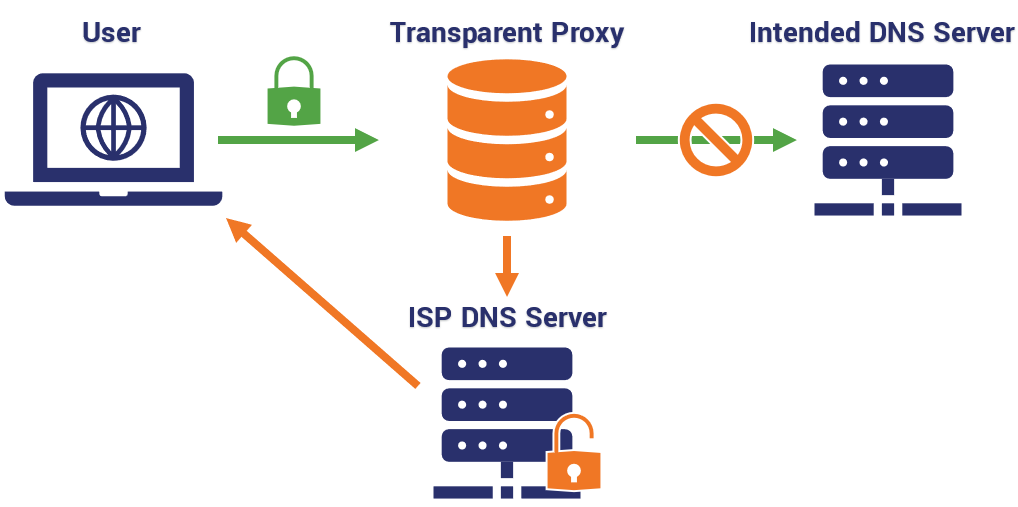
There is no one-size-fits-all advice for configuration, but generally you should have an option in your VPN to force the use of the VPN’s DNS servers. Alternatively, if you’re using an open-source app like OpenVPN, you’ll need to open the .conf or .ovpn file in your text editor and amend it to include the line:
block-outside-dns
In a moment we’ll discuss DNS-over-HTTPS and DNS-over-VPN a bit, this is one area where DNS-over-HTTPS has an edge. It sends its DNS requests via port 443, with the rest of the HTTPS traffic. That means that an ISP would have a much harder time using a transparent proxy to redirect your requests. Using DNS-over-TLS, which makes use of a dedicated port (853), is much easier to spot. Granted, redirecting those requests could still prove prohibitive, but blocking them entirely wouldn’t be.
You Might Need to Give Windows the What-For
Microsoft has produced a couple of features that have inadvertently caused DNS leaks in some contexts. Let’s start with Smart Multi-Homed Name Resolution, which was rolled out in Windows 8 and is intended to improve performance by sending out DNS requests to all available DNS servers and accepting the quickest response.

This is a perfect example of performance at the expense of security though. And DNS leaking is on the lower end of the severity spectrum. You can probably see how sending DNS requests to all available servers, as opposed to just using the secure DNS servers that you’d ideally have configured your network to use, could cause DNS leaks. It can also lend itself to DNS spoofing and poisoning, where an attacker can divert traffic to malicious websites by resolving DNS requests to the wrong IP address.
The biggest problem with SMHNR is that it’s difficult to disable, owing to the fact it’s built-in. The easiest way around it is to connect to your VPN using the OpenVPN client, where you can download a free plugin that takes care of the problem.
Failing that, there are two other options. If you’re a Windows 10 user, you can deactivate it using group policies:
- Type “Gpedit.msc” into the search field in your taskbar
- Double-click the file to open the editor
- In Computer Configuration, select Administrative Templates -> Network -> DNS Client
- Find the “Turn off Smart Multi-Home Name Resolution” field and select “Enabled.”
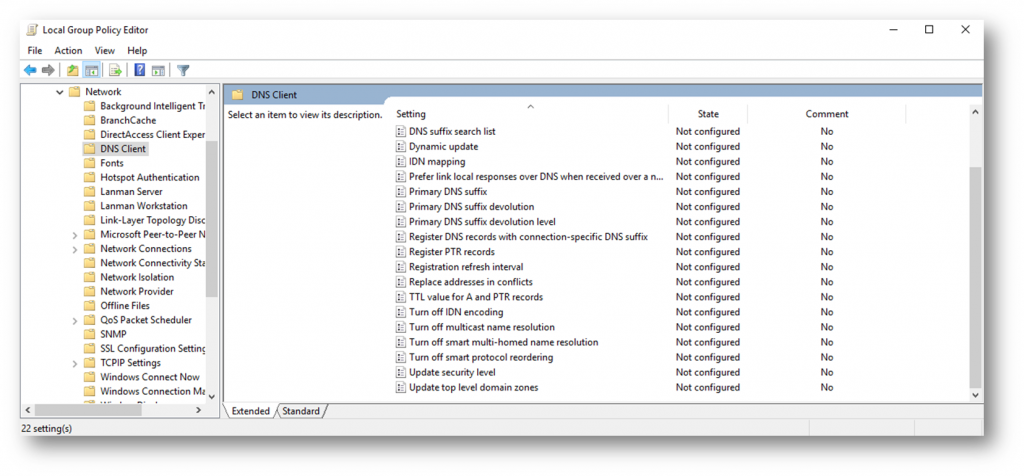
This won’t completely fix this issue, either. In the event the initial DNS request fails, SMHNR will kick on and send out a bunch of requests.
If you’re back on Windows 8 or 8.1, you can turn off SMHNR via the Windows Registry. Be careful if you go into the registry and make changes though, as you can really muck stuff up if you’re not careful. That’s why I’m not going to include how to bring up the registry, as a kind of technical barrier to entry sort of thing.
Here’s what you need to do: start by creating a file and naming it DNS.reg. Now add the following command lines:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\DNSClient]
"DisableSmartNameResolution"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters]
"DisableParallelAandAAAA "=dword:0000000
Now save it and double-click it to run the command. Voila.
The other Windows-based culprit for DNS leaks is called Teredo, which is a built-in feature that is supposed to assist with the aforementioned IPv4-to-IPv6 transition. Ideally it’s supposed to allow both schemes to co-exist peacefully.
The problem is that Teredo is also a tunneling protocol and if you’re not configured correctly it can take precedence over your VPN, which leads to DNS leaking. Fortunately, fixing this problem is a lot simpler than disabling SMHNR. Simply open your command prompt and type:
netsh interface teredo set state disabled
How Can I Prevent DNS Leaks?
We’ve already given some case-by-case advice for specific causes, but there’s also some higher-level things you can make sure you’re doing.
Use a VPN
Though we’ve basically written this article under the assumption that you should already be using a VPN, it bears repeating that a VPN server is still arguably the best way to prevent DNS leaks. Ideally, VPNs hide your traffic and obscure IP address. But, as we’ve illustrated, they’re not always successful in that endeavor. Still, using a VPN and ensuring that it’s configured to make DNS requests to its own secure DNS servers is a strong first step.
Use a Secure DNS Service
If you aren’t going to use one of your VPN’s DNS servers, make sure you’re configuring your network to use a secure DNS service that provides you with either DNS-over-HTTPS or DNS-over-TLS, we’ve gone in-depth before on the difference between the two. The important thing is that the connection is encrypted so that the requests can’t be seen by your ISP. Depending on whether you’re using DoH or DoT, the ISP may still be able to see you’re making DNS requests, but their contents will be encrypted and unreadable.
A good example would be Cloudflare’s 1.1.1.1, which supports both protocols and is also rated to be the fastest DNS service in the world.
Other examples of secure DNS services are:
- Comodo Secure DNS
- Main: 8.26.56.26
- Alternative: 8.20.247.20
- Google Public DNS
- Main: 8.8.8.8
- Alternative: 8.8.4.4
- Open DNS
- Main: 208.67.222.222
- Alternative: 208.67.222.220
Other Possible Fixes
Here are a few other suggestions and tweaks:
- If you’re using a VPN with an IP-binding feature, make use of it. This will essentially block any traffic that isn’t traveling through the VPN tunnel. You can also configure your firewall to do this if your VPN doesn’t support that feature.
- DNS Leak Tests are a good way to detect problems in your network, use them as part of a larger battery of tests and scans that you perform regularly.
- If you really want to stay on top of this, there are even VPN monitoring services that can keep track of your connections.
Let’s Wrap This Up
DNS leaks are a problem that not many people know about, much less truly understand. But as society grows more concerned with digital rights and data privacy, this WILL start to get more attention.

While the consequences of DNS leaking in the developed world can range from disconcerting to trivial, the consequences elsewhere sometimes rise to the level of being a human rights issue. Considerable effort has been made to encrypt connections between clients and servers. HTTPS can protect and obfuscate an internet user’s activity ON a website, but ISPs and third parties can still see that the user visited the website. And sometimes that, alone, can be enough to get someone in trouble.
HTTPS was a good first step, securing DNS interactions needs to be the next one. That’s the only way to prevent anyone from seeing what sites you’re visiting in the first place.
Considerable work has been done towards that end, but things like DNS leaks can undermine it all. So while it may seem like a non-issue, in reality, it’s a much bigger deal than that.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown