5 Key PKI Takeaways From the U.S.’s National Cybersecurity Strategy (2023)
The White House’s updated National Cybersecurity Strategy calls for greater regulation and enhanced security of our country’s critical infrastructure. Here are our top 5 takeaways from a public key infrastructure (PKI) perspective…
Every day, we see new headlines about cyber attacks, data breaches, and supply chain security issues. Cyber news has become synonymous with poor cyber security processes, a lack of cyber awareness, and the looming threats that await us in the digital world.
Last week, the Biden Administration released a new National Cybersecurity Strategy document. This is one of several cyber security initiatives in recent years that include the IoT Cybersecurity Improvement Act of 2020 and Executive Order 14028 “Improving the Nation’s Cybersecurity.” It’s no secret that we, as a country and part of the larger global community, need to figure out better ways to secure our digital world. This new official strategy serves as a step toward achieving that.
But the new document is getting some mixed reviews (as with most things political, I suppose). Some call the new National Cybersecurity Strategy ambitious while others say it’s poised to leave the industry in a worse place in certain ways (particularly for smaller organizations). But we’re not here to tell you what to think or discuss politics; you can read the entire strategy document and make your mind up for yourself.
In a hurry and don’t have time to read the entire National Cybersecurity Strategy? No worries. We’ve done it for you. But unlike other articles on the new strategy, our goal is to provide you with an understanding of the role public key infrastructure (PKI) plays in carrying out some of the strategy’s objectives.
Let’s hash it out.
A 30-Second Overview of the New National Cybersecurity Strategy
On March 2, 2023, the White House published its latest plans on how to secure our digital world. Its focus is on making the world’s digital ecosystem more defensible, resilient, and aligned with American (i.e., U.S.) values.
The Biden administration’s updated National Cybersecurity Strategy document, which replaces the 2018 National Cyber Strategy, outlines five pillars that leaders hope to achieve in the years to come:
- Defend Critical Infrastructure
- Disrupt and Dismantle Threat Actors
- Shape Market Forces to Drive Security and Resilience
- Invest in a Resilient Future
- Force International Partnerships to Pursue Shared Goals
Okay, cool. But how exactly is this supposed to work? The Biden administration says that achieving these intended goals requires changing mindsets and approaches. For example:
- Holding the “right” entities liable for securing cyberspace. Who are they, you wonder? Good question. This entails the “owners and operators of the systems that hold our data and make our society function” and the technology providers who build and maintain said systems. That’s a bit vague, isn’t it? With this in mind, the strategy can apply to virtually any company or organization that collects data (with special emphasis on critical infrastructure organizations). The strategy says it wants to move away from placing the blame on end users and small businesses, but regulations often tend to favor larger organizations and make it harder for smaller organizations to be compliant.
- Re-focusing efforts to favor long-term cyber security initiatives. Of course, this doesn’t mean forgetting about the cyber threats and issues we face today. Rather it’s about striking a balance to defend against those concerns now while planning and working to create a more secure tomorrow.
But in order to achieve these goals, organizations must embrace the technologies, policies, and processes that promote proven security, authentication, and data integrity protections. Public key infrastructure is one of the foundational frameworks that can serve as the foundation for many of these goals and cyber security as a whole.
5 Ways PKI Is Integral to the National Cybersecurity Strategy
Here at Hashed Out, the stuff we’re most focused on relates largely to PKI and digital identity. As such, it should come as no surprise that we’re going to highlight some of the strategic objectives that fall within our purview.
We’re not here to regurgitate all of the content shared in this nearly 40-page document. Rather, we want to share the juicy bits you can use: what the strategy intends to achieve, and how you can use PKI to achieve those goals and improve your organization’s cyber security.
1. Implement Strong IoT and OT Cyber Security — It’s No Longer Optional
The Internet of Things is notoriously insecure. As a whole, these devices tend to be plagued by insecurities that don’t get updated or patched. This is why companies across all industries need to integrate stronger cybersecurity controls, standards, and processes into their IoT and OT ecosystems, regardless of whether you’re talking about consumer goods or electrical grids. This is especially true for organizations within the realm of critical infrastructure.
Continuing research and development is important, along with improving risk management initiatives. But what are other things we can do to help improve security for IoT and OT technologies?
Move Toward Universality By Embracing New PKI-Based Standards
A few months ago, we shared about Matter, a new universal standard for Internet of Things (IoT) devices. The goal of this initiative for smart home consumer products is to ensure all devices, regardless of their manufacturers and controllers:
- are universally connectable, and
- have strong cyber security mechanisms in place to secure them against cyber attackers.
The idea here is that if all devices are built to adhere to the same security standards, it will reduce the vulnerabilities and incompatibility issues that have long plagued the smart home IoT industry. This same concept of creating universal standards can also be applied to other categories of IoT or OT products.
This is great when you consider that 90% of consumers don’t have confidence in their IoT devices’ security. And who can blame them when you read headlines about IoT devices being hacked or being used as part of larger botnets?
What does this have to do with PKI, you wonder? Public key cryptography is the foundation of Matter’s security. For devices to become Matter certified, they must use new special digital certificates called device attestation certificates (DACs). The purpose of these certificates is to ensure device authenticity and to enable secure device-to-device and device-to-cloud communications.
Ramp Up the Use of SBOMs
The National Cybersecurity Strategy document shares strategic objective 3.2 (Drive the Development of Secure IoT Devices) to help combat these cyber security concerns. Part of this strategy is to expand the use and development of security labels for IoT devices.
Software bills of materials, or SBOMs, are the software equivalents of the ingredient label you’d find on food products. The idea here is that it informs you about what components have gone into the creation of the software product (proprietary code, open-source components, etc.). From a software developer or vendor perspective, it’ll help you better secure your software supply chain by knowing what components within your product have known vulnerabilities so you can address them.
From a customer standpoint, knowing what goes into the products you install and use within your IT environment helps you stay on top of any security concerns and corresponding updates that need to be applied.
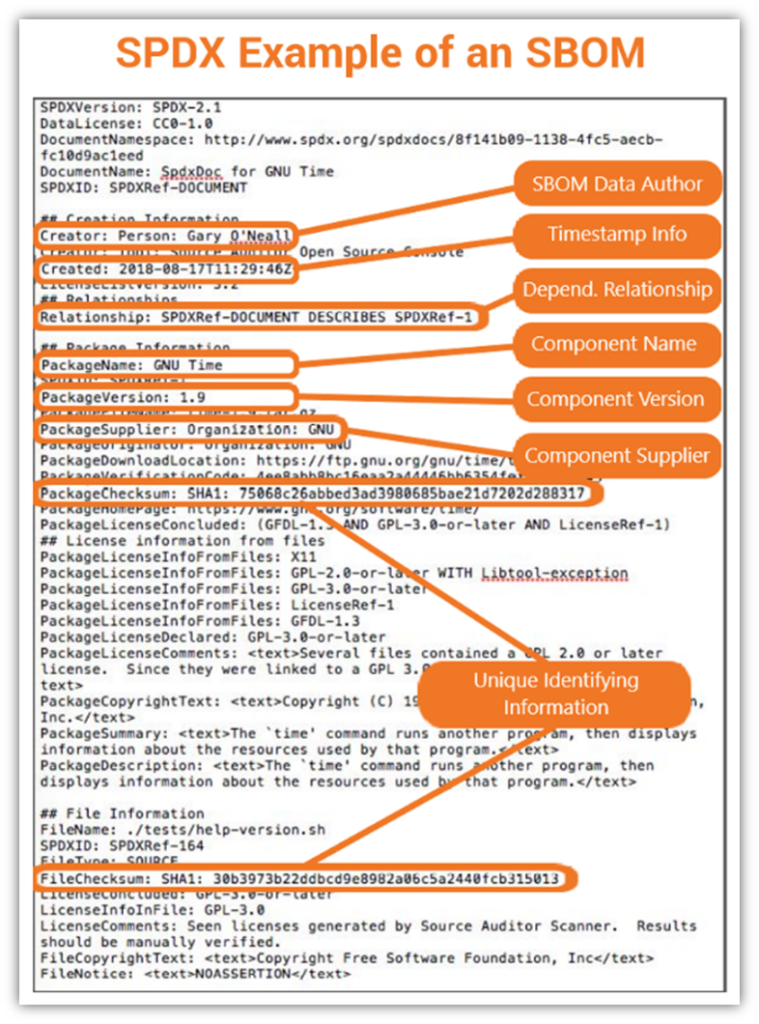
Digitally Sign Your Software, Including Updates
If you want to add another layer of security to your software and SBOMs, you could even digitally sign your file using a code signing certificate. This method attaches a digital signature to your software that proves your software’s authenticity and that no one has messed with it since you signed it.
Are digital signatures a requirement of SBOMs? No, not at this time. But it’s a way to help you prove to end users that your software and its SBOM aren’t fake.
We’ll speak more about code signing your software, code, and device updates later in the article. But it’s important to know that you can digitally sign your device’s software, including patches and other updates.
Secure Your Devices and Their Data Using IoT Device Certificates
Incorporating IoT and OT technologies into your digital environment isn’t enough; you need to do it in a secure way. This includes connecting your devices via a designated network (in some scenarios) installing PKI digital certificates onto your devices. These can be traditional PKI device certificates, or, for Matter-certificate consumer products, it can be the DACs we mentioned a little earlier.
IoT device certificates are small data files that add authentication, data confidentiality, and integrity to your devices and the data they transmit. This is done by adding a verifiable digital identity to your device and using cryptographic processes to ensure the data is transmitted securely from your device and hasn’t been altered in transit. When these certificates and their keys are managed properly, they offer these desired outcomes.
When you use IoT devices within your IT environment, you open up your systems and data to vulnerability-related risks associated with those devices. Cybercriminals love to exploit these issues to gain access to your data or the network the devices are connected to. Once they get in, they can move laterally across your network, seeking additional vulnerabilities to exploit and data to compromise.
For more information on IoT cyber security, check out our related article on how to secure IoT devices within your enterprise.
2. Embrace and Incorporate Digital Identity Within Your Organization’s IT Environment
The National Cybersecurity Strategy’s strategic objective 4.5 talks about the need for digital identity solutions and the infrastructure that’s necessary to support them. Digital identity is a term you’ve probably seen floating around the industry over the past few years. It boils down to creating digital trust through the use of verified digital identities.
But digital identity is far more than just a buzzword, and PKI is one of a few technologies that can be used to create it. Digital identity, in a nutshell, is about creating a secure and safe digital environment both for organizations and consumers. Companies often use public key infrastructure tools and processes to create environments that embrace digital identities.
Of course, the strategy document doesn’t mention PKI in particular by name; in fact, it rarely speaks to any specific types of technologies so directly. But it does encourage investments in “strong, verifiable identity solutions” that strengthen digital credential security and provide credential and attribute validation. PKI 100% fits that bill.
How to Incorporate Digital Identity Within Your Ecosystem
There are many ways to integrate PKI within your organization’s digital environment. Examples of digital identity are found in various types of digital certificates:
- SSL/TLS certificates —These are the digital certificates you install on your web server to assert identity on your website and protect customers’ data in transit against interception attacks. They’re what make the security padlock icon appear in customers’ browsers when they visit your website.
- Code signing certificates — These digital certificates attach your digital identity to your software, code, and executables to prove their authenticity and that they haven’t been modified.
- S/MIME certificates (email signing and encryption certificates) — These digital certificates enable you to digitally sign and encrypt sensitive information sent via email. (Be sure to check out our article on the new S/MIME baseline requirements that will go into effect in September 2023.)
- Client authentication certificates —These certificates provide passwordless authentication, so you can log into web applications and systems without using credentials that are vulnerable to phishing attacks and other password security-related issues.
- PKI device certificates— These are the certificates we mentioned earlier that you can install on your devices to protect the data they transmit from prying eyes. They also authenticate your devices to your network, so you know they’re legitimate and not imposter devices.
- Device attestation certificates — These certificates for IoT devices are the ones that help make your consumer IoT products Matter certified. Of course, other steps are involved in becoming certified, but installing these certificates are a critical step in that process.
- Document signing certificates — These certificates are used to digitally sign PDF files and other documents. Document signing enables you to prove that the documents are legitimate and haven’t been altered since they were digitally signed.
Digital identity is at the core of public key infrastructure. Without a verifiable digital identity, PKI wouldn’t work because there would be no way to authenticate parties.
3. We Need to Do What We Can to Help Secure Internet’s Technical Foundation
One of the key points highlighted in the strategy document is that we must secure the technical foundation of the internet. The first thing that came to mind when I read strategic initiative 4.1 was, “no kidding.” Some examples of the weaknesses the strategy wants stakeholders within the global community to address include mitigating border gateway protocol (BGP) vulnerabilities and securing DNS queries.
Clearly, this is a non-exhaustive list as there are many other ways to make the internet more secure. But making the internet as secure as possible, while critical, is no small task. The good news is that there are steps public and private organizations alike can (and should) take to make their piece of the internet as secure as possible.
For example, organizations can leverage existing cybersecurity frameworks, such as the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework and its Framework for Improving Critical Infrastructure Cybersecurity. Additionally, here are a few of the ways you can help make the internet (and your organization) more secure at a foundational level using PKI in particular:
Use HTTPS to Secure Website Connections
Here at The SSL Store, we’re huge proponents for transmitting data via the secure hypertext transfer protocol. When you enable HTTPS on your website, you’re enabling customers’ data (e.g., their login credentials or credit card information) to transmit using transport layer security.
This added layer of security keeps their sensitive information from being read by unintended third parties. It also brings authentication into the equation, ensuring that users are connecting to the right website and not an imposter.
Enable DNS Over TLS (DoT) or DNS Over HTTPS (DoH)
Domain name system (DNS) attacks have become increasingly common and dangerous threats to organizations globally. Unfortunately, many organizations tend to put their heads in the sand, leaving their DNS queries vulnerable.
But just how big a threat are DNS attacks? In 2021, EfficientIP and IDC reported that DNS attacks cost an average of $950,000. (Note: This stat includes mitigation efforts and other costs). What makes things worse is that eight in 10 (87%) of the survey respondents indicated that they had experienced at least one such attack.
Use the hypertext transfer protocol secure (HTTPS) to encrypt certain parts of your otherwise unencrypted domain name system (DNS) requests. This is known as DNS over HTTPS, or DoH for short. Doing this helps to encrypt what information users access on websites to increase their security and privacy.
Why is this important? Because, depending on where you live, accessing certain types of information could lead to serious consequences, including imprisonment. It also helps to previous bad guys, advertisers, or other interested parties from intercepting your DNS request data.
Another option is using DNS over TLS (DoT). It’s similar to DoH in that it’s encrypting some of your DNS request data. However, the biggest difference between DoT and DoH is that they use different protocols. It’s also easier for network administrators to monitor and block malicious traffic queries via DoT than DoH, because HTTPS-secured DNS requests are more easily concealed among the rest of your HTTPS traffic.
Use SMTPS to Secure Your Email Server
Another important aspect of foundational internet security can be found in the simple mail transfer protocol secure (SMTPS), which is the secure version of the otherwise insecure SMTP protocol. Traditional SMTP sends data without using encryption, authentication, and data integrity protection.
SMTPS requires you to enable TLS on your mail server to secure your data at the transport layer, which is why it’s sometimes referred to as SMTP over TLS. SMTPS is like writing a plaintext (i.e., readable) letter to your significant other and placing it inside a lockbox. A bad guy would need access to the secret key to access and read the contents of the lockbox.
This differs from the S/MIME encryption afforded by the email signing certificates we mentioned earlier. S/MIME certificates digitally sign and/or encrypt the contents of the email — your text, photographs, or other attachments — before the message leaves your mailbox. It’s like writing your letter in a secret language only your loved one understands before placing it inside an open envelope. Even if someone else pulls the message out of the envelope, they won’t be able to read it because they don’t know the secret code you and your loved one use to communicate.
When you pair SMTP with S/MIME email encryption, you secure both the message’s content and the channel it’s sent through. This protects your data via end-to-end encryption, protecting it both while it’s in transit and sitting on a server. If you want to take security to the next level, set a mail transfer agent strict transport security (MTA-STS) policy and enforce it. This ensures emails can be received specifically using TLS 1.2 or TLS 1.3 authenticated connections.
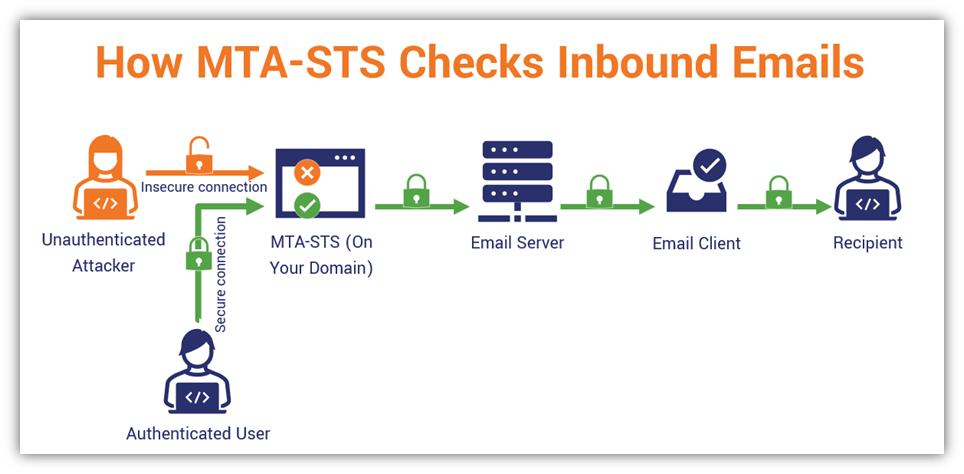
To learn more about MTA-STS and other email server security best practices, be sure to check out our related article on ways to secure your email server.
4. Organizations Must Do More to Secure Software Supply Chains
Sprinkled throughout the National Cybersecurity Strategy, there’s an emphasis on securing supply chains and mitigating their associated security risks. This encompasses both global physical supply chains as well as software supply chains, although the strategy document emphasizes the importance of securing critical infrastructure in particular.
One of the most obvious ways to make software supply chains more secure is for organizations to adhere to industry security standards and best practices. For example, NIST’s Secure Software Development Framework. Now, let’s focus on the PKI-specific approach…
Use PKI to Secure Your Servers and Software During the DevOps Lifecycle
Part of securing your software supply chain entails integrating security into your devops process (i.e., devsecops) and following industry software security best practices and recommendations. A few examples of ways to achieve this include:
- Installing SSL/TLS certificates to secure connections to your development and production servers, and
- Using client authentication certificates to secure authorized users’ access to them.
- Incorporating (private) code signing certificates into your development lifecycle to help authenticate and protect the integrity of your code or executable prior to its release.
But what can you do to add security to your code once it’s ready to be published or distributed?
Digitally Sign All Codes and Executables Prior to Release
Regardless of the release of the National Cybersecurity Strategy, one of the recommendations we always make is to authenticate and protect the integrity of your code, containers, and executables using publicly trusted digital signatures. You can do this using a code signing certificate that’s issued by a publicly trusted certificate authority (CA).
A code signing certificate attaches your digital signature (i.e., a representation of your digital identity, much like how you use a passport to prove you’re you) to your digital asset to prove its authenticity. It also uses another cryptographic function to ensure the integrity of your asset hasn’t been compromised in some way since it was released.
Unlike the private certificates we mentioned earlier that you can use during development (which aren’t trusted outside your network), Windows operating systems and browsers recognize these publicly trusted certificates. They’ll display your digital identity to users so they know your software is authentic.
In the case of extended validation (EV) code signing certificates, you can make it so your software is automatically trusted by Windows browsers and OS platforms — this way, no Windows Defender SmartScreen warnings will display to end users. This way, you can avoid alarming messages like this displaying:
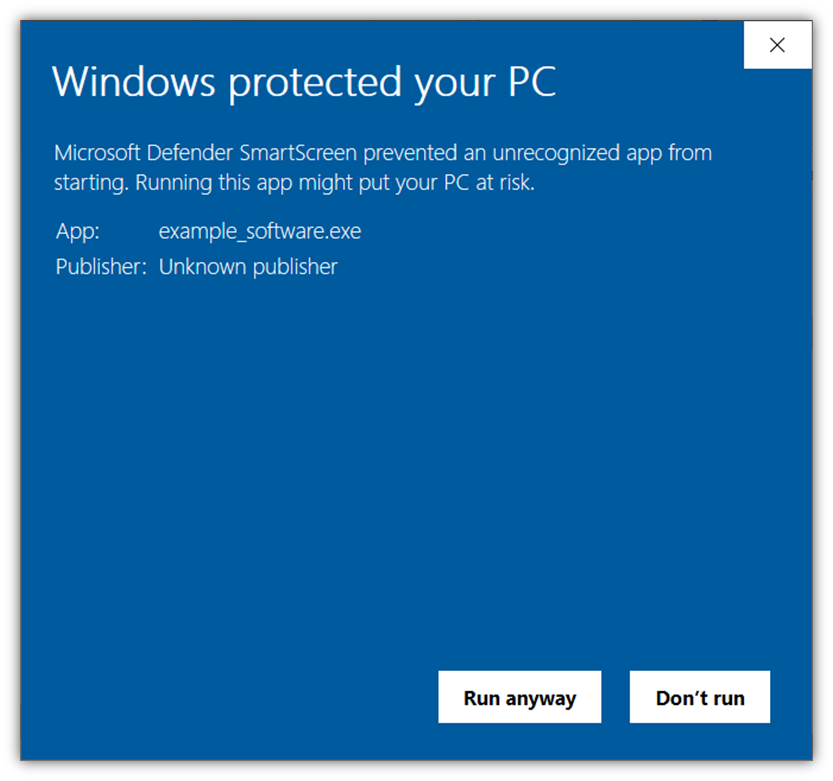
Implement Certificate Management Best Practices
A surefire way to undo all of the good you’ve achieved using PKI certificates is to mismanage them or their keys. If your organization’s public key infrastructure was Superman, then the mismanagement of your certificates and keys would be its kryptonite. This is why we always harp about the importance of carefully managing your certificates and keys.
This is because the cryptographic security these certificates offer is only as good as the security you provide to its keys. If a secret key becomes compromised, then all of the data or systems you’ve used it to secure are also at risk of exposure. So, to protect the security of your certificates and the data they secure, then protect the cryptographic keys that work behind the scenes.
Since this article is about the Biden administration’s National Cybersecurity Strategy, we won’t get into the specifics of certificate and key management there. Check out our related articles to learn more about encryption key management best practices and key management services.
5. Organizations Need to Start Preparing For Quantum Computing-Related Threats
Quantum computing is a threat that’s been looming over our heads within the industry since the early 1980s. It became a much more significant concern with the unveiling of Peter Shor’s quantum algorithm in 1994, which threatened to break modern public key cryptography as we know it. This will lead to what’s become known as the post-quantum cryptography (PQC) world.
What PQC means for companies and governments globally is that the systems we rely on to secure data, authenticate users and signatures, and validate data integrity will become broken and insecure. Knowing this, it’s easy to see why quantum computing is something we recognize as a real threat. However, in some ways, it’s also become an overplayed cry that many organizations have started to tune out over the years because it’s on the horizon but it’s not here yet.
PQC is a threat that every organization should be concerned about. It’s something to start preparing for now, but it isn’t a threat to our world quite yet. Basically, now is the time to prepare but it’s not the time to panic. It reminds me of Rule #7 regarding hurricane preparedness from my favorite Florida meteorologist, Denis Phillips: “Stop freaking out… until I tell you to. We’re fine…”
Start Migrating Your Systems Now
The National Cybersecurity Strategy calls on organizations to replace or migrate their systems. To face the threat on the horizon, the White House announced the new National Security Memorandum 10 (NSM-10), “Promoting United States Leadership in Quantum Computing While Mitigating Risks to Vulnerable Cryptographic Systems” in 2022. This memo outlines a multi-year process for migrating vulnerable public cryptographic networks and systems to ones that support quantum-resistant cryptography.
To prepare for a post-quantum cryptography (PQC) world, your organization needs to be resilient and must be able to evolve by beginning the process of transitioning to quantum-resistant algorithms. To help with this, leading certificate authorities like DigiCert have been working on solutions to aid these efforts. For example, DigiCert has a PQC test tool kit that’s designed to enable organizations to start testing PQC algorithms within their networks using hybrid certificates that are:
- backwards-compatible with both existing cryptographic keys (i.e., RSA/ECC),
- compatible with a new PQC keys (in this case, for the CRYSTALS-Dilithium algorithm).
Final Thoughts on PKI’s Role in the New National Cybersecurity Strategy
Although the new National Cybersecurity Strategy document doesn’t mention public key infrastructure specifically, PKI plays an integral role in helping organizations achieve the strategy’s desired cyber security outcomes. It touches everything from verifiable digital identities and IoT security to secure online communications and software supply chains.
We hope that this article has been a refreshing new take in the sea of recent articles talking about the White House’s new cybersecurity strategy. Be sure to share your thoughts and insights in the comments below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown