What Is a Firewall? Definition, Types & Business Uses
95% of Firemon survey respondents say firewalls are “as critical or more critical than ever” — let’s explore what firewalls are, how they work, and how they help to keep your organization (and data) safe from malicious internet activities…
Firewalls, the first of which Juniper Networks says was developed by the Digital Equipment Corporation (DEC) in 1988, have been helping good guys keep out the bad guys for the last 30 or so years. But what is a firewall? In the simplest terms, a firewall is one of your organization’s first lines of defense against external threats. It’s a tool that also provides you with visibility into your network traffic and enables you to have greater control of it.
Everyone from small businesses to large enterprises can benefit from using firewalls as part of their cyber defenses. But what is a firewall (more specifically)? What are the different types of firewalls? What does a firewall do? And how exactly does a firewall work? We’ll answer all of these questions and share insights from seven industry experts about how small businesses and enterprises can use network firewalls to their advantage.
Let’s hash it out.
What Is a Firewall? Network Firewall Security Defined & Explained
What is a firewall? A firewall definition can vary a bit from one source to the next. But in the most basic sense, a firewall is a tool that monitors, filters and controls the traffic entering or leaving your network. (These are known as ingress and egress traffic filtering, respectively.) Its job is to allow good (trusted) traffic to flow and to keep bad (untrusted) traffic from accessing or leaving your internal network.
To put it another way, firewalls keep bad guys out of stuff while letting everyone else use it normally.
Firewalls can be found protecting everything from your aunt Judy’s home computer to the networks of major governments and enterprises. Firewalls are available in both software or hardware formats. They also can be installed on your computers, various parts of your network, or in your cloud environment. Some companies even offer firewall as a service (FaaS) options that you can use!
Software vs Hardware Firewalls
Needless to say, firewalls (in one form or another) are everywhere. You’re likely using one right now! That’s because many antivirus programs come with firewalls, and operating systems typically have firewalls built in as part of their cybersecurity measures. Firewalls can operate on your existing routers or servers; they can also be a completely separate computer system. As a result, there are a lot of options out there to meet your specific needs and budget.
The definition of a hardware firewall is that it’s a separate appliance that monitors, filters and controls the traffic entering or leaving your network. A hardware firewall can be strategically placed in a network to optimize its functionality. This type of hardware is often coupled with a router to start at the root of the input/output stream. This differs from a software firewall, which you install on existing endpoint devices, servers, routers, etc. to regulate network traffic for that device. You’re likely wondering whether it’s better to use one over the other. A lot of the time, using both is a great option because they actually do things differently.
Firewall Definition Origins — Where Does the Term Come From?
What is a firewall in the original meaning of the term? Just for fun, let’s quickly talk about the meaning of firewall and where the term actually comes from. The term firewall is thought to have originated centuries ago (although no one knows exactly when). Essentially, a firewall (or “fire wall”) was originally a term used to describe a literal barrier that people would use to help prevent fire from spreading within their homes or storehouses. For example, brick walls served as physical firewalls, which is why people typically associate firewalls with brick wall graphics like this:

According to Merriam-Webster:
“In the mid-1600s, firewall named an earlier form of protection: an innovative wall made of noncombustible material to prevent the spread of fire. Such walls completely separated two parts of a building from the basement to above the roof.”
So, as you can see, the firewall definition has changed over time, but the general purpose remains the same: It helps to protect the things you value from dangerous factors. In the case of firewalls for cybersecurity, they keep out unwanted, potentially dangerous users/traffic.
So, now that you know what a firewall is, let’s go a little more in depth to talk about what it actually does.
What Does a Firewall Do?
In the most basic sense, a firewall is what helps to keep your organization’s internal network (or other devices, data, applications, etc.) safe from outside threats. More specifically, the purpose of a firewall is to allow safe, legitimate traffic through while keeping harmful traffic out. With the right type and configuration, a firewall can also prevent traffic from leaving your network as well.
Seems simple enough, right? But there are a lot of ways to go about doing that.
For example, here at our U.S. office of the SSL Store, we use a few firewalls to protect our network and devices. Of course, we have software firewalls that come with our antivirus and the built-in Windows Defender running on all of our endpoints. But in addition to that, we’ve also got a next-generation firewall (NGFW) appliance protecting our gateways and overall network from unwanted and untrusted traffic, plus web application firewalls to protect our websites.
Traditional firewalls inspect incoming and/or outgoing traffic and are programmed to either allow or block specific types of data packets. All data transmitted across a network (or between separate networks) does so in either TCP (transmission control protocol) or UDP (user datagram protocol) data packets. Each of these packets contains header information that communicates where the data comes from and where it’s going. TCP packets contain more packet header data than UDP data packets do, which means that they’re typically larger in size.
By inspecting the traffic coming into your network, you can prevent malicious code (viruses, malware, etc.) from entering your network where it would otherwise put your data and systems at risk. Of course, there are also firewalls that operate at the application layer, too. These target the traffic that flows to and from your application or service to determine whether traffic should be allowed through.
So, in summary, a firewall:
- Checks or enforces security policies (rules),
- Monitors or records network traffic that passes through it, and
- Limits internal network exposure.
Is a Firewall All You Need?
So, is a firewall a be-all, end-all cybersecurity tool? Heck no! A firewall is just one of many tools you should have in your cybersecurity toolkit. A firewall should be just one of multiple layers of security that help you to protect your organization and its data — it shouldn’t be your only one.
If your organization’s cybersecurity defenses solely rely on the use of a firewall without any other layers of protection, it would be like building walls for your home with holes for doors and windows but not bothering to install doors, windows, or locks to secure them. Sure, it might stop some threats, but you’d be leaving yourself wide open to plenty of others that would just go around them.
This is why it’s often good for organizations to have multiple firewalls to offer greater coverage and protection from different types of threats that use different attack vectors. (We’ll talk more about firewall needs for small and midsize businesses (SMBs) and enterprises a little later.) However, I do want to take a moment to mention that there are a couple of common misconceptions about firewalls in terms of their capabilities.
The National Institute of Standards and Technology (NIST) reports in SP 800-41 rev. 1 that many cybersecurity capabilities are often attributed to firewalls that actually belong to the other technologies that they’re often paired with. As such, organizations are entrusting firewalls with tasks that they weren’t originally designed to do. As Illumio reports:
“81 percent of respondents will leverage firewalls for segmentation, despite the fact that they are slow to implement, don’t adapt, are complex to work with, and were not built to serve this function.”
All of this is to say: Make firewalls part of your overall cybersecurity defenses but don’t forget to layer on other security measures, too.
How Does a Firewall Work?
Okay, now it’s time to get into the nitty-gritty part of the blog. The quick answer to the question “how does a firewall work?” is “it depends.” I say that because there are actually multiple types of firewalls that serve different functions and purposes. (We’ll talk about several of those shortly). Some firewalls are very basic in nature while others are more advanced and have greater capabilities.
Firewall Rules
In general, however, firewalls operate using a set of security rules that are known as access controls. Firewall rules typically include a few key pieces of information:
- Source IP address,
- Protocol,
- Port number, and
- Destination IP address.
The firewall uses these rules (or access controls) to allow or block traffic.
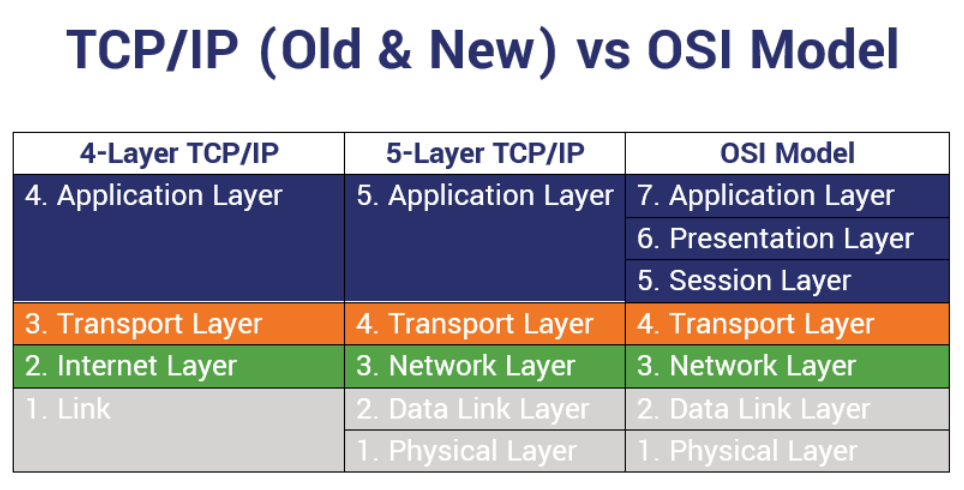
Firewalls & TCP/IP Layers
Traditionally, firewalls would protect the different layers of transmission control protocol/internet protocol (TCP/IP) model. While basic firewalls typically inspect traffic and work on the lower TCP/IP layers, the more advanced firewalls tend to operate throughout all of the layers.
Nowadays, however, people often associate modern firewalls with the seven layers of the open systems interconnection (OSI) model rather than the four layers of the traditional TCP/IP model or five layers of the new TCP/IP model.
To establish a TCP connection, this involves the use of a TCP handshake, or what’s known as a three-way handshake. If the handshake’s successful, then data exchanges, and then both parties agree to close the connection via a four-way closure. Some types of firewalls inspect this handshake to ensure that it’s valid.
Let’s take a few moments to go over how the most basic types of firewalls (packet filtering firewalls) work. This will help you dip your toes into the water without falling in head-first. (For our more advanced readers, we’ll get into some deeper water here shortly.)
Stateless Firewall (Static Packet Filtering)
The first type of firewall we’re going to talk about here is a stateless firewall. A stateless firewall is the most basic kind — it’s basically a packet filter that operates on OSI layers 3 and 4. This is the most basic type of network perimeter firewall.
Static packet filtering is a process that relies on the use of access control lists, or ACLs. It doesn’t track or keep records of active traffic sessions; it just looks at the traffic as it arrives at or leaves the network and compares it to a set of rules that serves as an access control database.
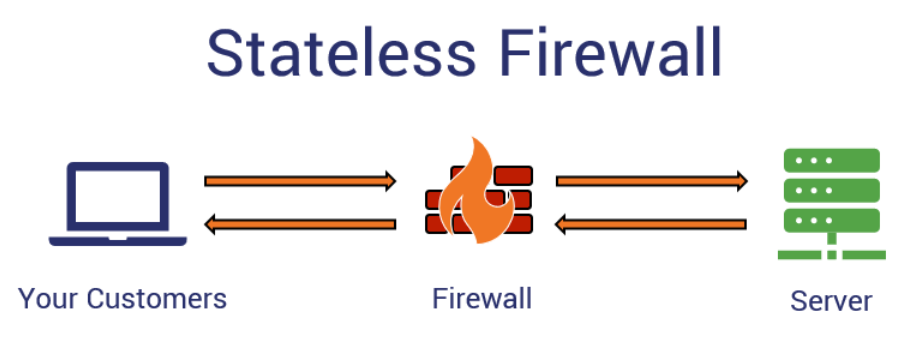
For traffic to be able to enter and leave a network, the firewall has two rules — one for incoming traffic and the other for outgoing traffic. The stateless firewall compares the packet information to the rules. If the source and destination info match and it has an “allow” rule, the traffic can flow in to the server. When the server responds and sends information back, the firewall again consults that rule base. So long as the information matches, then the data’s good to go and essentially gets the green light.
| Rule | Source IP Address | Source Port | Protocol | Destination IP | Destination Port | Action |
| #1 | 192.0.2.255 | 80 | TCP | 203.0.113.255 | 80 | Allow |
| #2 | 255.255.255.255 | 443 | TCP | 254.254.254.254 | Any above 1023 | Allow |
This table is a basic example of an access control list of firewall rules that stateless packet filtering firewalls use to route traffic.
Rule-Based Packet Filtering Is Like Buying Alcohol in the U.S…
So, let’s think of this like when you try to purchase alcohol from a store in the U.S. When you go to the store, you have to go there during the store’s operating hours and you walk in through the approved entrance. When you grab your beer or liquor, then you go to the register to complete your purchase. In the U.S., the rule is that no one under age 21 can purchase alcohol. If you don’t meet that rule (i.e., you’re underage), then you’re out of luck. You won’t get to buy the alcohol and you’ll likely get kicked out of the store (if the cops don’t get called on you).
Firewall packet filtering is much the same. For example, if an organization uses a stateless firewall, it inspects your packet data to determine whether or not to allow you to connect. If your IP address and port information match the info on the access control list, you’d be allowed to connect.
Stateful Firewall (Dynamic Packet Filtering)
This type of firewall, although it still involves packet filtering, is more dynamic and can handle more complex rules. A stateful firewall records the “state” of each active session (in a table format) for reference. This allows the firewall to carefully monitor and control traffic inbound and outbound traffic. A stateful firewall, which also operates on OSI layers 3 and 4, consults an access control list for incoming traffic that contains a one-way rule of either allowing or blocking traffic to and from the server.
Once an active incoming traffic session starts, however, things get a bit different. The firewall keeps tabs on the session’s traffic flow and creates an active session table that includes info about the source and destination IP addresses and ports. Responses from the server to the user in that active session have to return through the firewall, which refers to that active session table and verifies the information matches. If the outbound traffic matches, it also gets the green light. If it doesn’t, or it’s traffic that falls outside of that active session table, the traffic proceeds no further and essentially dies at the firewall.
Traditionally, firewalls were stateless packet inspection firewalls (the first kind we talked about a bit ago). However, most of the modern firewalls we use today are stateful firewalls. Many businesses today use a mix of stateless and stateful firewalls. It’s also important to note that many modern firewalls operate on the application layer rather than the network or transport layers.
Breaking Down the Types of Firewalls & Their Different Terminologies
Proxy firewalls. Filtering firewalls. Network firewalls. Computer firewalls. Software firewalls. Hardware firewalls. WAF. NGFW. The list goes on and on. Needless to say, there are a lot of terms to know when it comes to firewalls. And this is what makes things a little tricky when you’re trying to wrap your brain around all of them.
You see, IT companies and experts often refer to firewalls in different ways by using different language. They also lump them together into varying categories, too. They could talk about them in terms of:
- What they are (software or hardware appliances),
- Where they are (on prem or in the cloud), and
- What they protect (computer, network, or web applications).
This is why you might see one article talking about “5 types of firewalls” and then another saying that there are “8 different types of firewalls.” Sigh.
For someone who is new or less experienced within the industry, this can be confusing. (Heck, it was confusing for me when I was trying to learn about it since there are so many different names for things.) The reason why this is so non-specific is because there are there are multiple types of firewalls, and they’re often categorized by their different formats, traits, or functionalities.
But when people lump them all together with no apparent rhyme or reason, it’s the equivalent of categorizing vehicles and saying that the categories include cars, SUVs, Hondas, blue ones, red ones, and V6s. It just doesn’t make sense because they’re not comparing the same things. And this leaves people with more questions than answers.
Thankfully, some organizations traditionally categorize firewalls in terms of their:
- Processing modes — This category refers to the operations or functionalities of the firewalls.
- Development eras or generation types — This category refers to the period of when the firewall was engineered.
- Implementation structures — This category refers to the types of environments that firewalls are implemented in (residential networks, small/home business, commercial or enterprise, etc.).
For the purpose of this article, we’re just going to talk about the processing modes and generations of firewalls.
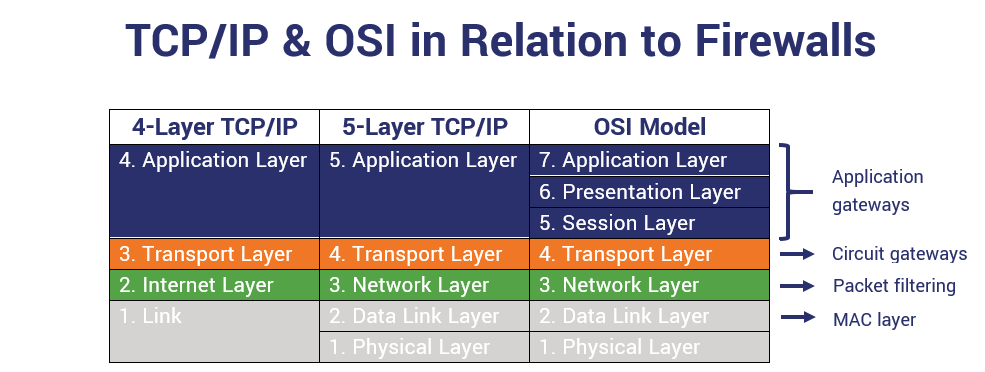
5 Types of Firewalls Categorized by Processing Mode
When considering processing modes, there are several major categories to consider:
- Packet filtering (which we’ve already talked about),
- Proxy or application gateway,
- Circuit gateway,
- MAC layer, and
- Hybrids.
1. Packet Filtering Firewalls
We’ve already covered this one in the last section, but we’ll just provide a quick summary here as a reminder. Packet filtering firewalls:
- Traditionally were stateless but are more commonly now stateful packet filters;
- Enforce security policies and rules;
- Monitor inbound and outbound traffic; and
- Have the ability to record key pieces of information about sessions.
2. Proxy or Application Gateway Firewalls
As the name implies, a proxy firewall serves as an intermediary that allows two systems to communicate indirectly via a client. This is typically done through the use of a proxy device or in the cloud. Basically, the firewall receives requests from the client and determines whether to allow or block the traffic. By preventing direct connections to transfer data, it offers greater protection to the internal network.
This type of firewall also is known as a gateway firewall or an application-layer firewall because its traffic filtering takes place at the OSI application layer. The advantage of this type of protective barrier is that it’s the most thorough type of firewall. However, this means it’s also the slowest because it checks destination IPs, validates TCP handshakes, and involves deep packet and stateful inspections.
3. Circuit-Level Gateway Firewalls
A circuit-level firewall is responsible for verifying the TCP handshakes of incoming traffic. It works at the OSI session layer, which falls between the transport and presentation layers (both of which are beneath the application layer).
Because this type of firewall doesn’t inspect packet information or verify destination IP addresses, it makes it one of the most efficient types of firewalls. However, it also makes it susceptible to malicious code that could be transmitted within those packets.
4. MAC Layer Firewalls
The MAC layer firewall, or what’s known as the media access control layer firewall, operates within one of two sublayers within the second layer of the OSI model (the data link layer). The two sublayers — logical link control (LLC) and MAC — fall between the network and physical layers of the OSI model. The purpose of the MAC sublayer is to control device interaction and data flow.
This type of firewall filters packets based on their ACL entries, which are tied to the MAC addresses of the accessing device. This allows the firewall to determine whether to block or allow the packets to access the network.
5. Hybrid Firewalls
As the name implies, a hybrid firewall is more comprehensive than other types of firewalls. This type of firewall performs a combination of processes and capabilities of its previously mentioned counterparts, including packet filtering, application layer proxy services, or even circuit gateways.
Other Types of Common Firewalls
- Web application firewalls (WAFs) – A WAF is one that monitors the traffic that enters or leaves your network via HTTP and HTTPS connections. As such, this type of firewall operates on OSI layer 7. This differs from a traditional network firewall, which focuses on traffic entering and leaving your overall network and operates on OSI layers 3 and 4.
- DNS firewalls — This type of firewall you deploy at your DNS, meaning that it’s outside the perimeter of your organization.
- Network address translation (NAT) firewalls — This type of firewall acts as an intermediary by allowing you to connect multiple devices to the internet via a single visible IP address. This helps to protect your individual device IP addresses from cybercriminals’ prying eyes.
- Next-generation firewalls — Despite the name, a next-generation firewall (next-gen firewall) isn’t actually all that new. It’s been around since the late 2000s and is a bit of a jack-of-all-trades in terms of what it can do. Many NGFWs wear multiple hats, serving as routers, firewalls, VPNs, and IDS/IPS solutions.
(Note: AN NGFW isn’t the same thing as a unified threat management (UTM) device or service. While a UTM frequently includes a NGFW, it offers other security measures that an NGFW doesn’t cover.)
Firewall Generations
When people talk about the “generations” or “eras” of firewalls, they’re referring to the progression of firewall technologies and where the particular firewall falls within it. Of course, people categorize generations differently (yeah, I know — let’s just make it as confusing as possible, right?). Some people say there are three generations of firewalls, others say there are four or even five generations of firewalls.
For our example here, I’m going to go with those who says that there are four generations of firewalls, and each offers different capabilities:
- First generation: This is a packet filtering firewall that offers basic network security by setting rules. Remember the stateless and stateful firewalls we talked about earlier? Yeah, they would fall into this category.
- Second generation: This type of firewall is one that offers deep packet inspection (DPI) capabilities. Circuit level firewalls would typically fall within this era of firewalls.
- Third generation: This type of firewall operates at the application layer (OSI layer 7). A next-gen firewall.
- Fourth generation: This generation of firewall is geared for on-prem and public cloud implementation, according to Forrester.
Okay, phew. You now know what a firewall is, what it does, how it works, and what the different types of firewalls are (as well as how they’re often categorized). Now, it’s time for you to figure out how to apply all of this knowledge to your own organization.
Does My Small Business Need a Firewall?
In a word? Yes. However, if you have a small business, you may be wondering if a firewall is really necessary and isn’t something you could just skirt by without for a while. After all, you’re a small target and cybercriminals only go after the big guys… right?
Wrong. Delete that line of thinking from your mind immediately because it’s a dangerous mindset for any small or mid-size business to think that only a minimum firewall — or no firewall at all — is acceptable. It’s this type of dangerous thinking — believing that you’re not an appealing target — that leads to SMBs being a major target for cyber attacks and breaches. In fact, BullGuard reports that nearly one-in-five SMBs experience cyber attacks or data breaches. Their research also shows that 23% of the SMBs they surveyed in the U.S. and the U.K. don’t even use endpoint security measures.
Peter Smythe, owner and founder of WePrivacy, equates using the right firewall to meet your organization’s needs is like choosing the right tires for your car:
“Yes, [a basic firewall] offers a basic level of protection but it’s not a full solution. It’s like saying the tires that came with your car are enough. Sure they will do their job but getting tires that meet your driving style and needs is an important investment.”
– Peter Smythe
Can I Get Away Using a Basic Firewall?
But what if you use the firewall that’s built in with your computer or antivirus? Is that alone enough of a defense? Perhaps some people argue yes. But Jay Akin, CEO of Mushroom Networks, isn’t one of them.
“Having a firewall on your windows PC or as an appliance does not automatically provide security — they still need to be configured and managed correctly. By centralizing security via a firewall appliance (or a cloud delivered security approach) vs many firewalls on PCs, the organization will avoid a potential misconfiguration and mismanagement nightmare of the too many individual firewalls.”
— Jay Akin
But one of the biggest hindrances when it comes to managing firewalls is a lack of automation. FireMon’s 2019 State of the Firewall report states that more than 65% of survey respondents don’t use automation.
Another tech expert, Heather Paunet, Senior Vice President of Products at Untangle, also chimes in with her concerns. As a former software engineer, Paunet she says that many small businesses get a false sense of security by relying on built-in firewalls alone:
“While many vendors or software companies may include firewall features within their applications, these features may not always meet the requirements to defend against emerging threats. For example, if Windows does include a firewall feature within their software application, how often is this updated? And if it is updated from the Microsoft side, are these same updates and patches being routinely implemented into their customer’s network?”
— Heather Paunet
Paunet goes on to state that taking a multi-layer approach to cyber security is a better bet for small businesses:
“In addition to the stateful firewall included in these applications, how can SMBs address other network points that may become gaping vulnerabilities? With a next-generation firewall, advanced web filtering, access control, and other leading cybersecurity features can create multi-layered solutions protecting an SMB’s network more extensively than any stateful firewall could.”
— Heather Paunet
Where Are Firewalls Are Most Needed?
The answer to this question depends on your business and its specific needs.
Aaron Phillips, Channel Platform Enablement at Sectigo, says that it’s important for small businesses to figure out the best use and configuration of their firewalls.
“One of the features of a firewall is controlled access. For small businesses to get the most, they should take some time to consider which of their computers needs access to servers, websites, internal documents and more.”
— Aaron Phillips
For IT and cybersecurity expert Greg Scott, it’s all about blocking threats at the greatest distance possible from your internal network:
“Put a firewall at your network boundary equipped with diagnostic tools and the ability to selectively log packets in and out of your network. With the right firewall, you can help internet service providers diagnose problems in their own systems. Which will enhance your credibility when you call to report problems and the people on the other end of the phone barely speak English.
If you’re a retailer with POS systems, put those in a DMZ network and strictly regulate which systems are allowed to interact with them. Alarm whenever they try to interact outside that list. This additional layer of defense will help keep your POS systems safe from the global pandemic of POS invasions and stolen credit cards.”
— Greg Scott
But what about a web application firewall? Surely you don’t need one of those as well…
Alex Peña, Senior Product Marketing Manager at Sectigo, says that managed WAFs are among the most essential firewalls for SMBs.
“The best firewall for a small business to implement is a fully managed cloud based web application firewall (WAF). With the challenges facing SMBs by remaining at the forefront of the ever evolving threat vectors, having a firewall that continuously updates its rule sets in real-time and protects against the OWASP top 10 is crucial.”
— Alex Peña
But what is it take makes this type of firewall so useful for SMBs and the security of their websites?
“Matching a WAF that has the ability to enable fine grained controls such as IP filtering while also enhancing it with additional solutions like a global anycast CDN and DNS will immensely strengthen a websites security protocol.”
— Alex Peña
Why You Shouldn’t “WAFfle” When It Comes to Web Application Security
Sorry, I couldn’t resist. Anyhow, Peña says that even for businesses whose web hosts have their own firewalls, it’s important that they use a web application firewall.
“If your apartment complex has a security gate at the front entrance, would you leave your condo unit’s front door unlocked or even eliminate it entirely?
Firewalls enabled by hosting companies at the network level work in the same fashion. They provide some protection by protecting the network infrastructure but attacks and threats are aimed at the individual sites themselves. Bad actors target specific website vulnerabilities not only those at the network level.”
— Alex Peña
Firewall Needs for Enterprises
But where’s the line between what’s considered acceptable firewall security for small businesses versus larger enterprises? Ross Thomas, our IT administrator here at The SSL Store, says that many small businesses can get away with using a main firewall and some software-based firewalls. But when it comes to larger enterprises or those that handle more sensitive data (such as hospitals, banks, etc.), then it’s better to drill down and use more specific firewalls to protect different systems.
Daniel Cooper, Former CTO and Current Managing Director on Firewalls for SMBs at Lolly Co technology consulting services, also stresses the importance of enterprises going beyond the minimum to protect their networks, web apps and data:
“I would say to an enterprise that considers Windows Firewall adequate that it is only the first line of defence and is nowhere near enough. It has several limitations including:
– It doesn’t protect you from ransomware
– It does not have advanced features such as an email or browser protection
– It slows down your computers during a scan”
— Daniel Cooper
To remedy some of the concerns that enterprises face regarding firewall implementation and management, Akin says that enterprises should consider alternative options: “For larger organizations, cloud delivered security is certainly one of the more modern approaches versus individual security appliances at each branch location.”
For Scott, it’s more important to focus on finding tools that are flexible enough to meet the specific needs of your enterprise:
“I spent 20+ years building custom firewalls with iptables scripts and various diagnostic tools. Commercial firewall vendors use the same tools. Enterprises need firewall systems that offer maximum flexibility because everyone’s network is different.”
— Greg Scott
But for anyone who thinks that cloud technologies mean that firewalls are no longer necessary, Scott offers a word of caution:
“With the rise of the cloud, lots of people say firewalls are obsolete. They’re wrong. Every enterprise needs something at its boundary to regulate traffic logically in and out. That’s what firewalls do.”
— Greg Scott
Final Thoughts on Firewalls, Definitions & Their Uses for SMBs & Enterprises
Firewalls are as integral to cybersecurity as air pump is to an inflatable raft. Sure, you may float along for a while, but you’ll eventually sink if you don’t refill it. Cybersecurity is the same way. Without firewalls, you may be lucky enough to avoid cybercriminals who are looking for ways to access your network for a little while. But, eventually, they’ll always come knocking.
In this article, we’ve covered what a firewall is (including a firewall definition), what a firewall does, how it’s used, the different types that are available and how you can deploy them to protect yourself and your organization’s data. But to quickly recap a few key takeaways for our skimming readers:
- Firewalls are the first line of defense between your trusted network traffic and the outside world (untrusted traffic).
- Firewalls operate on different levels of the OSI model — everything from the application layer down to the data link layer.
- There are multiple types of firewalls, and people within the industry love to categorize them in different ways. Most commonly, they are categorized in terms of their processing functions or their development generations.
- Firewalls are a must for individuals, small businesses and large organizations alike. And while small businesses can get away with fewer firewalls than an enterprise, they still should take a multi-layered approach to network security.
- Fully managed cloud web application firewalls are among the most important for SMBs because of their continually updated rule sets web app vulnerability protections.
- As long as there’s traffic heading to and away from your network and web applications, firewalls will always be a must.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown