What Is Smishing? Definition, Examples & Protection Tips
While SMS phishing text scams are nothing new, they’re a type of threat that’s gaining traction with cybercriminals. Proofpoint reports that 84% of organizations faced smishing attacks in 2019 alone…
Smishing, or SMS phishing, is a growing concern as more people use smartphones to stay connected. GSMA estimates that 5.2 billion people globally use mobile services, and their data indicates that 65% are smartphone users. In the U.S., Pew Research reports that 96% of Americans have cell phones of some kind (81% being smartphones). With this in mind, National Cybersecurity Awareness Month (NCSAM) seems like a great time to cover this topic.
We’re becoming increasingly reliant on these mobile devices. People use smartphones for everything from email communications and ordering food to doing online banking and paying bills. This increasing connectivity means that we, as users, are becoming easier for cybercriminals to reach (and scam). In fact, Proofpoint’s 2020 State of the Phish report indicates that smishing is a global issue. This is why we wanted to write an article that talks about SMS-based text message scams, or what is known as smishing.
But what is a phishing text message? To ensure that we’ve adequately covered this topic, I’ve enlisted some help from both my colleagues at The SSL Store as well as other industry experts. We’ll break down what smishing is, what some common characteristics text scams share, what makes them so dangerous to businesses and consumers. And just to add icing to the cake, we’ve got loads of examples of real SMS phishing messages that you can view (both in English and Dutch languages!).
Let’s hash it out.
What we’re hashing out…
- While SMS phishing text scams are nothing new, they’re a type of threat that’s gaining traction with cybercriminals. Proofpoint reports that 84% of organizations faced smishing attacks in 2019 alone…
- Smishing Definition: What Is Smishing? (What Does Smishing Mean?)
- Common Types of SMS Phishing Scams
- How Smishing Works: An Overview of the SMS Phishing Process
- What Makes Smishing So Dangerous
- It’s an Easy, Cost-Effective Attack Vector
- Targeting Your Phone Essentially Gives Attackers the Keys to Your Kingdom
- Smishing Can Get Employees to Give Up Sensitive Information
- Smishing Enables Cybercriminals to Bypass Traditional Security Mechanisms
- Smishing Poses Legal and Financial Ramifications for Consumers & Businesses
- SMS Phishing Damages Your Reputation and Brand
- It’s an Easy, Cost-Effective Attack Vector
- 20 Real World Smishing Examples
- What You Can Do to Protect Yourself & Your Organization from Smishing Attacks
- Final Thoughts on Smishing
Smishing Definition: What Is Smishing? (What Does Smishing Mean?)
Smishing = SMS text phishing. That’s because the term smishing is a portmanteau of “SMS text messages” and “phishing.” So, this means that smishing is a type of phishing that takes place via short message service (SMS) messages — otherwise known as the text messages that you receive on your phone through your cellular carrier. (SMS is a two-way paging system that carriers use to transmit messages.) The goal of smishing here is to scam or otherwise manipulate consumers or an organization’s employees.
These types of messages generally involve some type of content that will prompt you to click on a link. If you do press the link, it’ll take you to a website that tries to get you to provide your login details or other information. The goal here is to get you to provide information that the cybercriminal can use to:
- Access your personal or work-related accounts,
- Commit identity fraud, or
- Engage in some other type of malicious activities.
Wait, Smishing Sounds a Lot Like Phishing…
Yes, it does, and for good reason. That’s because smishing is phishing — or, more specifically, it’s one form of it. It’s kind of like how a cherry pie is just one of many types of pies that you can buy at the store.
Phishing itself is a pretty broad term that describes fraudulent activities and cybercrimes against people and businesses alike. In addition to SMS phishing text messages, phishing is something that can be carried out via through various channels, including:
- Email (think: spear phishing, whaling, CEO fraud, payroll fraud, business email compromise… the list goes on and on),
- Phone calls (vishing, or voice phishing), and
- Social media messages (such as LinkedIn, Facebook, Twitter and Instagram).
Where Did Smishing Originate?
Just as a little fun fact. Macmillan Dictionary says that “smishing” is a phrase that was coined by David Rayhawk in a McAfee blog back in 2006. Since then, people within the industry often refer to the cybercriminals who use SMS phishing attacks as “smishermen” (much like they refer to those who use phishing as phishermen).
While I could keep talking about smishing on my own — after all, there’s a lot to cover — I thought this would be a great opportunity to reach out to experts within the industry to get their thoughts on smishing. We’ll share their insights throughout the article.
Common Types of SMS Phishing Scams
Wondering what some of the most common smishing text scams are? Don’t worry, we’ll show you many real examples of smishing text messages shortly. But just to give you a quick idea, here are a few of the common types of SMS phishing scams cybercriminals use nowadays:
- Texts from banks, investment firms and other financial institutions stating there’s an issue with your account.
- Messages promising free money, products or services.
- Text messages from companies & service providers stating that there’s an issue and you need to update your payment account information.
- Messages from various “authorities about COVID-19 contact tracing updates and various pandemic-related resources.
How Smishing Works: An Overview of the SMS Phishing Process
A basic smishing attack isn’t something that’s all that complex. It involves a cybercriminal having a target in mind (or no target at all in some cases) and a few technologies at hand. More targeted attacks involve the use of social engineering tactics.
Let’s break down how a smishing attack actually plays out:
- A cybercriminal sends an SMS text message to you from a spoofed number. The content and number that the text originated from may make it seem like it came from the legitimate business. If they did their homework, they may even make the message more specific by pretending to be from a company or service that you actually use (such as a video streaming service or a bank).
- You receive the message on your phone that elicits some type of response. The message may contain a tempting offer, or it could be something potentially worrisome that aims to spur you to action.
- What you do next is the determining factor of how things play out. If you just ignore the message or report it, that’s basically the end of it. But if you click on the link, you’ll be directed to a website that appears legit (but isn’t). Either you’ll be prompted to provide info or to download something (such as a device or browser update) before you can proceed.
- You’ll be prompted to provide info you otherwise wouldn’t give away. On this website, you’ll be asked to log in or to provide some other type sensitive details. This could be personally identifiable information (PII), a credit or debit card number, or even your work login info.
- You’ll find yourself downloading something that contains malicious software. By getting you to download malware, you’ve now given them access to your device. They can use their access to spy on you, steal sensitive information, or to access your accounts.
What SMS Phishing Campaigns Tend to Have in Common
Although smishing text messages vary, there are some commonalities that some of the most “successful” (i.e., dangerous) types of smishing tend to share.
Smishing Texts Try to Appear Realistic or Legitimate
In reality, SMS phishing campaigns can span the gamut in terms of realism. In some cases, they’re as obviously bogus as a flashing neon sign that screams “This is a scam!” But in other situations, they’re actually highly targeted or specialized, which makes it harder for recipients to discern them from legitimate messages.
The success of a successful smishing campaign often boils down to how realistic the messages appear. If a cybercriminal can make their text messages seem legitimate, then their targets are going to be more likely to engage with them.
Pieter VanIperen, founder and Managing Partner of PWV Consultants, says legitimacy is key to these types of phishing attempts. As a veteran software architect and security expert, he’s seen many examples of smishing through his clients over the years:
“A successful smishing attempt will likely look legitimate, as if it truly came from where it says. People tend to be trusting, but they have become more educated over the years. This is what led to social engineered phishing attempts, which are being converted to smishing. So it can’t say, “You’ve won the prize! Click to claim!” Because very few people are going to buy that. But it could say there is a new transaction on your bank account that is suspected fraud. And since we often get notifications and 2FA SMS from random 5 and 6 digits numbers we very likely could click on that. Your credit or debit card being stolen and [receiving] an alert about a purchase is quite plausible.” — Pieter VanIperen
Smishing Text Messages Typically Contain Website Links
As with other types of phishing, the goal of an SMS phishing text is to get people to engage with it. Often times, the goal is to get them to click on a link that will take them to a phishing or malicious website. The goal may be to get them to input sensitive information such as their login credentials, or to visit a site that installs malicious software onto their device. Either way, the end results spell bad news.
One quick note to mention is that in many cases, smishing messages typically use URL shorteners. These tools are useful for legitimate organizations that want to minimize the size of messages. However, they’re a go-to tool for cybercriminals because shorteners enable them to disguise malicious URLs. Some good news is that there are tools you can use to expand some shortened URLs, but they don’t work in all cases.
Smishing Text Messages Convey Urgency & Prey Upon Their Targets’ Emotions
So, how exactly do cybercriminals get users to click on SMS phishing message links? Often times, it’s the same as with other types of phishing messages: by conveying a sense of urgency or eliciting other emotional responses. VanIperen touched on this in his example about the suspected fraudulent bank transaction. If a message seems important — like a text from your utility company saying that your power will be shut off for non-payment — people are less likely to simply ignore it.
Smishing Frequently Uses Phone Number Spoofing
We’ve talked in the past about email spoofing, but as you now understand, spoofing isn’t limited to just email phishing. Spoofing is also a tool for phone call scams and SMS text messages. (Yeah, there’s nothing like being in the middle of a virtual meeting when working from home when, all of the sudden, it appears that your own phone number is calling or texting you…)
Spoofing is a useful tool for scammers because it allows them to operate in anonymity. Using mobile apps and other online tools, smishers can send their nasty SMS phishing text messages to people while making it look like it comes from someone else’s phone number.
In the main part of this article, I’ll share with you 20 examples of smishing texts. Something you’ll notice about them is that I’ve edited out the phone numbers that the messages were sent from. The reason for that is that because scammers typically use spoofing, I’d hate to actually display what could be someone’s potentially legitimate phone number that was used in the scam.
What Makes Smishing So Dangerous
Verizon’s Mobile Security Index 2020 report shares that 17% of phishing occurs via messaging. In fact, they shared an example from a Lookout customer that was alarming to say the least. Basically, a global food distributor decided to test the cybersecurity prowess of their executives. They sent the execs an SMS text message that appeared to come from a hotel that they were going to be staying at. You can imagine their disappointment when more than half (54%) ended up clicking on the link.
It’s an Easy, Cost-Effective Attack Vector
But why is smishing so popular with cybercriminals? Morten Brøgger, CEO of the security platform Wire, answers the following:
“SMS phishing is heavily used by cybercriminals because it is one of the easiest, cheapest, and effective methods of cyberattacks. It works by exploiting human error, which is the greatest cybersecurity weakness of regular users and can never be truly prevented since everyone makes mistakes. Cybercriminals need only to send malicious links disguised in seemingly helpful messages with the name of familiar organizations attached to catch a few consumers off guard and gain access to their data. All it takes is a single mis-click for SMS phishing to succeed.” — Morten Brøgger
Targeting Your Phone Essentially Gives Attackers the Keys to Your Kingdom
It’s no secret that people use smartphones as their primary means of communication. They use apps to chat and network with others, bank, engage in ride shares, and conduct their daily activities.
VanIperen says this is what makes smishing attacks so impactful to those who are affected by them:
“SMS phishing is so dangerous because people today carry their entire lives on their mobile devices. There’s an app for everything and we have the world at our fingertips. The problem lies in that mobile devices do not come with antivirus or antimalware programs, so if you click a link that is sent to you by SMS, you’re opening the door for thieves. They can steal anything from your contact list to your phone permissions to your financial information, depending on what the author of the malware designed it to do. Since we keep everything on our mobile devices, attackers can gain access to our entire lives.” — Pieter VanIperen
Smishing Can Get Employees to Give Up Sensitive Information
SMS phishing is a tactic that cybercriminals use to infiltrate organizations through their employees. In these situations, employees become pawns — either with or without their knowledge — and serve as a way for cybercriminals to achieve their goals.
Reuben Yonatan, founder and CEO of GetVoIP, highlights these concerns in terms of blackmailing and a text message form of CEO fraud:
“Cybercriminals have been known to use smishing to blackmail an employee into revealing company secrets. An employee will get a text urging them to reveal x, y, z about the company or something horrible will happen imminently.
Alternatively, the cybercriminal can make the employee reveal the secrets unwittingly. They can send a convincing text pretending to be the boss.” — Reuben Yonatan
Smishing Enables Cybercriminals to Bypass Traditional Security Mechanisms
Brøgger says that smishing allows cybercriminals to bypass many of the security mechanisms that businesses have in place:
“Businesses and organizations spend millions of dollars every year to secure sensitive data worth billions of dollars. SMS phishing can sneak malicious software through firewalls and secure networks by hitching a ride on an unsuspecting employee’s phone. This is particularly concerning with the transition to remote work where employees are in a more relaxed environment at home without the secure networks, systems, and reminders to reinforce their adherence to proper procedures. These risks have loomed large this year as well known companies and people fell victim — the Twitter breach in July and successful hack of Jeff Bezos’ phone (revealed in January), to name a few.” — Morten Brøgger
Smishing Poses Legal and Financial Ramifications for Consumers & Businesses
Kaelum Ross, founder of What in Tech and Senior Technical Project Manager at Fujitsu, looks at the risks in more legal and compliance-focused terms:
“SMS phishing is dangerous to consumers because the end goal of attackers is nearly always to see enough data to complete fraudulent actions (most notably purchases in the consumer’s name) or even blackmail if sensitive personal/employee data is obtained.
The most concerning and common risk for businesses is the risk phishing proposes to breaking laws and legal agreements with suppliers/customers. For example, many business phishing attempts today target data that could be exposed as a leak of GDPR legislation; or for companies operating in say, financial or military industries, phishing can be used to obtain data that is by very strict regulation (or law) meant to not be seen out of employee’s hands with the necessary security clearances. Such breaches can lead to serious legal, reputational, and financial damages.” — Kaelum Ross
SMS Phishing Damages Your Reputation and Brand
Your issues from smishing attacks don’t stop with legal and financial concerns. You also risk customers losing trust is your company or organization.
“Customers expect organizations to protect them from fraud and data theft. They will not only blame the organization if a successful smishing attempt hurts them, but also seek to distance themselves from the company,
A loss of trust from customers can easily crumble your business.” — Reuben Yonatan
Okay, so we now know what SMS phishing is and why it’s so dangerous. Let’s take a look at some examples of smishing.
20 Real World Smishing Examples
Here at The SSL Store, we have employees working from home and in offices in the U.S., the Netherlands, and other regions of the world. So, just for fun, I asked my colleagues to submit examples of some of the smishing messages that they’ve recently received. And, boy, they did not disappoint!
Here are more than a dozen examples of smishing campaigns that my colleagues and I have received on our smartphones.
Cybercriminals Use Smishing Messages That Are Generic or Personalized
The following compilation of smishing example screenshots come from our Director of Sales, Roni Bliss. In some of the examples text message scams below, the attackers reach out to her by name whereas others are spray-and-pray SMS text message phishing attempts.
In the former, they try to use her name to make the messages more engaging and realistic. In the latter, they send out these messages to random numbers with the hope that at least a few of them might reach gullible (or desperate) targets.
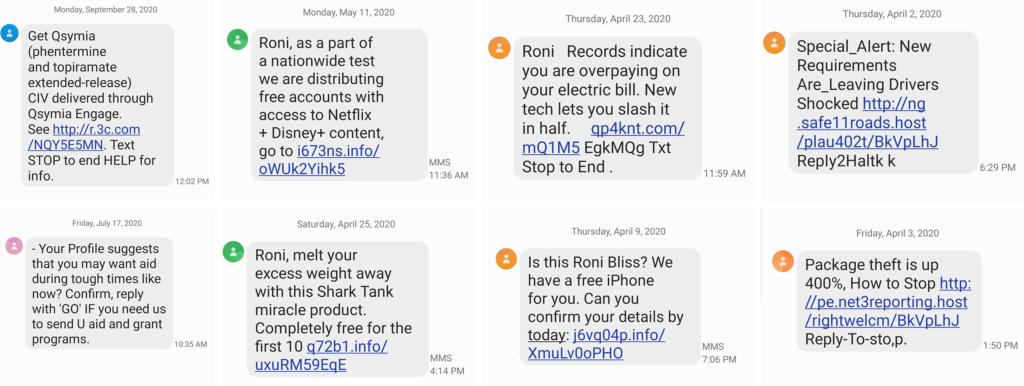
While it’s fortunate for me that my colleague received so many smishing messages (talk about hitting pay dirt for this article), I also feel bad because she seems like a popular target for these messages. So, needless to say, I’m sorry, Roni, but thanks for your contributions to this article!
Cybercriminals Use Smishing to Impersonate Banks & Other Financial Institutions
There’s no such thing as free money. SMS phishing scammers would love you to believe otherwise, but that’s just to get you to click on their malicious links. Here’s an example of a smishing message that was sent to our Business Analyst, Eric Dornbush (and, apparently, nine other individuals as well):
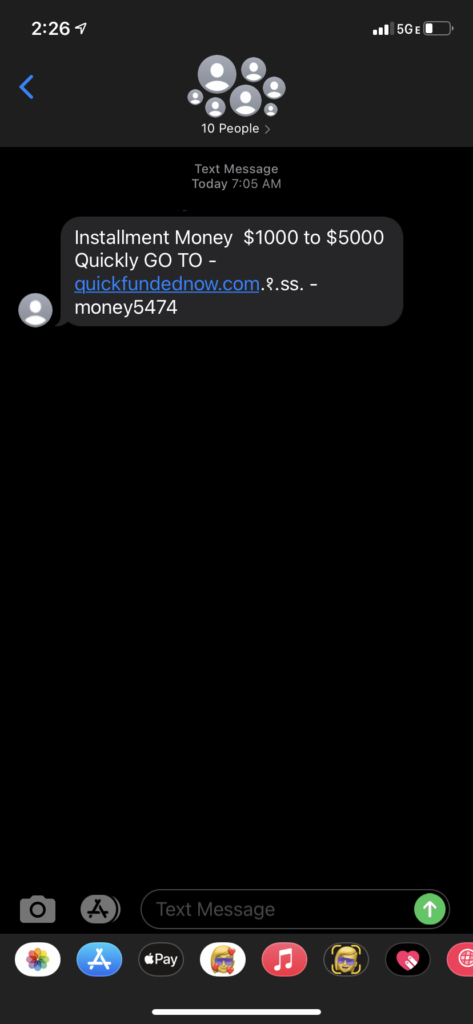
Thankfully, Eric recognized this smishing scam for what it is and didn’t fall for it. Unfortunately, though, all it takes is one person to fall for these types of text message scams for cybercriminals to continue using them.
The next several examples come from my Dutch colleagues in The SSL Store’s EMEA office in the Netherlands. First up is a message that Director of Channel Operations Luc Hullegie received:
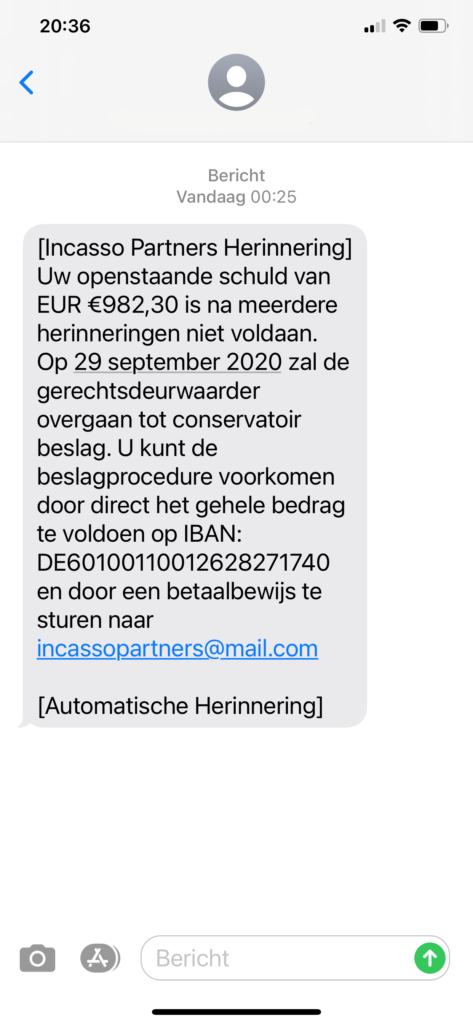
Luc was kind enough to translate the message for me:
“[Collection Partners Reminder]
Your outstanding debt of EUR €982,30 is after several reminders still not paid.
On September 29th 2020 will the [judicial officer proceed to a prejudgment attachment]. You can stop this procedure by immediate payment of the full amount on bank account number IBAN:DE601001100126282711740 and to send us a copy of the proof of payment to email address
incassopartners@mail.com
[Automatic Reminder]”
Cybercriminals also like to impersonate legitimate services to try to steal banking and payment card information. The following three screenshots come from our EMEA Customer Experience Manager Patrick Dijkstra. (Thanks, Patrick, for translating the messages you received.)
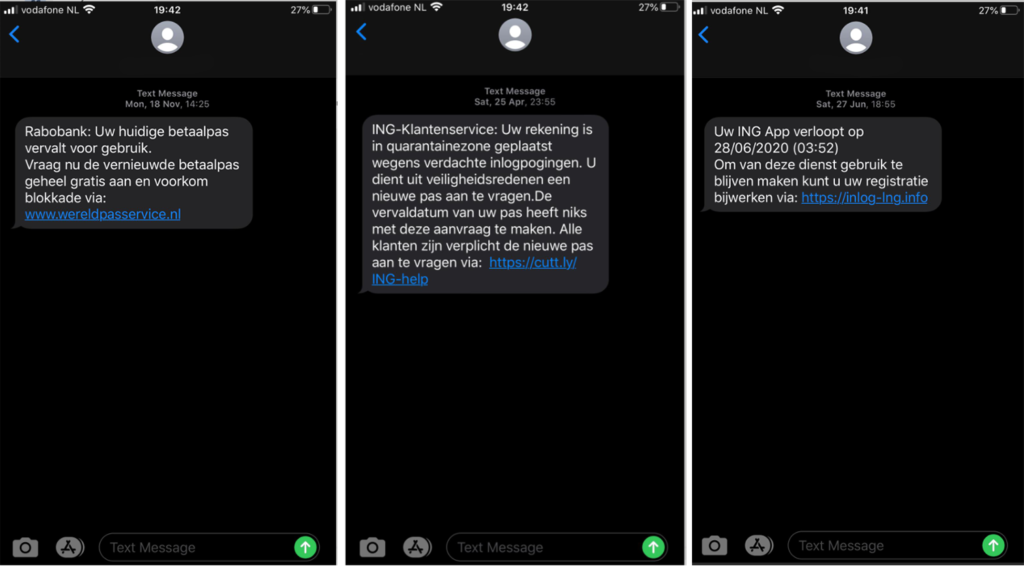
Rabobank is a multinational financial services and banking company that’s based in the Netherlands. ING Group is another such corporation that’s headquartered in Amsterdam. And, apparently, smishermen really like to impersonate both of them in their SMS phishing messages.
The first message is as follows:
“Rabobank: Your current debit card is about to expire. Request the renewed debit card, completely free of charge and prevent being blocked via: www.wereldpasservice.nl”
The second message reads:
“ING Customer Service: Your account is placed in quarantine due to suspicious login attempts. Due to security reasoning, you need to request a new debit card. The expiration date on the card doesn’t matter to this request. All customers are obliged to request a new card via: https://cutt.ly/ING-help”
The third message definitely tries to prompt the user to take immediate action (lest they lose access to their account):
“Your ING App expires on 28/06/2020 (03:52)
To be able to make use of the service, you can update your registration at: https://inlog-Ing.info”
EMEA Customer Experience Agent Kimberly Arler received another similar message from a smisherman impersonating Rabobank.
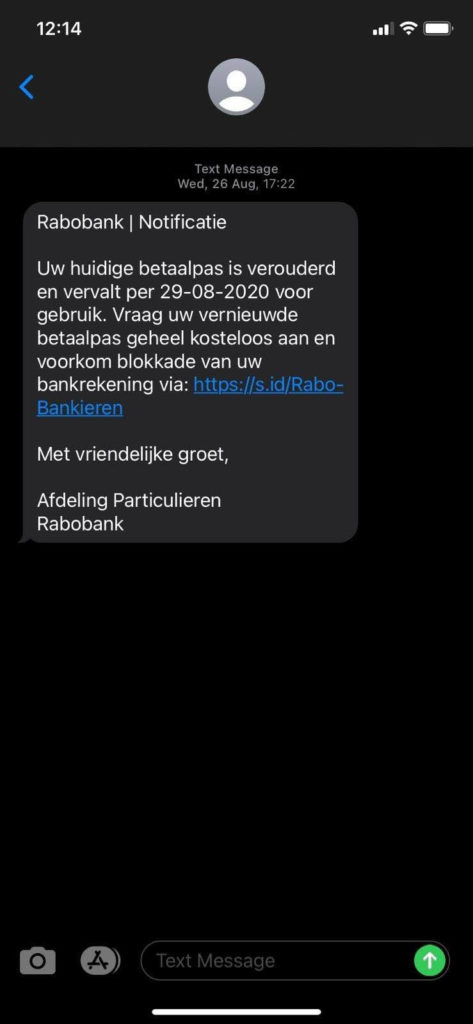
Accord to good ol’ Google Translate, this message says:
“Rabobank | Notification
Your current debit card is outdated and will expire for use on 29-080-2020. Request your renewed debit card completely free of charge and prevent blocking of your bank account via: https://s.id/Rabo-Bankieren
Kind regards,
Rabobank Private Individuals Department”
Come on, now. No legitimate bank is going to sent you a text message to say that there’s an issue with your card. Typically, they’ll send you a secure email (which requires you to log in to their website). You may also receive a regular email that tells you that you’ve got a secure message waiting for you in your online account. But, again, you’d still have to go log in to your account on their legitimate website to access the message.
Cybercriminals Spoof Everything from Netflix to the U.S. Postal Service (USPS)
Scammers are always trying to find new and creative ways to cheat, lie, and steal. Sometimes, this just involves putting new lipstick on their old pigs by changing up old tactics. Unfortunately for many major companies and organizations, they’re often the ones that smishermen love to impersonate in smishing text message scams. Let’s explore some of these examples.
USPS
The U.S. Federal Trade Commission (FTC) is warning users about different types of package delivery-related scams. There’s the “waiting package” scam, which sounds just like what the name would imply. Basically, smishers send SMS texts to targets stating that they have a package waiting for them and include a link for more information.
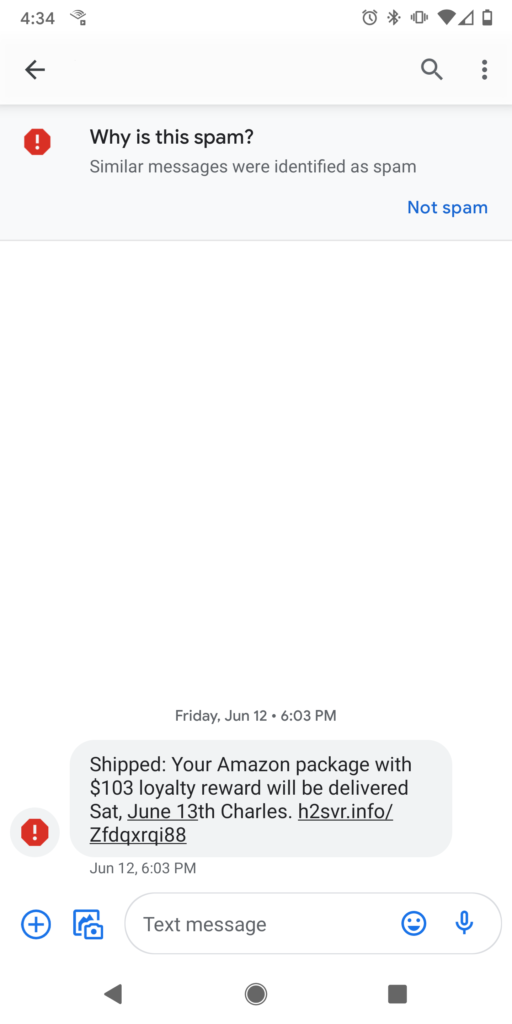
U.S. Director of Customer Experience Marina Lee and U.S. Customer Experience Specialist Philip Ott received the following two examples of smishing messages impersonating the U.S. Postal Service. In the first message that Marina received (although it was directed to someone named “Charles”), you’ll notice that her mobile service provider recognizes the message as a spam message and serves up a warning to indicate as much.
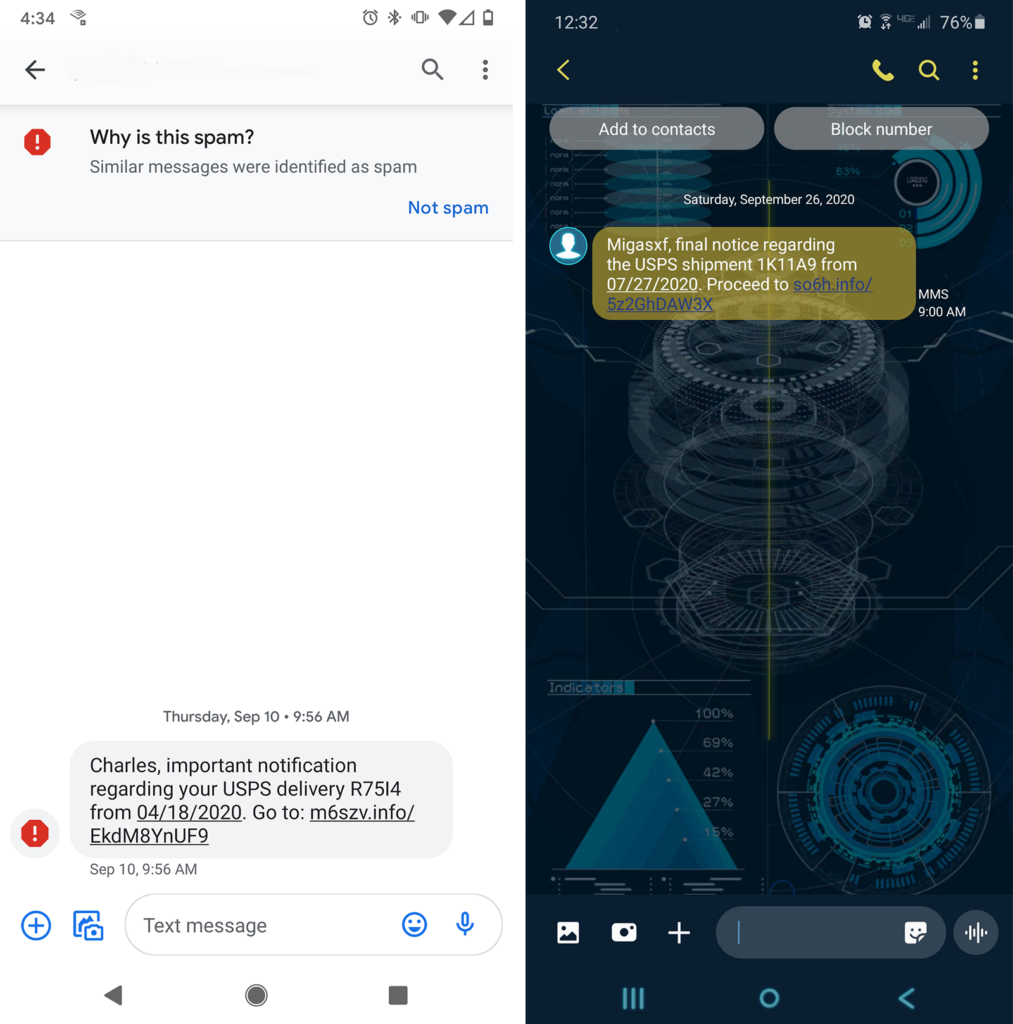
In the second message, Philip’s phone provides no such warning. However, it follows the same type of format as the last message (just with different language):
- A brief statement to create a sense of urgency,
- Delivery tracking info to create a sense of legitimacy,
- A date to further substantiate their claims, and
- A call to action with a link for additional info.
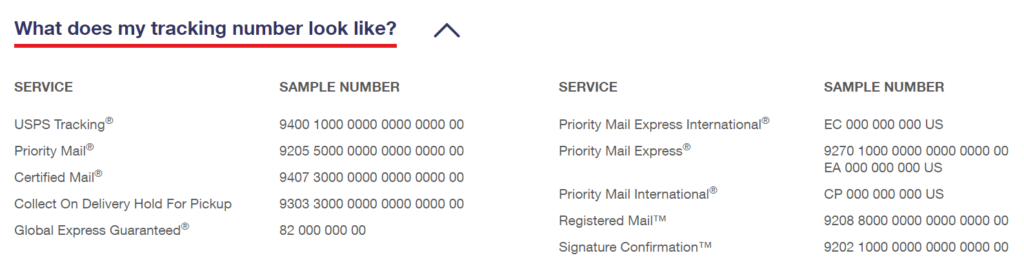
But how are you to know that it’s not a legitimate message? Well, first, ask yourself if you signed up for USPS Text Tracking. (These are texts that notify you about packages that are in transit.) If not, then that should set off a red flag. But another thing to note is that USPS tracking numbers typically range between 10 and 22 digitals (as seen below). Most contain no letters or special characters, and those that do are typically only at the beginning or ends of the tracking numbers. They certainly don’t look anything like the tracking codes included in the messages that Marina and Philip received.
Longtime IT and cybersecurity professional Greg Scott says that the success of these types of messages often relies on timing. He shares an example of a smishing campaign that he personally experienced recently:
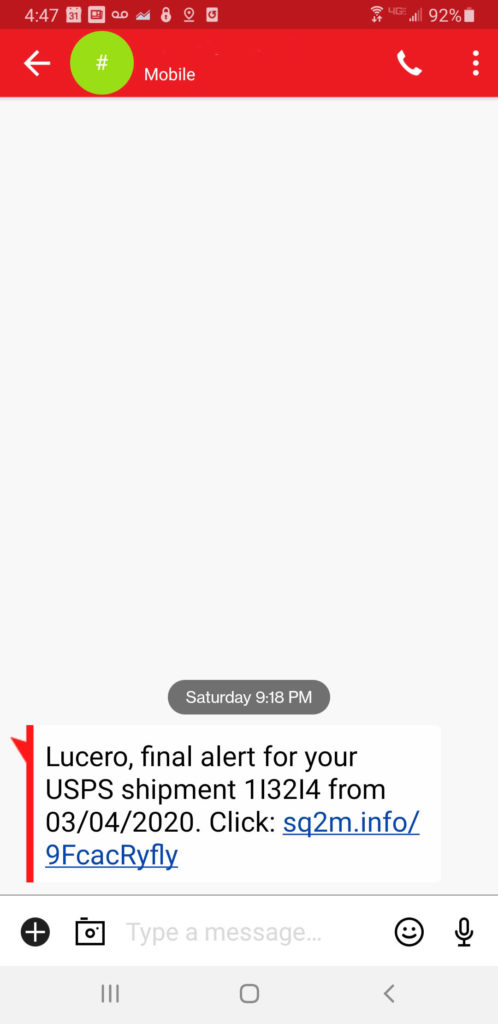
“Timing is everything. We lost a Toyota hubcap a couple weeks ago and I went online and ordered a new set. We’re expecting it to arrive shortly. And so when a text message claiming to come from the USPS came into my phone day-before-yesterday, I almost tapped it to follow the embedded link. Until I looked more closely and noticed it referenced a USPS shipment from 03/04/2020. Why would a shipment from that long ago show up on my phone in September? And then I wondered how did the USPS know my cell phone number?”
— Greg Scott
These are the sorts of questions that people need to ask themselves when they receive SMS text messages. This way, they can ensure that they don’t become another smishing example or SMS phishing statistic.
For curiosity sake, Scott used a virtual machine to see where the link in the message would take him:
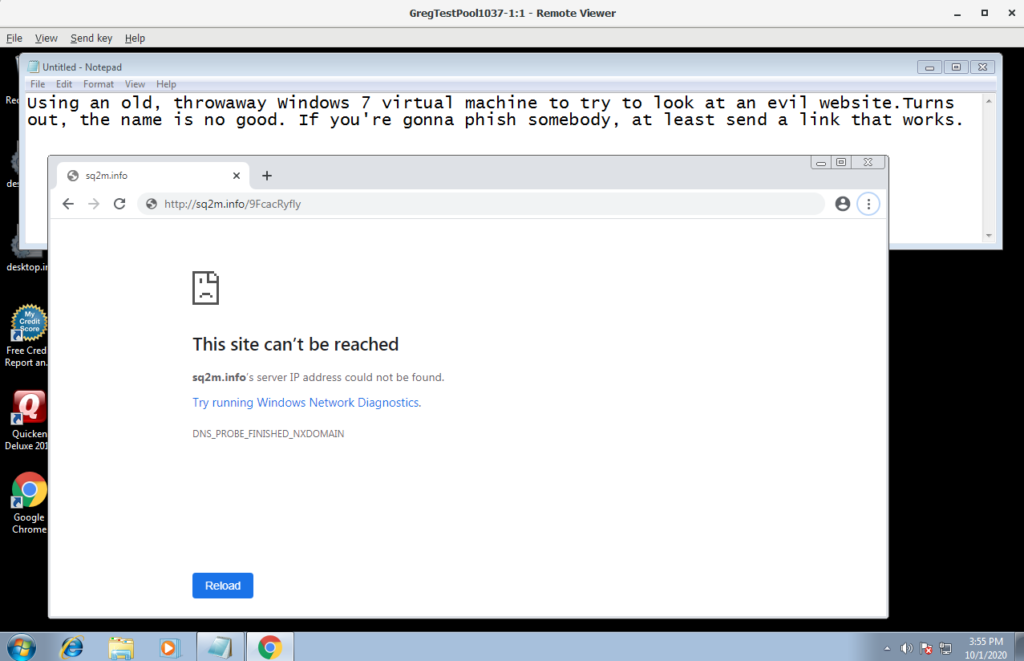
The answer? Nowhere, fast. He received a similar message a day later and decided to check it as well — ending with the same result. According to Scott, “Someone registered the domain name, but there’s no website URL behind it. Maybe it’s a probe just to see if the phone number is good.”
While the links for Scott didn’t resolve or take him to a phishing website, that doesn’t mean you’ll always be so lucky if you click on a smishing link. You might get the real deal and find yourself facing some ugly consequences. So, to put it simply, save yourself the headache and just don’t do it.
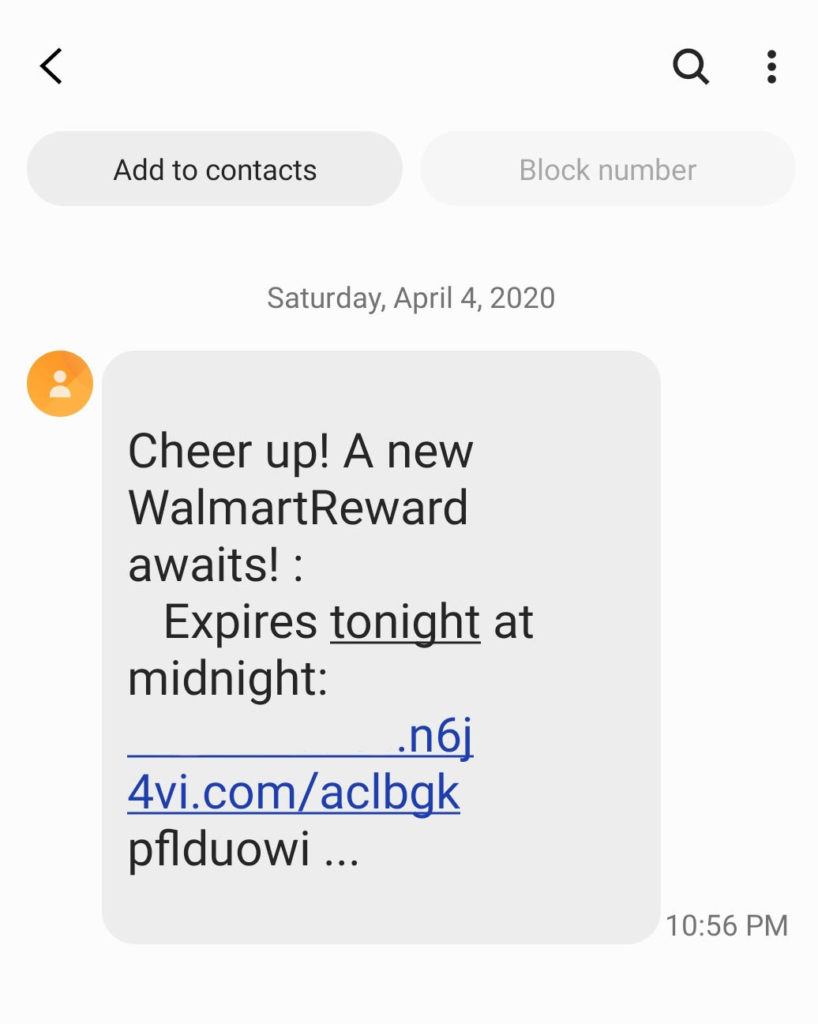
Walmart
In this next example, which was provided by Roni, the attacker makes it look like she has a Walmart Reward available that’s about to expire. The first part of the URL (which I’ve edited out for her privacy) contains her phone number. The message is riddled with errors — a few examples include missing spaces, extra spaces, and extraneous punctuation. Not to mention the clearly non-Walmart URL…
Amazon
No list of smishing examples would be complete without Amazon. Amazon has become such a big part of modern life, and hackers love to take advantage of our reliance on its services. The following screenshot is another example of an SMS phishing scam from Marina. It banks on the fact that many people order from Amazon and that people are attracted to offers of free rewards.
Netflix
I’m sure you’ve seen plenty of examples of Netflix phishing scams in other articles online. While those are frequently email scams, it doesn’t mean that Netflix is immune to smishing text scams. Here’s an example of one such message that my colleague Philip received:
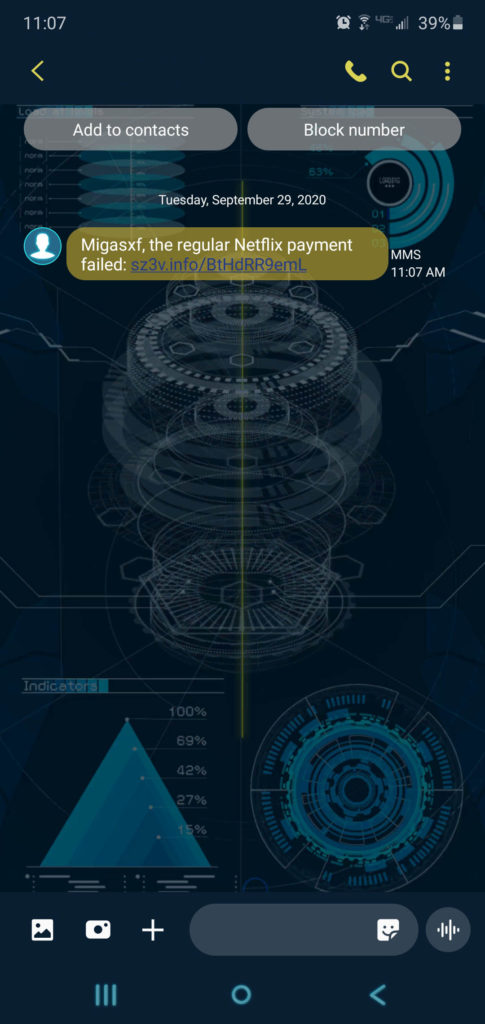
I’ll admit, neither of us is sure what the “Migasxf” means at the beginning of the message (this was included in his USPS message as well). Your guess is as good as ours. I assume it’s where the attacker was supposed to insert Philip’s name. But just look at that URL — does that look anything like something that came from Netflix.com? Yeah, didn’t think so. Straight into the trash this type of message should go!
What You Can Do to Protect Yourself & Your Organization from Smishing Attacks
You can see what kind of a threat smishing is, but what can you do to protect yourself or your organization from it?
How Individuals Can Protect Their Devices and Information
- Don’t open text messages from unknown users. If you get a text from an unknown number — particularly one that contains a link — don’t open or otherwise engage with it.
- If you do open a text, don’t click on any links. Okay, so you’ve opened a text from someone you don’t know and it contains a link that looks like it’s from your bank. Now what? If you aren’t sure whether a message is legitimate, don’t click on it. However, you can always open your web browser and type in your bank’s website address there.
- If you do click on the link, don’t provide any information. This should go without saying but bears repeating since people seem to do this anyway. Never give away any sensitive information via text messages (PII, financial info, work or personal credentials, etc.). If you’re asked to provide info and are directed to a website, go to that website directly in your browser and verify the website is legit by looking at the website’s security certificate information in your browser.
- If you do click on a link and provide info, take action. Okay, you really need to take this time to try to protect yourself. Depending on the type of information you provide, this may involve changing your account security information (passwords in particular), contacting your bank or financial service to report suspected fraud or to cancel your debit/credit card information, filing a report with the major credit bureaus, etc.
- See if your phone has a block or filter feature. Although not all devices may have these options, check to see if yours does. For example, here’s how it looks on my Samsung phone:
Digital Trends has an article that walks you through how to block texts on Android and iOS devices. If this doesn’t work for you, then…
- Contact your cell provider to see if they have a tool or service that’ll do it. Some phone companies may offer such a tool or service to their customers to help you block SMS text messages from known (and/or unknown) numbers.
How Organizations Can Protect Their Customers, IT Systems and Data
Of course, many of the talking points on the list above are also applicable to businesses through employee training. But here are a few other things that businesses and organizations can do:
- Provide cyber awareness training to all employees. The first step to fighting any type of cyber fraud issues is to educate your users about the different types of dangers that exist. This includes educating about phishing, smishing, vishing, and other types of cyber threats. Many of the things we covered in the last section are things you can cover in your training.
- Implement a BYOD policy. If you’re one of the many organizations that allows (or requires) your employees to use their personal devices for work, then this is for you. Create a policy that outlines rules that your employees need to follow when using personal devices and how your IT team will support those devices. This can help you mitigate security risks by controlling how your employees use those devices.
- Use access controls to limit access to only those who need it. You and I know that not everyone within your organization needs access to everything. This is why you should limit access to websites, databases, networks and other essential systems to only those who need access to do their jobs. By limiting access, you’re reducing your potential exposure in the event that someone’s account becomes compromised through smishing or other social engineering efforts.
- Provide a way for customers to notify you about potential scams. In our digital world, it’s always a good idea as an organization to give customers a way to report suspicious messages or suspected fraud.
- Notify customers about potential SMS phishing scams. If you receive word that someone is impersonating your organization, be sure to inform your customers as soon as possible via email. Be sure to reiterate that your organization would never ask customers to verify account information through text messages, social channels, or email.
How to Report SMS Phishing Attacks and Text-Based Fraud
Well, if you’re in the U.K., there’s a new SMS SenderID Protection Registry that’s trying to crack down on SMS phishing text messages for you. So, that’s good news. According to the Mobile Ecosystem Forum (MEF), so far in 2020, “there are more than 50 bank and Government brands being protected by the Registry, with over 14 banks and Government agencies participating.”
Now, if you’re in the U.S. and receive a message that you suspect is an SMS phishing text message, you should report it to the Federal Communications Commission (FCC), and the FBI’s Internet Crime Complaint Center (IC3). (USA.gov’s Online Safety site says that they’ll be able to forward your complaint on to the appropriate local, state, federal or international law enforcement agency.) Of course, you can also report these types of messages to your mobile carriers as well:
- Report smishing and spam text messages to AT&T
- Report suspicious calls, texts or emails claiming to be Sprint
- Report suspicious and spam texts to T-Mobile
Final Thoughts on Smishing
Smishing text message scams aren’t new, but they’re also not going anywhere any time soon. Smishing is definitely one of the areas that every organization should cover in their cyber awareness trainings. This is particularly the case as more individuals use personal and company-issued mobile devices to handle business-related functions.
Cybercriminals are always looking for new ways to target potential victims, or to put new spins on old tricks. I hope this article has provided you with what you need to ensure that you and your employees don’t become the next victims of SMS phishing scams.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)











5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown