Real Photo vs AI-Generated Art: A New Standard (C2PA) Uses PKI to Show an Image’s History
It’s getting harder to tell what’s real and fake online. A new technical standard from Adobe, Microsoft, Sony, DigiCert and dozens of other industry leaders aims to solve this problem.
We’re living in a time when the general public no longer feels they can trust what they see, hear, or read in the news or online. And, honestly, why should they? We’re hearing daily proclamations about “fake news” and seeing artificial intelligence (AI) tools being used to create deep fake videos, photos, and other media to cause harm or push agendas. Examples include phony videos and images of a former U.S. president being arrested or foreign leaders saying things they’ve never said.
People need a way to cut through the noise; to have a way to differentiate between real and fake media as consumers. This is where the Coalition for Content Provenance and Authenticity (C2PA) comes into play. This specification, which uses public key infrastructure (PKI), takes the guesswork out of authenticating and validating digital files by providing a tamper-evident record that anyone can review.
Intrigued? We’ll look under the hood at what C2PA is, how it works, and why it’s poised to change how businesses and consumers approach content creation and media validation.
Let’s hash it out.
What Is C2PA? An Overview of This Open Technical Specification

The Coalition for Content Provenance and Authenticity (C2PA) is an open standard created to help users identify who or what created a digital file (such as an image, audio recording, or video) and how it’s been edited. The goal is to enable users to more easily distinguish real photographs or videos from AI-generated images and digital art.
The coalition, which launched in February 2021, is a Who’s Who of more than 50 industry leaders, including Adobe, Microsoft, Sony, DigiCert, and the Recording Industry Association of America (RIAA). Closely related to Project Origin and Content Authenticity Initiative (CAI), C2PA is an Adobe-led initiative that creates open tools for C2PA (which we’ll talk about later). It also plays a critical role in promoting and educating about the open industry standard, which is now in version 1.3.
In a nutshell, C2PA allows “content creators and editors worldwide to create tamper-evident media” so that internet users can see “who created or changed digital content and how it was altered.” In other words: if you see a photo of the Pope in a puffy coat on social media, you’ll be able to quickly check and see if the photo came from a camera or an AI art generator.
So, who was the C2PA created for? This open standard is meant to be adopted by everyone from software creators and device manufacturers to regulatory bodies and government agencies for the benefit of businesses and consumers alike. The goal is to create transparency and authenticity for digital media files.
C2PA has built-in safeguards (including PKI-based digital signatures) to ensure that the authorship or origin information is accurate and can’t be faked or falsified. This is done by including digital media “provenance statements” (i.e., assertions) in a media file, which is then signed using cryptographically based credentials and sealed within a manifest. Assertions are trust signals that inform about the origins of a piece of content and what changes have been made to it.
How to Define ‘Digital Provenance’
Digital provenance is a fancy way of referring to historical information about a photograph, video, or audio recording. A digital provenance record includes information such as:
- When and where a media file was created (using GPS data),
- Who created it,
- How they created it (e.g., using a specific make of camera),
- What changes were made to it (e.g., changes to the image’s color profile),
- How those changes were made (e.g., using Photoshop) and
- When those changes were made.
The goal is to help protect the integrity of digital media by providing a history of a file’s origins and any changes that were made to it. This information is contained within a digitally signed and sealed C2PA manifest that’s contained with each asset. When an author binds key pieces of information to their media file, that data will remain with the content indefinitely.
Here’s a quick visual that breaks down C2PA architecture and the relationships between its various elements:
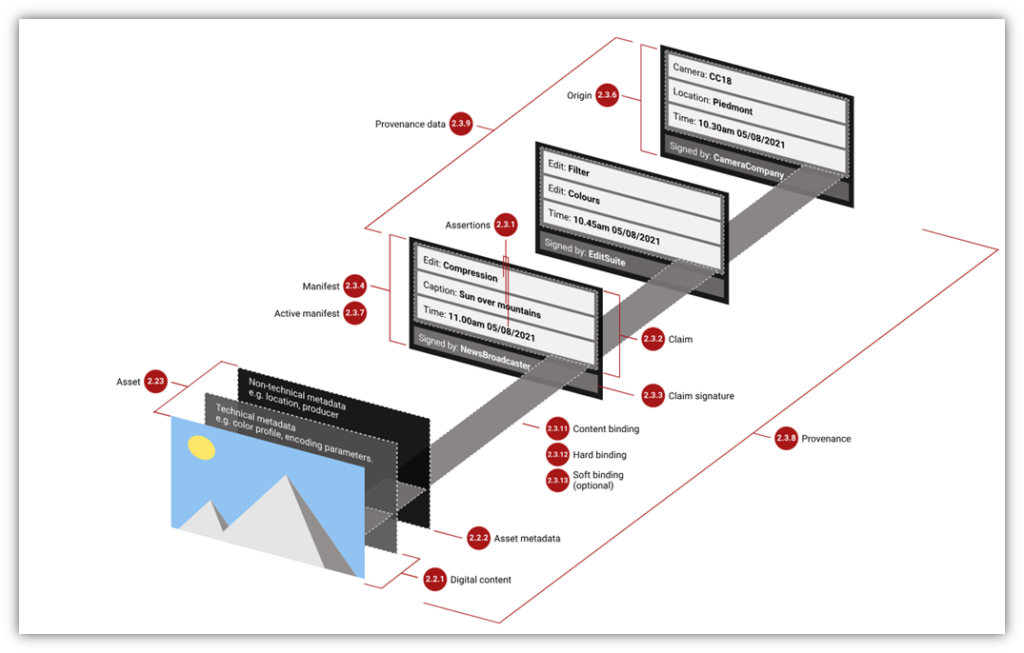
Amit Sinha, CEO of DigiCert, recently expressed his excitement about the initiative in a LinkedIn post:
“Let’s say you take a picture on your phone. Information such as camera, location, time are captured in a manifest and most importantly, digitally signed by the device. Once signed, it cannot be altered. Subsequently, you edit the photo. The filters applied and edits made are captured in another manifest that is digitally signed by the editing software. If the image was used by your local TV station, any changes such as compression applied or captions added are included in another signed manifest.
The key is all these manifests are cryptographically bound in a tamper-proof way to the image. When a user sees the image, they can easily validate its provenance.”
Why the C2PA Open Standard Is Needed
Wondering why all of this is necessary? The internet is an incredible wealth of information, resources, and tools. It puts the world’s information at our fingertips. But to quote the uncle of a famous arachnid superhero, “With great power comes great responsibility.” This is particularly true regarding the power of generative AI and its increasing use in video and image creation.
Of course, not all manipulated media involve the use of AI; someone can use image editing software to carry out these tasks as well. But doing so is often a slow, laborious task. Artificial intelligence speeds up the process and often does a better job of it.
Generative AI technologies are advancing at break-neck speeds, making it hard for consumers to tell what’s real and what’s fake. While some of these “fakes” are created with neutral or humorous intentions, others have more malicious purposes in mind, including:
- Spreading misinformation and disinformation
- Pushing political or social agendas
- Carrying out social engineering attacks to scam companies and individuals
- Creating fraudulent pornographic materials using a real person’s likeness without their permission
- Performing other malicious functions that further erode digital trust
Check out this news piece that talks about how realistic generative AI videos can be:
This media validation process may not be necessary if you’re taking pictures of, say, your dog. However, it serves a critical function if you’re documenting important events, such as capturing photos of civil unrest, recording war-related events, or creating other important societal records.
What C2PA Looks Like in Action
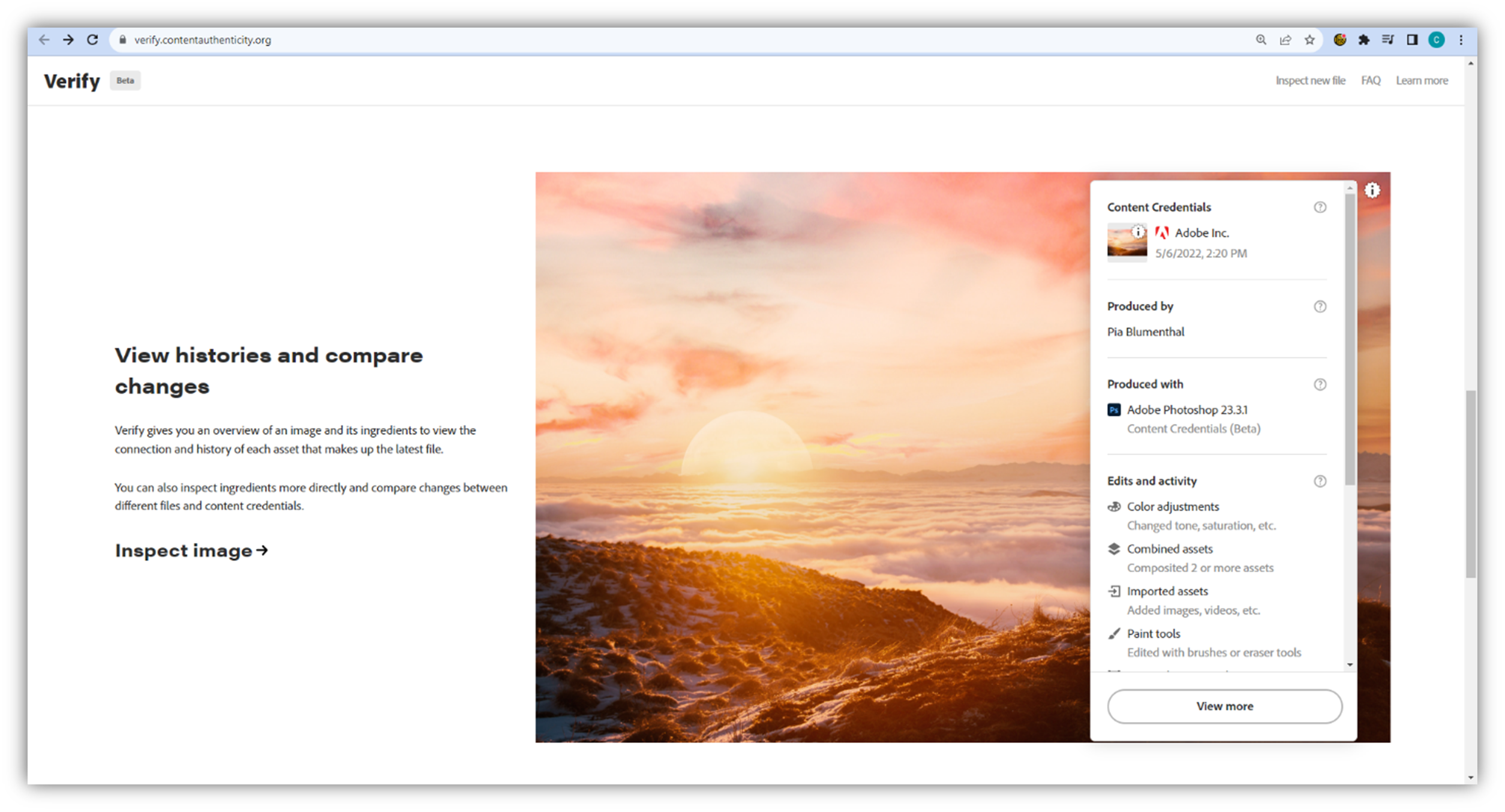
Okay, that was a lot to take in. Before we move on to more technical information, let’s consider an example of how a C2PA-enabled image displays provenance information using CAI’s Verify tool. In the example below, you’ll see overview information about who created the image, what tool they used, and what changes were made to it:
Now, let’s take a look at the content’s “ingredients” to see what went into creating the image:
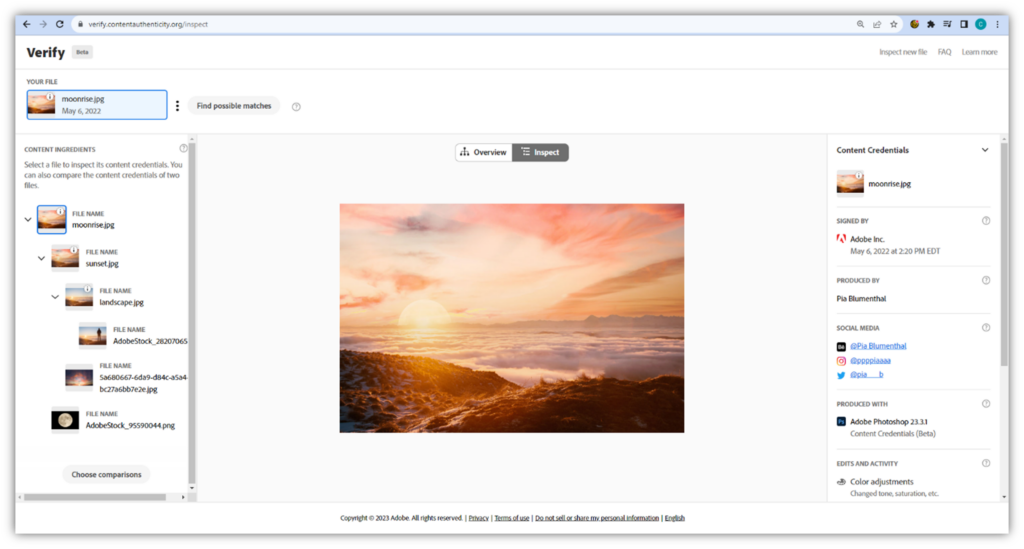
In the Content Ingredients window on the left, you have an option of looking at the original file, along with several iterations of the file that breaks down how the picture has been altered. This allows you to see how the file was manipulated, with the image creator taking elements from several separate photographs and combining them to create the stunning (fake) image you see above. In it, a person has been removed, the sky has been altered, colors have been modified, and the moon has been inserted in a way that almost appears like it’s the sun.
How to Showcase Edits Using Adobe’s Content Credentials (Beta)
Now, let’s take another approach. Here’s a quick look at what it looks like when you have Adobe Content Credentials enabled in Photoshop and make edits to an image. (NOTE: This photograph was shot on my smartphone, which isn’t C2PA enabled.)
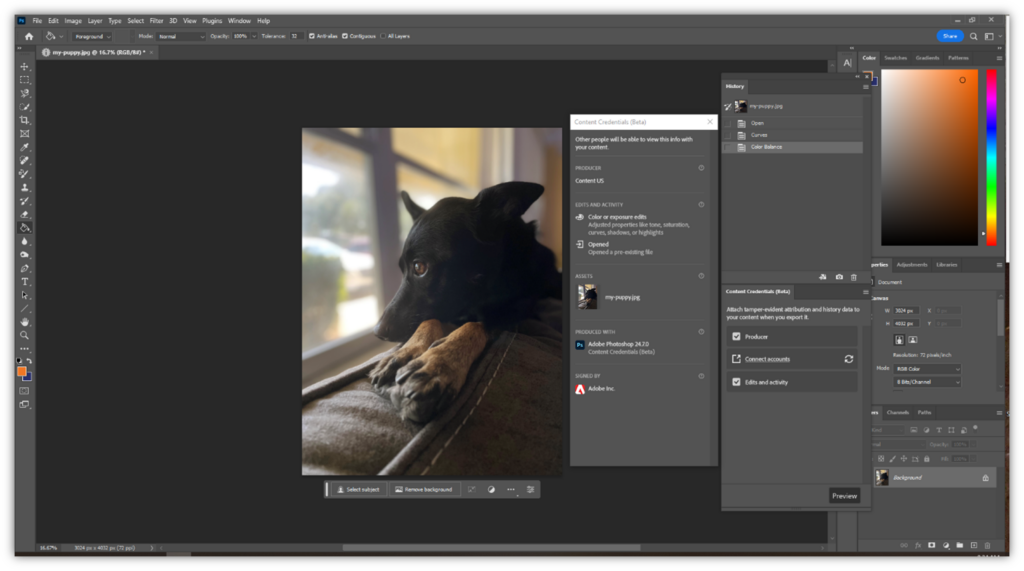
If I was using a C2PA-enabled device to take the picture, the provenance record would contain info about the device I used to capture the image and where the photo was taken. However, that info isn’t available because I used a non-C2PA device. But as you can see in the screenshot above, Photoshop does show:
- Edits I made to the image in terms of curves, saturation, and color balance.
- That the edits were made and exported by me (“Content US”)
- That the edits were made using Adobe Photoshop version 24.7.0
- The Adobe Content Credentials were recorded by Adobe Inc.
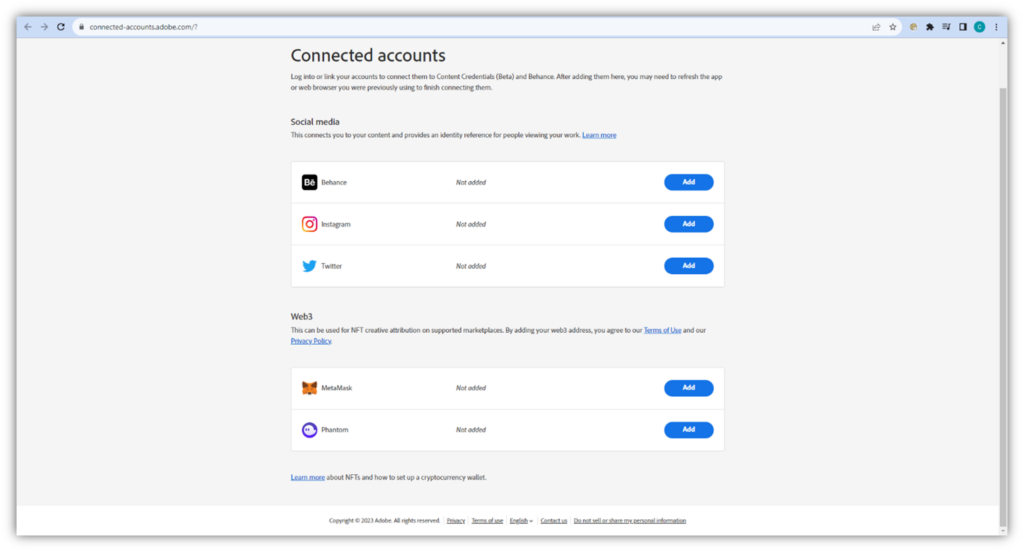
If I opted to connect accounts (using the Content Credentials (Beta) pop-up window, I could connect the content with other accounts, including Behance, Instagram, and Twitter (now known as X).
Now that we know was C2PA is and what it’s intended to do, it’s time to explore how all of this works together to make media validation and trust possible.
How the C2PA Standard Works
Earlier, we mentioned that this standard uses public key infrastructure to make this file validation process a reality for consumers and software. (PKI is the underlying framework of technologies, processes, and policies that we use to secure data and authenticate devices on the internet.) Basically, C2PA uses a combination of cryptographic algorithms, content credentials (using X.509 digital certificates and public-private key pairs), and a trust list to validate the origins of and changes made to a media file.
Let’s consider a quick example with the idea of capturing a photo. When you take a photo using C2PA, certain basic information about the image (i.e., provenance data) is automatically recorded. This creates a record that provides basic file data, including:
- Date and time of when the image was captured,
- Photographer’s name,
- Location information (i.e., where the image was captured)
- How the image was created
Here’s a basic overview of how this multi-layered process works:
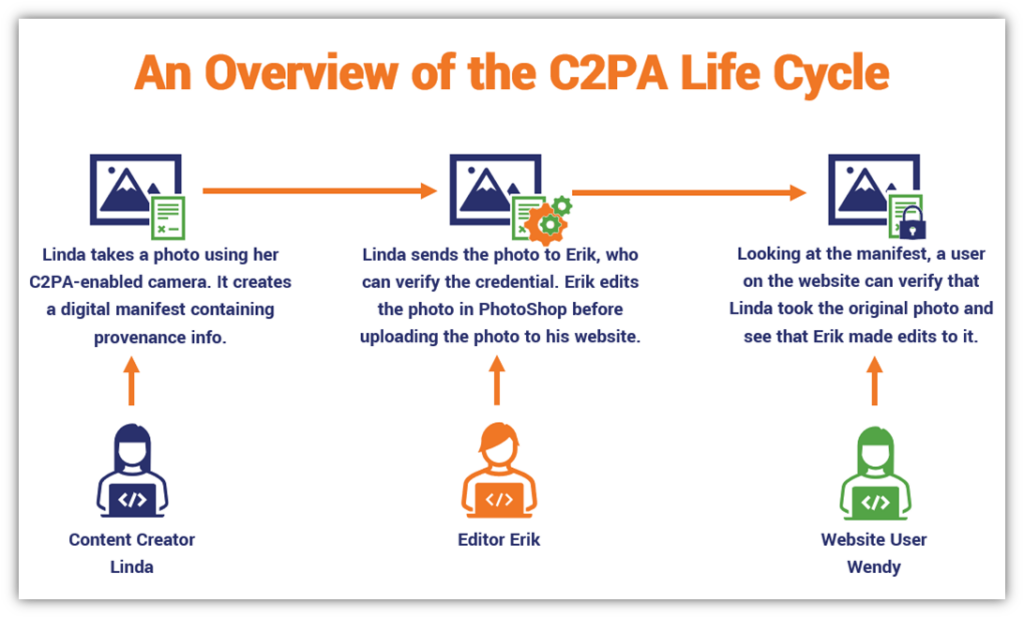
Now, let’s look a little closer at what’s happening under the hood.
- The user takes a photograph using a C2PA-enabled device, which automatically adds the provenance statements to the media file.
- A cryptographic hash function is applied, and then that resulting hash value is digitally signed by the creator using their certificate-based signing credentials. This is then bound together with the image and sealed within the file’s manifest — ideally, with a timestamp that proves the image was published within the signing certificate’s validity period.
- When an editor or another user makes changes to the image using C2PA-enabled software, their changes are recorded in a new set of assertions. This data is then digitally signed within a new manifest that’s attached to the old one, and it’s bound to the image and sealed.
Any changes that are made to the file or its record, no matter how small, will alter its cryptographic hash value in a way that will no longer match the original. This informs a user that the file has been changed at some point and gives them a way to review those changes.
How PKI Plays a Role in the Technical Standard
C2PA relies on the cryptographic algorithms, digital certificates, signatures, and keys that we’re always talking about here at Hashed Out. According to CAI, to get or modify signing Content Credentials that you can use to create and sign manifests, you must first purchase an X.509 digital certificate from a trusted third-party certificate authority (CA). The certificate must include at least one extended key usage (EKU) field that specifies the certificate can be used for document signing and/or email protection. Without it, the certificate won’t work with the open-source C2PA tools (more on those in just a few moments).
The Content Authenticity Initiative recommends using an organization validation (OV) or extended validation (EV) certificate, so your content credentials display your organization’s verified name.
To create trust, the technical specification does make certain recommendations regarding cryptographic algorithms, key types, and key sizes:
- SHA-256 cryptographic hashing algorithm for protecting data integrity, and
- Cryptographic key pairs for generating the signer’s credentials:
- Elliptic curve cryptography (ECC)-generated key pairs (using P-256, P-384, OR P-521 elliptic curves), or
- 2048-bit mod Rivest-Shamir-Adleman (RSA) key pairs
In order for these keys to work, however, they must keep them secure by adhering to the industry’s cyber security and key management best practices. This means using hardware security modules (HSMs), key vaults, or other key management systems to keep them secure. Otherwise, the keys can become compromised and may be used for nefarious purposes.
Which Vendors Currently Support C2PA
The C2PA initiative has only been around for a couple of years and is gaining traction within the industry. Here’s a few C2PA provenance tools and vendors that are helping pave the way to global adoption:
- Trupic — This C2PA-enabled photo capture tool allows someone to take a picture and record provenance information into a manifest. That manifest information is then bound with the image using a cryptographic digital signature.
- Adobe — Adobe Photoshop currently offers Content Credentials in beta testing. These credentials allow an editor to make adjustments to the image and then digitally sign those changes, adding the data to the file’s provenance chain.
- Ravnur — This C2PA-enabled cloud content manager and streaming service is available in Microsoft Azure that incorporates C2PA manifest data into video content.
- Microsoft — C2PA certificate and key management are currently supported through Microsoft Azure Key Vault.
3 Open-Source Tools for C2PA Adoption
Want to build C2PA into your website or product? The Content Authenticity Initiative offers three open-source tools to enable organizations to incorporate provenance data into their app, site, or service:
- Javascript SDK — This library allows a user to view and verify C2PA manifest data. However, it doesn’t allow you to write C2PA data into files.
- C2PAtool — This command line tool enables you to read and add C2PA manifest data to media assets. This allows you to display trust signals on your site or app.
- C2PA Rust SDK — This enables embedded apps, mobile or desktop devices to create, sign, and embed manifests in assets.
To avoid going down a rabbit hole, we’re going to stop here. Click on the links above if you want to learn more about these three resources.
It’s Time to Wrap This Up
Generative AI marks an incredible advancement in creative technological capabilities. And I don’t know about you, but I don’t want to see anything prevent the wheels of progress from turning. However, there’s a growing need for digital trust in media content as a result of this progress. We, as the public, need a way to tell real images from fake or manipulated ones. And content creators need a way to prove genuine content from imposters.
As the first global initiative of its kind, C2PA goes beyond traditional image watermarks and file metadata to provide greater control and security of your media and the files’ integrity. The provenance chain provides a complete view of your files’ journeys, showing every change that’s been made since the image was originally captured.
What’s particularly great about this technical specification is that its security and validation processes are based on PKI. Because it relies on the cryptographic processes and tools we already use to secure data online and validate devices and users, it means that there’s already a known and trusted framework in place. It’s not something new that’s started from scratch.
Although C2PA is still in its early stages, it’ll be interesting to see its progression over time; ideally, as the open standard grows in its adoption. This standard serves as another way to create digital trust in our brave new AI-embracing world.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)











5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown