Cybercrime Will Increase — And 9 Other Obvious Cybersecurity Predictions for 2022
While cybercrime and cybersecurity are no laughing matters, many cybersecurity articles tend to state the obvious in their predictions. With this in mind, we thought it would be fun to cover some of the most blatant cybersecurity predictions with a tongue-in-cheek approach
It’s not hard to predict the future when it comes to cybersecurity:
- Cybercrime will reach new record-setting levels in 2022.
- Businesses and consumers are going to get scammed out of hard-earned money.
- Bad guys will continue attacking the most vulnerable targets.
Now I’m not psychic, but this seems pretty straightforward to me. But let’s have a little fun with it anyhow. In this article, we’ll explore nine of the most obvious cybersecurity trends and predictions for 2022.
Let’s hash it out.
Prediction #1: A Major Brand Will be Breached Due to an Easily Avoidable Oversight
Data breaches make headlines on a daily basis. Let’s check out the recent Google News headlines regarding data breaches:
Ugh. Not pretty — and they’re certainly not the types of headlines you want your organization to make. Of course, there’s no single cause we can point to or blame for all of these security incidents. Data breaches can occur for many reasons, including the following:
- Network, servers, devices, or applications have unpatched vulnerabilities
- Poor security processes or procedures (or a lack of any documented processes & procedures) are in place
- Employees rely on weak or otherwise insecure credentials
- Employees aren’t trained to recognize or respond to cyber security threats
- Misconfigured servers and websites are being used to collect or store sensitive information
However, there is something that many data breaches have in common: avoidable issues that remained unaddressed within organizations until after crap hit the fan. Whether it’s a misconfigured database or someone falling for a phishing scam — there are steps organizations could have taken to mitigate these issues.
It doesn’t matter how big or small your company is — everyone is at risk of being the target of a data breach. It’s not so much a matter of if an attack will occur but when, and how effectively you prepare yourself so you’re ready for the inevitable. Am I being pessimistic? No, just realistic. The difference in your organization’s outcome depends on how well you prepare for preventing, detecting, and responding to cyber threats and attacks.
Prediction #2: Ransomware Will Continue Its Upward Trajectory
Ransomware is malicious software that’s used to encrypt data and devices to keep a target’s employees from accessing critical systems. Attacks involving ransomware also increasingly involve the theft of sensitive data, too. Last year, Sonicwall reported that ransomware increased from 78.3 million attacks in Q3 2020 to 190.4 million attacks in Q3 2021.
Let’s take a quick peek at their data:
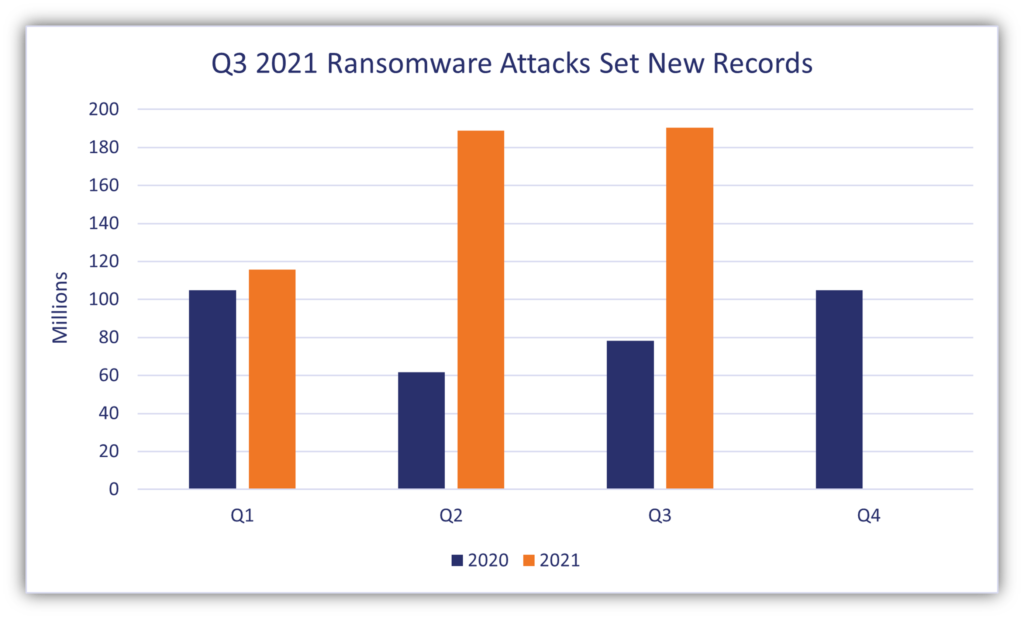
According to their report, as of the end of Q3 2021, the year was “the most costly and dangerous year on record” as far as ransomware attacks were concerned. (Shocking, I know…) If 2022 is anything like last year, and cybercriminals continue to profit on the backs of companies lacking strong cyber defenses, then it’s all but guaranteed this upward trend in ransomware will continue.
To help public and private sector organizations combat ransomware, several branches of the U.S. government came together to create the website StopRansomware.gov. For other related ransomware-related data and examples, be sure to check out our articles on recent ransomware attacks and ransomware statistics.
Prediction #3: Remote Work Isn’t Going Away — Neither Are Related IT Security Risks
In this quasi post-COVID 19 era, many workers aren’t wanting to give up working in their pajamas or sweatpants. (There’s something to be said for being comfortable while working!) As such, many companies are embracing the move to remote working.
However, allowing employees to work remotely isn’t as easy as flipping a switch from a security perspective. Organizations need to invest the time and labor into preparing for at least a partially remote workforce. This includes:
- Securing end users’ devices with antivirus software, virtual private networks (VPNs), etc.
- Creating documentation and processes that facilitate secure access and account creation,
- Securing your network through the use of firewalls, intrusion detection and protection systems (IDS/IPS), and other monitoring tools
- Setting up user access permissions and restrictions to secure network resources
- Providing phishing and cyber awareness training to employees and other network users
Prediction #4: Shadow Digital Certificates Will Lead to Large Site Outages & Other Issues
Although having expired or unknown certificates within your environment may not sound like a big issue, these unknown elements can lead to a litany of issues. But what happens when a digital certificate expires? Important websites and applications that people rely on go down. A few big-name examples of certificate outages in the past few years include:
- Epic Games, which turned their certificate expiration gaff into a teachable moment
- Spotify had to face the music after a certificate expired
- GitHub allowed an SSL/TLS certificate to expire
- Microsoft forgot to renew an authentication certificate (affecting Microsoft Teams)
Considering that DigiCert reports the average organization has 50,000 certificates, it’s no surprise that staying on top of tracking all of these certificates can be challenging. But what makes matters worse is that many organizations aren’t managing their certificates effectively. The 2021 State of Machine Identity Management report from Keyfactor and the Ponemon Institute shows that two in five (40%) organizations rely on manual spreadsheets for tracking their digital certificates.
Another issue that can further increase certificate management-related challenges is that PKI digital certificates now have shortened lifespans. The CA/Browser (CA/B) Forum limited certificate lifespans to no more than 398 days as of September 2020. Understandably, this adds an extra layer of complexity to the situation because certificates now expire in half the time as they did in 2018!
To avoid this issue, organizations should consider investing in certificate management solutions. A good certificate management provides visibility of your network so you know where every digital certificate and its corresponding cryptographic keys are located, how they’re being used, when they expire, and who is responsible for managing them.
Prediction #5: Companies Will Mismanage Employees’ Access to Data & Systems
We’ve said this before and we’ll say it again: no matter how nicely they ask for it, your employees don’t need access to everything. Practicing strong user identity and access management is integral to the security of your data and critical systems. This is why access to databases, servers, drives, customer and employee data, and other sensitive information should be limited to only those whose jobs require it.
Handing out access to everyone like candy expands your attack surface and makes it easier for attackers to breach your network. Why? Because the more people who have access to something, the more at risk it becomes. It’s like giving out the keys to your home: anyone with access can walk in. All it takes it one person not keeping their key secure (e.g., having their login credentials stolen in a phishing attack) to put your safety and belongings at risk.
Another access control issue is not maintaining a current list of active users. If an employee leaves, their accounts and credentials should be deactivated immediately. This way, the former employee (nor anyone else who manages to get access to those credentials) can use that information to access your organization’s sensitive information.
Prediction #6: Users Will Continue to Fall For Phishing & Social Engineering Tactics

Phishing is one of the most common attack methods threat actors rely on for targeting businesses and individuals. It’s an attack tactic that largely relies on social engineering and aims to get someone to click on a link or open a malicious attachment. (The goal is often to get users to provide their login credentials or other sensitive data.)
There are multiple types of phishing that are categorized in various ways depending on the communication methods used and who is either being targeted or impersonated. But why are these attack methods so successful? Perhaps it’s because of the “it won’t happen to me” mindset some organizations have, or maybe it boils down to their employees’ ignorance about the types of phishing tactics bad guys use. Take your pick.
Regardless of the cause, phishing attacks continue to be successful across virtually all industry sectors and organization sizes. Bad guys know that they can continue using these tried-and-true tactics because they work. We don’t expect to see this pattern change anytime soon — especially not within the next year. So, the best steps you can take to combat phishing-related threats include the following:
- Educate your employees on the latest phishing scams and attack methods
- Run periodic phishing tests to test your employees’ knowledge and identify areas where additional training is needed
- Set up your email filters (SPF, DKIM, and DMARC) to limit emails that are sent to and from your domain
- Use brand indicators for message identification (BIMI) and verified mark certificates (VMCs) to protect your brand and domain against misuse
Prediction #7: The IT Security Industry Will Have More Open Jobs Than Skilled Talent
It’s no secret that skilled cybersecurity professionals are in high demand — as they should be. In an increasingly digital world, you’ll find these jobs in virtually all organizations and industries globally. Cyberseek’s supply and demand heat map shows that there are nearly 600,000 cybersecurity jobs open in the U.S. alone.
A 2021 survey of cybersecurity professionals by the Information Systems Security Association (ISSA) and Enterprise Strategy Group (ESG) shows that the cybersecurity skills shortage is still in full effect. While this may seem like a great thing for job seekers on the surface (because it means they have more options), it’s not all so rosy for them — and certainly not for their prospective employers — when you take off those tinted glasses.
The ISSA/ESG’s survey data shows that 95% of the survey’s respondents indicate that they haven’t seen improvement in the skills gap. Furthermore, they think the skills gap has contributed to issues ranging from increased workloads and worker burnout to jobs remaining unfilled.
Prediction #8: Insecure IoT Devices Will Leave Networks Exposed to Attack
For businesses, the internet of things (IoT) represents a connected world of technologies that exist to automate tasks and streamline processes. However, while there are many upsides to integrating IoT within your environments, there are also some serious drawbacks as well. IoT security is challenging as many devices aren’t known for being secure. For example, these devices:
- Typically lack manufacturer updates and patches.
- Can introduce unpatched vulnerabilities to your network that leave you exposed to attack.
- Increase your organization’s larger attack surface by adding new (and potentially insecure) connections to your networks, servers, or applications.
An important example we saw in the last year regarding IoT devices’ vulnerabilities was Name:Wreck. This set of nine vulnerabilities that Forescout Research Labs discovered is thought to affect millions of IoT, OT, and IT devices.
Until IoT manufacturers take the necessary steps to make their devices more secure, we’re still bound to see many vulnerabilities being exploited in 2022. But there is a sliver of light in all of this doom and gloom: there are steps you can take to make using IoT more secure. Check out our related article on how to secure IoT devices within your environment to learn more.
Prediction #9: Businesses Will Increase Their Adoption of Zero Trust Technologies
Zero trust is a concept that entails continuously verifying the identities of parties not just during the initial login process but throughout their entire connected session. But just how popular is zero trust? Keyfactor’s 2021 zero trust PKI research shows that 21% of survey respondents’ organizations have already adopted a zero trust strategy and 49% say they intend to do so within the following year.
However, considering that President Biden announced an executive order that speaks specifically to adopting zero trust architectures and more secure cloud services for federal agencies, it only makes sense that we’ll see zero trust adoption rates increase in that public sector as well. (Biden discussed this executive order and other cybersecurity-focused initiatives in a meeting with 30 industry leaders at the White House in August 2021.) And considering that public key infrastructure (PKI) is a critical element of zero trust and internet security as a whole, we’re sure to see an increase in the use of PKI as well.
Final Thoughts
We’re not trying to reinvent the wheel here with this article. This goal here is to drive home the point that overlooking the basics often serves as the impetus for many cyber attacks and data breaches. To break this cycle and keep your business, data, and customers secure in 2022, cover your main bases by doing the following:
- Educate your employees on cyber threats to increase awareness.
- Provide your IT security team with the tools they need to keep your network and other IT infrastructure secure.
- Document and enforce all processes and procedures.
- Implement identity and access management across your organization.
Use PKI certificates and technologies to increase identity and security within your organization.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown