Digital Signature vs Digital Certificate: A Quick Guide
Digital certificates are akin to the internet’s versions of certificates of authenticity. Here’s what you need to know about them and the public key cryptographic technologies that make them work
Digital certificates and/or signatures make your world more secure virtually everywhere you look online. These tools allow you to send secure emails and exchange sensitive information remotely without having to worry constantly that your data might fall into the wrong hands.
But what is a digital signature? What is a digital certificate? How do they integrate seamlessly into your everyday life as both a consumer and service provider (even if you don’t know it)? We’ll answer all of these questions in this article that breaks down the difference between a digital signature vs digital certificate.
Let’s hash it out.
Digital Certificate vs Digital Signature: A Look at the Differences Between the Two
Digital certificates and digital signatures are just two halves of the same coin. When you’re talking about a digital signature vs digital certificate, each plays a role in establishing and validating digital identity and aids in helping your organization facilitate digital trust. Digital trust is critical to elevating your brand and helping customers feel confident and secure doing business with you.
We’ll go more in-depth on each of these concepts throughout the article. But first, we know some of you are in a hurry and don’t have much time to read this article. We’ve put together a brief overview so you’ll quickly get the gist of the differences and can move on your way:
| Digital Certificate | Digital Signature | |
| What It Is | A small data file (X.509 format) that contains identifying information (usually about a person and/or an organization) | It’s a signed digital asset that consists of a string of characters created by hashing data and encrypting the resulting value. You use a digital certificate to create a digital signature. |
| How to Describe It to Your Non-Technical Colleagues | It’s like a passport for the digital world: it’s issued by a trusted third party and offers assurance that you’re you | It’s like a notarized signature; it’s often used to show that digital assets (such as documents, messages, files, etc.) you create are authentic and haven’t been altered somehow |
| What It Does | A digital certificate ties your organization’s verified identity to a digital asset (website, email, software, etc.) | A digital signature shows who created a file, message, or other digital asset, and that it hasn’t been changed since it was signed |
| How It’s Created | Create a certificate signing request (CSR) and send the information to the certificate authority. They’ll verify your identity and issue the certificate | In most cases, you’ll need a digital certificate in order to create a digital signature. Once you have a certificate, many platforms (Windows Server, OpenSSL, Microsoft Word, Adobe, etc.) make it easy to create and apply a digital signature through the use of a hash function and encryption |
| Where You Can Find One | Installed on web servers, web applications, email clients, computers, mobile devices, IoT devices, etc. | Many important files (such as software installers, PDFs, secure emails, etc.) contain digital signatures. |
| How Long It Is Valid | Each digital certificate is created with a set validity period — i.e., it has both issuance and expiration dates | Digital signatures can be valid far longer than the certificate that created it when it is timestamped |
Alright, now that we’ve had this overview that highlights a digital signature vs digital certificate, let’s dive a little more in depth into each of these elements…
What Is a Digital Certificate?
A digital certificate is a digital file containing verifiable information about you or your organization that validates your authenticity. Basically, it’s a way for the other party you’re connecting to, to check whether you are who you say you are (i.e., you’re not a fraudster).
Digital certificates are kind of like the organizations that issue certificates of authentication for athletes’ autographs. If I want to ensure that I’m getting hockey goaltender Andrei Vasilevskiy’s signature (Go Bolts!), I’m not just going to buy it from some random person on eBay. I’m going to get it from a reputable source that provides a genuine certificate of authentication.
Likewise, the same concept applies to installing code, software, and other executables from reputable sources. You won’t just download unsigned software from a third-party website that could be counterfeit and contain malware, right? (Please say you won’t.) It’s too risky and leaves you vulnerable to data compromise, identity theft, and a slew of other security issues.
Digital certificates are X.509 files that you’ll find at the heart of public key infrastructure (PKI). They come in multiple varieties that serve various purposes:
- Code signing certificates help you prove the authenticity of your software, containers, and code and protect it against unauthorized modifications.
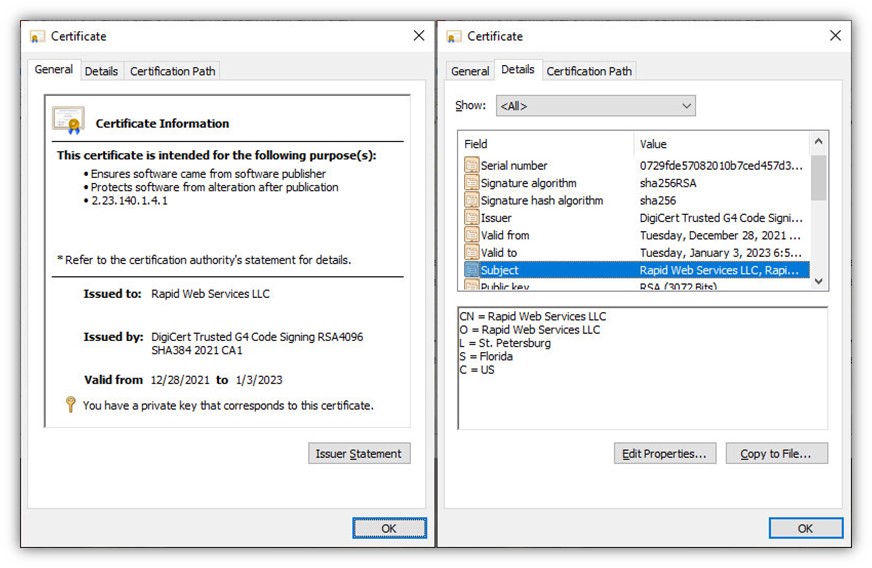
- Document signing certificates help you prove the authenticity and integrity of your Microsoft Office and PDF files. (NOTE: Not all document signing certificates can be used to digitally sign Adobe PDFs.)
- Email signing certificates help you prove to recipients’ email clients and servers that your emails are legitimate and haven’t been altered. They also enable you to send secure, encrypted messages to recipients who also use email signing certificates.
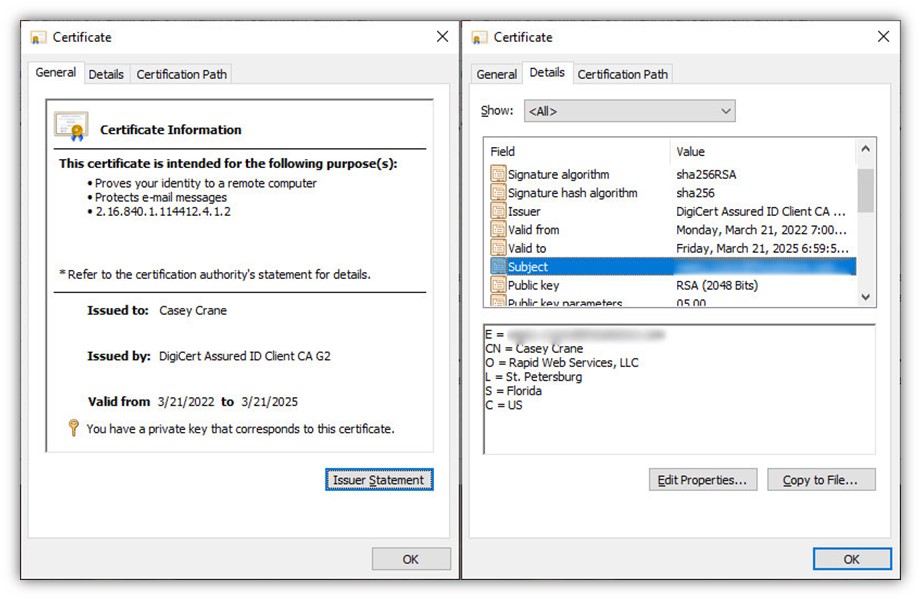
- Client authentication certificates (AKA personal authentication certificates) help you remotely verify your identity so you can access web apps and other resources online. These are frequently the same certificates as email signing certificates
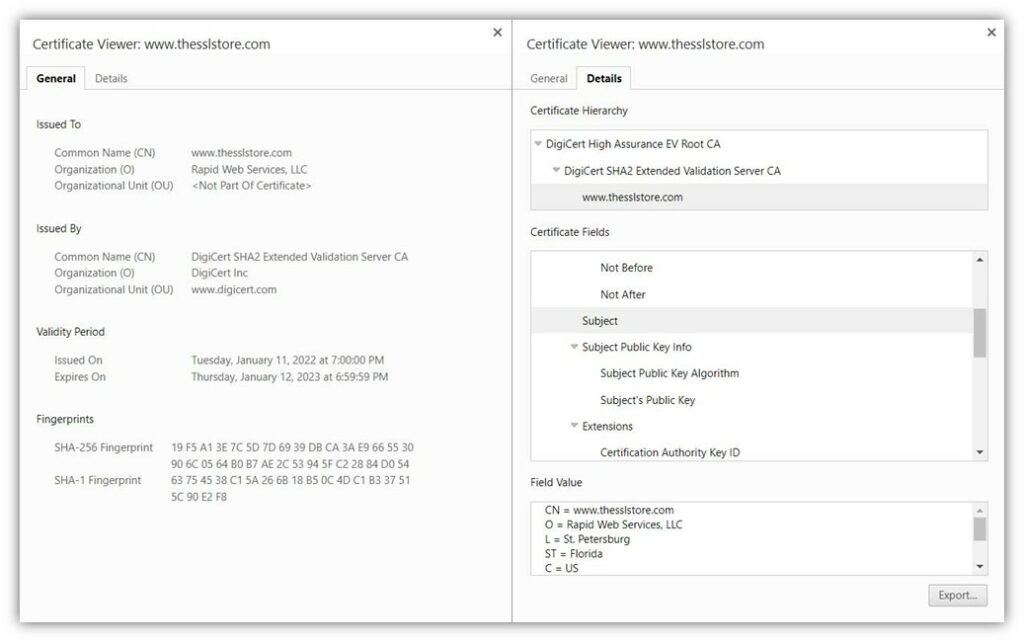
- SSL/TLS certificates help you prove that your website is authentic (owned by you) and enables your server to establish secure connections with users to protect their data in transit.
What Is a Digital Signature?
A digital signature is something you apply to a specific file (using your digital certificate) to prove that the file was created by you and is authentic. In the most basic sense, a digital signature is a way to prove you’re really you (authentication) and that something you created is legitimate (data integrity). More technically speaking, it’s data that proves your identity and that the digital asset you’ve created and signed hasn’t been secretly modified.
In a more technical sense, digital signatures are the values that result from applying a hash function to the data of the digital asset (software, email, document, etc.) you wish to protect and authenticate. This creates a string of data known as a hash value, which you then encrypt using a cryptographic key.
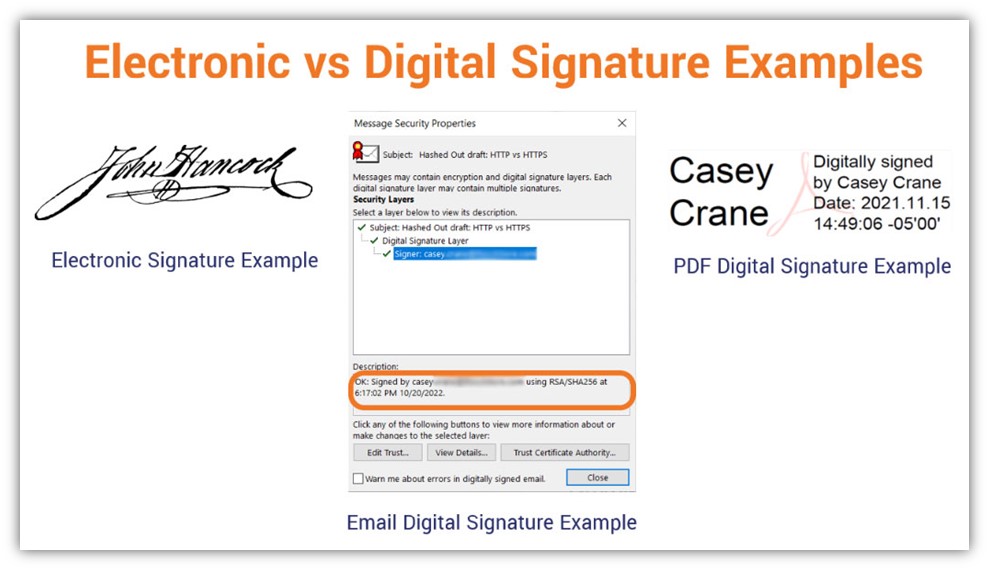
There’s sometimes a bit of confusion surrounding digital signatures and electronic signatures. You’ll find people and companies within the industry referring to them interchangeably. However, that’s not quite accurate. A digital signature is a type of electronic signature, but not all electronic signatures are digital signatures. It’s kind of like how all fudges are desserts, but not all desserts are fudge.
An electronic signature is the digital equivalent of your handwritten signature, whereas a digital signature is something else that doesn’t always have a visual element representing it. Electronic signatures can often be mimicked or faked, but digital signatures cannot be easily copied or faked.
To learn more about what a digital signature is and when to use a digital signature certificate, be sure to check out our other articles on those related topics.
Timestamping Extends the Life of Your Digital Signature
If you want to get the most out of your digital signature, use a timestamp. Timestamping is a method of proving that whatever you signed was signed at a specific moment. It’s an indelible record that shows when your digital asset was signed or modified. By adding a timestamp to something you digitally sign, you’re also extending your signature’s longevity.
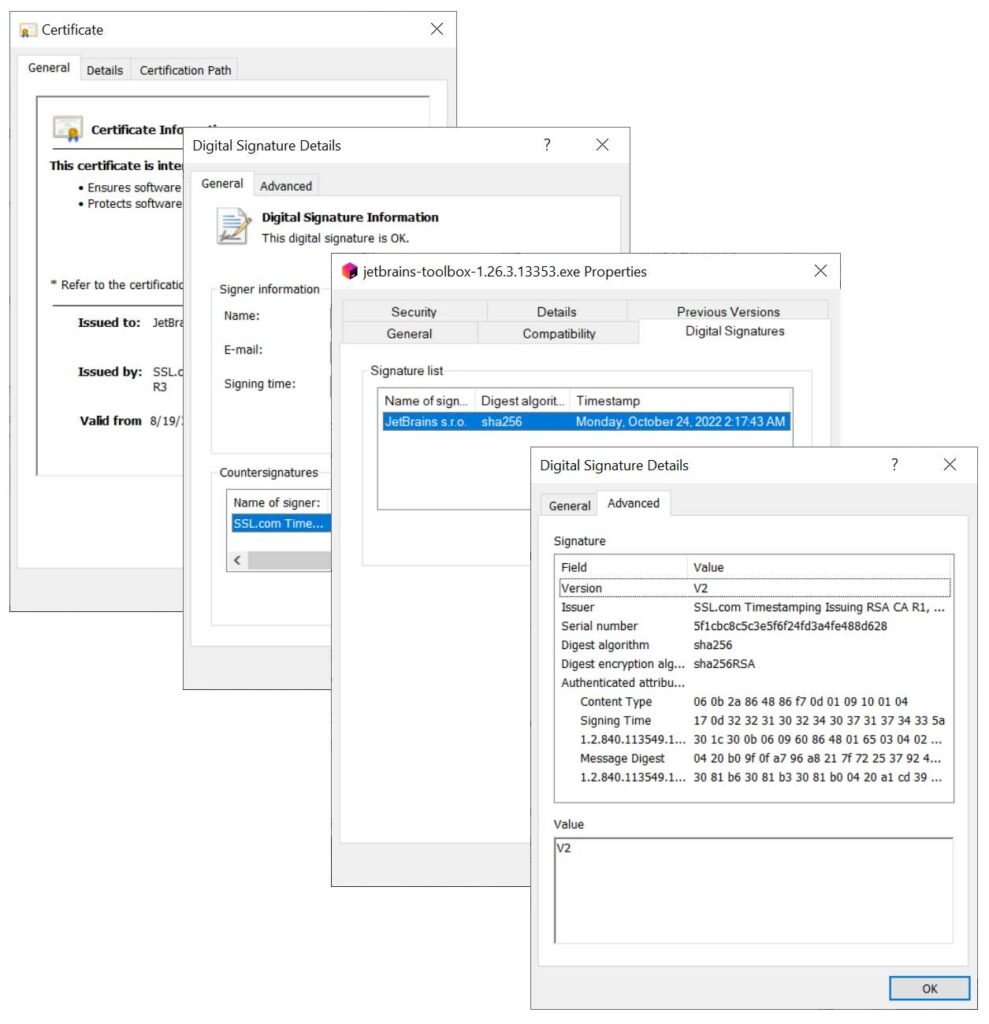
Of course, you don’t always have to timestamp your digital signature; it’s considered an optional feature in some use cases. But timestamping is something you should definitely consider doing when signing software and documents. Why?
- Timestamping your digital signature enables it to be trusted years beyond when your digital certificate expires.
- Adding a timestamp provides a verifiable way to show the precise moment when something was digitally signed.
- Adding a timestamp to your code also mitigates the error messages that would otherwise appear when your digital signature certificate expires. It also means you don’t have to re-sign and release a new version of your asset (unless you changed the file somehow).
- Trying to fake your digital signature’s timestamp would be challenging for cybercriminals to achieve.
There’s a bit of a misnomer that timestamping means that your digital signature is valid forever and will never expire. This isn’t the case. Your signature will eventually expire; it just won’t expire as quickly as your digital signature certificate does.
Digital Signatures and Certificates Are at the Heart of Digital Trust
Nowadays, you always hear people throwing around the term digital transformation, which is all about integrating digital technologies to fundamentally enhance your organization (e.g., increase connectivity and operational efficiencies). But there’s another concept that isn’t just a buzzword and deserves more attention than it receives: digital trust.
Digital trust is everything relating to establishing and upholding trust — it’s the behind-the-scenes processes, compliance, and security mechanisms that make trusting your brand possible for customers. At its core, digital trust boils down to three key elements:
- Digital identity — Offering assurance regarding your verifiable digital identity so they know you’re real and aren’t a shyster,
- Data integrity — Providing assurance and the means for customers to verify that they can trust your asset’s legitimacy, and
- Encryption — Securing communications and data and communications so they can feel confident doing business with you.
Now, I’m going to say something a bit controversial here: you don’t deserve your customers’ trust. While this may sound very negative, the truth is that trust isn’t something customers should give blindly; those days are long gone. In the Age of the Data Breach, trust is something you should — and must — strive to earn.
You can have the fanciest office and IT technologies at your fingertips. But without achieving and securely managing digital trust, your digital transformation is half-baked and won’t live up to your (or your customers’) expectations.
Keeping Your Certificates Secure Requires Careful Management
Your digital certificates and the signatures they create won’t do your business any good if you don’t bother to keep them — or, more importantly, their keys — secure. You see, every digital certificate is issued with a key pair. In the case of publicly trusted certificates (such as the ones we’ve mentioned that are used for external uses), that keypair includes a public and private key. Public keys are available to virtually anyone, but private keys are secrets that must be protected.
As of 2020, Keyfactor reported that the average business’s IT environment has an average of 88,750 digital certificates and keys to authenticate systems and secure data. In 2022, Keyfactor also reported that the average number of “internally issued certificates in an IT organization alone” has surpassed 267,000.
If a bad guy manages to get their grubby paws on even one of your organization’s private keys, then you’re in for a world of pain. A compromised key can lead to everything from data compromises, unauthorized modifications, losses, and theft to costly data breaches and compliance issues. Not only will your reputation suffer potentially irreparable harm, but your customers may, too. Needless to say, this will have a devastating effect on your bottom line.
This is why it’s essential to carefully manage and monitor your PKI. This entails keeping visibility of your IT environment and the certificates and keys within it, managing who have access to your keys and resources, and rotating out certificates and keys as they expire or, on the rare occasion, become revoked.
A carefully managed PKI helps you achieve digital trust and makes for a healthy and successful business.
Final Thoughts on a Digital Signature vs Digital Certificate
As you’ve learned, digital signatures and certificates aren’t so much an either/or kind of thing: you need both to secure your organization and its data. To assert your digital identity, you need to use a digital signature. In order to create a digital signature, you need to have a digital certificate. But when creating your digital certificate, a reputable third party (i.e., a CA) must use their trusted root’s digital signature to offer assurance that your organization has been properly vetted and can be trusted… it goes on and on.
If you want your organization to avoid making the next data breach headline, you must secure your digital identity, data, and communications. Carefully manage and use digital certificates and signatures together to achieve this goal.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown