A Pentester’s Guide to Strengthening Your Cloud Security Defenses
Penetration testing is one of the most effective steps toward maintaining cloud security. But knowing how to pentest effectively is easier said than done — here are some insights from a pentesting expert that may help your organization get started
Editor’s Note: This is a guest blog contribution from cybersecurity specialist and penetration tester Isla Sibanda. Isla shares her expert perspective on how organizations should plan and carry out penetration testing to strengthen their cloud security defenses.
Gone are the days when businesses needed to establish and maintain their own server environment to host and run applications on their premises. Today, cloud-based services have become a basic necessity for companies to fulfill their virtual functionalities. The COVID-19 pandemic further fueled this need as many organizations transitioned to remote working.
As a result, the cloud security market is growing exponentially to match the demand. In fact, studies show that the cloud security market is expected to hit $106 billion by 2029 — a CAGR (compound annual growth rate) of about 18% throughout the forecast period.
But along with this market growth come some frightening cybersecurity risks. It’s no secret that cyberattacks are getting more complex with each passing day. Criminals are devising new and better ways to break through your cyber defenses and steal sensitive data. This means that now more than ever, you need all the help you can get.
That’s why pentesting remains one of the most effective methods to maintain cloud security for any organization. In this article we will explain:
- What pentesting is and how it applies to your cloud systems
- Why you should perform cloud pentesting
- Who you should select to do your cloud pentesting
- What steps the company must take to implement pentesting
- How the company can build best practices for its cybersecurity program through pentesting
Let’s hash it out.
What Is Cloud Penetration Testing?
Cloud pentesting testing (short for penetration testing) is a cyber security simulation, usually carried out by a third-party ethical hacker or your company’s internal IT security staff, to test and identify security vulnerabilities (in this context, of a cloud computing system).
Cloud pentesting is like the cloud IT security version of a fire drill. Typically, a fire drill is carried out to re-enforce proper evacuation strategies and other crucial fire practices. In the same way, pentesting your cloud systems enables you to check for exploitable vulnerabilities so you can figure out effective ways to remedy them before bad guys do. Pentesting can be an effective precursor to formal risk assessments.
So, what exactly is cloud pentesting? Pentesting is simply the process of simulating a controlled cyber attack to identify potential vulnerabilities in a cloud computing system. When done correctly, pentesting can help companies discover the various methods hackers can use to gain unauthorized access to sensitive information or engage in other destructive actions that can lead to a data breach.
Why Should You Pentest Your Cloud Systems?
Many companies fail to properly understand their responsibilities for security of their cloud systems. Many assume that because they are purchasing third-party services, their cloud provider will manage and oversee all security processes. But, in fact, cloud services work on a shared responsibility model (see graphic below), and a cloud customer must take security into its own hands for many issues, depending on the extent of the services it uses.
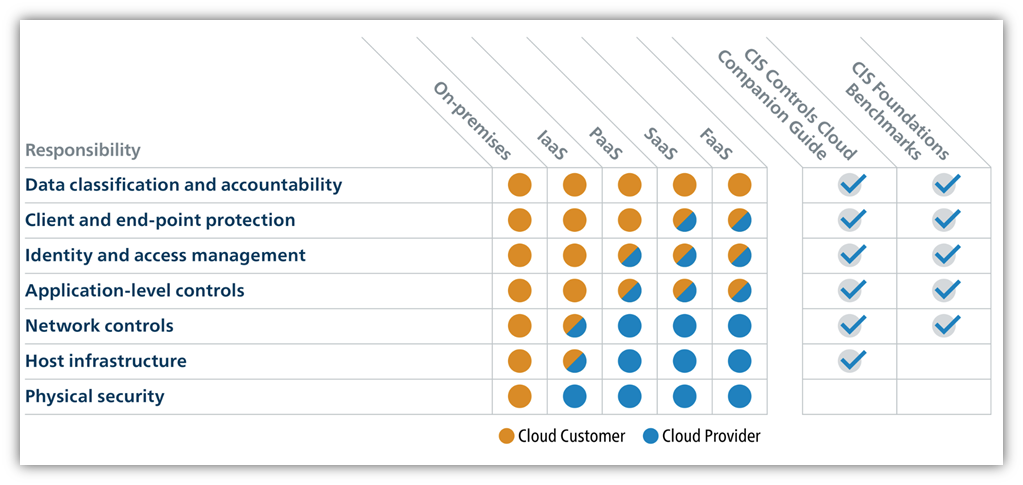
The shared responsibility model makes sense because many common security vulnerabilities for cloud systems arise on the end of the cloud customer. Common examples of cloud system vulnerabilities include:
- Vulnerabilities resulting from lax security policies and enforcement. The classic example here is prioritizing employee convenience over cybersecurity, for example, by having weak password policies. Too many companies open themselves up to attack because they don’t want to deal with the morale fallout of requiring strong passwords that employees must change regularly. Unfortunately, poor password hygiene is one of the most significant security weaknesses for corporate cloud systems.
- Vulnerabilities resulting from failure to control access. Unrestricted access to cloud systems is another major vulnerability for many organizations. Failing to implement role-based access controls and permissions significantly expands an organization’s attack surface.
- Vulnerabilities resulting from poor implementation of cloud systems. Many of the worst cloud system vulnerabilities come about because companies do not properly configure and maintain their systems. Indeed, most successful cloud system attacks today exploit cloud server misconfigurations. But technical vulnerabilities go beyond misconfigurations, extending to improper API usage and insecure internal development efforts that interface with cloud systems (think badly coded web interfaces that allow cross-site scripting attacks).
Pentesting can help you meet your shared security obligations by assessing which of these vulnerabilities affect your cloud systems. You can then prioritize your response, as well as your future cybersecurity efforts, to address the most critical concerns. In particular, cloud pentesting can help you:
- Identify potential workarounds to your cyber defenses that cybercriminals can use to their advantage
- Determine how long it takes intrusion detection and prevention systems to detect and block attacks before any damage is done
- Determine if there are certain types of attacks your systems don’t effectively identify
- Evaluate response times for your team (or your third-party managed security service provider) once potential attacks have been identified
Who Should Do Your Penetration Testing?
After committing to pentesting, an organization must decide whether to use an outside third-party expert or rely on its internal IT security staff. Research shows that about 42% of companies prefer to build an in-house team; for instance, building red-team/ blue-team security exercises that include pentesting. But this may not be the most effective approach, especially given that the IT staff of many organizations is already overtaxed and understaffed due to the significant cybersecurity talent gap.
Third-party security companies can offer dedicated and highly experienced professionals, who conduct pentesting on a regular basis. Moreover, they come into the process with an unbiased and objective perspective that may allow them to see vulnerabilities that internal teams can overlook.
When choosing a third-party pentester, investigate them thoroughly:
- Look for proven experience, recommendations from trusted sources, and clear knowledge of and application of the latest tools and methods.
- See whether their staff have certifications that indicate proficiency or expertise (for instance, are they Certified Ethical Hackers).
- Ask if they can provide you with sample reports so you can assess the value of their services. You can also visit the Public Pentest Reports site to see many different report examples from a range of providers.
But whether you choose to use your own personnel or outsource your pentesting efforts, it is crucial that you select experienced professionals with proven track records.
How to Carry Out Penetration Testing
The cybersecurity industry has developed a multi-step standard for pentesting, appropriately named the Pentesting Execution Standard (PTES). PTES divides the pentesting process into seven core stages:
- Pre-engagement interactions
- Intelligence Gathering
- Threat Modeling
- Vulnerability Analysis
- Exploitation
- Post Exploitation
- Reporting
The standard provides extensive documentation of all the intermediate steps within each stage, both for pentesting professionals and corporate decision makers. Let’s look at how these stages will play out internally.
Stage 1: Outlining and Designing the Plan
In the first stages of the process, you will define the scope and the goals of the testing so it’s clear what you’re planning to achieve and how to achieve it. Frequently, the cloud service provider contract and associated policies provide some guidance for customers regarding which systems to test and which testing methods to use.
This is also a critical time for the company to begin fully understanding the scope of its systems and its potential exposure, because the organization will need to build a complete database of relevant cloud assets. Asset databases should also include descriptions of the types of data that the company needs to protect, the relative importance of the data sources and all storage locations, along with all existing company security policies. If you don’t know what you have, you can’t effectively protect it.
It is also in this stage that you address very practical considerations, such as:
- When you will perform pentesting,
- Who will be doing the pentesting (internal employees or external vendors or contractors)
- What systems may be impacted, and
- How you can bypass any system problems to avoid interrupting normal business workflows.
Stage 2: Carrying Out Intelligence Gathering
In the intelligence gathering portion of pentesting, your security professionals will try and quickly assemble as much information as they can about company resources, to create a foundation for the pentest. Pentesters often use tools such as the following for gathering company data:
- Social engineering — This is one of the most popular intelligence-gathering techniques cybercriminals employ. Social engineering is the process of using psychological tactics to trick or manipulate individuals into doing something or sharing sensitive information they normally wouldn’t.
- Google — Pentesters use search engines to collect general company data, including leaked content.
- Recon- NG — This open-source reconnaissance and analysis tool can be used for web-based information gathering. Because it is purpose-built for reconnaissance activity, it is more effective and efficient than Google.
- Censys — This tool focuses on asset identification and management of an organization’s attack surface. It maintains a continuously updated inventory of IT assets and includes risk detection and remediation tools.
Stage 3: Performing Threat Modeling
If the organization has not yet assembled its asset and data maps, now is the time to do so, as they’re essential at this part of the game. After gathering all the information, the pentester needs time to analyze the data and systems to develop the best possible execution strategy.
This stage also demands that the organization and its security staff investigate who its potential attackers are and how they will likely work. By modeling both the corporate attack surface and the hypothetical attacker, pentesters gain a better understanding of where the most significant vulnerabilities lie. These understandings set the baselines for the actual attack simulations.
In this stage, your security professionals will also be using their models to assess what their best tools will be for the testing. Which brings us to our next stage of the penetration testing process…
Stage 4: Carrying Out the Vulnerability Analysis
Pentesting tools should be able to simulate an actual attack, so the pentester should find tools that can simulate the same procedures that hackers use to gain access to a cloud system. For example, hackers often leverage machine learning (ML) to find system vulnerabilities, such as guessing passwords or hunting for application programming interfaces (APIs) that enable data access. The tools that the pentester selects should reflect the technology and methods that the attacker will use.
A few examples of tools that pentesters commonly use include:
Stage 5: Testing Exploits to Determine How They Can Be Used
This is the active stage of the process, where you see how well the models play out. During this stage, the pentester will use web application attacks, such as backdoors and SQL injections, to find system vulnerabilities and then try to exploit those vulnerabilities (typically by escalating privileges, intercepting traffic that’s not secured with SSL/TLS encryption, or stealing unprotected data.) This will help understand the level of damage that the vulnerabilities can cause.
The tester might also try persistent presence in the exploited cloud system to see how that will affect the system’s defenses. The goal is to replicate advanced persistent threats, which can stay in a system for months (or even years, if left undetected/unmitigated) to steal sensitive data.
Stage 6: Conducting Post-Exploit Analysis
It’s not enough to simply conduct the test and determine if it succeeded or failed; pentesters also should provide the target company with information about what would happen in the event of a successful attack. This is the post-exploitation phase. This process involves determining the following:
- What assets an attack may impact,
- The magnitude of the damage to those assets if the attack is successful,
- What potential ongoing damages there may result due to those threats,
- How there may be possible lateral movement, and
- Whether existing controls and remediation processes will work effectively.
Stage 7: Reporting Your Findings
For the company, this is the most crucial stage of the whole process. Business decision makers don’t want to be concerned with the mechanics; they just want the results. After completing the tests, the pentester will compile a report detailing the following:
- Information identifying areas where security is strong;
- A threat level assessment of the risks and vulnerabilities identified;
- A breakdown of the vulnerabilities found and exploited;
- Info about the sensitive data that was exposed, accessed or exfiltrated;
- The length of time taken to execute each attack; and
- The effectiveness of existing remediation processes.
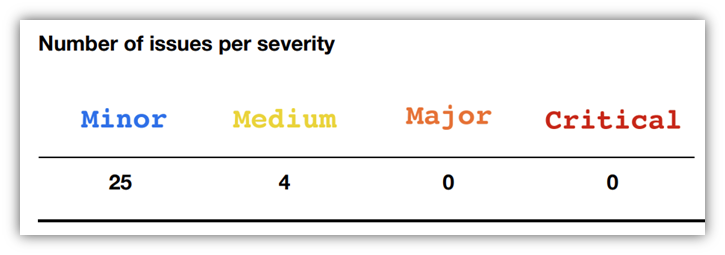
For example, in most reports, you will see a summary of the number of issues identified and the severity of each. Check out these sample screenshots from a sample report from Consensys (which is available on publicpentestreports.com):
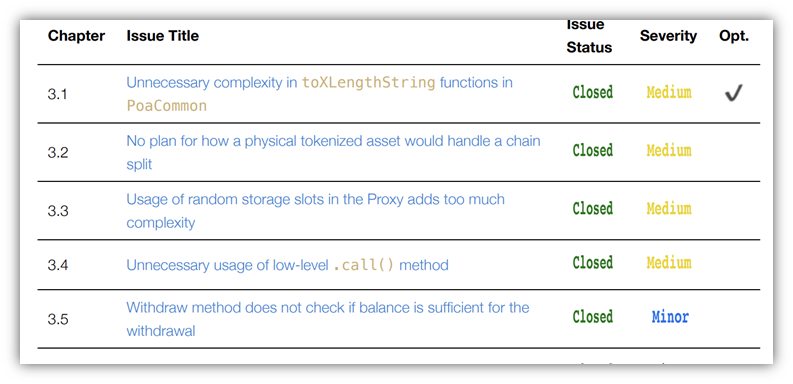
The report should then provide a detailed list of the issues and expand upon each one individually to provide further clarity:
How to Put to Use What You’ve Learned Through This Exercise
A cloud security specialist will then review this data and draw recommendations to help configure the company’s web application firewall (WAF) settings and other application security solutions to patch vulnerabilities and prevent further attacks. You should then follow these recommendations and take the necessary precautions to protect your organization against potential future incidents.
Here is where the company will see tangible benefits from pentesting, as the report will help management:
- Prioritize cybersecurity budgets to address the most critical issues and improve your cloud security posture.
- Build best practices and effective cyber security policies.
- Minimize the effect of successful attacks, thereby protecting the company’s reputation.
- Meet data privacy and protection compliance requirements.
Best Practice for Pentesting from Practical Experience
This is where things get really interesting. Here are some of my recommendations that I think you’ll find particularly helpful when implementing pentesting within your organization:
- Choose your pentesting provider carefully. While it may be tempting to just use internal staff for pentesting, quite often in the long run it is both more cost effective and less disruptive to the business to use an outside provider. And you likely will end up with better overall results.
- Understand your responsibilities under your cloud service provider contract. Pentesting can involve substantial investments of time and resources, so before you decide what to do, you need to know what you have to do. Understanding your contract can help you limit expenses and avoid problems for failing to meet your security responsibilities.
- Don’t put off pentesting. The cost associated with pentesting can deter many organizations from doing it — this is especially true for smaller companies. But avoiding the expense can have disastrous consequences. One ethical hacker shared the experience of being able to access the money in users’ accounts for a fintech application because the company waited too long to do testing.
- Do the work to understand what your vulnerable assets are. Even the best pentester can’t help you if they don’t know the full scope of what they are trying to protect. Yes, it will involve a lot of upfront work, but the cost/benefit analysis weighs heavily in favor of investing the time and in being open with your security professionals.
- Don’t just do the minimum. Cyber security can sometimes be a “you get what you paid for” world. Look carefully at the results of your planning stage. If it identifies numerous threats to your most sensitive data and assets, you cannot afford to be cheap about testing and remediation.
- Don’t plan on a one-and-done pentest. Cybercriminals are very creative and they work quickly; as a result, many new threats emerge daily. Pentesting should be a regular part of your cybersecurity program. The frequency of the tests depends on your company’s risk level. Ideally, if your company has no critical data on its network, you may just need to test monthly, but an e-commerce site with a high risk of personal and financial information theft may need to test weekly or daily.
- Listen to the results and do what must be done. Having undertaken the time and expense of pentesting, you need to follow through and apply what you learned. Most often, not everything will need to be addressed immediately, and you will be able to prioritize your budget to address critical vulnerabilities. Failure to do so can put you in a very difficult position. The pentesting professionals you work with are trying to help you, not waste your time and money. And as one ethical hacker, Jahmel Harris, put it in an interview for Tech Nation: “That can be quite frustrating for a security tester, we do a lot of work to find something and it’s ignored.
Conclusion
Penetration testing is one of the best ways to stay proactive and protect your company and its cloud systems from potential hacking. Whether you’re implementing penetration testing to meet compliance requirements or just want to take your organization’s cybersecurity “temperature,” it’s crucial that you do it (and do it regularly at that). It doesn’t matter whether you opt to use an in-house team or hire a qualified third party; pentesting is something that must be done to ensure your defenses are as secure as possible.
So, as a business owner, are you doing your part in helping curb cybercrime and protect your business’s data, customers, and reputation? How often are you testing your cloud systems and infrastructure to ensure there are no vulnerabilities criminals could exploit to harm your business? It’s not too late to start planning and pentesting your systems now.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)





 (6 votes, average: 4.33 out of 5, rated)
(6 votes, average: 4.33 out of 5, rated)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown