Massive Google Docs OAuth Phishing Attack Spreading via Email
OAuth oversight allowed Google Docs ‘worm’ to spread like wildfire
Update: For now, it looks like the Google Docs OAuth phishing attack is over. Cloudflare has killed the domain behind the attack. Google has revoked the app’s authentication token, and is marking emails as spam. Continue to be on high alert and do not give permission to any apps with the name “Google” in them.
A Google Docs OAuth phishing attack is spreading like wildfire right now – dozens of business, government offices, and universities have sent out warnings to their users about a Google Docs phishing email.
Most phishing sites attempt to trick you into visiting a fake website designed to imitate the target. This is how the attack that targeted the DNC and John Podesta worked.
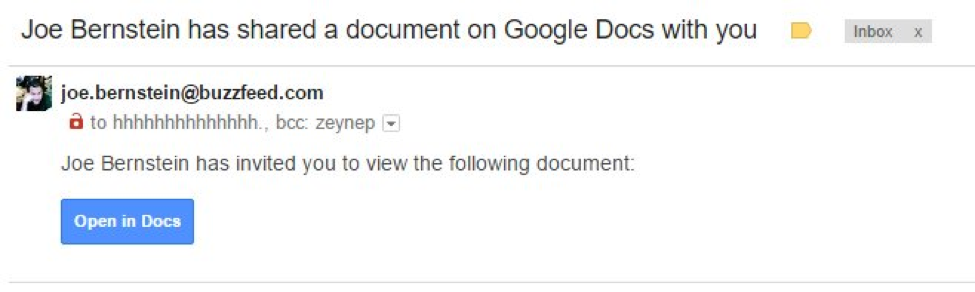
Today’s Google Docs phishing attack is using a slightly different strategy. When you click the “Open in Docs” link, you are sent to the *real* Google.com. But instead of being sent to Google Docs, you are asked to give an app permission to access to your account.
This app is named “Google Docs,” but it’s not the real service operated by Google. It’s a malicious app that has simply given itself the same name. The app requests permission to “read, send, delete, and manage your email” and “manage your contacts.” Clicking on the hyperlinked name of the app tells you it’s published by “eugene.pupov@gmail.com” – a random developer.
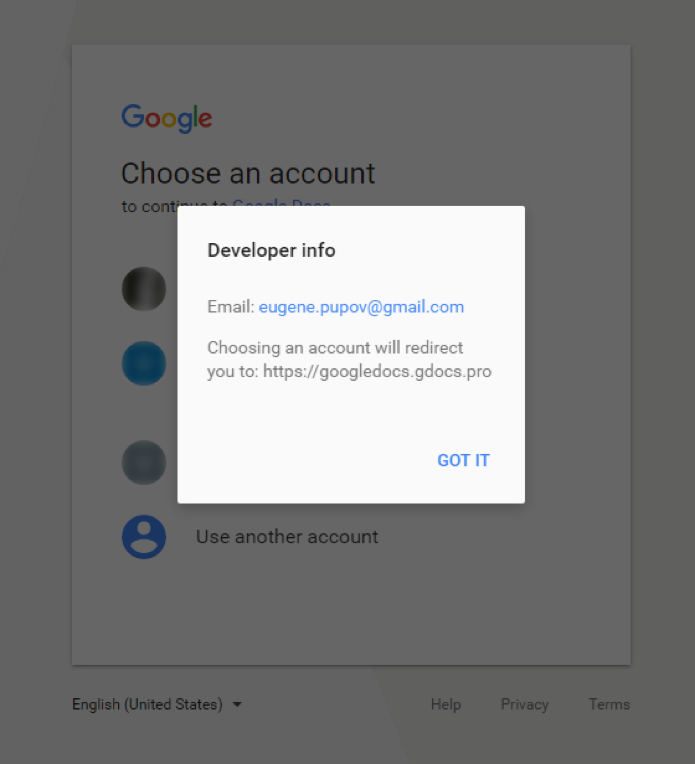
If you hit allow, you are granting permission through a genuine Google page to a malicious app. That app now has the ability to automatically send out emails to all your contacts – which is how it is spreading so quickly.
Google uses a standard called “OAuth” to allow third-party services to connect with your Google account and Google APIs. OAuth is used by thousands of legitimate sites to integrate with the data in your account and extend certain functionality.
But today’s attack has shown that OAuth can also be used maliciously and with great effect. The fact that Google has no restrictions on any application information – including names or images, has revealed how trivially easy it is to craft a convincing attack.
Using Google’s legitimate authentication system for malicious purposes cleverly circumvents the protections of two-factor authentication or authorization.
It is unclear what the goal of this attack was. It attracted so much attention to itself by spreading quickly that it ultimately got itself caught. This raises the question if the attack had malicious intent or if it was more of a nuisance.
Because the app had full access to your contacts and email history, it could have easily been copying that data or looking for high-value targets it had compromised.
If you gave access to this app, visit this Google page and “Remove” the malicious “Google Docs” app. At this point, Google has already killed the app on their end, so it should not be able to cause any more harm but you should still clear up your account.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown