Fancy Bear and Cozy Bear, APT28 & APT29, Already Targeting 2018 US Election
The two Russian groups were behind the 2016 attacks, too.
Earlier this week Symantec announced that APT28 and APT29, perhaps better known as Fancy Bear and Cozy Bear, are already hard at work trying to subvert the 2018 US midterm elections. Just like they did in 2016.
 I think one of the biggest problems with these groups are our naming conventions. Fancy Bear, Cozy Bear, Lucky Mouse—these names belie the serious nature of these groups. Yes, they’re funny. But what they’re attempting to do is not. APT stands for Advanced Persistent Threat and that’s far more accurate. These are state-backed attackers with substantial resources and abilities.
I think one of the biggest problems with these groups are our naming conventions. Fancy Bear, Cozy Bear, Lucky Mouse—these names belie the serious nature of these groups. Yes, they’re funny. But what they’re attempting to do is not. APT stands for Advanced Persistent Threat and that’s far more accurate. These are state-backed attackers with substantial resources and abilities.
The breadth of the havoc that these groups wreaked in our last election is only now beginning to come to light. There were thousands of emails stolen from the Clinton campaign and the Democratic National Committee. Those emails were then published by WikiLeaks. There was a massive misinformation campaign perpetrated across social media. Fake news ran rampant. There’s even evidence that votes were changed.
This time, the US is a little more prepared (for the most part), but APT28 and APT29 have also had a couple of years to continue refining their tactics and probing our digital infrastructure.
Today we’re going to take a quick look at the threats facing the 2018 US Election, specifically from APT28 and APT29,
Let’s hash it out.
What Are APT28 and APT29?
While there’s still a lot we don’t know about these two groups, the prevailing wisdom is that they are backed by different Russian government entities. That is one of the biggest distinctions between them.
APT28 is traditionally associated with the Russian military intelligence agency GRU. It has been active since at least 2007. Initially Fancy Bear just stole information from various governments in the Europe, and the US. They became a bit more antagonistic in the lead-up to the 2016 US Presidential elections.
 In September of 2016, the World Anti-Doping Association (WADA), which is itself no paragon, announced that it had been breached by APT28.
In September of 2016, the World Anti-Doping Association (WADA), which is itself no paragon, announced that it had been breached by APT28.
WADA oversees Olympic drug testing and the Russian federation had been heavily penalized, to the point of being banned in the 2016 Olympics, as a result of a massive doping scandal.
APT28 used an account that had been created by the International Olympic Committee (IOC) to gain access to WADA’s network and steal medical records on athletes, some of which were leaked and others used for attempted extortion.
By this point APT28 was already hard at work subverting the US elections.
APT29 or Cozy Bear is associated with the Russian Foreign Intelligence Service. It’s a bit more recent, first appearing on the radar in early 2010. And like Fancy Bear, it started with simple cyber espionage operations before escalating into more subversive activities during the 2016 Elections.
Or rather, both groups really began their escalation with campaigns in the Ukraine and other former Soviet states. Those attacks get less attention owing to their geography, but make no mistake about it—this where both of these groups cut their teeth before their efforts in 2016.
How Do APT 28 and APT29 Operate?
The one tactic both groups have used successfully is spear-phishing. Spear-phishing is a specialized form of phishing that leverages social engineering to create extremely specific campaigns aimed at specific individuals. In the lead-up to the 2016 US Election, APT29 sent over 1,000 spear-phishing emails. These emails contained links that installed malware on the victim’s computer. This is how the Clinton campaign got hacked.
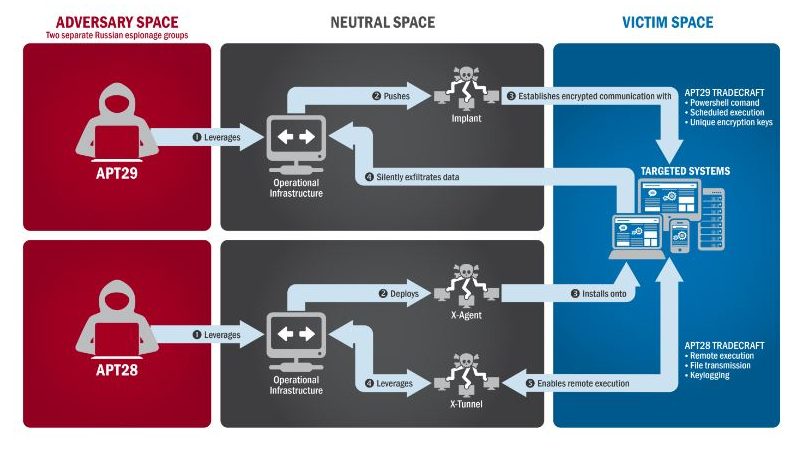
Per Symantec, APT has employed the following tools:
APT28 is a bit more diverse in its approach, it uses spear-phishing, too. As it likely did with the DNC compromise. Fancy Bear also makes use of watering hole websites – infecting a site a group targeted users is known to frequent – infected devices and various exploits (including zero-days).
Once again, per Symantec, these are APT28’s tools of choice:
Will APT28 and APT29 Be a Problem in the 2018 US Elections?
Undoubtedly. Symantec has already offered to provide additional support to US election sites.
“The issues that plagued the 2016 election are still prevalent today and are likely to continue to persist through the midterm elections, into 2020, and into elections globally,” Symantec CEO Greg Clark told TechCrunch. “It is important for all parties, public and private, to contribute to protecting the security and integrity of our elections and democracy.”
And there does seem to be a concerted (albeit a little delayed) effort from the US government to try and shore up its election infrastructure. Microsoft has been working to take down fake websites. Facebook and Google are working to combat fake news.
And in July, Special Counsel Robert Mueller indicted 12 Russians for their role in the 2016 US Election interference.
But there will still be problems.
That may seem a bit fatalistic, but these are very sophisticated attackers that have so far succeeded in subverting not only US elections, but US culture.
This time we’re more prepared though. Hopefully that makes a difference.
What Can My Business or Organization Do to Stop Russian Attacks?
Well, let’s start with this: unless you’re somehow a part of the US government or military apparatus, you likely aren’t a target. While APT28 and APT29 have targeted government organizations, think tanks, universities and a few corporations, the average business probably doesn’t have much to worry about. Still, the US Department of Homeland Security has offered some guidance on best practices for avoiding cyber attacks:![]()
- Back up everything – Make sure you have backed up all critical information. Make sure you have backups offline. And make sure you have tested your mechanism to revert to a backup (don’t find out if it works after an attack).
- Risk Analysis – Make sure that you conduct a proper risk assessment and then follow up on the actionable items to help harden your security posture.
- Staff Training – The biggest threat to your organization is your own employees. 70% of US employees don’t know cybersecurity best practices. Don’t let this be your downfall. Train. Train. Train.
- Vulnerability Scanning and Patching – You should be performing regular scans and patching as soon as the available updates have been tested on your network. Not patching is part of what caused the Equifax breach.
- Application Whitelisting – Only approved programs and applications should be running on your network, this helps minimize risk by limiting what happens on your network.
- Incident Response – Have you practiced what will happen in the event of an attack? It’s one thing to document the process, it’s another to actually put it through its paces before you have to use it for real.
- Business Continuity – Do you know how long your business operations could continue in the event of an attack? How long would it take to recover? What, if any, contingencies do you have in place?
- Penetration Testing – The best way to figure out if anyone could hack your systems is to try to hack your systems. Think like a black hat and throw everything but the kitchen sink at your network trying to break it. If you don’t, someone else who isn’t on your payroll will.
As always, leave any comments or questions below…







































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown