Hello? Is That a Cybercriminal? A Look at Vishing Attacks
47% of organizations reported experiencing a vishing or social engineering attack in 2021 — let’s explore how artificial intelligence can catch your employees off guard and what you can do to avoid it.
Editor’s Note: This is a guest blog contribution from Keven Knight, Co-Founder and Chief Operating Officer (COO) at Talion. Knight shares his expert perspective on some of the ways cybercriminals are using vishing attacks to target organizations and what you can do to fight back.
With more than 3 billion domain spoofing (fake) emails sent worldwide every day, it’s no news that cybercriminals continue to rely on human intervention to access sensitive information and infiltrate networks. Social engineering banks on instinctual human traits and emotions to catch employees off guard when they least expect it, and it’s a tactic commonly used in voice phishing (vishing) attacks. Voice phishing is where cybercriminals use phone calls to trick or coerce targets into doing something they shouldn’t.
But why move from email to the phone? It may seem counter-intuitive — surely, you would know who is on the other side of the phone simply by the voice, but it’s not always the case. There isn’t always a “familiar” contact when it comes to banking institutions or an employee at a partnered company — or if there is, we aren’t always familiar with how they sound.
We believe the words, not the voice, and the words tell us to trust them. So, how should your employees work out if a phone call is legitimate? This article explores voice phishing — or, more specifically, a couple of different types of vishing — and what you can do to avoid falling prey to a vishing attack.
Let’s hash it out.
Vishing Attack: No, Really — A Cyber Criminal Is On the Other End of Your Phone
As humans, we often feel in denial when bad things happen — especially as victims of cyber attacks. Whether it’s our egos holding us back or we believe the facts match up, we often don’t question an email or phone call when we hear who it is and where they’re from. We trust that they are who they say they are, frequently without stopping to question the situation.
While a sense of urgency can be created with a phishing email, such as informing the recipient of a looming closure to their account, this is heightened tenfold with a voice phishing (vishing) phone call, where the caller is waiting for immediate information, literally hanging by a thread. Our human instinct to trust builds a desire to answer questions, take action, and work in collaboration with the caller. Despite phone calls having no “time limit,” we still feel pressured to answer the caller immediately to fill that silence and because we don’t want to question someone in a perceived position of authority.
Cornering employees through vishing increases cybercriminals’ chances of retrieving sensitive information. This is because vishing targets tend to give in to calm the feelings of pressure placed upon them, often handing over information they don’t necessarily mean to.
How can you ensure your employees are wary of these risky calls?

The Two Common Types of Vishing Attacks
There are two different types of vishing every employee should be aware of:
1. Hybrid Vishing Attack
Traditional phishing relies on a user clicking a link, and traditional vishing relies on someone answering a phone call. Hybrid vishing, also known as callback phishing, combines these tactics to create a two-step approach that builds credibility before taking a strike. Let’s consider the following real-world example of such a message:
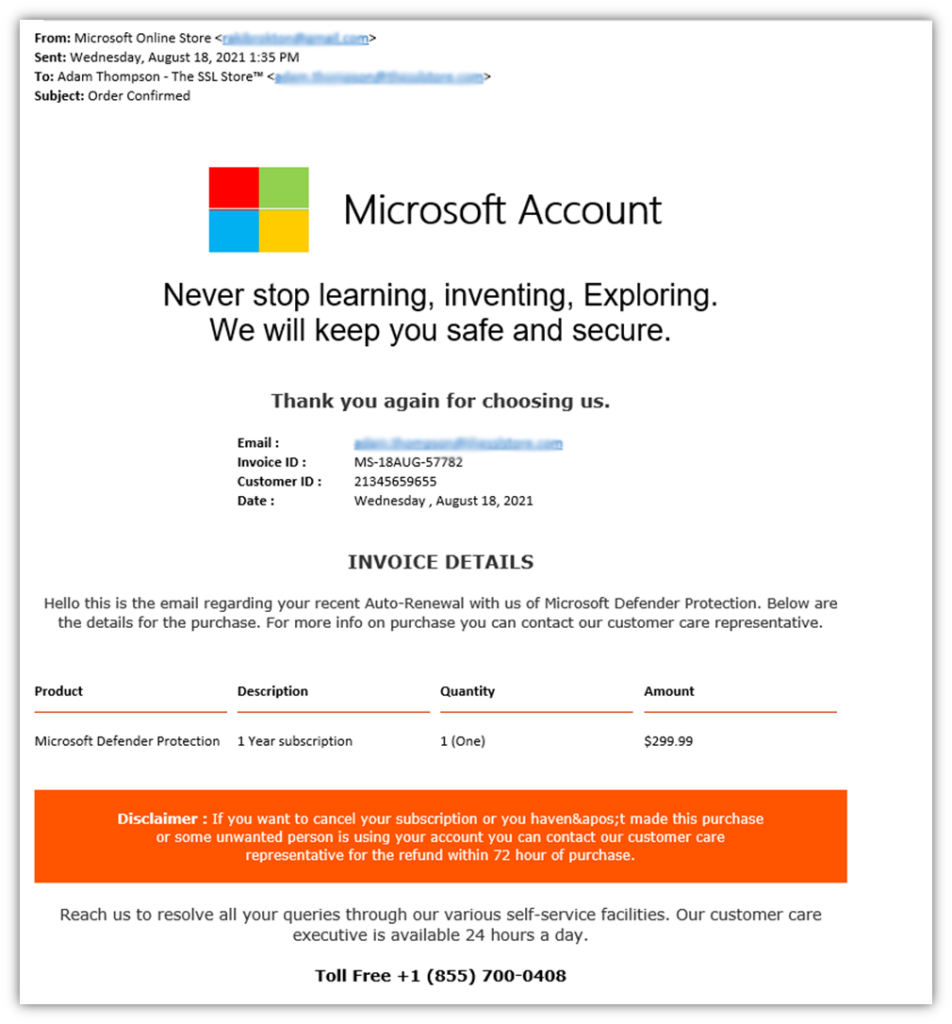
Often, with hybrid vishing, an email is sent in reference to something you are already aware of — for example, a recent purchase or a suspected problem with your account. Rather than sending a link in the hope that you’ll click it, the message provides a phone number for you to call to fix the situation.
When the user calls the number, a real person is behind the phone who tricks you into carrying out a series of actions that enable them to access your account or network. For example, they may try to trick or coerce you into downloading a particular software or sharing your password.
Although hybrid vishing has been around for a while, researchers believe it gained greater traction with the email campaign BazarCall. In this campaign, the Ryuk ransomware gang (now rebranded as Conti) used a particular spear phishing technique to target specific victims at organizations. Convincing victims to give remote desktop control, the cybercriminal silently entrenches in the users’ networks, weaponizing legitimate tools. As a result, they gain entry points into the victims’ networks and exploit them to gather business data.
Hybrid vishing saw a 625% increase last year in just three months, likely due to cybercriminals taking advantage of vulnerable situations and remote conditions during the pandemic.
It’s vital we continue to share awareness on this topic to help prevent others from falling prey to attacks.
2. AI-Based Vishing Attack
Cybercriminals are increasingly using more sophisticated tools in attempts to get through to victims using social engineering. The growth of artificial intelligence (AI) is proving to have a huge cyber influence in building flexible, autonomous systems that require less maintenance.
Since artificial intelligence (AI) is built on an algorithm that detects patterns, it can produce iterations of processes, such as conversations based on voice recognition, that repeat without the need for constant human input. Artificial intelligence can save cybercriminals time and effort since they work automatically once those processes are in place.
In 2021, it was reported that a company director’s voice was impersonated by a fraudster using AI technology. Using this technology, cybercriminals convinced a bank manager to authorize the transfer of $35 million as part of a company acquisition. A lawyer had been hired to coordinate the procedures to make it seem legitimate, and deep fake technology was used to mimic the director’s voice, minimizing any chance of suspicion.
Jake Moore, a former police officer at Dorset Police Department and current cyber security expert with ESET, shared the following with Forbes:
“Audio and visual deep fakes represent the fascinating development of 21st century technology yet they are also potentially incredibly dangerous posing a huge threat to data, money and businesses. We are currently on the cusp of malicious actors shifting expertise and resources into using the latest technology to manipulate people who are innocently unaware of the realms of deep fake technology and even their existence. Manipulating audio, which is easier to orchestrate than making deep fake videos, is only going to increase in volume and without the education and awareness of this new type of attack vector, along with better authentication methods, more businesses are likely to fall victim to very convincing conversations.”
As Moore has pointed out, employees are often unaware that deep fake technology exists and that a familiar voice can’t always be trusted. The number of deep fake videos online has been increasing at an estimated annual rate of about 900%. As a result, it’s likely that deep fake vishing incidents will continue to rise, especially as AI and discussions about the metaverse continue to make rounds.
How a Vishing Attack Aims to Catch You Off Guard
If vishing attacks were always easy to spot, then they wouldn’t be a problem. But, like any social engineering technique, cybercriminals exploit recipients’ emotions and good nature to get what they want. Bad guys take advantage of their targets’ desirable qualities, such as their feelings of trust and desire to help others; in many cases, they target the targets’ fears and insecurities.
Here’s a look at the impact of vishing based on exploited emotions and other exploited aspects of human nature:
- Curiosity — If someone unexpectedly calls or knocks on our door, many of us think, “it’s someone trying to sell me something,” but that curiosity often still leads us to answer the phone or peep out the window. This is, essentially, what happens with vishing, even if the timing or number doesn’t seem right.
- Helpfulness — Helping others makes us feel good about ourselves, especially when the person we’re helping is struggling. If you’re caught in a phone conversation with a stranger who has a baby crying in the background and is asking for help getting into your network, it’s easy to be manipulated into feeling sympathetic towards the person, not realizing it’s a staged scenario.
- Fear —Vishing often plays on your emotions. It conveys feelings that we’re running out of time, losing or missing out on something. As soon as our pre-frontal cortex goes into overdrive, logic is out the window and we’re more likely to act without thinking.
These emotions and attributes are human instincts — we simply can’t help them. But that’s exactly why they’re so effective in a cybercriminal’s strategy. While we can’t stop ourselves from emotionally reacting to a vishing attack, we can change how we act in response to them and what actions we do (and don’t) take.
6 Ways to Avoid Vishing Attacks
No employee or business likes to think they can fall victim to a vishing call, but with advanced artificial intelligence mimicking familiar voices better than ever before, it’s more common than you think.
Make sure your employees are aware of key techniques used in effective vishing calls so your business remains protected. Increasing their level of cyber awareness is also crucial to improving your organization’s cyber defenses.
Here are some other ways your organization can protect against vishing:
- Verify, verify, verify — It’s not enough for someone to recite their name and job role anymore. With openly accessible corporate information all over the internet, cybercriminals can easily latch on to personal details and use them to their advantage. Instead of taking someone at their word, verify the caller’s identity by:
- asking them to send you an email and checking the domain is correct (or asking for email signing certificates to check legitimacy), or
- hanging up and calling them back directly using a reputable source (such as the number listed on their website).
- Never give sensitive information over the phone — Most legitimate organizations, such as banks, wouldn’t ask for details such as your password and PIN. Don’t give any information you wouldn’t give to a stranger, and take your time before making a decision. Many governments have issued business guides for protecting personal information to help organizations stay safe because they recognize that if your data ends up in the wrong hands, there is a high chance of identity theft or fraud.
- Consider using a managed phishing detection and response (MPDR) tool – Are you lacking internal expertise but want to augment your existing team or lessen the burden of alert fatigue on your security team? Then consider investing in an outsourced cyber security provider, which could help you save time and resources. MPDR seamlessly blocks attempted cyber attacks and ensures cyber awareness across the breadth of your company, so employees are far less likely to fall victim to phishing and vishing attacks.
- Implement internal processes — Who picks up the phone when the general organization phone number rings? Could it easily end up in the wrong employee’s hands? Passing the phone between different users can easily cause confusion, leading employees at the target organization to lose sight of who is on the other side of the call. Hiring a dedicated receptionist to filter out the bad from the good can be useful where necessary and ensuring all employees verify the caller when it’s handed over from someone else. Another option is to create a process wherein the recipient confirms with the “requestor” directly through another official channel before handing the phone over to them.
- Prioritize password security — In the case of a cybercriminal getting through your initial wall of security, always have backups in place and ensure password salting wherever possible to increase password security. In a LastPass report, data shows that employees reuse a password an average of 13 times. How easy is it then for cybercriminals to brute force their way into your account once they’ve got one of those passwords? Very likely. Use a different password for each account where possible or consider a password manager for ease of use.
- Ensure all devices have multi-factor authentication — Using high-strength passwords is all well and good, but multi-factor authentication provides those extra layers of security that ensure your account can’t be compromised with a single password. Google announced multi-factor authentication as mandatory for 150 million users in 2021 to deliver an enhanced layer of security against threats, thereby decreasing the number of accounts compromised by a whopping 50%.
To learn more about preventing phishing attacks that can lead to vishing and other issues, be sure to check out Talion’s Ultimate Phishing Guide eBook.
Final Thoughts on the Different Types of Vishing Attacks
Vishing may not be top of mind for your organization, but it should be. No matter how smart or capable you and your colleagues are, social engineering tactics are powerful enough to catch anyone off guard.
Now that you’re aware of the different types of vishing, how artificial intelligence (AI) can mimic familiar voices through deep fake technology and what processes you can put in place to avoid vishing, it’s important to share this information with your employees.
Let them know that questioning a caller and verifying information with someone through official channels can be the difference between safe data and the risk of a cyber incident or data breach.
To learn more about the impact of phishing, vishing and the emerging need for MPDR, take a look at Talion’s blog.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)





 (5 votes, average: 4.40 out of 5)
(5 votes, average: 4.40 out of 5)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown