Asymmetric Encryption: What It Is & Why Your Security Depends on It
From securing websites to signing software, you’ll find asymmetric cryptography (including encryption) in use virtually everywhere online. Here’s what you need to know about the cryptographic process that helps keep your data secure online
Asymmetric encryption is the backbone of internet security. Without it, stealing your critically sensitive data is as easy as taking candy from a baby for most cybercriminals. We’ve seen plenty of the painful reminders over the last few years in data breaches that resulted from expired SSL/TLS certificates. (Hence why we always talk about the importance of certificate management to avoid these issues.)
But what is asymmetric encryption? We’ll start with a quick public key encryption definition before moving on to explore this more technical topic at length. Don’t worry, we’ll try to keep this briefer than our usual tome-style explanatory posts.
Let’s hash it out.
What Is Asymmetric Encryption? Public Key Cryptography Defined & Explained
To put it simply, asymmetric encryption encrypts and decrypts the data shared between two parties in public, insecure channels (like the internet). This process involves using two separate but related keys. In a nutshell, it’s all about securing your sensitive information to keep it out of the hands of unauthorized users or entities (e.g., cybercriminals) when you need to upload it to a website, send it via email, etc.
Asymmetric encryption is also part of what’s known as asymmetric key cryptography and public key cryptography because the two keys used are mathematically related but unique (hence, asymmetric):
- One key, which is called a public key because it’s known by everyone, typically encrypts data.
- The second key, aptly named a private key because it’s only known to the key holder, decrypts data.
Here’s a basic look at how this process occurs using the two keys:
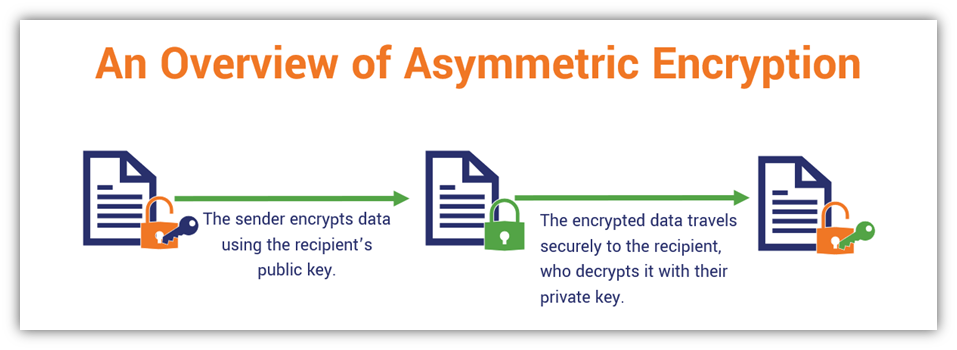
Frankly, asymmetric encryption is a term that sounds more complex and intimidating than it actually is. Once you understand the basics, the whole thing will make a lot more sense. But if all of this is a bit hard to grasp, let’s imagine that you have a special safe that uses two locks — one key locks the safe and the other opens it. Likewise with asymmetric encryption, anyone who has access to the public key can use it to encrypt data, but only the person who has access to the private key can decrypt that information.
Asymmetric encryption is at the heart of a framework known as public key infrastructure. We aren’t going to get into the specifics of how PKI works because, frankly, describing it in every article is a bit of a “time suck” and gets monotonous. So, we’ll just give you a quick summary before moving on: PKI is the foundation of technologies, policies, and processes that enables us to send sensitive data securely across the internet. It relies on a combination of public- and private-key algorithms, digital certificates, and policies.
Purpose of Using Asymmetric Encryption for Data Security Online
The purpose of encryption is to ensure that any sensitive data you want to share with a specific person is kept secret to everyone except your intended recipient. This is necessary because we live in a time when we share and transmit data via multiple ISPs and routers, and many miles of cables beneath the oceans.
Historically, you used to have to meet up with someone face to face to exchange messages or secret keys to unlock future communications. (This is known as key distribution.) This process typically required taking a horse, boat or train to meet up with the other party to give them a copy of your secret key. But with the internet, these time-consuming rendezvous needed to exchange communications have been replaced with near-instant digital communications via the internet.
This is all fine and dandy except for one (not so teensy) little issue: the internet is incredibly insecure. Without a way for users to securely exchange keys to encrypt their data, then anyone could intercept the communications in transit. Asymmetric encryption solves this key distribution issue by creating a way to securely exchange keys (or key-related data) without ever having to meet the other party in person.
Exchanging Keys, or Key Data, Requires a Lot of Mathematical Footwork
Encryption works by applying a complex mathematical formula to your original plain text (readable) data to convert it into a long, indecipherable data string. So, if you took the message “I can’t wait for season 4 of “Stranger Things!” and encrypted it using a 2048-bit RSA public key (more on RSA later), you’d wind up with a gibberish message that looks like this:
gb7Ty/ZcAz2PQF8wLW28ji3g1znuIjucFkgbSjCvvkfgRWStvz/f4atUiNeLbzoJi/agxRJPGuffzPyEBUf4lwZESWEN+UNQRsqhKrp5dYtVYY+wMaevf7rOBBN8O/lHRdJXUyHgF2nPvjkJsnU1AspAB8llYOyUFyL/0vhfi9DAmT0PoB4a8TKKUPVuZG6WN0L56fXtEtl0sx9QMFPHZNU4EPfE+0H6KB7joGw8livqHACSHYL3r63ePFWh/0qG1s2ZYjf6CWrBghih2HUCJx6IcprA0+UJE7AgJBBLMqOTP53xwwz9sFRFhHRHepWaboxCuUXHNtbiebeB2qfVwg==Clearly, this isn’t something that any human being can make heads or tails of in terms of deciphering the message — that’s a good thing when it comes to keeping your sensitive information secret. The good news is that computers allow us to use encryption keys this size — and larger — to encrypt data in a secure way so that unauthorized users can’t access it.
What makes this even better news is that even if a bad guy tried using a modern supercomputer to try to crack the key, they’d still be out of luck. This is because the sheer computational processing resources and time required would span far longer than their entire lifetime and the lifetimes of many generations of family members that follow — i.e., we’re talking millions of years here.
We’ll talk you through the process of how asymmetric key encryption works later in the article. But for now, we want to point out that asymmetric key encryption isn’t the only tool we have up our sleeves when it comes to PKI…
Asymmetric Encryption Typically Works Hand-in-Hand With Symmetric Encryption
Technically, asymmetric encryption could be used on its own as a way to send and receive data. But why would you want to do that? It’s just too bulky and resource-intensive to be used for that purpose at scale. (Not good for large businesses that handle a lot of connections to their websites and services.) This is why, in many cases, asymmetric encryption is used initially as a way to securely exchange sensitive data between two parties before they switch to using symmetric encryption for the rest of the exchange.
Symmetric encryption, or what’s sometimes called symmetric key encryption, uses just one key for both for data encryption and decryption. This means that there’s only a single key that must be kept secure — hence, why this method of encryption is known as private key encryption or secret key encryption.
Symmetric encryption is faster and also is thought to be more secure than asymmetric encryption when the parties are using smaller key sizes. (When using large key sizes, asymmetric encryption wipes the floor with symmetric encryption but does so at the cost of speed.) But each cryptographic approach has its uses and applications. Check out our other article to learn more about the difference between asymmetric vs symmetric encryption.
Where You’ll Find Asymmetric Key Cryptography in Use
So now that we know what asymmetric key encryption is and have a basic idea of what it does, let’s explore a few examples of how you can use it to improve your organization’s data security:
- Website security: Asymmetric encryption is used as part of the SSL/TLS handshake. The handshake is the virtually instantaneous process in which a server authenticates to the browser that tries to connect with it. The two parties exchange data they can use for key exchange or generation. (After that, they use that shared key to establish a secure, symmetrically encrypted communication channel.)
- Email encryption: When you encrypt sensitive messages and attachments, you’re using the recipient’s public key to digitally sign everything so that only their corresponding private key can decrypt it. So, in case you’re wondering, yes, both parties (sender and recipient) need to have email signing certificates to exchange encrypted messages.
- Digital signatures (documents, software, emails, etc.): Asymmetric encryption also is integral to digital signatures (not to be confused with electronic signatures). These cryptographic signatures are used to assert the identity of the document, executable, or email creator.
- Blockchain: A blockchain is a long, sequential line of data blocks that “chain” (tie) back chronologically all the way back to the first data block. Each new block contains data from the previous block, which helps to serve as a historical record. Ever heard of Bitcoin? This cryptocurrency is an example of a digital currency that’s built upon a blockchain. But blockchains have other uses as well, such as providing an avenue of decentralized financial transactions, inventory management, and supply chain management.
5 Asymmetric Encryption & Digital Signature Algorithms
Algorithms are, basically, the instructions that computers use to solve a problem. Asymmetric key encryption algorithms come in different “flavors” or varieties for you to choose from. But you can’t take a one-size-fits-all approach when it comes to selecting the right asymmetric encryption algorithms to meet your needs.
Of course, there are clear differences between many of these asymmetric key algorithms — how they operate, what their specific key lengths and security strengths are, etc. You have to choose the right one based on your needs or use cases. Let’s quickly explore two of the most common public key encryption algorithms:
- Elliptic Curve Cryptography (ECC) — The ECC algorithm uses something known as an elliptic curve (mathematical structures) to generate public-private key pairs. Basically, it looks slightly similar to a wonky bell curve resting on its side. The advantage of ECC is improved performance due to smaller key sizes and the amount of computational overhead involved.
- RSA (Rivest Shamir Adleman) — RSA is considered one of the most secure (and commonly used) asymmetric key encryption algorithms. It’s virtually uncrackable using modern computers. RSA uses two unique, large prime numbers in elaborate algebra to generate its public-private key pairs. RSA also is used as a key exchange algorithm in TLS 1.2, but it’s been deprecated as a key exchange algorithm in TLS 1.3.
Of course, RSA isn’t the only asymmetric key exchange algorithm. Here are a few other notable algorithms worth mentioning for secure remote key distribution as well:
- Diffie-Hellman — This key exchange protocol or, more accurately, a key generation protocol (although the terms are often used interchangeably) is based on exponential calculations. What we mean by that is instead of exchanging keys, DH enables the two parties to exchange public values that are used to calculate secure, symmetric session keys. When an ephemeral key is used, it creates what’s known as perfect forward secrecy because the keys are generated for each session. Qualys SSL Labs reports that only 0.6% of surveyed sites on Alexa’s list of the world’s most popular websites don’t support forward secrecy (as of May 18, 2022).
- Digital Signature Standard (DSS) —This digital signature and encryption algorithm is based on elliptic curve cryptography and is the newer version of the digital signature algorithm (DSA). However, both DSS and DSA have been deprecated and should no longer be used for remote key exchange.
- Elliptic Curve Digital Signature Algorithm (ECDSA) — This key exchange protocol, which builds upon the digital signature algorithm, uses elliptic curves to derive its small cryptographic keys. The advantage here is that because the keys are smaller than, say, RSA, it helps make them more efficient.
To learn more about each of the different types of asymmetric algorithms, be sure to check back with us over the next few months. We’ll publish an article that will focus on that exact topic (much like what we did with symmetric encryption algorithms).
A Quick Overview of How Asymmetric Encryption Works
Asymmetric encryption between two parties works by using a public key to encrypt data and a private key to decrypt it. The process looks something like this:

If you were to break down what this process looks like, let’s consider the Stranger Things example from earlier. Let’s say I want to send you the following message: “I can’t wait for season 4 of “Stranger Things!” (Not sure why this message would be sensitive enough to require encryption, but let’s just run with it.) In this case, I’ll use your public key (which looks something like this when using a 2048-bit RSA key) to decrypt the data:
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvsMXSpjUnpcjhKlmcKs3JZXQPbRCZedVr3nd0TLlm70gyl4OWwSKiIhH754xf3yuj4a3qgnjHFBzd3SEJyd1ciyfZ7npRc4lMY38/54iB7bG2++i5cHAHcUXvB/+T/72HQquGc16heskGj+ZC9ePfNmWv5w8s8DtRjM3ykq3QDLoLi91XITzB9xGTRnOJN+AtGm0zMLrhOceXBvcAM/SNGLApbDoXEbMe3F/cx9mxklz+CLjQBO0hTPtijv/Ruv6h76msDaGQ3JFyNjPUXEVCoqBSHW9HiV5MPjtkwv+joKEQpgWIb4VOZ+MrZn9KarrZPDRJaHGzoYLl9x1EH8EbwIDAQABWhen you apply it to the message, you’ll wind up with the data string we showed you earlier:
gb7Ty/ZcAz2PQF8wLW28ji3g1znuIjucFkgbSjCvvkfgRWStvz/f4atUiNeLbzoJi/agxRJPGuffzPyEBUf4lwZESWEN+UNQRsqhKrp5dYtVYY+wMaevf7rOBBN8O/lHRdJXUyHgF2nPvjkJsnU1AspAB8llYOyUFyL/0vhfi9DAmT0PoB4a8TKKUPVuZG6WN0L56fXtEtl0sx9QMFPHZNU4EPfE+0H6KB7joGw8livqHACSHYL3r63ePFWh/0qG1s2ZYjf6CWrBghih2HUCJx6IcprA0+UJE7AgJBBLMqOTP53xwwz9sFRFhHRHepWaboxCuUXHNtbiebeB2qfVwg==Obviously, you won’t know what I’m saying with the message still encrypted. You’ll then use your private key, which is considerably longer to decrypt the data string:
MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQC+wxdKmNSelyOEqWZwqzclldA9tEJl51Wved3RMuWbvSDKXg5bBIqIiEfvnjF/fK6PhreqCeMcUHN3dIQnJ3VyLJ9nuelFziUxjfz/niIHtsbb76LlwcAdxRe8H/5P/vYdCq4ZzXqF6yQaP5kL14982Za/nDyzwO1GMzfKSrdAMuguL3VchPMH3EZNGc4k34C0abTMwuuE5x5cG9wAz9I0YsClsOhcRsx7cX9zH2bGSXP4IuNAE7SFM+2KO/9G6/qHvqawNoZDckXI2M9RcRUKioFIdb0eJXkw+O2TC/6OgoRCmBYhvhU5n4ytmf0pqutk8NElocbOhguX3HUQfwRvAgMBAAECggEBAKXo+Y3opCuWWc7conrlfp4S0T2JVKJac9ydSj3TXX15HVbEPQoORgp/NMmDtZsirpOn4H9kAAG1OuevD+0Z1XzKsI0/VVJf+1tBGcScHQ7Geef5YJ0hSNzbeUwmK0IaBqW1jzxjyOdGXmzx2UNCZMp6WDEoSmcwKW1/yEsJdp2+51lIAglNeTo1axmRHAcbP6M/gOhCytdC3Vb6e51XKuEQzwT/+Lxpin+EMfRhjCMyws308MAROEBaOLW1HaijMGfVES5jk8HNaLkMFQwxxP4TahKIuq5ArixwpzDvD88fvkwDeWswGWLsY9R6EUOKty37jwEaXQcXQD9TlUxZ6ukCgYEA7gFNsp2PRMkZmPVRPjs/4Um/4WCPZ7UfLULbWGwBKtr5BZ+/Uiq+qYbBlHzODzczIMEH+9mxWsZoBGkRe/mYJaHu0fgGLSe71LZDMeC4cCktzchc/OPVe8LGRJ2imvP1A36Mi6O2fh2szUEhMzXJEYwlXGb+lG97nXqYD+bfJ10CgYEAzS9goBALH88s74EhJWHfXnYNfeQqVrSImSMZBhTcIGueIDH8SUKaHHTlvCtNzhcUdzSSuWwiGLRA2JagxHHw+AK5iTkamuG5guodOHl4nXq2Isprcsee7ocbgkt6Omd1CE9e9ehtJ3NghDKMQ6xfKgbqyrycOcVY0wpWSku/mjsCgYBqeprQNj1KgM266MWYGdnSaLQ3mIOP2jBAh5CqVmePTLfsFDP8BrOWFHu2er+VfxSYqsNvoUz/V5RhpL/1vwyaiX/W4CejPAuEdqZJQkhBpaqgTeuMGEICRHl/aSa+PDZ5gbxPHMcgVRZiHalEx+NUvmZYmJt8vQOIyLgPJTLg4QKBgGmTHBufxamLVyqw/ZYXgvA+u/hvwx0z7SkmdwS7DPydgxI7xf0ICPXlbCPjADivhXdElM5VhkHB1a/b6ULLAdsKw96IhFj3FhX3UiuxzM7yye6iyqCXd/5xhEUJgw20F/K7rDfJbQikhB/hRmy3r4uXXY4NeDD9ixOjuPyndyHrAoGAcnqQM09aY1S/OlwWGVzUZEe0MSDxypR80ezTQ8up9G3C/wYIZN2YGbGUbxS/KcoyonO8LuKopf8Gib7IkagXMWTiX9xgV+vU80E/KzMPaVZtnry5ffpeBXnYCs9UEeBvkoGQwyXO9Tfy/k2AQEpBLZKbP2968c0o+QPHB25C9Uk=This will then decrypt the data and allow you to read the original plain text message.
Don’t worry, we’ll cover all of this more in depth in a future article. Stay tuned for that!
Final Thoughts on Asymmetric Encryption
Alright, we’ve droned on enough about asymmetric cryptography and its corresponding encryption and key exchange algorithms. Hopefully, you’ll leave this article with greater knowledge of asymmetric cryptosystems than you started with.
Asymmetric encryption and key exchange algorithms are the cornerstones of modern public key infrastructure. Without them, there would be no way to remotely exchange sensitive or otherwise secret information via public channels like the internet. We’d still be using clandestine face-to-face meetings like stereotypical spies from Hollywood films.
Understanding what asymmetric encryption is and how it all works is the first step to helping strengthen your organization’s cyber defenses. When you realize the importance of managing your certificates and protecting your cryptographic keys, it’ll help you avoid many of the pitfalls that help companies make unflattering headlines due to data breaches and other security incidents.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown