Is HTTPS Secure? A Look at How Secure HTTPS Is
From securing banking websites to protecting data during your online purchases, the HTTPS (HTTP secure) protocol can be found all over the internet
When you visit your favorite website (say, Amazon or GitHub), you connect to that site via a secure, encrypted connection. This secure connection triggers a little padlock security icon to appear next to your browser’s web address bar.
But is HTTPS secure? If you’re looking for a quick answer, it’s yes. But that positive response is only true so long as:
- HTTPS is properly implemented, and
- the mechanisms that enable HTTPS are protected.
If you want to learn more about how secure HTTPS is in a more technical sense, then we’ve got you covered, so keep reading.
Let’s hash it out.
Is HTTPS Secure? And, If So, How Secure Is HTTPS?
When it comes to data security, one of the most trusted and heavily relied upon internet protocols is the hypertext transfer protocol secure. (Note: HTTP secure should not be confused with secure HTTP or S-HTTP, which the Internet Engineering Task Force [IETF] listed as an experimental protocol in RFC 2660.) HTTPS is a way to securely transmit data between two parties or entities (e.g., browsers to web servers in traditional SSL/TLS web sessions). It relies on a mix of cryptographic techniques and tools.
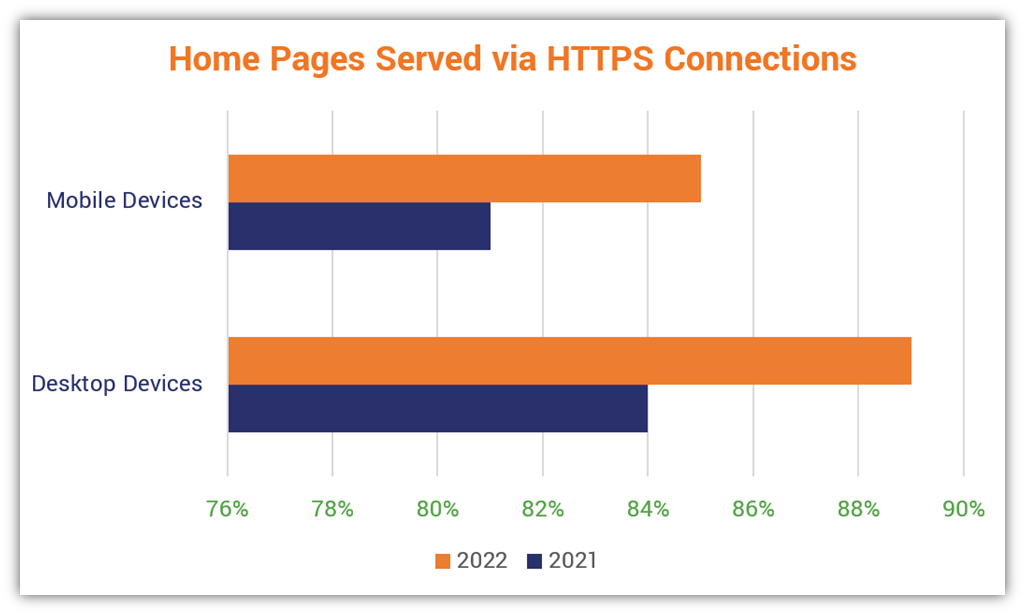
But just how secure is HTTPS? Well, it’s the de facto standard protocol for secure communication on the world wide web — it’s been chosen as the most secure option by the stakeholders that help run the web. The U.S. federal government requires all federal websites and services to be provided via HTTPS connections. So, that should say something about its security. And according to HTTP Archive’s 2022 Web Almanac report:
- 94% of total website connection requests on desktop devices and 93% on mobile devices use HTTPS.
- 89.3% of website home pages are served up on desktop devices via HTTPS; the same can be said for 85.5% of mobile site home pages.
Why the difference between the total request percentages and the percentages of home pages being served via HTTPS? According to HTTP Archive, this has to do with the requests largely using third-party services that have higher HTTPS adoption rates.
Here’s a quick chart to show the increase in HTTPS usage over the past reported year:
Okay, so now that we know HTTPS is secure overall, let’s actually talk about what HTTPS is.
What Is HTTPS? HTTPS = HTTP + TLS
As we mentioned earlier, HTTPS is an internet protocol. More specifically, it’s the successor of HTTP, which is the hypertext transfer protocol. Unlike its HTTP predecessor, however, it’s a secure protocol. This is because HTTPS, also known as HTTP over TLS, relies on the transport layer security protocol to transmit HTTP data for requests and responses.
It used to be HTTP over SSL, which is why you’ll sometimes see SSL/TLS used interchangeably, even though they’re technically different protocols at the granular level. TLS is the successor of SSL.
So, to better understand what HTTPS is and how secure it is, you first need to understand what it isn’t. Let’s quickly compare the two protocols to get an understanding of how they differ.
| HTTP | HTTPS (HTTP Secure) | |
| What It Stands For | Hypertext transfer protocol | Hypertext transfer protocol secure |
| How Data Transmits | Data transmits in plaintext format via the internet | Data transmits via a secure, encrypted connection on the internet |
| Is HTTPS Secure? | No, it’s an insecure protocol | Yes, so long as it’s using an up-to-date version of TLS (TLS 1.2 or later) and proper key management best practices are followed |
| What It Does | It transmits data in plaintext format. It doesn’t provide any mechanisms to protect data security, integrity, or ensure authentication | Provides authentication, data confidentiality, and integrity protection to transmit data securely |
| What It Requires | An internet connection | An internet connection and an SSL/TLS digital certificate issued by a publicly trusted certificate authority |
| Default Port | Commonly uses port 80 | Commonly uses port 443 |
To learn more about what HTTPS is, be sure to check out our other article on the topic.
3 Reasons Why HTTPS Is Secure
Okay. Simply saying that HTTPS is secure isn’t enough. Let’s go over the reasons why HTTPS is considered secure by reviewing what it does…
1. HTTPS Uses Encryption to Keep Data Confidential
At its core, HTTPS is all about transferring data securely via insecure channels (i.e., the internet). Encryption takes readable data (plaintext) and converts it into something undecipherable (called ciphertext) using a cryptographic key. It’s then decrypted on the other party’s end using a corresponding secret key. This protects data from unintended eyes as it transmits from one party to the other.
The process looks like this if you picture a conversation between two users:
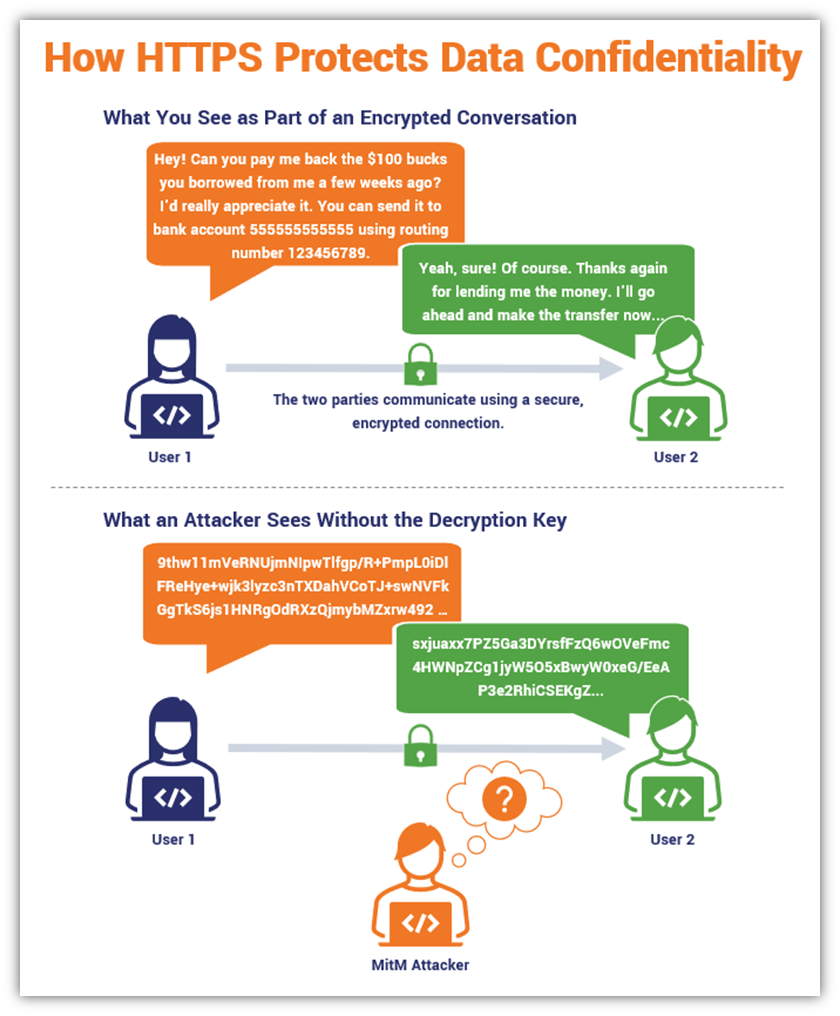
To better understand HTTP secure, let’s put ourselves in the shoes of a hypothetical website user. Imagine that you want to log in to your favorite website. After you enter your username and password, you hit enter. On a secure website, your plaintext data is converted into something that no one can read without the use of a special secret key.
This key, which only your intended recipient has access to, enables the recipient to decrypt your data and return it to a readable format. This means that anyone who intercepts your data in transit (i.e., as it moves from your browser to the website’s server) will be able to see the gibberish but won’t be able to make any sense of it. Pretty cool.
But encryption on its own isn’t enough to ensure that a site you visit is safe. Secure, yes, but not safe. You need additional layers of security to help with that.
2. HTTPS Authenticates Who You’re Communicating With
If it walks like a duck and quacks like a duck, then it’s probably a duck, right? Not always. Just because someone claims to be from the FBI over the phone doesn’t mean they’re necessarily the FBI; they could be a cybercriminal trying to hustle you. This is a common phishing scam tactic: they’ll pretend to be someone in a position of authority to trick, manipulate or coerce you into doing something.
To trust that it’s really the FBI, you’ll need to hang up and call back the supposed representative using the FBI’s official agency phone number. Never trust any information given to you by an unknown caller — this includes the phone number to call them back at. Chances are, the person who called isn’t a real agent; they’re a cybercriminal looking for an easy payday. Likewise, just because a website looks like your favorite website doesn’t mean it is: it could be a phishing or otherwise malicious website that’s designed to look legitimate to lull you into a false sense of security.
Let’s continue with the hypothetical example of being a website user. Imagine that you type amazon.com into your browser but accidentally misspell it (or maybe DNS poisoning routes you to the wrong server). Instead, you land on a look-alike site with a slightly different URL but don’t realize it. You make your purchase, not realizing anything is wrong. A few weeks later, you’re going through your credit card statement and see a bunch of unknown charges. Turns out, a cybercriminal stole your personal information and credit card data through that mistyped website. Now, they’re going on daily shopping sprees and are having a positively fabulous time — all on your dime.
This is where website authentication comes into play. Authentication is a way to verify that the website you’re visiting is legitimate because a publicly trusted third party has checked it out and given it a stamp of approval in the form of an SSL/TLS certificate. By issuing this small digital file, the trusted third party (known as a certificate authority) attests that the organization in control of the domain is authentic by checking official records and resources.
Choose the Right Validation For Your Data Security Needs
These digital certificates are available in a few validation levels:
- domain validation validates your domain only,
- organization validation offers domain + basic business validation, and
- extended validation which offers domain + the most in-depth validation of the organization.
It’s best to use organization validation certificates as a minimum if you’re collecting any type of customer information to provide users with a way to verify your authenticity.
But authenticating the website’s legitimacy isn’t enough, either; you need other another way to know that the data sent between your browser and the web server is protected from unauthorized alterations.
3. HTTPS Ensures Data Isn’t Tampered With (i.e., Offers Data Integrity Protection)
The concept of data integrity is that the data you send or receive via a network isn’t modified, deleted, or otherwise altered from the time one party sent it to when it was received by the second party. Why is this important? Because if someone alters key pieces of information behind the scenes, if you don’t have data integrity checks in place, neither you nor the other party you’re communicating with would realize something’s amiss until it’s too late.
Think of it like the data equivalent of a tamper-proof container or product packaging; it’s here to ensure that no one has messed with your product between the time it left the manufacturer to when you bought it. Yup, that’s it in a nutshell. Now, let’s apply this to the hypothetical website user scenario.
Imagine you’re a bank customer and want to transfer some money to a friend using the bank website. You set up the transfer, but as you hit submit, you don’t realize that someone has positioned themselves in the middle of your connection and all of your data transmissions flow through them. (This is known as a man-in-the-middle attack, or MitM attack.)
What this means is that without certain security measures in place, they can alter critical information to suit their purposes. For example, they can:
- Change the bank account you’re sending the money to, to one they control,
- Upgrade the payment to a higher number (e.g., turning a $100 transfer into a $1,000 payment or more), and
- Remove or change other critical information from the data you transmit in the session.
Why Using HTTPS Matters (And Why You Should Use It)
To reiterate, HTTPS is secure and HTTP is not. If your website can’t ensure confidentiality, authentication, or integrity, it’s definitely a problem, regardless of whether you’re a website user or a website owner. It’s just bad news all the way around.
- Without verifiable identity, you don’t know who the other party is, let alone if they’re trustworthy. If you receive data from an unknown party, how do you know it’s legitimate? Or, if you send sensitive data to an unverified party, how do you know your data is safe, and you haven’t just handed it over to a bad guy? You can’t if you don’t have a way to verify they are who they say they are.
- Without data encryption, you can’t know if your sensitive info will stay confidential. If you’re sending data across an insecure network like the internet, you shouldn’t expect privacy or confidentiality. It’s like getting naked in the middle of the street: someone’s inevitably going to see your “private assets” (if you know what I mean) because it’s likely that at least one person will want to take a quick peek.
- Without data integrity, you have no way of knowing whether critical data has been changed. When exchanging data with another party, you need to know that no one has been messing with it in transit. Otherwise, how can you or the other party trust anything that’s been sent or received in the communications? You can’t.
Is Your TLS Version Secure?
But there is another important factor in play when it comes to HTTPS security. Earlier in the article, we mentioned that for HTTPS to work, you need to use a current version of the TLS protocol. The industry as a whole is slowly making its shift from TLS 1.2 to TLS 1.3. Additional data from HTTP Archive (from the same report we shared earlier) shows that 67% of home pages designed for desktop devices are served via TLS 1.3. Their research also shows that TLS 1.3 is supported by 70% of mobile website home pages.
So, it’s not just about using a TLS connection for HTTP responses; it’s about using a valid, up-to-date TLS protocol that’s supported by browsers and servers. With this in mind, avoid using protocols older than TLS version 1.2 (TLS 1.1, TLS 1.0, or any of the SSL protocols).
To learn more about how HTTPS works, be sure to check out our other blog on the topic.
How to Get HTTPS on Your Website
To enable HTTPS on your web servers, you need something known as an SSL/TLS certificate. This digital certificate, also known as a website security certificate, is a small data file you install on your website’s server. It’s essential to public key infrastructure and enables the use of HTTPS. In some ways, an SSL/TLS certificate (and its corresponding cryptographic keypair) is much like a passport in that it:
- Ties your organization’s verified identity to the certificate and your domain (much like how a passport proves your personal identity).
- Is issued by a trusted third-party certificate authority (much like the U.S. Department of State issues passports).
- Requires secure storage of the certificate’s cryptographic private key to prevent the certificate from being compromised (much like how you likely keep your passport locked up to keep it safe).
- Must be carefully managed to ensure you renew it before it has a chance to expire (much like how you can’t fly with an expired passport, expired SSL/TLS certificates won’t do you any good, either, and result in outages).
How to Ensure Connections Are Forged via HTTPS Automatically
A lack of HTTPS leaves users’ data at risk of compromise. To keep your website and users secure, you’ll want to ensure they’re using HTTPS to connect to your site. This is commonly done by setting redirect rules on your server to switch users from http:// to https:// automatically.
You can take it a step further with HTTP strict transport security, or what’s known more commonly as HSTS. HTTP strict transport security is a browser response header. When you have HSTS in place and a client requests an HTTP connection to your website, your server’s response to the browser will include this header. This message will tell the browser to load the site using HTTPS. You can set up specific directives that inform browsers to load subsequent connections based on set parameters.
Here’s an example of an HSTS header that says a domain (and subdomains) should only be contacted over HTTPS for 31,536,000 seconds (one year):
Strict-Transport-Security: max-age=31536000; includeSubDomains; preload
But how popular is HSTS? HTTP Archive reports that 25% of mobile responses and 28% of desktop device responses include HSTS headers. We previously shared that new U.S. .gov domains would be required to use HSTS preloading starting Sept. 1, 2020. Major browsers like Google Chrome, Mozilla Firefox, and Microsoft Edge have their own versions of HSTS preloading lists (although many of the others are based on Google’s).
Implementing an HSTS policy helps to prevent protocol downgrade attacks as well as cookie hijackings. Downgrade attacks enable bad guys to get the browser and server to switch to using older, insecure parameters for encrypting data in transit. By doing this, they can exploit vulnerabilities that enable them to intercept and decrypt your data while it’s moving between the two legitimate parties.
So, Is HTTPS Secure? Final Thoughts
Alright, it’s time to wrap things up. We hope this clearly explains how HTTPS is secure and why it’s the go-to protocol for secure website connections. We’ve shared quite a few resources throughout this article, including links to more in-depth information on what HTTPS is and how it works.
The big takeaway here is that HTTPS is secure, so long as it’s properly implemented. This means:
- Using SSL/TLS certificates issued by a trusted CA that offers at least organization-level validation
- Implementing HSTS to prevent downgrade attacks
- Carefully monitoring and managing the cryptographic certificates and keys within your digital environment
If you have any additional thoughts to share on HTTPS security, be sure to share them in the comments below.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown