What Is Blockchain and How Does It Work?
Lifting the lid on the tech we’ve all heard so much about, yet many of us haven’t wrapped our heads around… yet
Although the term “blockchain” has become part of our modern lexicon, a lot of people are left asking, “what is blockchain?” Is it a cultural phenomenon? A reimagining of the internet’s potential? A fool-proof answer to online security issues?
There are more questions surrounding the nature of blockchain than there are cryptocurrencies in existence — and, believe us, there are a lot of cryptocurrencies. (More than 7,850 as of the publication of this article, according to coinmarketcap.com.) But there remains plenty of confusion regarding what blockchain is, what it does, and how blockchain works. You might know that blockchain relates to cryptocurrencies in some way, but you might not know in what capacity, or what other industries this technology applies to.
While nobody is entirely sure who Satoshi Nakamoto is — potentially the creator of Bitcoin (the first cryptocurrency), according to Newsweek — there’s no denying that blockchain is a technology that’s developed, evolved, and grown into one of the defining inventions of our age. With new blockchain benefits emerging every year, it feels as though we’re only at the beginning of a truly remarkable technology.
With that in mind, let’s focus on the big question. What is blockchain, really? And how does blockchain work?
Let’s hash it out.
What Is Blockchain? Blockchain Definition and Explanation
In the most basic sense, a blockchain is a publicly-managed and verified record of transactional data. All of the data blocks are ordered chronologically and are connected to form a “chain” — hence, the term “blockchain.” All of the chain’s old blocks of data are permanent; they can’t be modified or altered retroactively.
Blockchain is an alternative to traditional centralized systems (like the traditional banking and financial system), which is why blockchain is integral to many cryptocurrencies. However, it’s not only useful for cryptocurrencies — there are other potential applications for blockchain in other industries and sectors as well (although Gartner predicts that 90% of such projects for supply chains will fizzle out by 2023). We’ll explore some of those potential applications later in the article.
As far as a technical blockchain definition goes, this technology is a decentralized and distributed public ledger constructed around a P2P (peer-to-peer) system. This system can be openly shared among its users to form an immutable record of transactions. Each of these transactions are time-stamped and indelibly connected to the previous chain link. Each time a transaction is added, the fresh data forms a new block at the end of the chain.
Here’s where it gets clever (and hard for cybercriminals to manipulate). Blockchain is only able to be updated by consensus. That is, the participants in the chain system must agree on additions and changes to the chain itself — something which becomes significant when you factor in that nothing entered into the blockchain can be removed. Verifiable and auditable, blockchains allow for precise and transparent record-keeping.
Blockchain: The Google Sheets of Cryptocurrencies
If that all sounds a little confusing, let’s give you a neat analogy based upon something we all know and love: spreadsheets. Here, we’ll consider the use of traditional Excel spreadsheets versus Google Sheets, and how Google Sheets is similar to a blockchain (but with one very important difference).
Imagine, if you will, a spreadsheet that has been duplicated 10,000 times across a wide network of computers. Now, picture in your mind that this network has been designed to keep this spreadsheet updated in real time. That’s it — that’s blockchain, right there. Let’s delve a little deeper into this analogy and see what else we uncover.
Traditionally, spreadsheet documents that were shared for collaborative purposes had to undergo a certain process in order to make that happen. An Excel document would have to be created, saved, and emailed to a recipient who’d then be asked to make their edits, save once again, and email it back. It worked — there’s no question about that — and there are clear benefits to “locking out” the other party while the editing is underway (for example, in the world of banking, you can’t have two owners manipulating or changing the same record at the same time). However, for many users, it wasn’t the most efficient way of doing things.
You’d run into a variety of spreadsheet management issues. People would lose track of the most recent versions of documents or wind up updating old versions of the spreadsheet. There had to be an easier way for everyone to have access without having 10,000 versions of a spread in different iterations, right?
Enter Google Docs (or, more specifically, Google Sheets) — a real game changer. With a Google Sheets file, all parties with access to a single “live” version of the spreadsheet can view, edit, and modify the document simultaneously at any given time. (While this isn’t a perfect analogy, it gives you the general idea of how a blockchain works.)
Therein lies a whole number of benefits, which are inseparable from how blockchain actually works. All of the data held on a blockchain exists as a continually reconciled and shared database, and the plus-points that arise from this system are fairly easy to see, and not by any means just in the realm of document sharing. However, unlike a shared Google Sheets file, the blockchain isn’t stored in one location, ensuring that any data it keeps remains public and easy to verify. What’s more, hackers can’t get into a centralized version of the data, and the data is accessible to anyone on the internet at any given time.
How Blockchain Works
Now that we understand what blockchain is, it’s time to actually explore the components of the process and answer the question “how does blockchain work?” How blockchain works, to put it simply, is through a time-stamped series of data records, managed by a group of computers not under the ownership of any single entity, individual, or corporation. The blocks of data (which are, indeed, referred to as “blocks”) are bound to one another with the use of cryptographic principles, forming the eponymous “chain.”
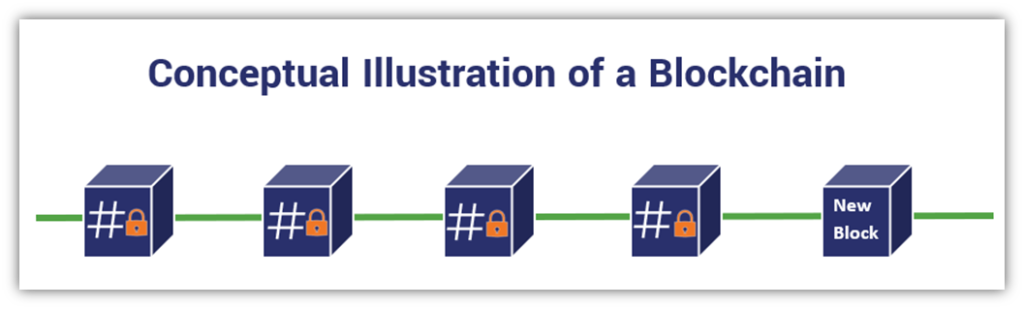
Public blockchain ledgers are primarily managed autonomously and are used in peer-to-peer networks to exchange data between connected groups of parties. As is the nature of blockchain, there’s no need for an administrator. The users work together as a collective administrator. Another form of blockchain, generally known as a permissioned or “private” blockchain, allows an organization to both create and administer transactional networks that can be used with partners, either internally or from one company to another.
Every blockchain transaction goes through the same steps regardless of whether it’s used for financial transactions or product tracking. The basic principle of the operation of any blockchain can be broken into four distinct, contiguous steps:
- A record is made of each transaction. This record, which contains certain details of the people making the transaction, is authenticated using the digital signature of each.
- Each transaction is verified to ensure its validity. This verification process is completed by the computers connected to the network, each of which independently checks to ensure that the trade is legitimate. Because this is a decentralized process, it means that every node in the network needs to agree before the process can be completed.
- Once verified, each transaction is added to a block that gets hashed. “Blocks” are basically groups of transaction records, and each one is unique. Each block also carries a code known as a hash value (or hash digest), which both uniquely identifies it and calls out its position within the blockchain. The hash also ensures the integrity of the data to show that it hasn’t been modified since it was recorded in the block.
- Once complete, the block is added to the end of the blockchain. This brings us to the end of the blockchain creation and verification process. Once one block is complete, another block will soon follow — typically within just a matter of minutes.
The Three Pillars of Blockchain That Make It Hard to Fake
Another important aspect of understanding blockchain involves the so-called “three pillars” of the system. A quick aside — there’s some real dispute in the online community regarding just how many pillars blockchain features. Some place it as seven, others say nine. For simplicity’s sake, we’re going to stick with three. These are:
- Decentralization
- Transparency
- Immutability
Blockchain Pillar 1: Decentralization
Let’s kick things off with the first one. Up until the arrival of blockchains, we were accustomed to services that were fully centralized. Look at banks, for example. Your high street bank collects your money, and you can’t access it online (or in person) without directly going through the bank’s centralized systems.
While these centralized systems, like traditional spreadsheets, have served us well for many years, they are far from perfect. When a centralized system is upgraded or changed, everything grinds to a halt. If it gets shut down, anyone who needs to use it is automatically shut out.
Because blockchains are, by their very nature, decentralized systems, the information is owned by every node in the network. As such, you don’t need to go through third parties in order to interact with the data. This was one of the driving forces behind the rise of Bitcoin. Quite simply, you and you alone are in charge of your money, and there’s no need for a bank to be involved.
This is not to say that Blockchains are not vulnerable to hackers. There have been plenty of high-profile hacks of blockchains, and owners have been guilty of de-anonymizing data and irreversible public disclosure. On the whole, however, the decentralized nature of blockchains means that they are more difficult to hack than traditional infrastructures.
Blockchain Pillar 2: Transparency
Interestingly, the concept of blockchain transparency is one which is often misunderstood. How can you achieve absolute privacy and absolute transparency at the same time? Well, via the use of complex cryptography and public addresses. For example, an individual’s transaction history will be represented by an encrypted code known as ciphertext. While Bitcoin.org says that anyone can see the balance and transactions from a particular address, this makes tracing this information to an individual a lot more challenging.
Most blockchains are pseudonymous in this way, but that doesn’t mean that they’re completely anonymous. Nonetheless, in this system, real identities can be kept mainly secure, as long as users are careful to do so. According to Bitcoin.org:
“Since users usually have to reveal their identity in order to receive services or goods, Bitcoin addresses cannot remain fully anonymous. As the block chain is permanent, it’s important to note that something not traceable currently may become trivial to trace in the future. For these reasons, Bitcoin addresses should only be used once and users must be careful not to disclose their addresses.”
Blockchain Pillar 3: Immutability
At the center of blockchain is the concept of immutability. This means that once something has entered the blockchain, it cannot be altered, changed, or tampered with. This transparent record also aids in preventing double spending.
As far as financial security goes, this could be valuable in an ideal world. Imagine how many money laundering cases could be stopped in their tracks once people understood that company accounts would be significantly harder to manipulate, and books could no longer be cooked. However, considering that Bitcoin and other cryptocurrencies like Monero are still the overwhelming currencies of choice for cybercriminals, it’s still uncertain whether this would have the ideal positive impact one would hope for.
Which Industries Currently Use or Could Benefit from Blockchain?
Blockchain is working to establish a new era of trust in online communication. And although it’s still a relatively new technology, it’s proving its usefulness and effectiveness across a number of vital industries.
The potential of these blockchains remains at a fever pitch, and has manifested in many surprising ways. For example, after a number of customers fell ill after eating a batch of lettuce infected with e-coli, IBM and Walmart worked alongside each other to create a blockchain which tracked fresh goods from the farm to customers’ homes. Once this blockchain was established, Walmart’s produce could be automatically followed via “‘smart contracts,” which helps reduce human error and creates a chain of accountability along the way.
Some other companies IBM has worked with on its blockchain project include Tyson Foods, Nestle, and Golden State Foods, protocol.com reports. But changing decades’ old supply chain processes isn’t an overnight process. Implementation takes years to roll out, and IBM is still working on doing so with many of these companies.
It should come as no surprise that financial services is one industry in which blockchain is poised to shine. The technology essentially works to remove third parties from financial transactions. There’s no need for bankers, brokers, or government backers to get involved, and that means no fees for the individual. However, with those benefits also come some potential disadvantages. For the average user, their trust in a financial system relies on things such as being able to chargeback a payment, knowing they have fraud protection, and that they are regulatory bodies over financial systems.
Healthcare is another industry making profound use of blockchain. In this context, the technology serves as a collaboration network, allowing various parties to exchange and develop information in real time. When the technology is applied to a patient’s electronic healthcare record, which can only be updated by authorized users, the benefits in regard to privacy is obvious.
If you’re a visual learner and would prefer to see blockchain info presented in that manner, finish reading this article and then take a look at this short video:
The Internet, Reincarnated?
The next two-part question is an obvious one: What makes blockchain important, and how is it poised to potentially transform the nature of computer technology?
The key to answering that revolves around the fact that blockchain networks have no central authority. They are, as such, an inherently democratic system, and due to the fact that they are shared, anyone in the chain has access to the data blocks it holds. This creates a level of transparency that’s rare in the Internet Age. Anything built upon a blockchain is accessible, and every member of the chain is accountable to themselves, and to each other.
However, with the advantages of blockchain come disadvantages as well (which we’ll go over in the next few sections).
Further Benefits and Disadvantages of Blockchain

There’s never been a time when such a system has been more called for, or more needed. Online security and data privacy are two hot topics of our times. As such, expect today’s common privacy software to eventually incorporate blockchain technology in order to take advantage of next generation data protection.
Of course, like any new technology, blockchain isn’t perfect. There remains the ever-present threat of bugs in the software used in conjunction with blockchain. Thus far, it hasn’t removed the need to encrypt data or remove the security measures we’ve become accustomed to. Another concern is its energy consumption. Blockchain consumes a lot of power globally. Cambridge University’s Cambridge Bitcoin Energy Consumption Index (CBECI) estimates that Bitcoin’s energy consumption (88.87 terawatt-hours [TWh] per year) is greater than the annual energy usage of many countries, including Finland (82.79 TWh) and Belgium (82.16 TWh).
Nonetheless, blockchain has made a heck of a buzz in the tech world, and shows no sign of slowing. Perhaps the most obvious reason for its growing popularity is that the world’s number one cryptocurrency, Bitcoin, has blockchain underpinning it. It’s the engine that makes open network payments possible, and allows a level of anonymity within its own blockchain. Bitcoin opened the floodgates but, since then, countless copycat (and some improved) cryptocurrencies have landed on the market with varying degrees of consumer success.
Blockchain: Is it Secure?
Whether you’re a small business looking to increase your online security, a private user concerned about identity theft, or a multinational corporation in need of protection against hackers, online security is paramount. The truth is, sadly, that no system is completely unhackable, and cybercriminals are adept at keeping up with changes to security systems. Blockchain however, with its simplicity and transparency, might be one of the most secure system at our disposal, if implemented correctly.
The reason for this is that in order for anything of value to take place in a blockchain, the network of nodes must be in consensus that the transaction is a valid one. This means that no single entity can say — one way or another — whether a transaction took place or not. If you were to hack a blockchain, you’d have to simultaneously hack into the hundreds or thousands of computers on the targeted network, all while the network fights back.
However, it’s not quite as simple as this. The decentralized nature of blockchain can act as a security feature because so many copies of the blockchain are held in so many places that it can be extremely difficult for an attacker to affect them all simultaneously. However, research by Emin Gun Sirer and Ittay Eyal, as highlighted by Mike Orcutt at MIT Technology Review, casts doubt on this simplistic picture.
Orcutt says their research shows that:
“neither Bitcoin nor Ethereum is as decentralized as you might think. They found that the top four bitcoin-mining operations had more than 53 percent of the system’s average mining capacity per week. By the same measure, three Ethereum miners accounted for 61 percent.”
This means that networks that claim to be decentralized are, in fact, highly centralized, and therefore vulnerable to attack.
One blockchain vulnerability is known as a 51% attack, a name that refers to bad actors who manage to gain majority control of computers in a cryptocurrency mining pool. Essentially, if a hacker can access more than half of the computers in a blockchain (something which, realistically, is only going to happen on smaller blockchains), they’re more likely to succeed in taking control of the system as a whole. This exact scenario took place on the Ethereum Classic token exchange in January of last year, and led to trading being frozen on the second-most popular cryptocurrency.
What’s Next for Blockchain?
The blockchain revolution, while already impressive in its scope and transformative potential, is really only beginning. In fact, there still remains a certain amount of resistance to blockchain among some organizations. It is true that the technology comes with both drawbacks and opportunities.
Blockchain offers immutability and transparency. Traditional systems, on the other hand, offer control, full confidentiality, and more resource efficiency. Trading those off will depend on the product and the requirements. For example, a public blockchain showing donations to politicians might be a good idea. A public blockchain showing the schedules of preschoolers, however, would be a horrible idea.
In other words, there are also a significant number of challenges that need to be addressed before blockchain technologies can go mainstream. There are very real concerns that must be addressed, and businesses need to weigh the options that are best for them.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown